On an ARM Processor
wget https://go.dev/dl/go1.24.4.linux-arm64.tar.gz sudo tar -C /usr/local -xzf go1.24.4.linux-arm64.tar.gz
Then execute this command:
On an Intel (or AMD) Processor
wget https://go.dev/dl/go1.24.4.linux-amd64.tar.gz sudo tar -C /usr/local -xzf go1.24.4.linux-amd64.tar.gz
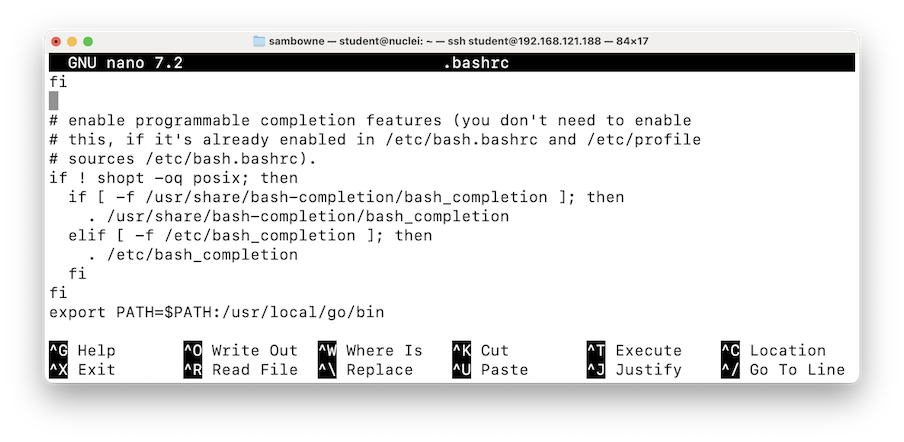
nano .bashrc
export PATH=$PATH:/usr/local/go/bin

Then execute these commands:
source .bashrc
go version
go install -v github.com/projectdiscovery/nuclei/v3/cmd/nuclei@latest
nano .bashrc
export PATH=$PATH:~/go/bin
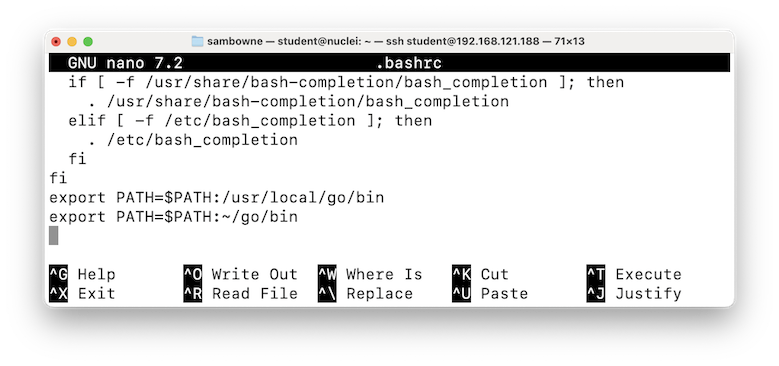
Then execute these commands:
source .bashrc
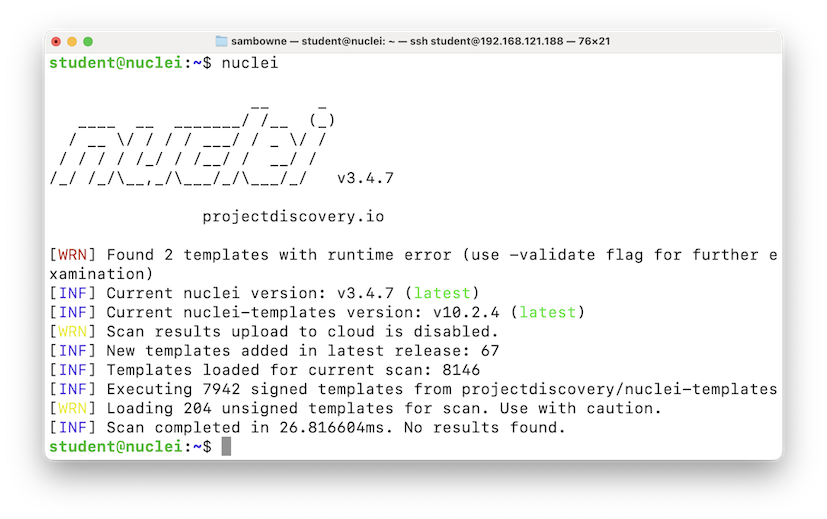
nuclei
On your Linux machine, execute these commands:
sudo apt update
sudo apt install docker.io -y
sudo apt install docker-compose -y
