This is the #6 most important security flaw in mobile apps, according to OWASP.
So to make the project easier, we'll use the old app from January.
In the extra-credit portion, you can prove that the modern version of the app still has the same flaw.
Download this APK file:
Drag it and drop it onto your Genymotion phone to install it.
The Staples app launches, as shown below.

The Account page opens, as shown below.
Click "CREATE YOUR STAPLES ACCOUNT".
Fill in any email address and password, as shown below. Click the "CREATE ACCOUNT" button.
If your password is too simple, you may need to change it. I found that P@ssw0rd worked.
The Account page now shows that you are logged in, as shown below.
Here are common examples of SDK paths:
NOTE: If you are using Windows, remove the "./" before "adb".
cd ~/Library/Android/sdk/platform-tools
./adb shell
cd /data/data/app.staples
grep -r Password .
exit
If a password must be stored locally, it should be stored in the Android Keystore, as explained here:
Where is the best place to store a password in your Android app
The password can be recovered from the local store for this app, as detailed below.
One common error in cryptography is using ECB (Electronic Code Book) mode. In ECB, each block of cleartext encodes to a block of ciphertext without adding any varying "nonce" to it. This means that input with two identical blocks of cleartext will encode to identical ciphertext blocks.
At the top of the "Account" page, click Preferences.
In the Preferences screen, click the "Sign out" button, as shown below.
In your virtual phone, at the top left, click the little head icon.
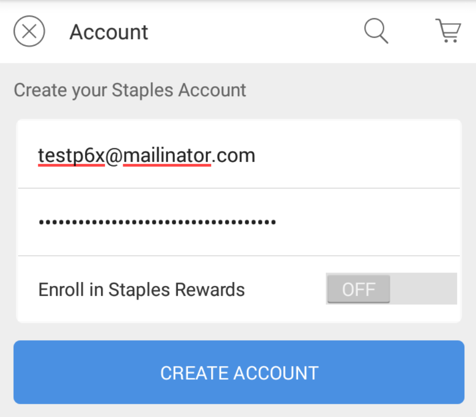
In the Account page, click "CREATE YOUR STAPLES ACCOUNT".
Fill in any email address, and use this password, which is 32 "x" characters followed by "123A".
xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx123A
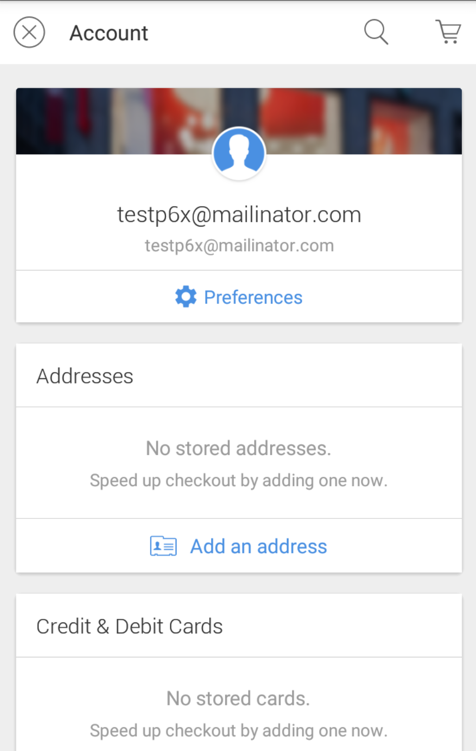
The Account page opens, showing your new email address at the top, as shown below.
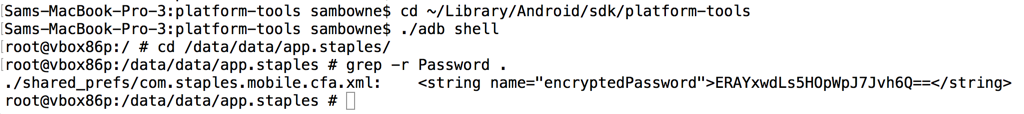
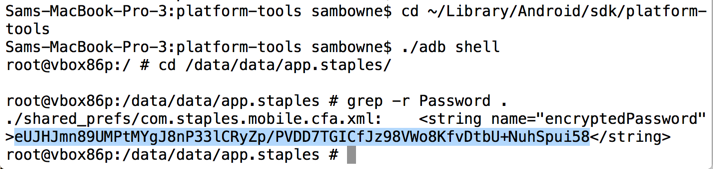
From that directory, open a shell on the Android device, as shown below.
