This will certainly provide my students with practice using Burp, and it may also help to inspire Amazon to modernize their security practices.

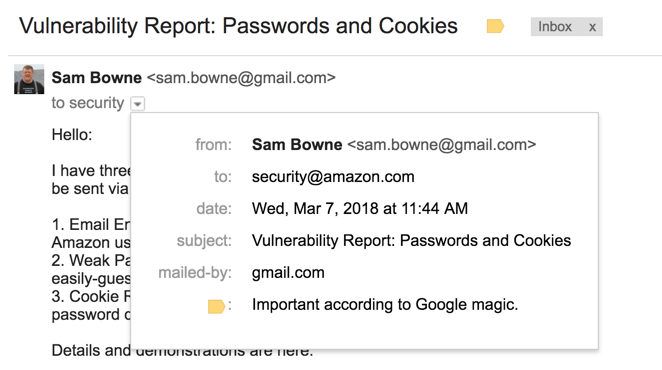
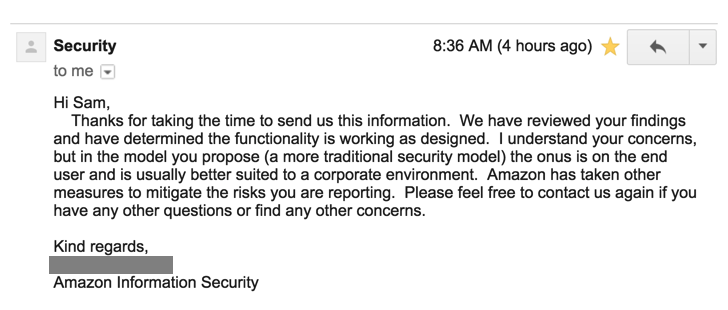
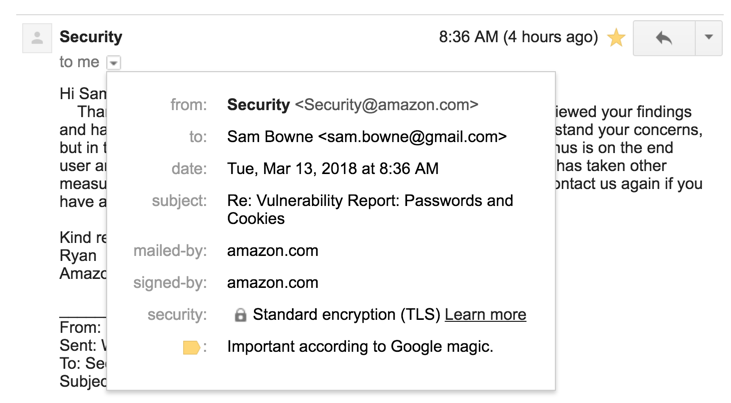
They responded within a few days, saying that there's no actual problem, and the site is working as intended. Evidently there's nothing to worry about.
Launch Burp.
At the first Burp page, accept the default selection of "Temporary project" and click Next.
At the second Burp page, accept the default selection of "Use Burp defaults" and click "Start Burp".
In Burp, click the Proxy tab and the Intercept sub-tab and make sure "Intercept is off".
In Burp, on the Proxy tab, click the Options sub-tab and make sure the proxy is running on local port 8080, as shown below.
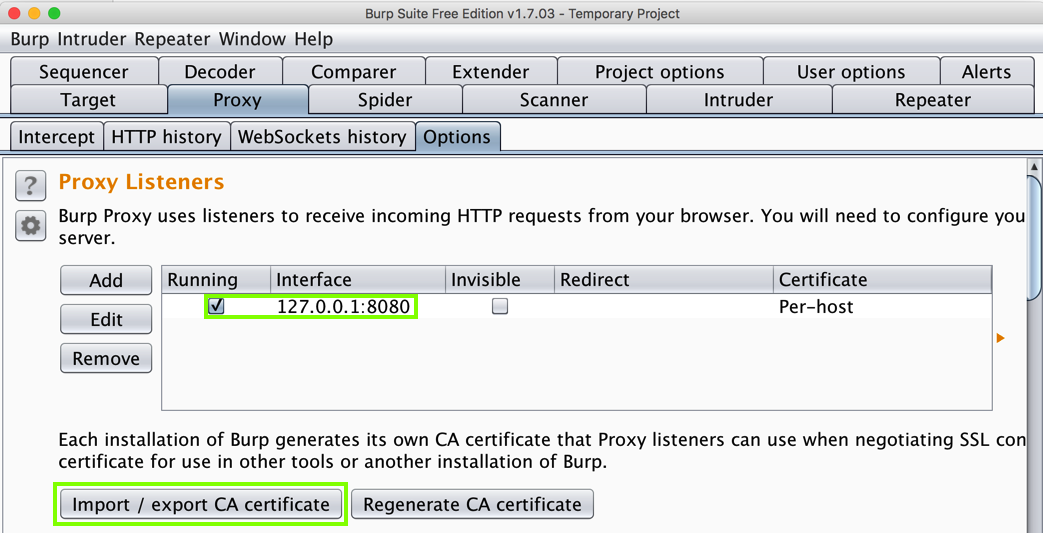
In Burp, click the "Import / export CA certificate" button, as shown above.
