This is such a serious security flaw that the FTC punished Fandango and Credit Karma for doing the same thing in 2014.
From the Android home screen, click the circle at the bottom center.
Open Settings.
In Settings, click "Network & internet".
Click Wi-Fi.
Click AndroidWiFi.
Click Advanced.
In the "Network details" screen, at the top right, click the Pencil icon.
In the "Proxy" field, click the down-arrow.
Click None.
Then click Save.
Install the "Harvard Health Info" app, as shown below.

Click Wi-Fi.
Click AndroidWiFi.
Click Advanced.
In the "Network details" screen, at the top right, click the Pencil icon, outlined in green in the image below.
In the "AndroidWifi" box, in the "Advanced options" row, click the down-arrow.
In the "Proxy" field, click the down-arrow.
Click Manual, which is outlined in green in the image below.
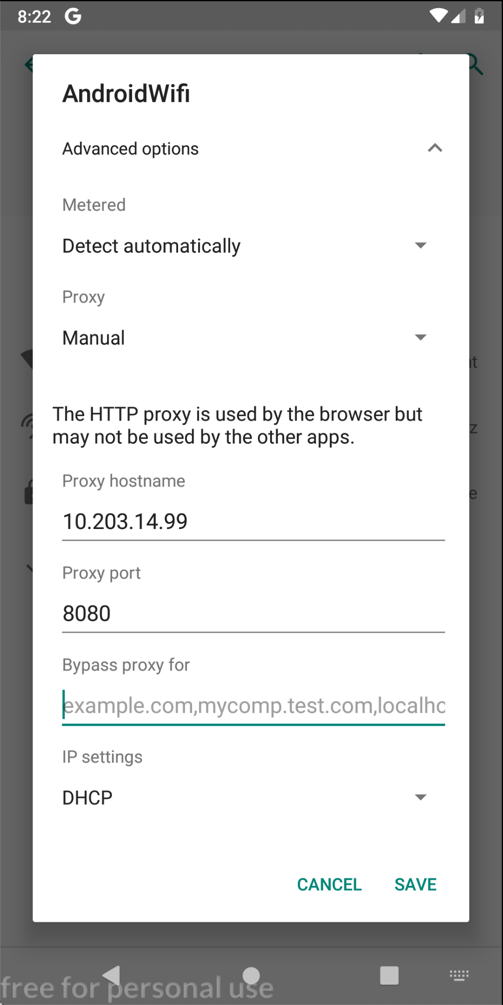
Enter the IP address and port number of the Burp proxy listener, as shown below.
On your Android device, click SAVE.
At the bottom center of the device, click the round Home button.
Click "Sign in" and enter test credentials, as shown below.
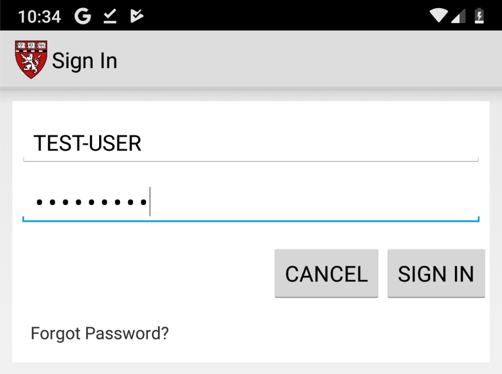
Click "SIGN IN".
In Burp, on the Proxy tab, click the "HTTP Requests" sub-tab.