NOTE: If you are using Windows, remove the "./" before "adb".
cd ~/Library/Android/sdk/platform-tools
./adb shell
cd /data/data/app.staples
grep -r Password .
exit
Highlight the Base64 blob, as shown below, right-click it, and copy it into the clipboard.
http://tomeko.net/online_tools/base64.php?lang=en
In the "Base64 string" field, paste in the blob you copied from the Android device.
Click the Convert button to decode this blob to a hexadecimal string, as shown below.
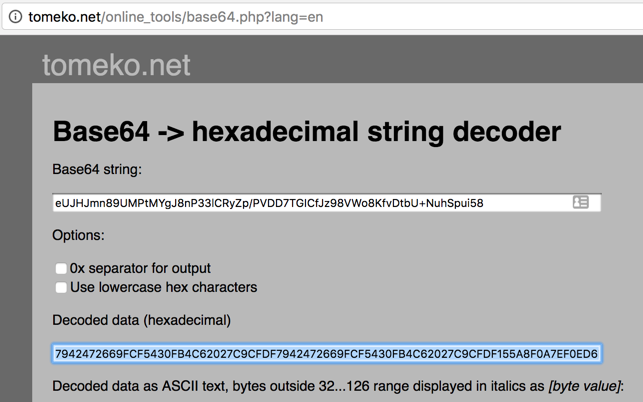
Highlight the "Decoded data (hexadecimal)" field and copy it to the clipboard.
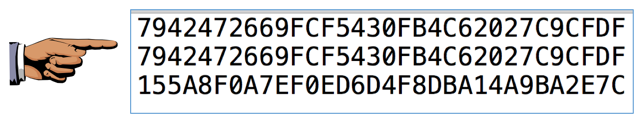
Paste it into a text editor so you can examine it.
Resize the text editor to prove that the first 32 characters are repeated, as shown below.
Save a full-desktop image. On a Mac, press Commmand+3. On a PC, press Shift+PrntScrn and paste into Paint.
YOU MUST SUBMIT A FULL-SCREEN IMAGE FOR FULL CREDIT!
Save the image with the filename "YOUR NAME Proj 6xa", replacing "YOUR NAME" with your real name.
To find out, we'll examine the source code.
https://connortumbleson.com/2017/01/23/apktool-v2-2-2-released/
Save the file in the same folder you used for the Staples APK file you downloaded previously, such as Downloads.
Open a Command Prompt or Terminal.
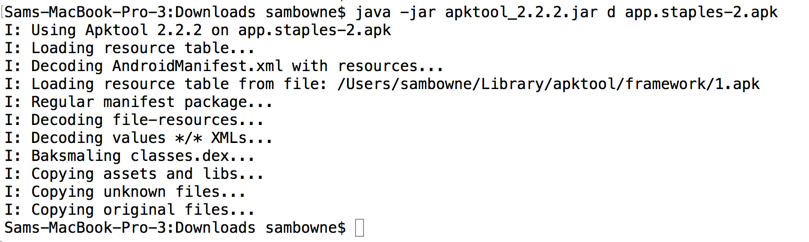
Change directory to the location you placed the downloaded file and open it with java, as shown below.
cd Downloads
java -jar apktool_2.2.2.jar d app.staples-2.apk
cd app.staples-2
grep -r encryptedPassword .