On the next page, in the Export section, click "Certificate in DER format" and click Next.
Save the file on your destop as burp.der
Open Firefox. At the top right, click the icon with three horizontal dashes.
Click Preferences.
In the "Find in Preferences" box, type certificates
Click the "View Certificates" button.
In Certificate Manager, click the Import... button, as shown below.
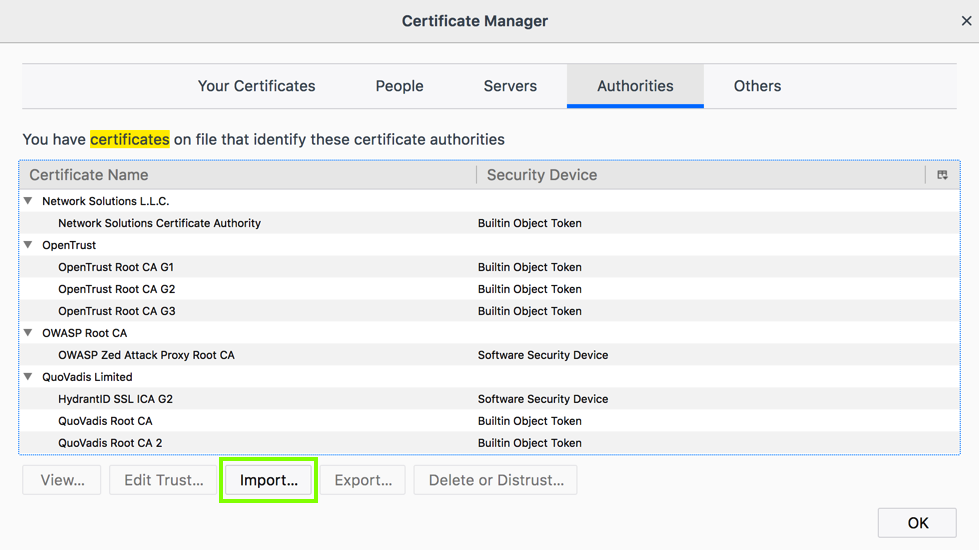
Navigate to your burp.der file and double-click it.
A box pops up, as shown below. Click "Trust this CA to identify websites" and click OK.
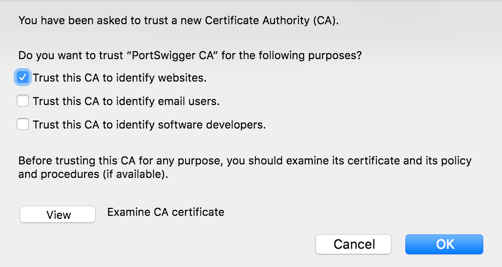
In the Certificate Manager box, click OK.
In the "Find in Preferences" box, type proxy
In the "Network Proxy" line, click the Settings... button.
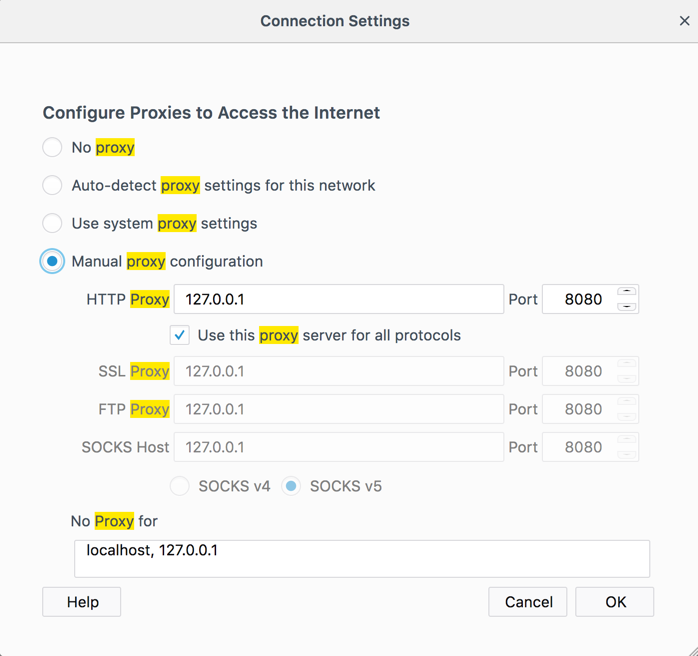
Configure Firefox to use 127.0.0.1 on port 8080 for all protocols, as shown below. Then click OK.