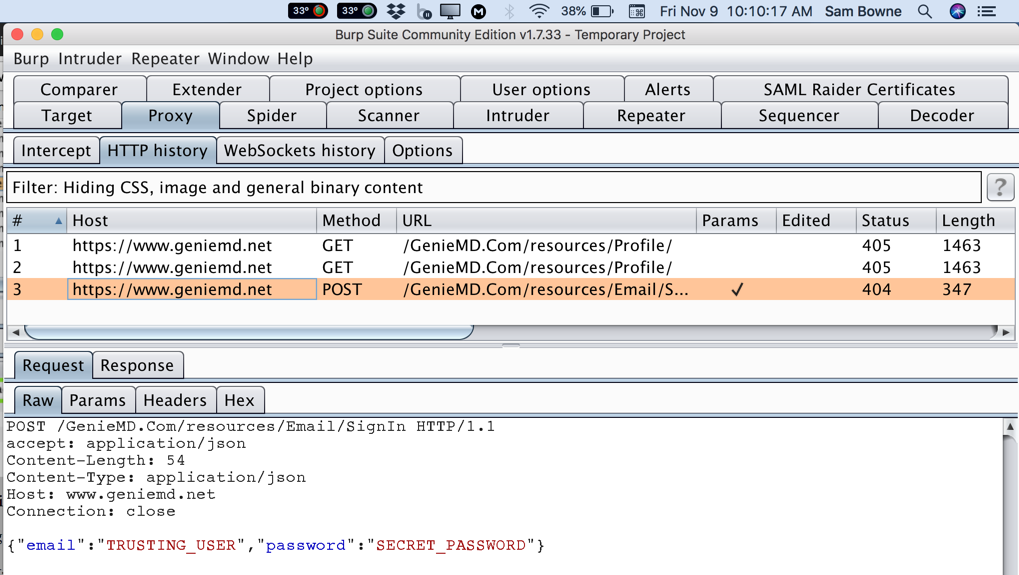
Find the POST method going to /GenieMD.Com/resources/Email/SignIn.
The username and password appear in Burp, as shown below:
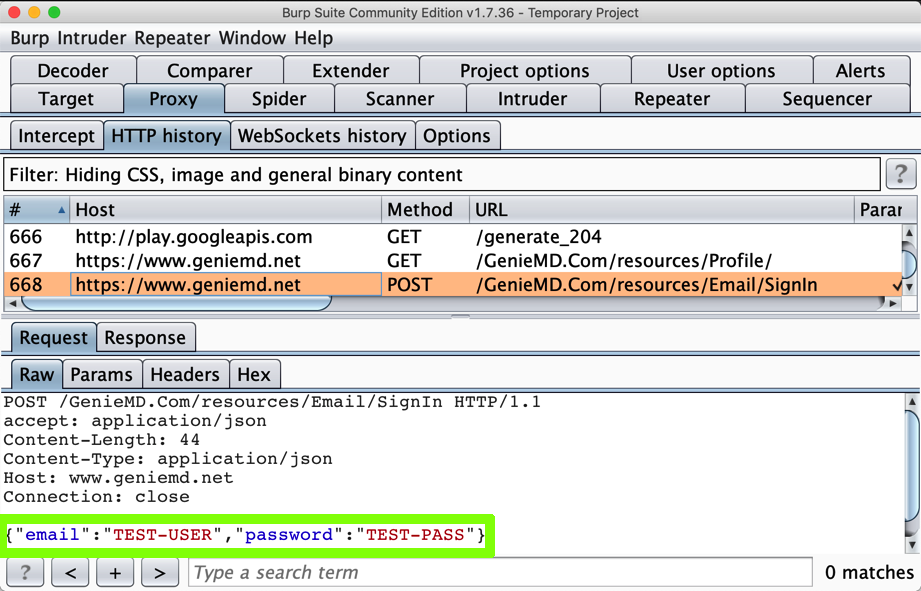
If you have been doing these projects in order, this is not a security problem, because you have the PortSwigger certificate installed--your Android device has been told to trust Burp.
In Burp, on the Proxy tab, on the "HTTP history" sub-tab, right-click any entry and click "Clear history". Click Yes.
Click OK.
Enter your PIN.
You should see an error message, as shown below.