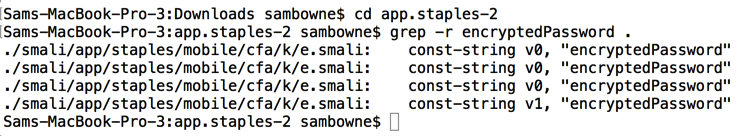
Find the code shown below and notice these features:
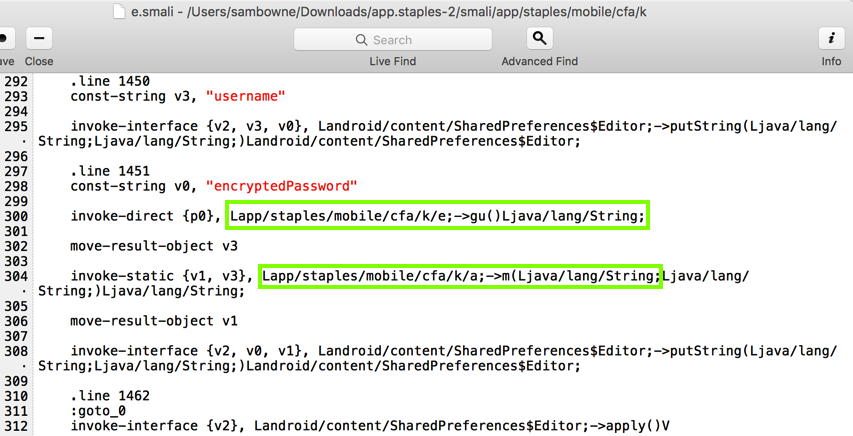
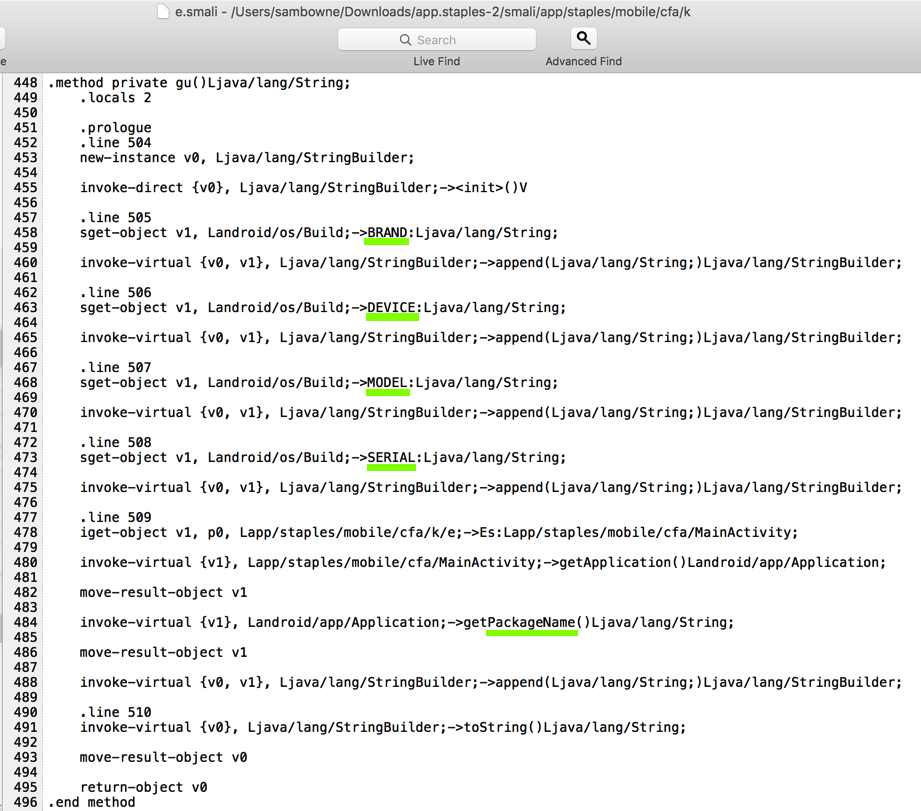
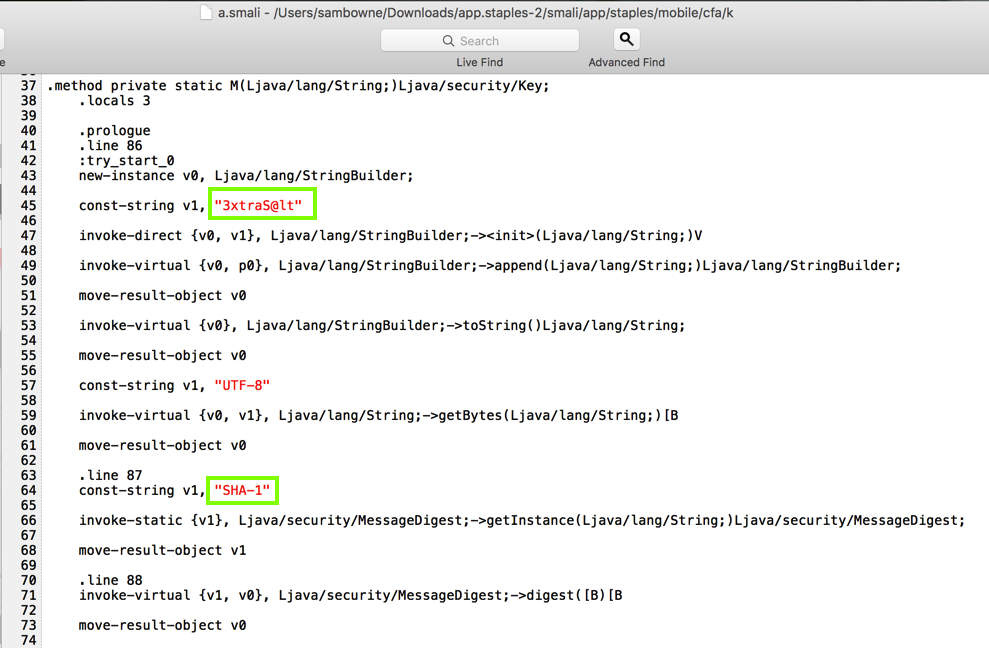
This code simply finds five strings and appends them together. Here are the five strings it uses, as shown below.