In Firefox, open https://samsclass.info/
The page should open.
In Burp, on the Proxy tab, click the "HTTP history" sub-tab.
You should see a GET request to https://samsclass.info/ as shown below.

At the top right, click the "Sign In" button.
Type in test210@mailinator.com and press Enter.
The next page says "There was a problem", as shown below.
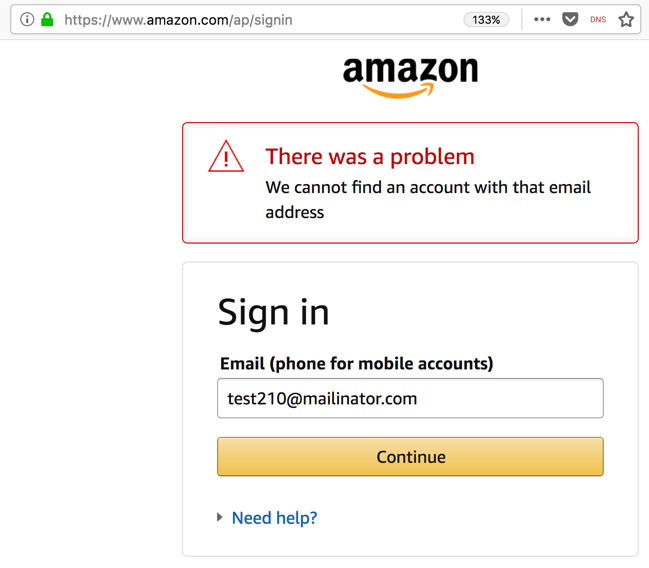
This sort of notification is unwise, because it permits username enumeration, as we will see below.
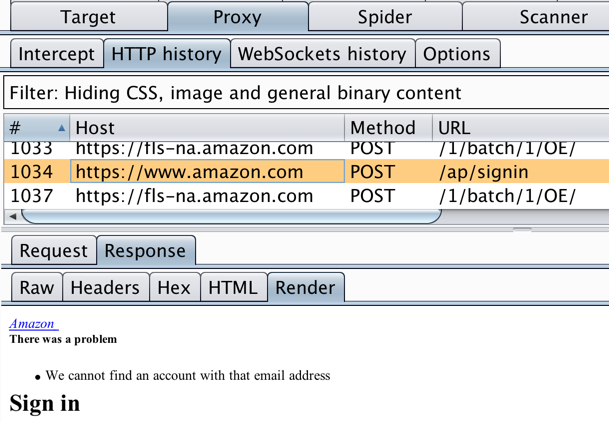
In Burp, scroll to the bottom of the "HTTP history" list and find the POST request to ap/signin, as shown below.
In the "HTTP history" list, click that POST request to highlight it. In the lower pane, click the Response tab and the Render sub-tab. You should see the "There was a problem" message, as shown below.
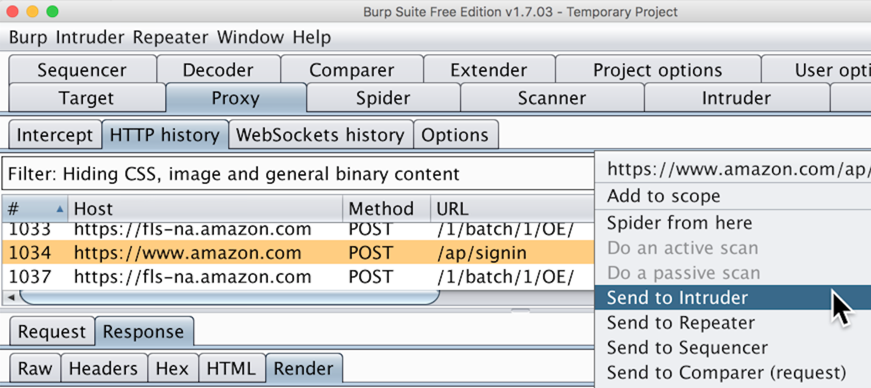
In Burp, click the Intruder tab. Click the Positions sub-tab.