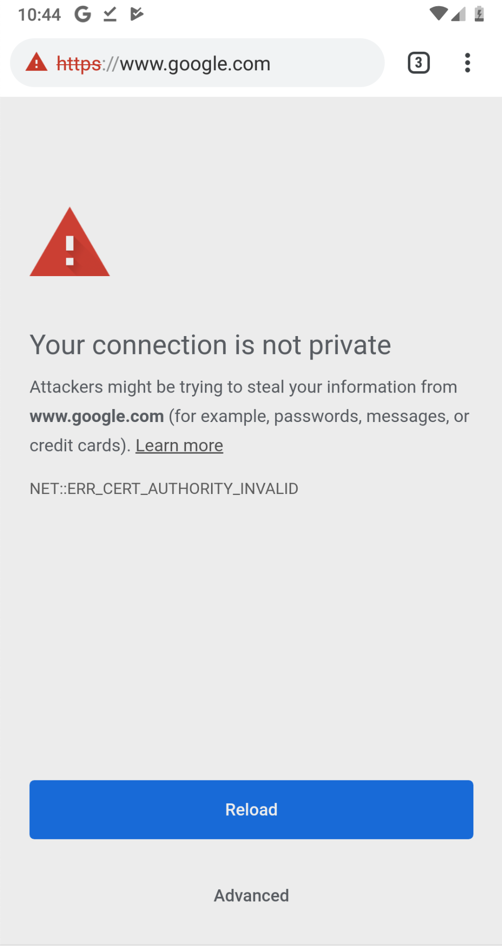
No valid HTTPS connections can be made from your device now, because it no longer trusts Burp.
Click "Sign in" and enter test credentials, including your name, as shown below.
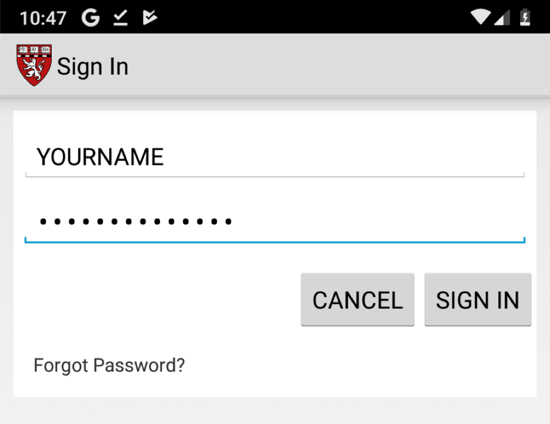
Find the POST method going to /GenieMD.Com/resources/Email/SignIn.
The username and password still appear in Burp, as shown below:
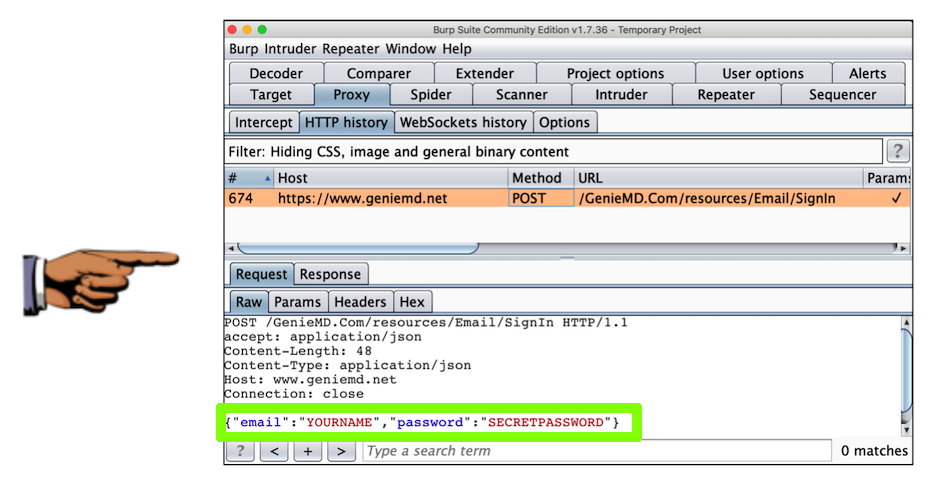
This is a big problem--the MITM attack is allowed. GenieMD exposes its users to this attack, because they don't bother to validate SSL certificates.
Save a full-desktop image. On a Mac, press Shift+Commmand+3. On a PC, press Shift+PrntScrn and paste into Paint.
YOU MUST SUBMIT A FULL-SCREEN IMAGE FOR FULL CREDIT!
Save the image with the filename "YOUR NAME Proj 4", replacing "YOUR NAME" with your real name.
I re-tested the app in 2015 and it was still vulnerable. I notified the vendor again and they replied on Twitter, saying that they are not legally required to use SSL properly under HIPAA. I tested the newest version, 5.9.9.54, updated October 26, 2016, on December 21, 2016. It's still vulnerable. GenieMD clearly doesn't care at all.


They both still have this flaw, as shown below.