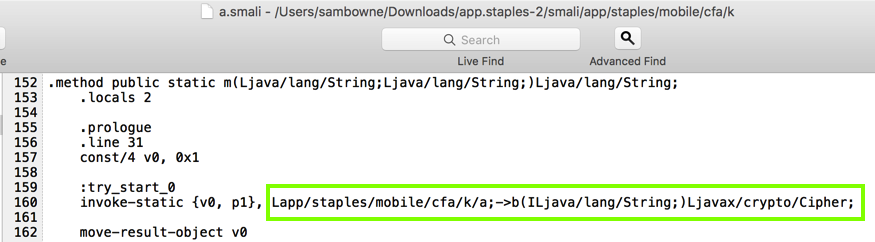
This function calls the Lapp/staples/mobile/cfa/k/a;->b() function, as shown below.
Notice these two features, as shown below.
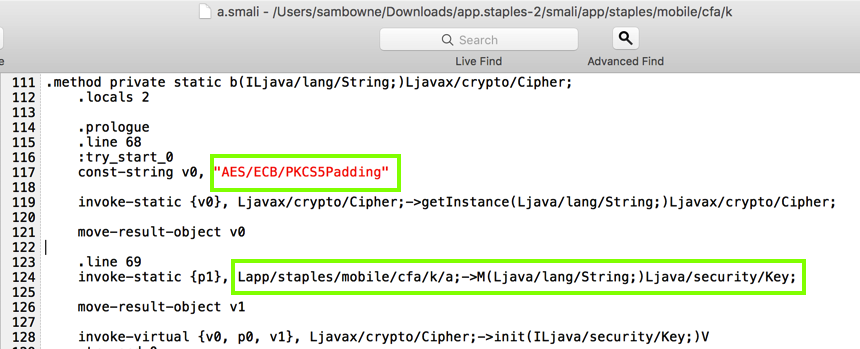
Notice these two features, as shown below.