sudo usermod -aG docker $USER
newgrp docker
sudo reboot
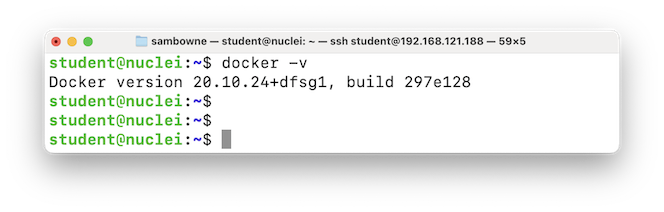
docker -v
On your Linux machine, execute these commands:
sudo apt install git -y
git clone https://github.com/projectdiscovery/nuclei-templates-labs.git
cd nuclei-templates-labs
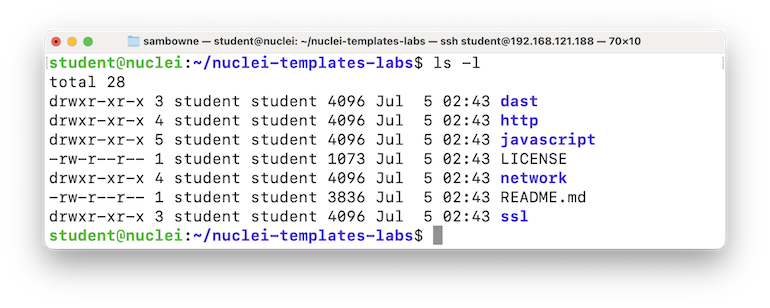
ls -l
cd http/cves/2025/CVE-2025-31161
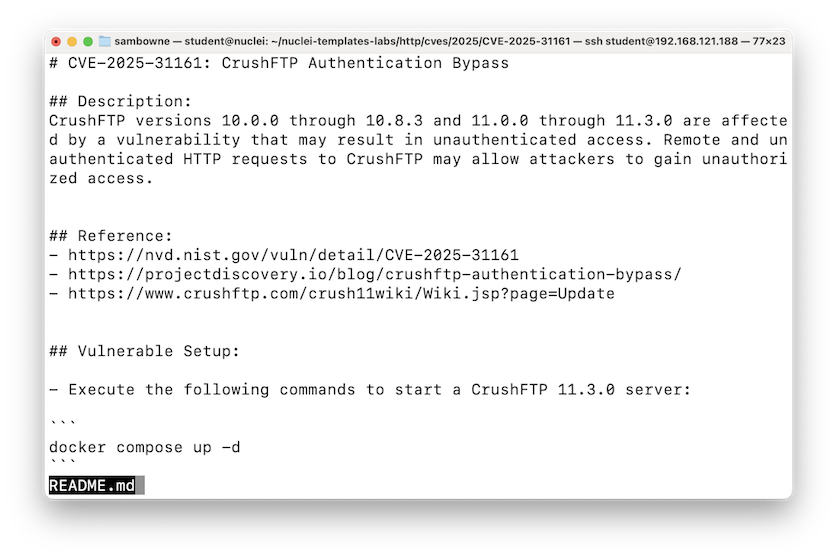
less README.md
To start the server, execute this command:
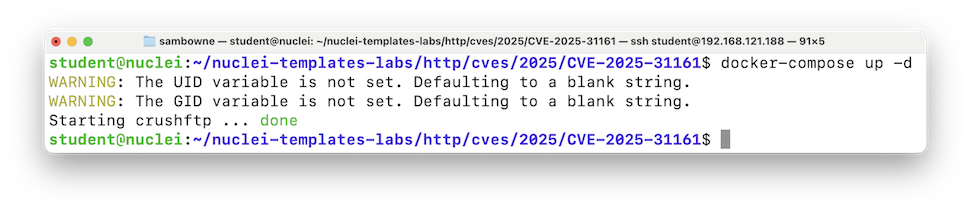
docker-compose up -d
sudo ss -pntl
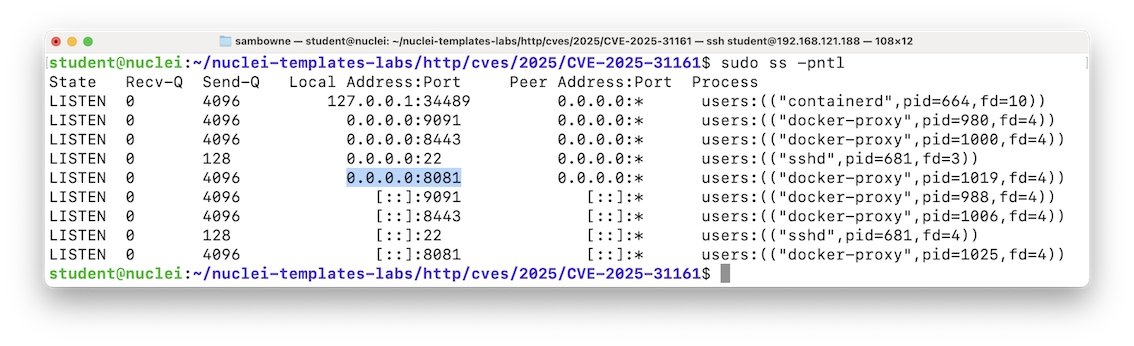
Then, in a Web browser on your host system, open this URL, replacing the IP address with the correct address of your Linux machine:
http://192.168.121.188:8081/WebInterface/login.htmlYou see a CrushFTP login page, as shown below.

