Amazon Password Vunerabilities
Executive Summary
Amazon's login process has three serious flaws, which expose their users to phishing attacks and account compromise:
1. Email Enumeration allows an attacker to discover valid emails for Amazon users
2. Weak Password Policy allow users to choose very simple, easily-guessed passwords
3. Cookie Re-Use makes an account compromise permanent--changing a password does not eject an intruder
The Amazon login process should be changed to remediate these vunerabilities, as detailed below.
1. Email Enumeration
The Amazon login page is shown below:
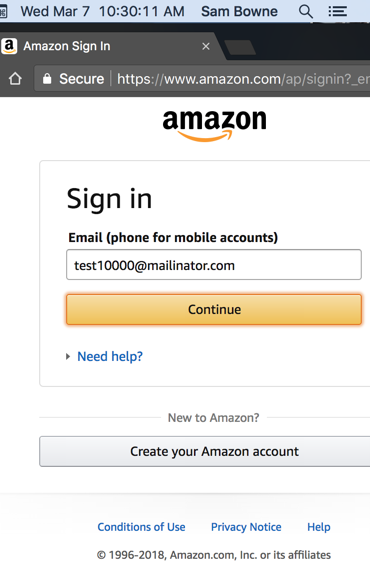
Submitting an invalid username leads to this page:
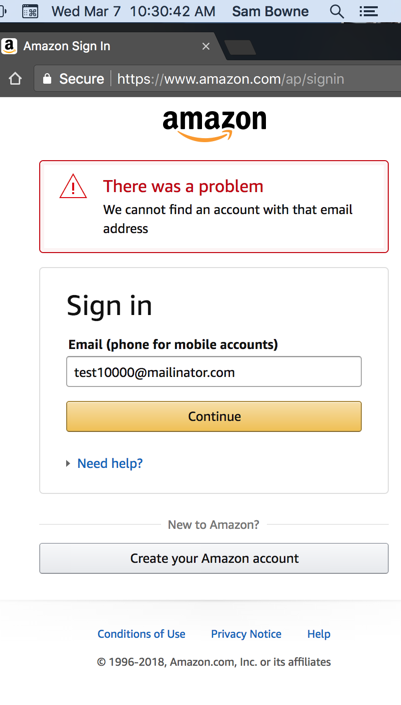
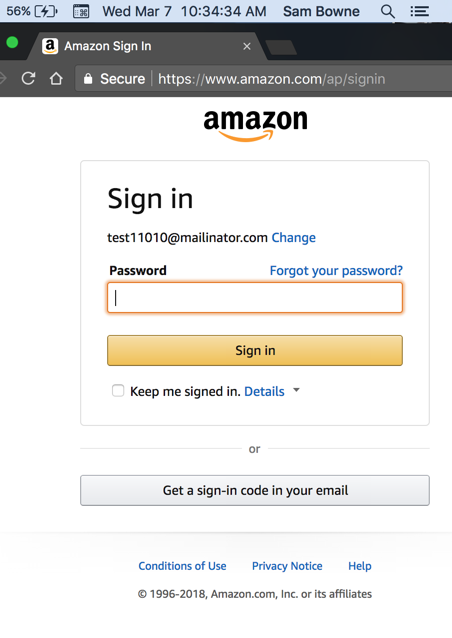
Submitting a valid username leads to this page:
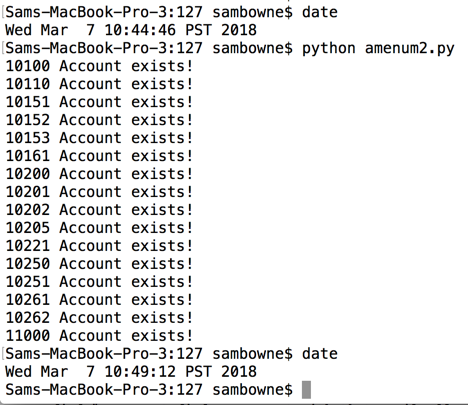
I wrote a
simple Python script
to search 1000 email addresses, and it
tested them all in less than five minutes,
as shown below.
Recommendation
The username and password should both be collected for every login, and lead only to a generic error message, not informing the user which value was incorrect. If that is regarded as too unfriendly, the username entry screen should require a CAPTCHA after some number of invalid usernames, such as five.
2. Weak Password Policy
The Amazon account creation page says
passwords must be "At least 6 characters",
as shown below.
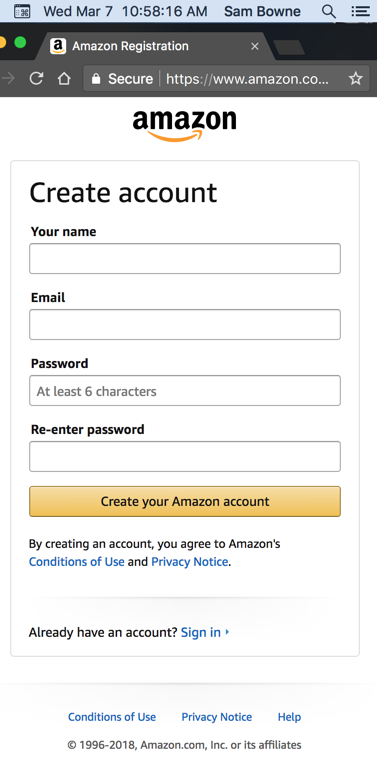
There are no other restrictions. I was able to create accounts with passwords from the
THE TOP 25 MOST COMMON PASSWORDS,
including these:
123456
qwerty
111111
123123
666666
123456789
12345678
1234567890
1234567
password
987654321
qwertyuiop
mynoob
654321
555555
google
123qwe
1q2w3e
According to
this source,
"using the top 10 passwords, a hacker could, on average, guess 16 out of 1,000 passwords."
Manually trying the top ten passwords in a browser
should succeed more than 1% of the time. If the attacker is very slow, and must solve CAPTCHAs, at least one guess per minute should be easily achievable. At that rate an attacker should be able to compromise one account every two hours, even without automating the process at all.
Recommendation
Passwords that are known to be compromised
should not be allowed. Existing accounts with
such simple passwords should be forced to
choose better passwords.
3. Cookie Re-Use
Once a user logs in, Amazon sends them an
authentication cookie. If the user logs out,
the old cookie remains valid. Even changing
the user's password does not invalidate the
old cookie. This means that once an account is compromised, the user has no way to eject the
intruder except to close the account entirely.
Details about cookie re-use are
here.
Recommendation
When a user logs out, the old cookie should
be rendered invalid on the server. When a
password is changed, all outstanding cookies should
be invalidated.
Posted 3-7-18 by Sam Bowne