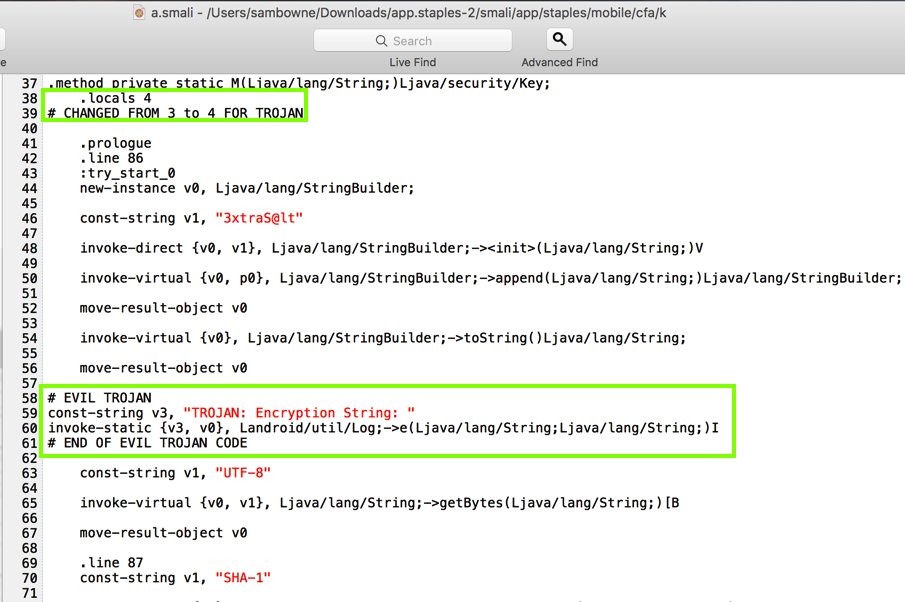
First, change ".locals 3" to ".locals 4"
Then insert these lines before the 'const-string v1, "UTF-8"' line:
# EVIL TROJAN
const-string v3, "TROJAN: Encryption String: "
invoke-static {v3, v0}, Landroid/util/Log;->e(Ljava/lang/String;Ljava/lang/String;)I
# END OF EVIL TROJAN CODE
java -jar ../apktool_2.2.2.jar b .
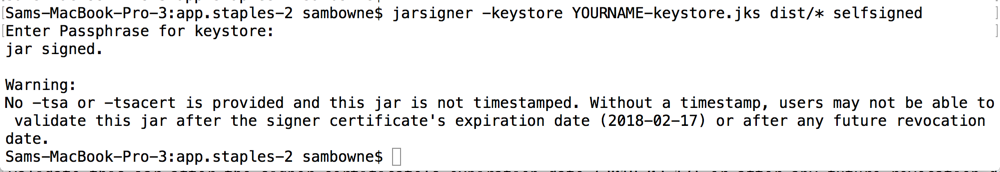
keytool -genkey -keyalg RSA -alias selfsigned -keystore YOURNAME-keystore.jks -storepass password -validity 360 -keysize 2048
jarsigner -keystore YOURNAME-keystore.jks dist/* selfsigned
Tap the circle at the bottom center.
Tap Settings.
Tap Apps.
Tap Staples.
Tap Uninstall.
Tap OK
cd ~/Library/Android/sdk/platform-tools
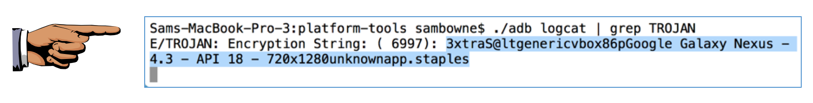
./adb logcat | grep TROJAN
In the Staples app, log in or create a new account
The log shows the encryption string, as shown below.
Highlight the entire string and copy it to the Clipboard.
Save a full-desktop image. On a Mac, press Commmand+3. On a PC, press Shift+PrntScrn and paste into Paint.
YOU MUST SUBMIT A FULL-SCREEN IMAGE FOR FULL CREDIT!
Save the image with the filename "YOUR NAME Proj 6xb", replacing "YOUR NAME" with your real name.
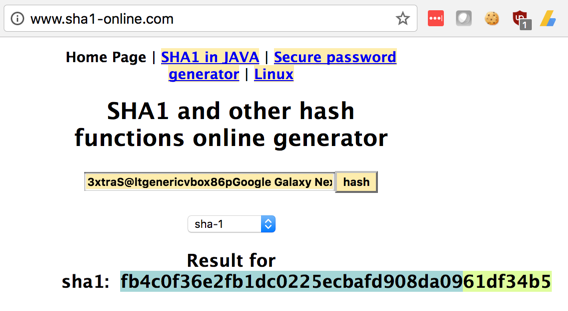
Paste in the encryption string, as shown below.
Click the hash button.