Flag 312.1: Scanning the Vulnerable Server with Nuclei (15 pts)
On your Linux machine, execute the commands below.The "-es info,low" switch tells Nuclei not to bother with unimportant findings.
Nuclei runs thousands of tests very quickly.
The flag is covered by a green rectangle in the image below.
docker ps
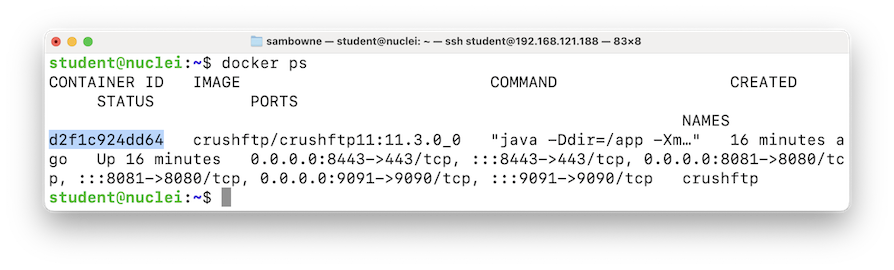
docker stop d2f1c924dd64
docker rm d2f1c924dd64
(Note that the README.md file has an incorrect command to start the container.)
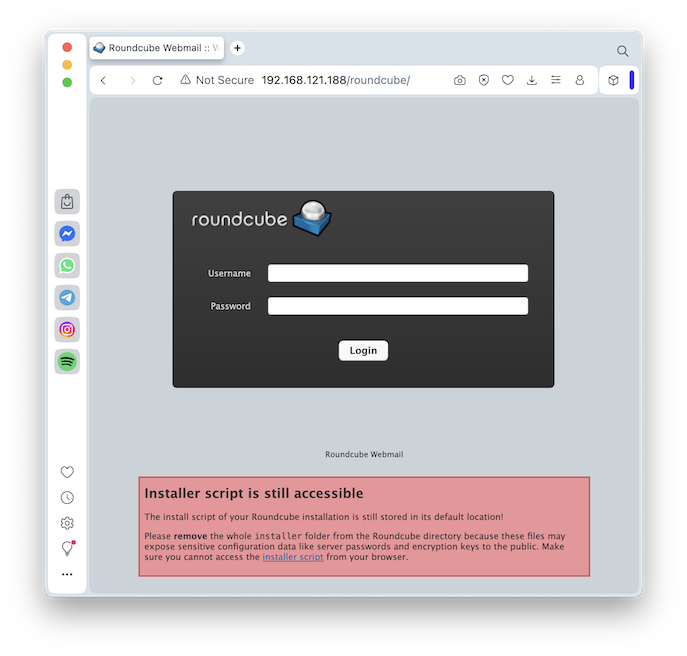
View the Web page, as shown below.
Flag 312.2: Scan the RoundCube Server (10 pts extra)
Scan the server, as you did above.The flag is covered by a green rectangle in the image below.
Delete the server when you are done with it.
Flag 312.3: Deprecated TLS (10 pts extra)
Use this container:~/nuclei-templates-labs/ssl/deprecated-tlsFollow the README file. You need to create a directory and a SSL certificate.You don't need to write a template.
Scan the server. Don't exclude info results.
The flag is covered by a green rectangle in the image below.
Delete the server when you are done with it.
Flag 312.4: Default Login (10 pts extra)
Use this container:~/nuclei-templates-labs/javascript/default-logins/postgres-default-loginsFollow the README file.You don't need to write a template.
Scan the server.
The flag is covered by a green rectangle in the image below.
Delete the server when you are done with it.
Learn Nuclei in 30 minutes - DEF CON Nuclei Demo
Posted 7-5-25