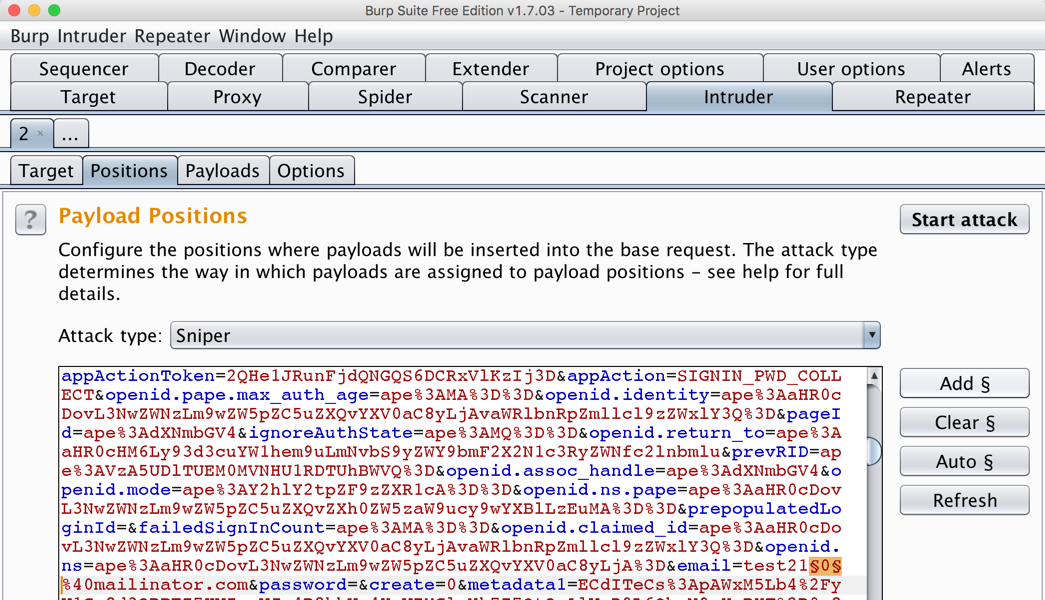
On the right side, click the "Clear §" button.
In Burp, in the lower pane, scroll down and find email=test210. Highlight the 0, as shown below.
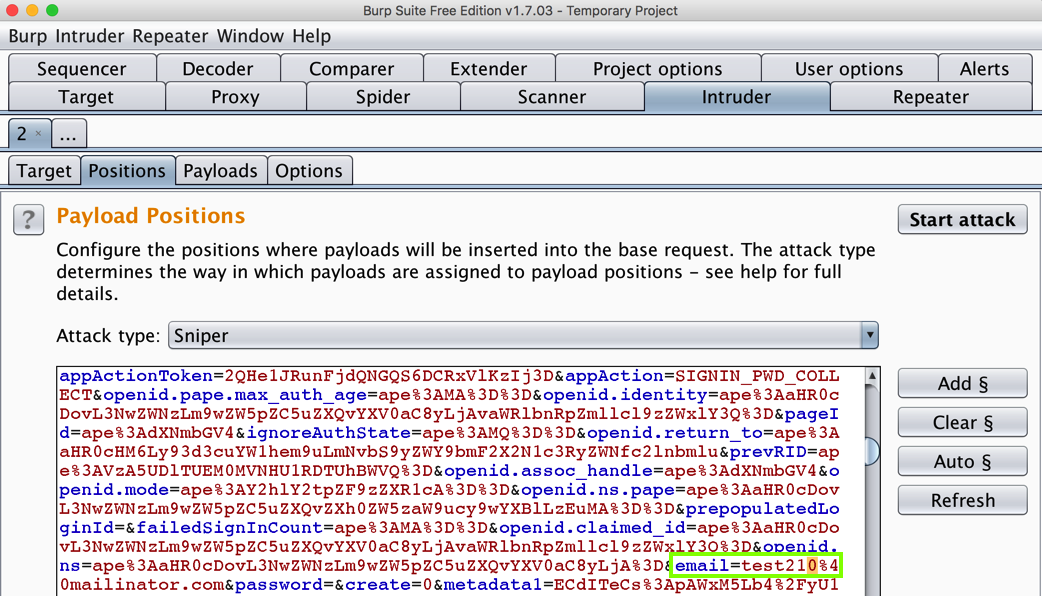
On the right side, click the "Add §" button.