The SHA-1 hash appears, as shown below. This hash is 160 bits long, but an AES key is only 128 bits long.
Carefully highlight the first portion of the hash, omitting the last 8 hexadecimal characters, as shown below, and copy that to the Clipboard.
http://aes.online-domain-tools.com/
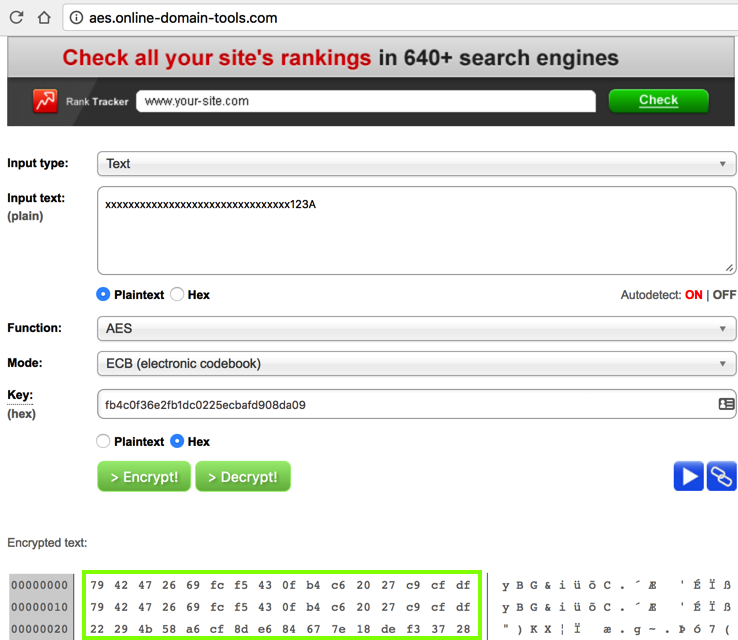
In the "Input text" field, enter your password of
xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx123A
Below the Key field, click the Hex box.
Click the Encrypt button. The encrypted text at the bottom shows the hexadecimal values of the encrypted text, as shown below.
To get extra credit, use the information below to hack into my account and steal my stored credit card number. You'll only get the type of card and the last 4 digits. Send in an image with the correct credit card information to get credit.
I used the latest version of the Staples app, on a much more modern device running Android 7.0.0, to generate this data. The fact that the same process works proves that Staples has not changed their encryption method at all.
<?xml version='1.0' encoding='utf-8' standalone='yes' ?>
<map>
<long name="locationTimestamp" value="0" />
<string name="wcToken">2191966755%2Col7HhTWcNrvTx8c2sB%2Fd3G5sBjKxGQBUiKImRY2dkkfSQ2ZrrOz21VbMrzpeZODRi4PfDicLaqAoyeyWpFZawQiaU8s4O90PUdlD6HtFd%2B%2B3%2FChSYygb4LQEUSTJkAW2rcI0C6a9R2glIjypffeM5kmPHTZjBz%2FcHqi9NavHhuyM3M%2B%2Bj4Wyco78w7CKrSH87yQfeMp8WrOqCr42dOHw5g%3D%3D</string>
<string name="postalCode">01702</string>
<string name="username">proj6x@mailinator.com</string>
<float name="locationLongitude" value="-71.4889" />
<boolean name="preferredLocationFlag" value="true" />
<float name="locationLatitude" value="42.291313" />
<string name="encryptedPassword">YHjpLAbxAgCMaIHKouN0pc1yis5dbNSwqlA9+cwAYww=</string>
<string name="wcTrustedToken">2191966755%2CFXIocQ9oyLIotOVQH2rnWaTz6kw%3D</string>
<string name="locationProvider">Default</string>
</map>
Sams-MacBook-Pro-3:platform-tools sambowne$ ./adb shell
vbox86p:/ # getprop ro.product.brand
Android
vbox86p:/ # getprop ro.product.device
vbox86p
vbox86p:/ # getprop ro.product.model
Google Nexus 9 - 7.0.0 - API 24 - 1536x2048
vbox86p:/ # getprop ro.product.serial
vbox86p:/ # exit
Sams-MacBook-Pro-3:platform-tools sambowne$