
That makes it a good time to harvest all attacks on the RDP port, TCP 3389, because there may be interesting stuff there!
This is a simple way to set up an RDP honeypot on a Linux machine. But BE CAREFUL! I have no reason to imagine that this is safe or secure, so I recommend using something like an Amazon Free EC2 machine with nothing you love on it, so there's nothing there for a hacker to take.
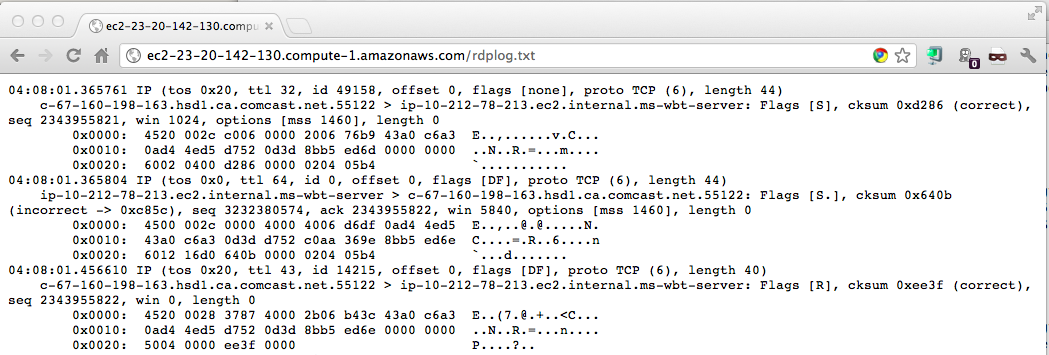
Packets Captured on My RDP Honeypot
Demonstration of the MS12-20 RDP DoS Attack
Execute these commands:
sudo yum install gcc make pam-devel openssl-devel vnc-server libtool libX11-devel libXfixes-devel curl tcpdump -y
wget http://sourceforge.net/projects/xrdp/files/latest/download?source=files
tar xzf xrdp-0.5.0.tar.gz
cd xdrp
./bootstrap
./configure
make
sudo make install
sudo /usr/local/sbin/xrdp
Execute this command:
netstat -an | grep 3389

https://console.aws.amazon.com/ec2
Log in with your Amazon account.
On the right side, in the "My Resources" section, click "1 Running Instance".
In the left pane, click "Security Groups".
Near the top of the panel, check the "quick-start-1" box.
In the lower pane, click the "Inbound" tab.
In the lower pane, on the left, enter a "Port range" of "3389". Click the "Add Rule" button.
Your list of TCP ports should now include port 3389(RDP), as shown below (you may not have all the other ports open):
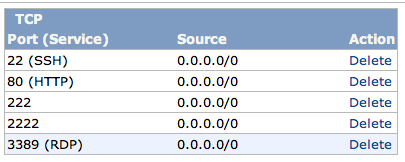
In the lower pane, on the left, click the "Apply Rule Change" button.
In the left pane, click Instances.
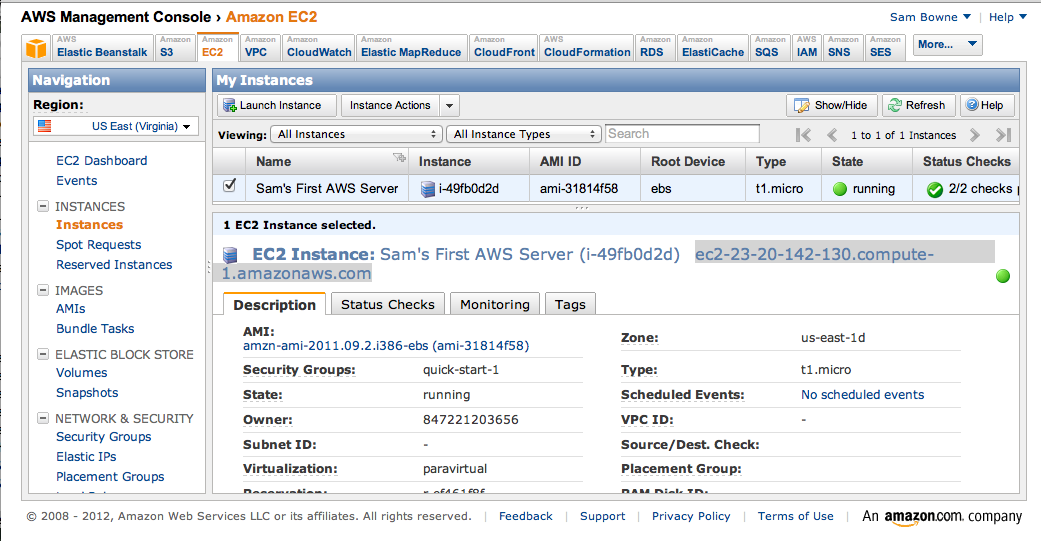
In the top center, check the box next to your running instance--in my example below, it is named "Sam's First AWS Server".
In the lower center, the complete DNS name of your Amazon machine appears. Make a note of this name--you will need it later.
In my example below, the name is ec2-23-20-142-130.compute-1.amazonaws.com
Execute these commands:
cd
sudo tcpdump tcp port 3389 -i eth0 -vvX >> /var/www/html/rdplog.txt &
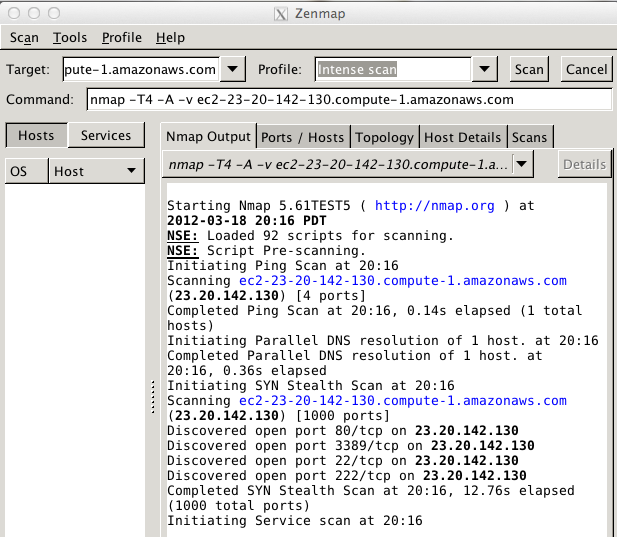
Run nmap and perform a default scan of your Amazon web server, using the DNS name you found earlier.
In my case, the name was ec2-23-20-142-130.compute-1.amazonaws.com
You should see port 3389 open, as shown below:
That's it! Now you can see who is trying to exploit your RDP.