Your Burp window should look like the image below.
Click the Payloads sub-tab.
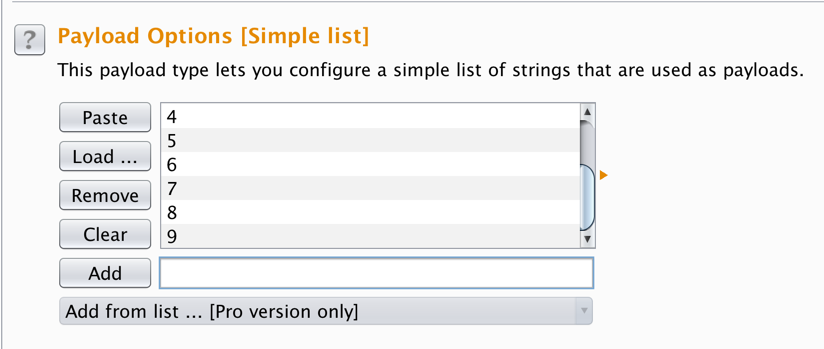
In the "Payload Options [Simple list]" section, in the field to the right of the Add button, type 0, as shown below.

Click the Add button.
Enter 1 and click the Add button again. Continue adding numbers up to 9, as shown below.
At the top right, click "Start attack".
Click OK.
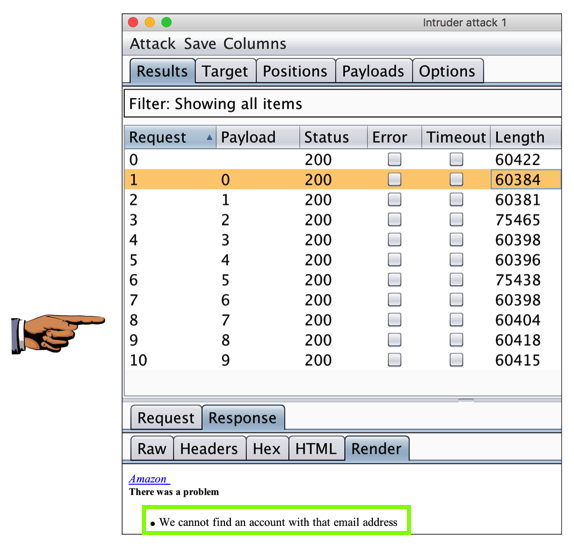
Burp makes ten requests. Some of them have responses with a length near 60,400 bytes, and others are near 75,000 bytes, as shown below.
In the list, click a line with a response length near 60,400 bytes. In the lower pane, click the Response tab and the Render sub-tab. You should see the message saying "We cannot find an account with that email address", as shown below.
Capture a whole-desktop image.
Save the image with the filename "Your Name Proj 10xa". Use your real name, not the literal text "Your Name".
YOU MUST SUBMIT AN IMAGE OF THE WHOLE DESKTOP TO GET FULL CREDIT!
Anyone who wants to hack Amazon accounts can exploit this weakness to test a long list of email addresses and find out which ones are use by Amazon customers. They can then send phishing emails to them, or just brute-force the passwords, as we will do below.
There are no other restrictions. I was able to create accounts with passwords from the THE TOP 25 MOST COMMON PASSWORDS, including these:
According to this source, "using the top 10 passwords, a hacker could, on average, guess 16 out of 1,000 passwords."123456 qwerty 111111 123123 666666 123456789 12345678 1234567890 1234567 password 987654321 qwertyuiop mynoob 654321 555555 google 123qwe 1q2w3e
If you use Amazon (and who doesn't?), you should protect yourself by choosing a long, complex password or two-step verification.
But users who don't bother to do that are sitting ducks.
samccsf00@mail.com
samccsf01@mail.com
samccsf02@mail.com
...
samccsf98@mail.com
samccsf99@mail.com
Warning
Please don't hit the Amazon servers with a lot of requests. You should not need to enumerate more than 100 accounts, and once you find the account, you shouldn't need to test more than 10 passwords.
Save the image with the filename "Your Name Proj 10xb". Use your real name, not the literal text "Your Name".
YOU MUST SUBMIT AN IMAGE OF THE WHOLE DESKTOP TO GET FULL CREDIT!