Popular Android Apps with SSL Certificate Validation Failure
Vulnerable Android Apps |
| App | Vulnerability |
| PicsArt (100 Million Downloads) | SSL MITM; still vulnerable 5-23-15 |
| ASTRO File Manager with Cloud (50 Million Downloads) | SSL MITM |
| ES File Explorer File Manager (100 Million Downloads) | SSL MITM |
| CityShop - for Craigslist (10 Million Downloads) | SSL MITM |
| Truecaller - Caller ID & Block (50 Million Downloads) | Plaintext PII Transmission |
| Instachat (5 Million Downloads) | SSL MITM; still vulnerable 5-23-15 |
| Phone for Google Voice & GTalk (1 Million Downloads) | SSL MITM |
| OkCupid (5 Million Downloads) | SSL MITM; fixed as of 5-23-15 |
| Safeway (1 Million Downloads) | SSL MITM |
| DISH Anywhere (5 Million Downloads) | SSL MITM |
| SomNote (1 Million Downloads) | SSL MITM, but hashing reduces the harm |
| Supermovil Santander Mexico (500,000 Downloads) | SSL MITM |
| Minha Conta (Santander Brazil) (1 Million Downloads) | SSL MITM |
| State Bank Anywhere (1 Million Downloads) | SSL MITM |
| Snap Secure (100,000 Downloads)
| SSL MITM FIXED 4-30-15 |
| AMC Security (5 Million Downloads) | SSL MITM |
| Amway (100,000 Downloads) | SSL MITM |
| Ask (1 Million Downloads) | SSL MITM |
| Band (10 Million Downloads) | SSL MITM |
| Club Personal (1 Million Downloads) | SSL MITM |
| DailyFinance from AOL (100,000 Downloads) | SSL MITM |
| DMV NOW (California DMV) (500,000 Downloads) | SSL MITM |
| Equifax (100,000 Downloads) | SSL MITM |
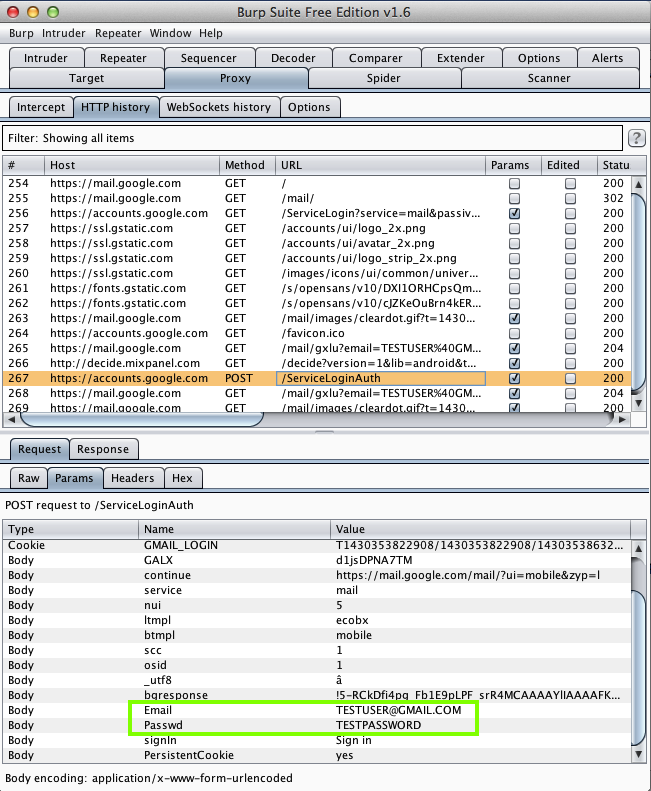
| Floating Browser (100,000 Downloads) | SSL MITM; exposes all credentials entered into the browser |
| Foxit MobilePDF - PDF reader (1 Million Downloads) | SSL MITM; exposes DropBox, Box, Microsoft, and Google credentials (fixed 5-18-15) |
| GittiGidiyor (eBay) (1 Million Downloads) | SSL MITM |
| IM+ (100,000 Downloads) | SSL MITM; exposes Google credentials |
| InstaG (1 Million Downloads) | SSL MITM |
| InstaMessage (1 Million Downloads) | SSL MITM |
| KickSend (500,000 Downloads) | SSL MITM |
| Kid Mode (1 Million Downloads) | SSL MITM |
| Lyoness (100,000 Downloads) | SSL MITM |
| Mini Online Shopping (1 Million Downloads) | SSL MITM; password hashed |
| NBA (5 Million Downloads) | SSL MITM |
| InstaPost (1 Million Downloads) | SSL MITM |
| Pizza Hut (5 Million Downloads) | SSL MITM |
Vulnerable Medical Android Apps
HIPAA Requirements

In my opinion, all the apps below fail to comply with HIPAA
|
| EyeXam (5000 Downloads) | SSL MITM |
| Garland & Associates (10 Downloads) | SSL MITM |
GenieMD (10,000 Downloads)
UPDATED with Vendor Response | SSL MITM |
| Liver Health - Hepatitis C (500 Downloads) | SSL MITM |
| LowestMed Corporate Rx (1000 Downloads) | SSL MITM |
| Order Mvi (50 Downloads) | SSL MITM |
| Pain Timer (50 Downloads) | SSL MITM |
| Pharmacy Health Connect (1000 Downloads) | SSL MITM |
| Pulsara (100 Downloads) | SSL MITM |
| RCEMS Field Guide (1000 Downloads) | SSL MITM |
| RCP Sacramento (500 Downloads) | SSL MITM |
| Rx Refills (1000 Downloads) | SSL MITM |
| T-Res Fast Clinical Logging (1000 Downloads) | SSL MITM |
| UCLA eIBD (100 Downloads) | SSL MITM |
| UCLA Health (1000 Downloads) | SSL MITM |
| Virtual Physician's Network (1 Download) | Plaintext HTTP authentication |
Background
CERT tested many Android apps in 2014,
and notified the authors of SSL certificate
validation vulnerabilities.
I found that "snap secure" was still vulnerable
to a trivial MITM attack, and wrote
a
homework project for my students.
I decided to test more apps on the CERT list,
just to see what I could find.
Here are details of the CERT test and
notification, from
9/3/2014:
Finding Android SSL Vulnerabilities with CERT Tapioca.
This spreadsheet from CERT,
shows "Android App SSL Failures":
Android apps that fail to validate SSL
Testing Method
I have Burp set up as a proxy for my
Genymotion Android emulator, without
the PortSwigger certificate installed,
so secure sites give a warning in
the default Web browser:
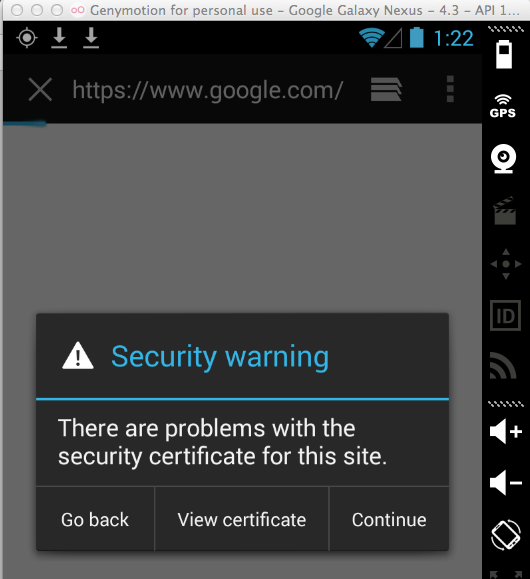
So no HTTPS connections should be
possible through the proxy.
PicsArt (100 Million Downloads)
Here's the app:

CERT notified the author about the
SSL vulnerability on 8-27-14, and
the app was updated on 3-13-15,
but it's still vulnerable.
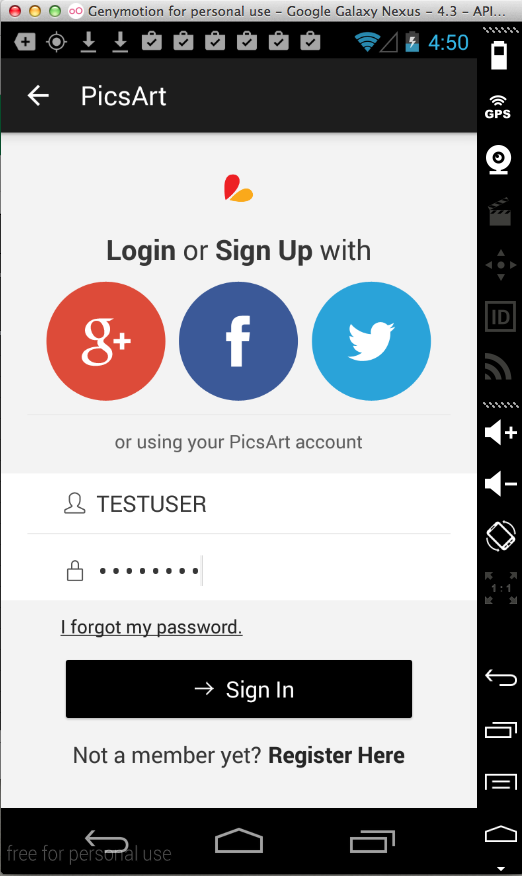
Sending test credentials:
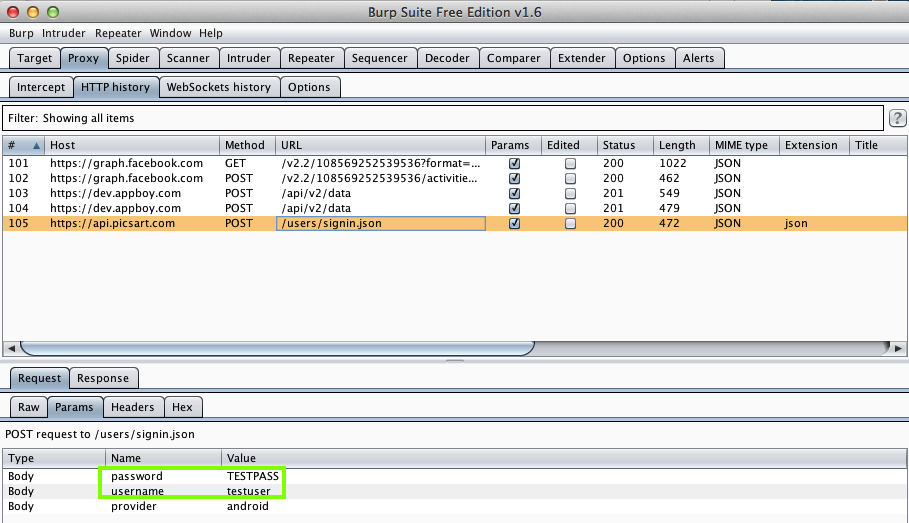
Harvesting them from Burp via MITM attack:
ASTRO File Manager with Cloud (50 Million Downloads)
Here's the app:

CERT notified the author about the
SSL vulnerability on 9-11-14, and
the app was updated on 4-24-15,
but it's still vulnerable.
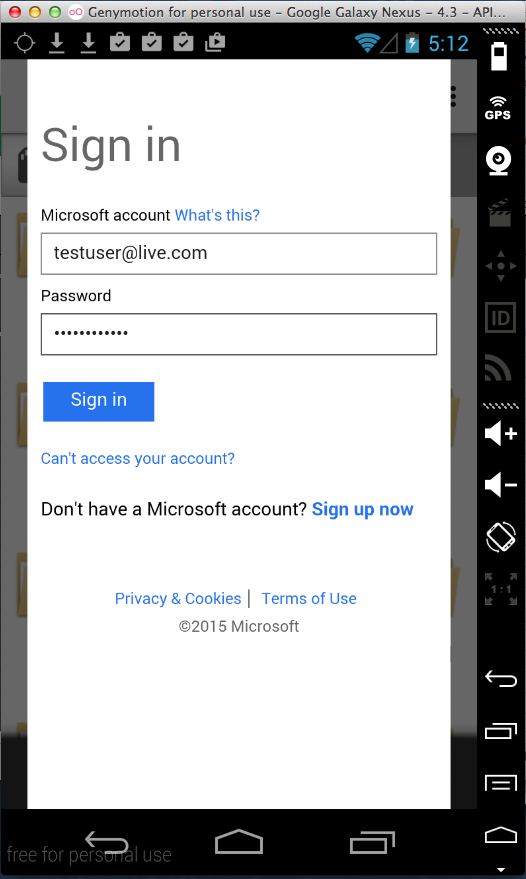
Sending test credentials to connect a
Microsoft OneDrive account:
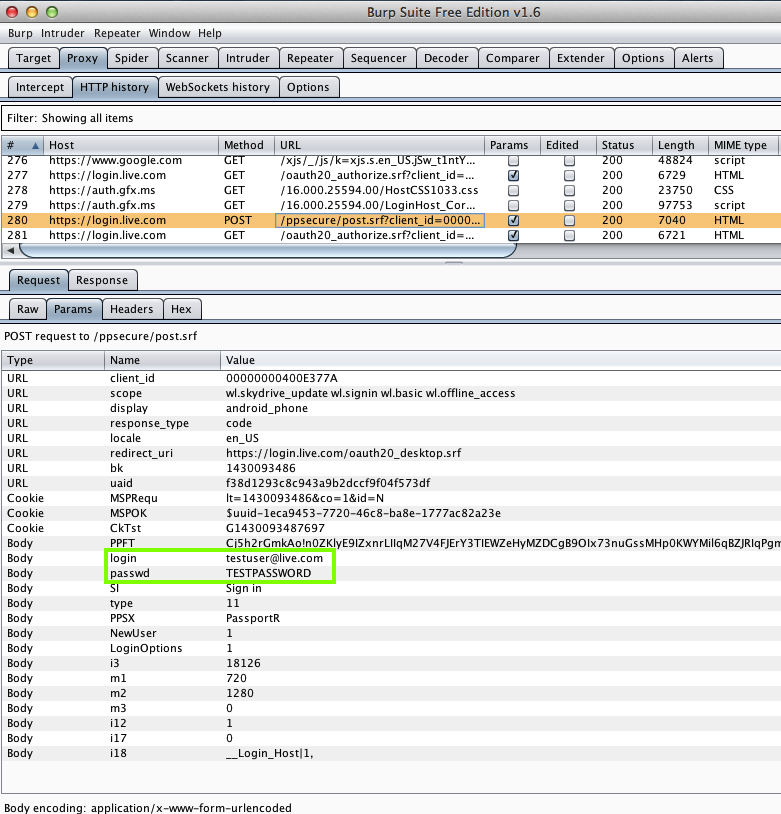
Harvesting them from Burp via MITM attack:
ES File Explorer File Manager (100 Million Downloads)
Here's the app:

The app was updated on 4-16-15,
but it's still vulnerable.
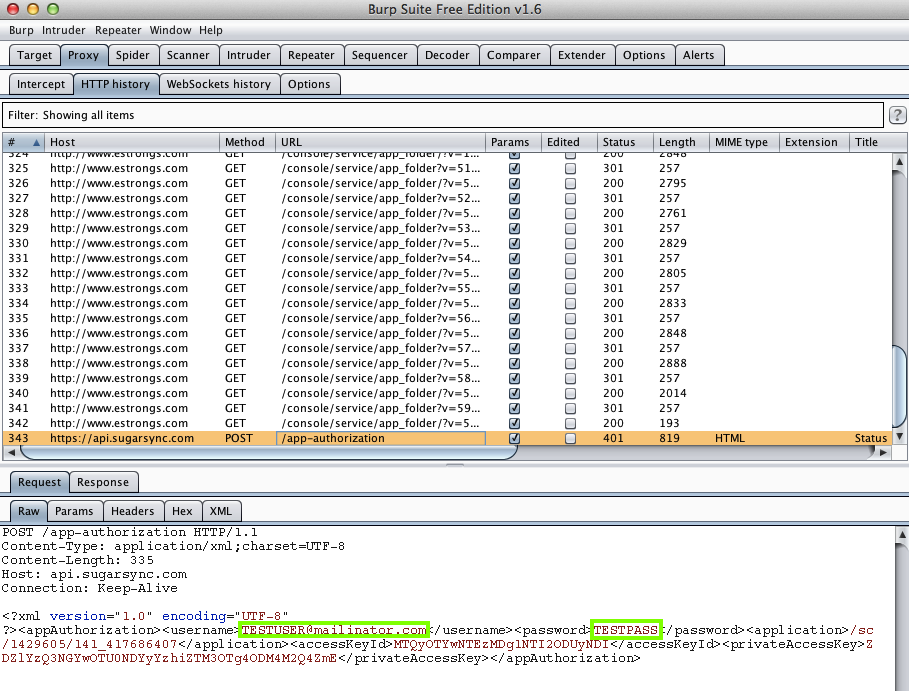
Sending test credentials to connect a
SugarSync account:
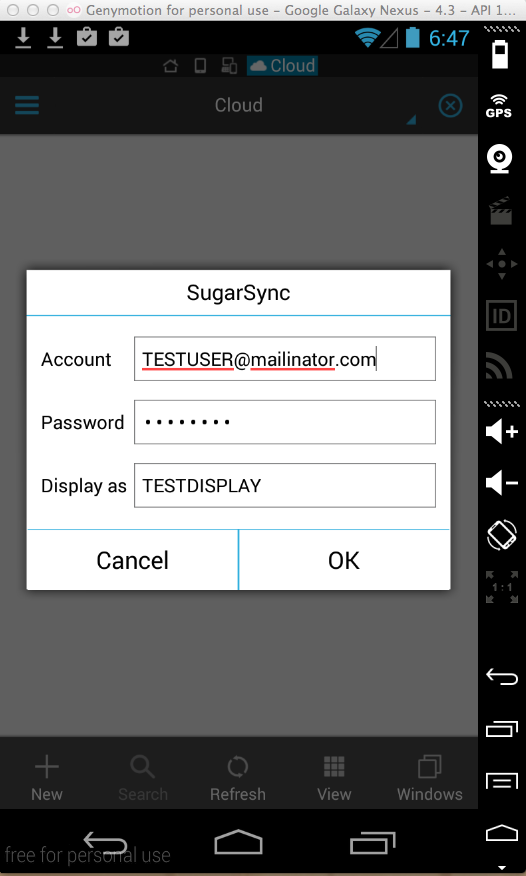
Harvesting them from Burp via MITM attack:
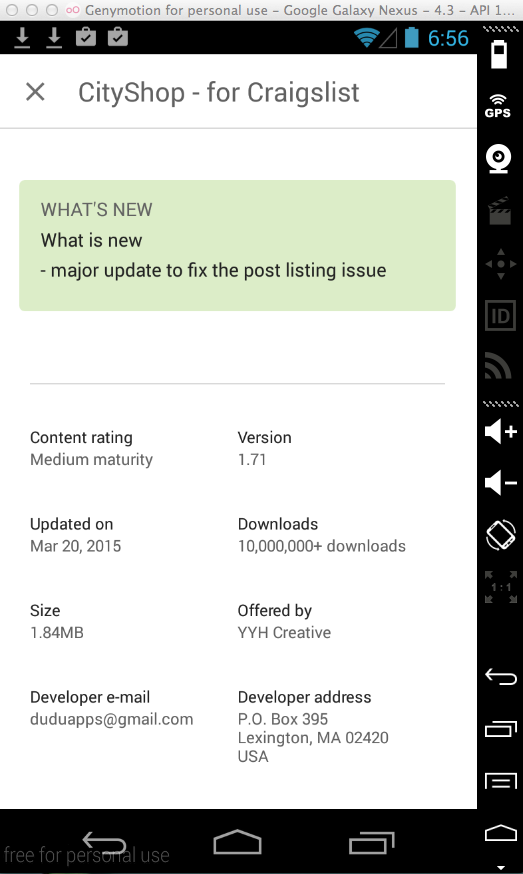
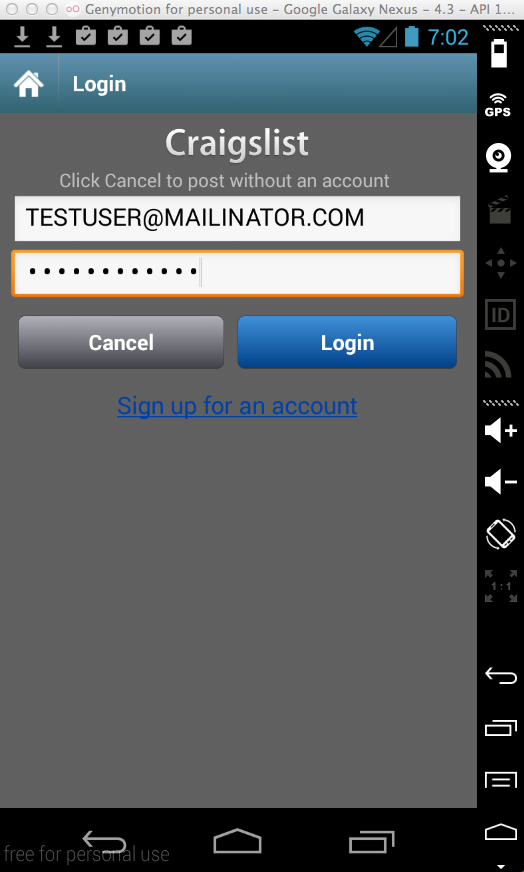
CityShop - for Craigslist (10 Million Downloads)
Here's the app:

The app was updated on 3-20-15,
but it's still vulnerable.
Sending test credentials:
Harvesting them from Burp via MITM attack:
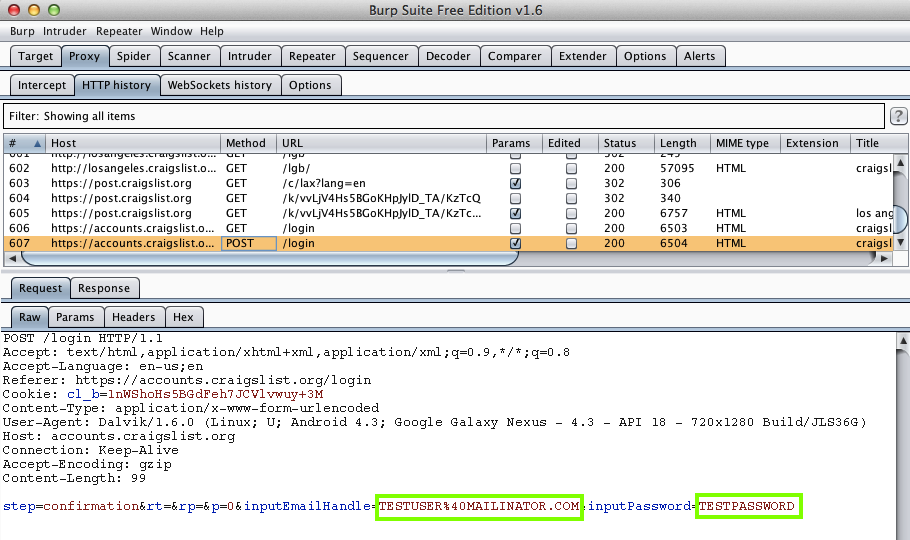
Truecaller - Caller ID & Block (50 Million Downloads)
Here's the app:

The app was updated on 4-21-15.
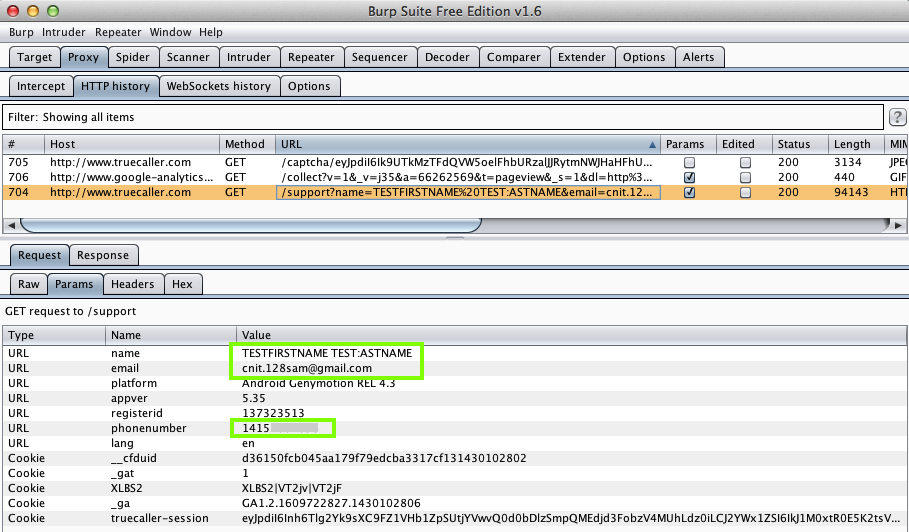
The app doesn't use SSL at all. Instead,
it sends the user's private data (email,
name, and phone number, which is redacted
in the image below) in plaintext each
time the user clicks "FAQ":
That is a strange thing to do, since the
Privacy settings mislead the user into
imagining that he or she has control
over who can see profile data:
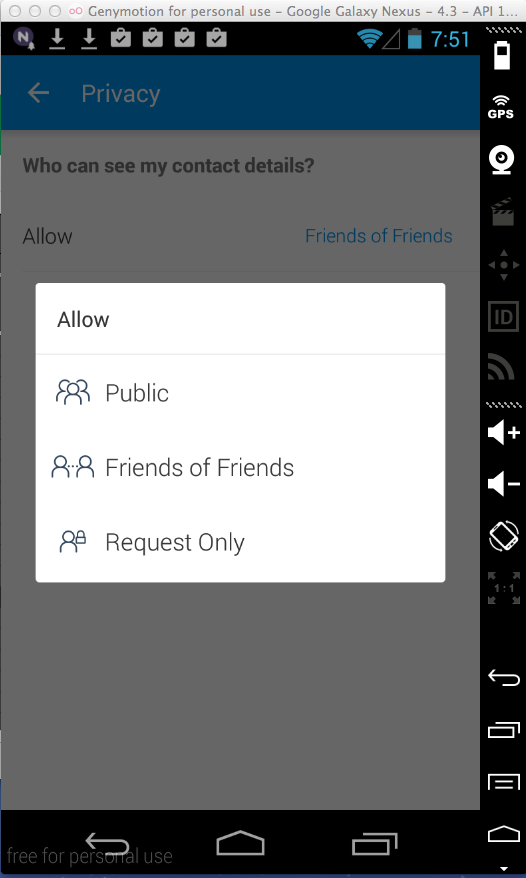
Instachat (5 Million Downloads)
Here's the app:

The app was updated on 2-27-15,
but it's still vulnerable.
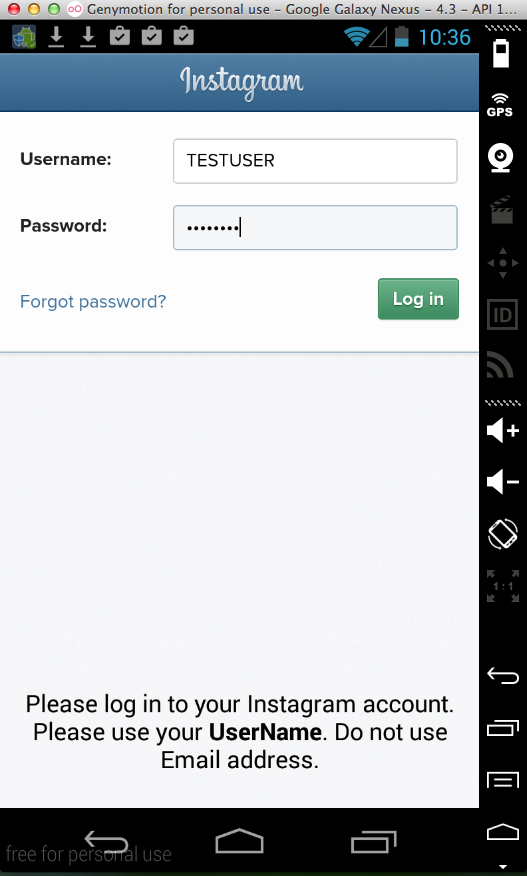
Sending test credentials:
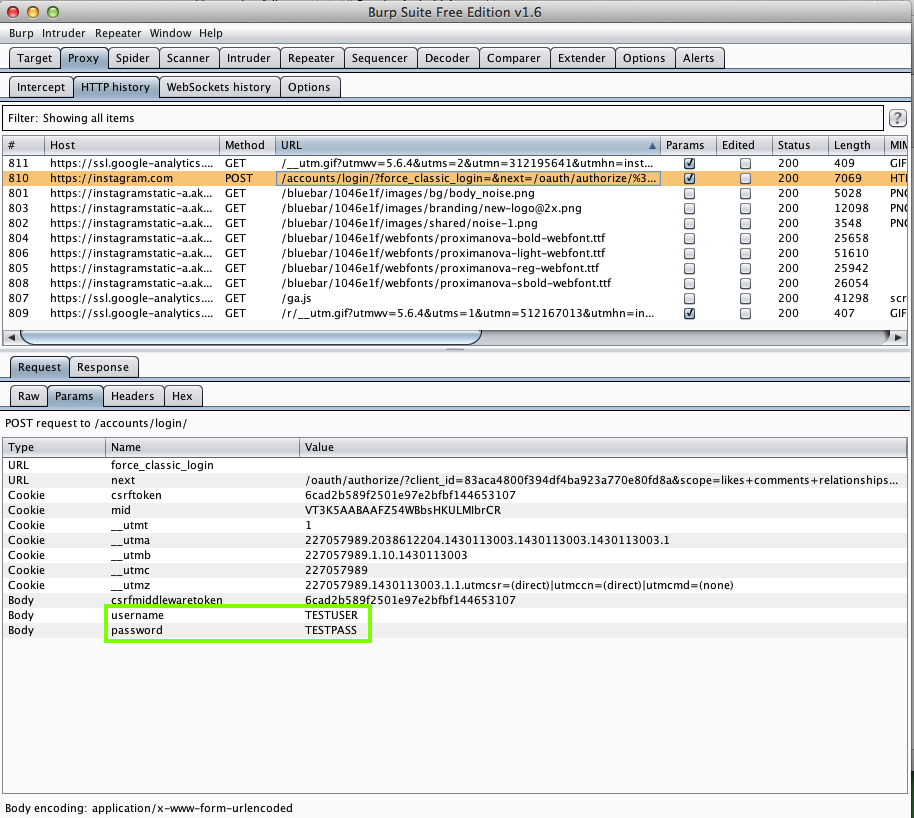
Harvesting them from Burp via MITM attack:
Phone for Google Voice & GTalk (1 Million Downloads)
Here's the app:
The app was updated on 2-10-15,
but it's still vulnerable.
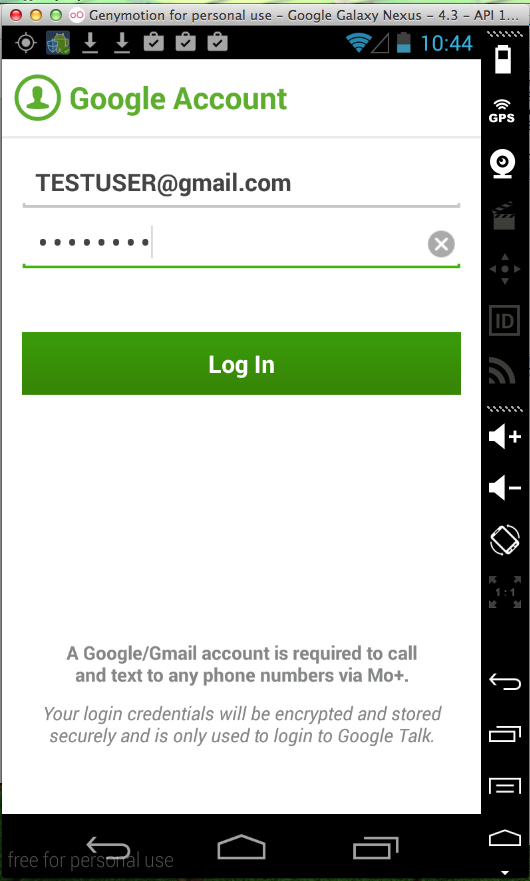
Sending test credentials:
It gives a connection error:
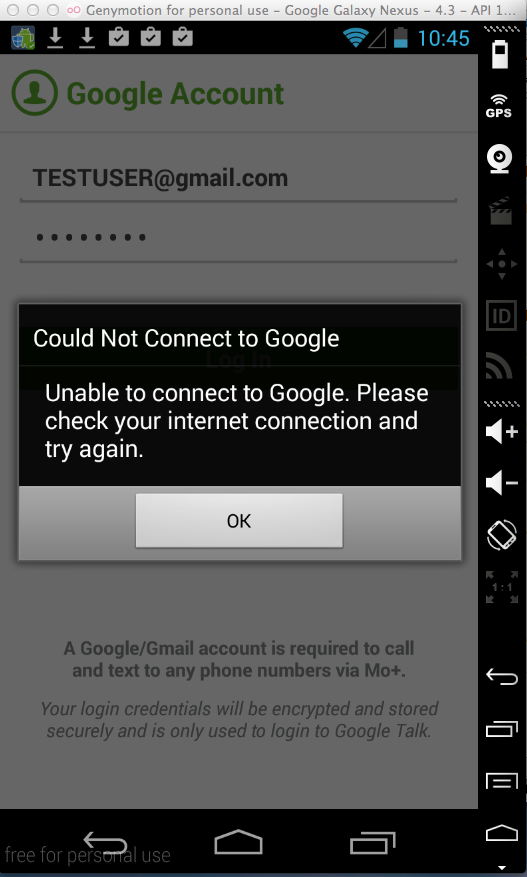
But it sends the credentials to the attacker
anyway:
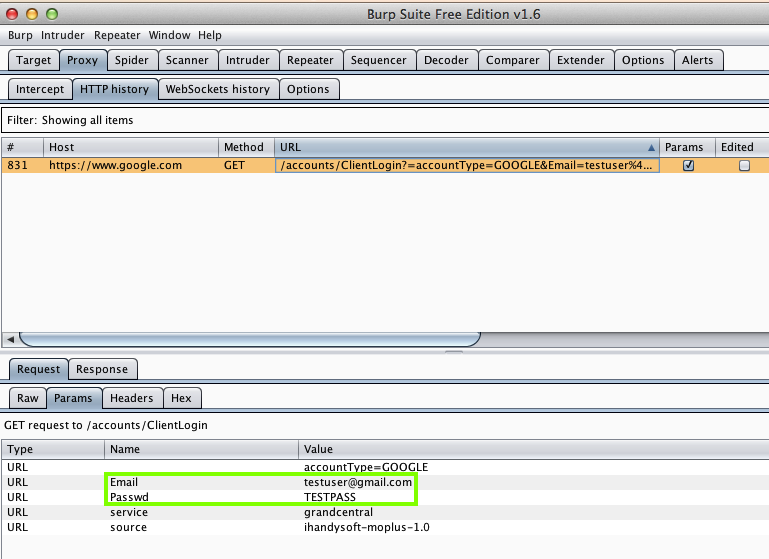
OkCupid (5 Million Downloads)
Here's the app:

This is droll--it tries to place the
blame on the user for its broken
HTTPS implementation. I decided to use
Wi-Fi anyway.
Sending test credentials:

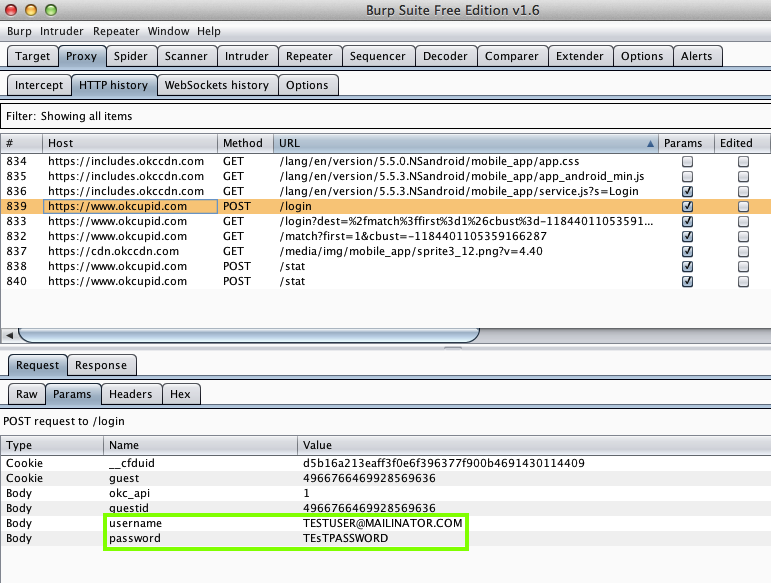
Harvesting them from Burp via MITM attack:
Safeway (1 Million Downloads)
Here's the app:

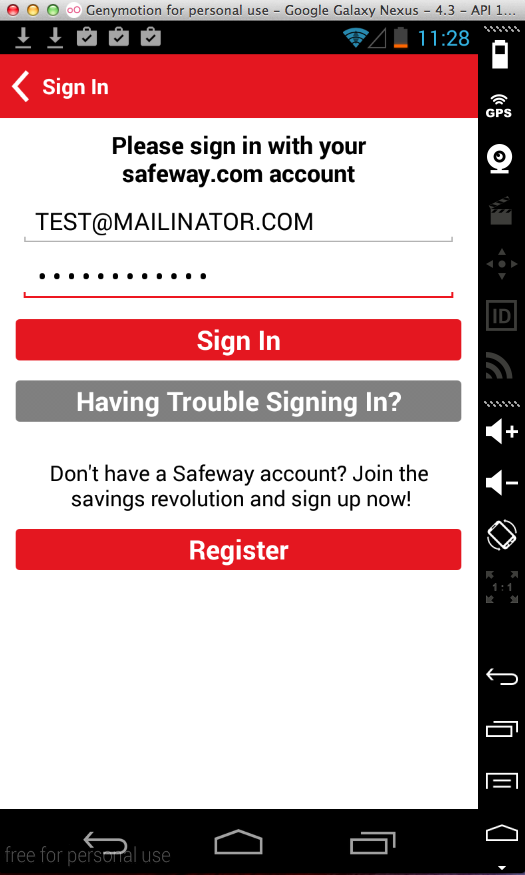
Sending test credentials:
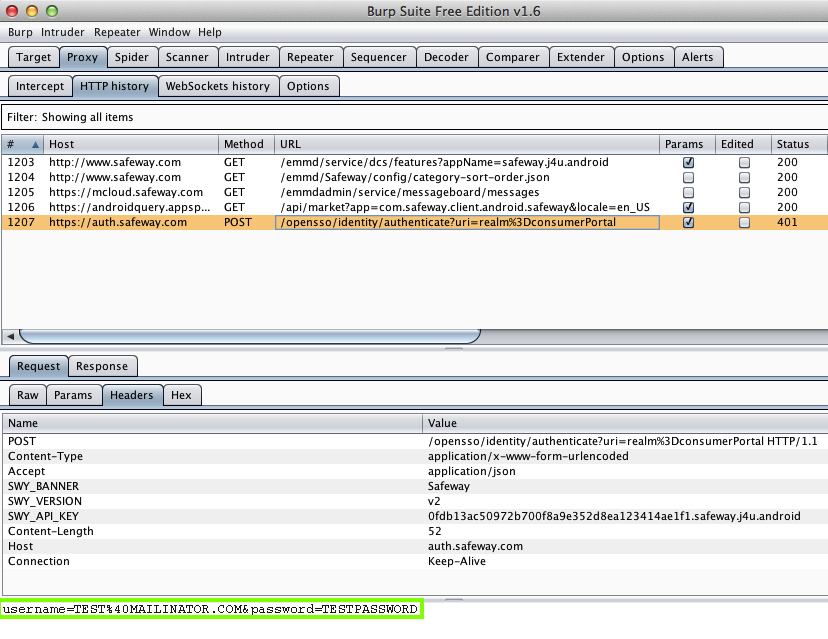
Harvesting them from Burp via MITM attack:
DISH Anywhere (5 Million Downloads)
Here's the app:

Sending test credentials:
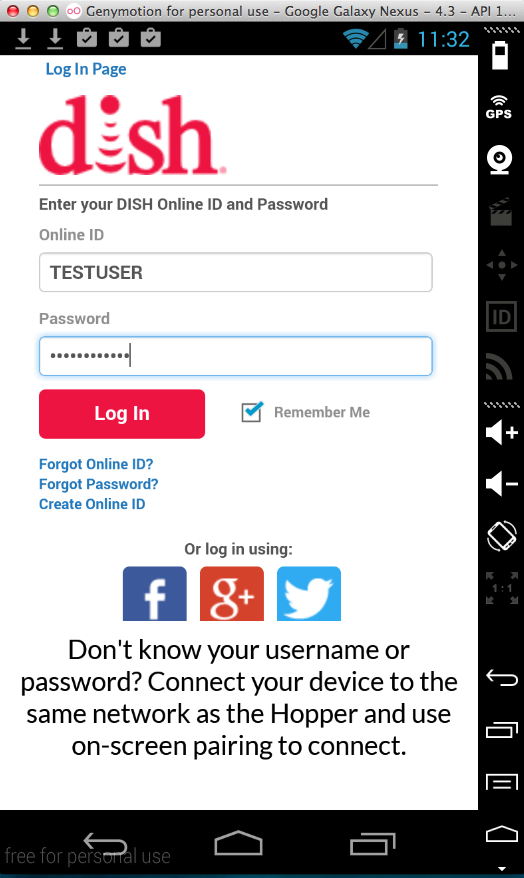
Harvesting them from Burp via MITM attack:
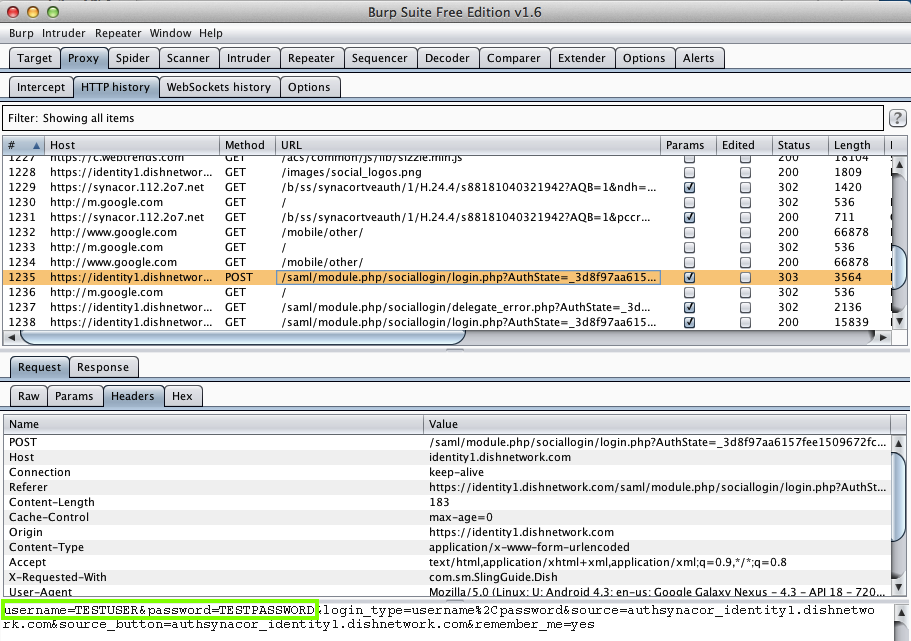
SomNote (1 Million Downloads)
Here's the app:

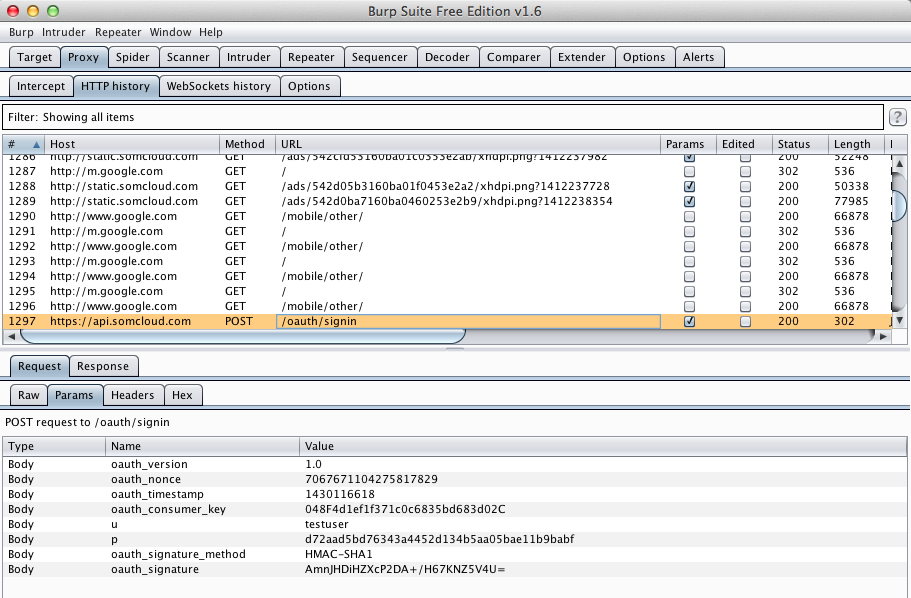
I logged in with test credentials,
and harvested them from Burp via MITM attack.
Note that the HTTPS certificate is not
validated, so the username is visible,
but since the app uses hashing the password
is not visible.
AMC Security (5 Million Downloads)
Here's the app:

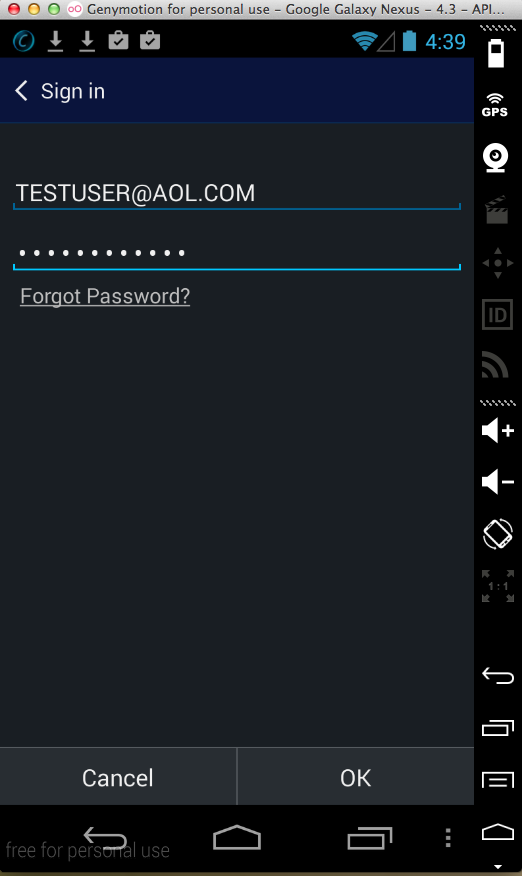
Sending test credentials:
Harvesting them from Burp via MITM attack:
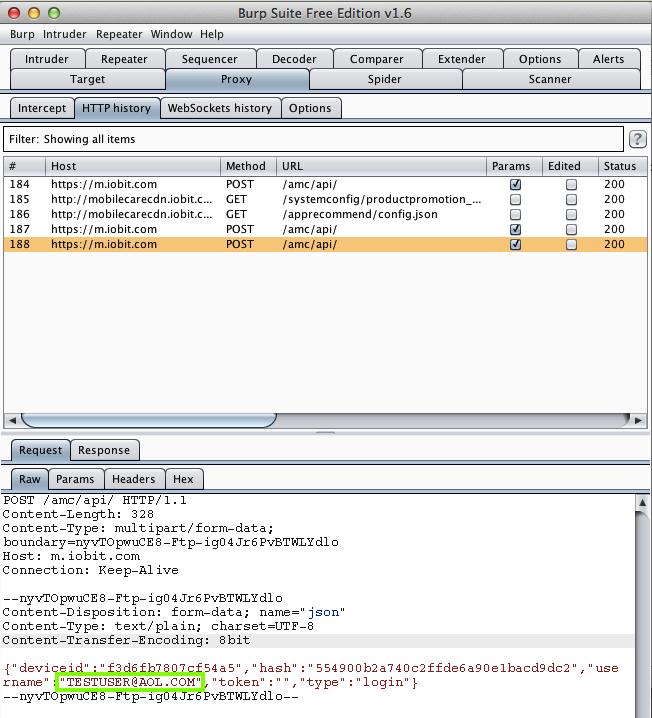
Note that the password is hashed or encrypted
so that it cannot be trivially captured, even
though AMC broke HTTPS. Three cheers for
defense in depth!
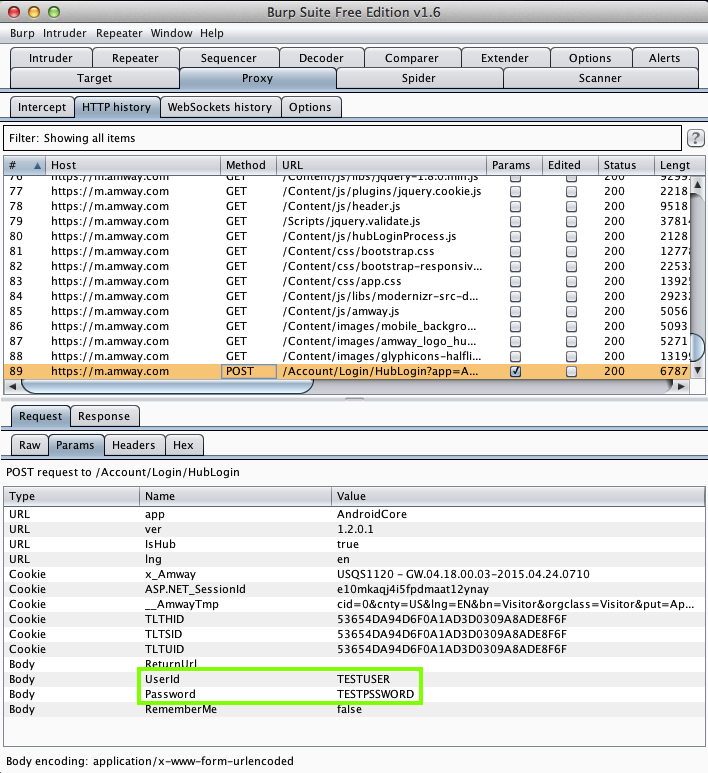
Amway (100,000 Downloads)
Here's the app:

Sending test credentials:
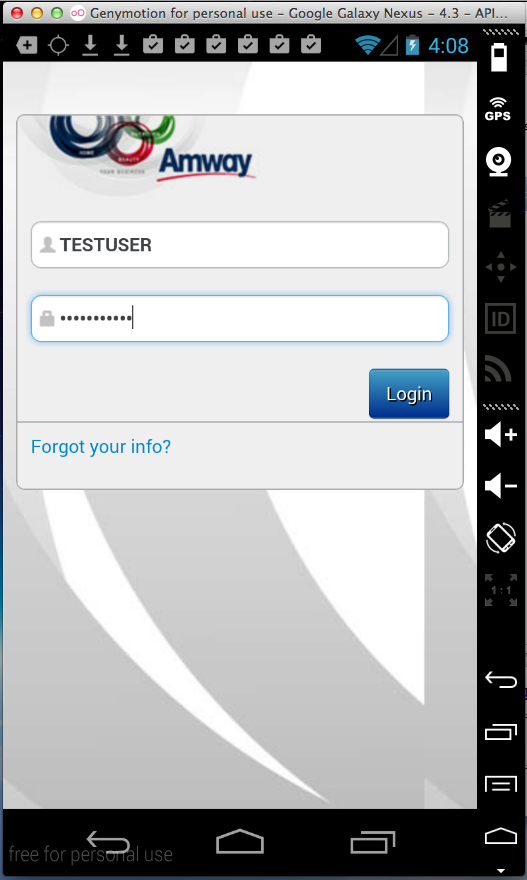
Harvesting them from Burp via MITM attack:
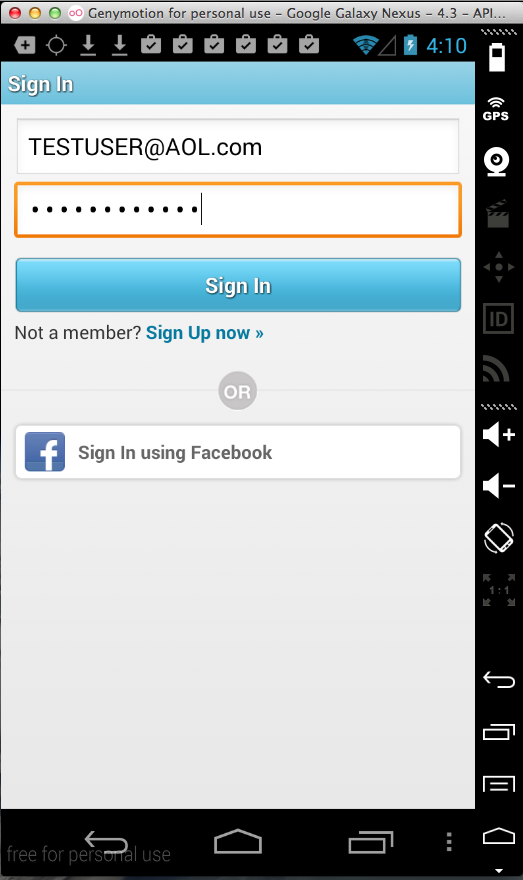
Ask (1 Million Downloads)
Here's the app:

Sending test credentials:
Harvesting them from Burp via MITM attack:
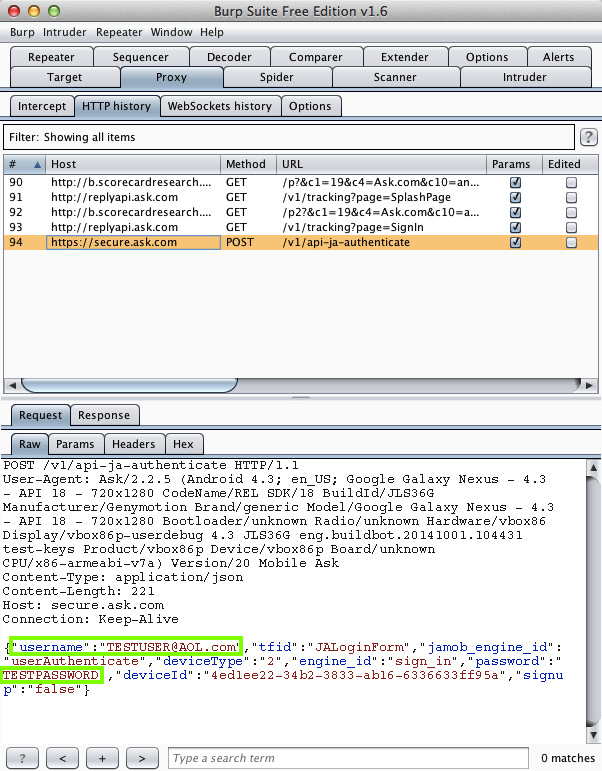
Band (10 Million Downloads)
Here's the app:

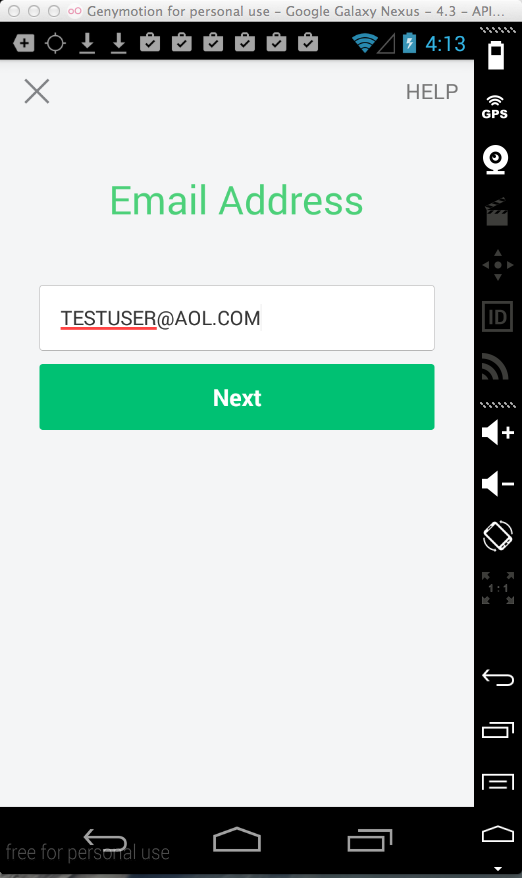
Sending test credentials:
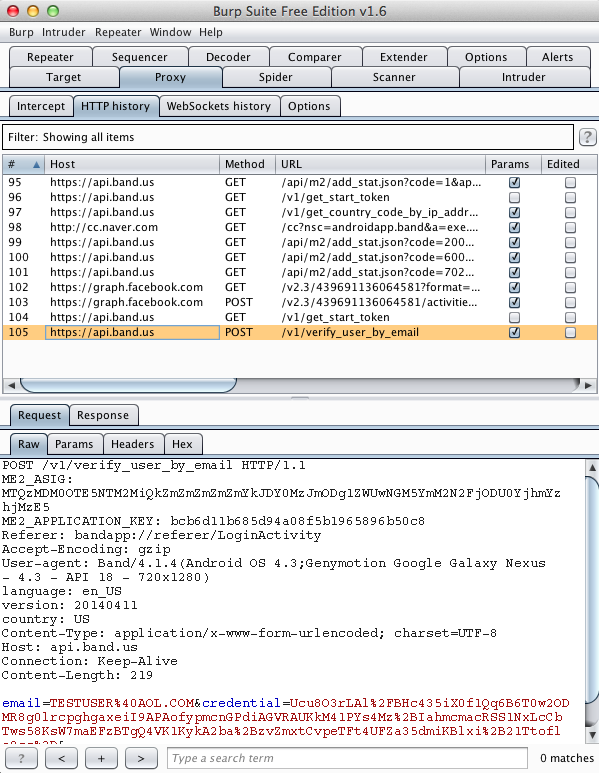
Harvesting them from Burp via MITM attack:
Club Personal (1 Million Downloads)
Here's the app:

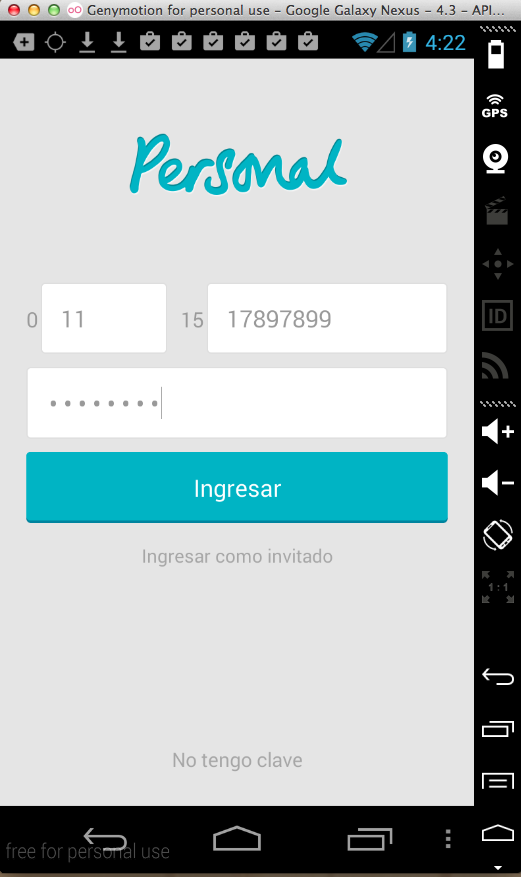
Sending test credentials:
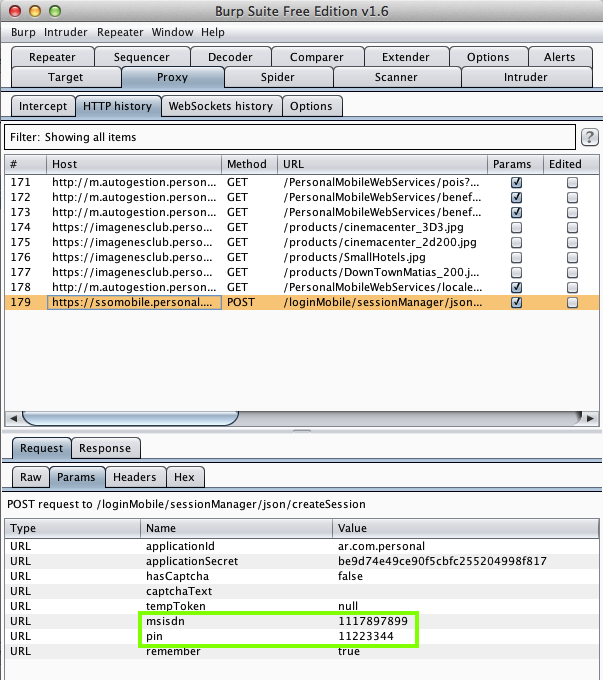
Harvesting them from Burp via MITM attack:
DailyFinance from AOL (100,000 Downloads)
Here's the app:

Sending test credentials:
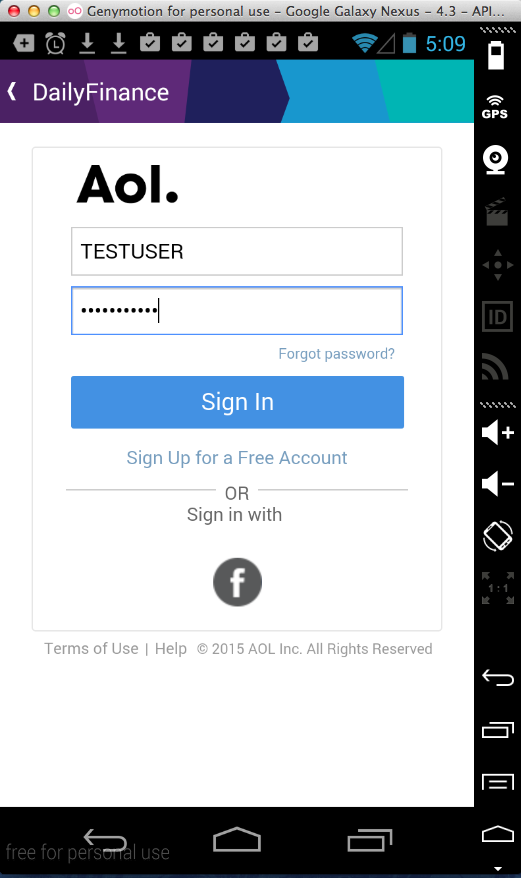
Harvesting them from Burp via MITM attack:
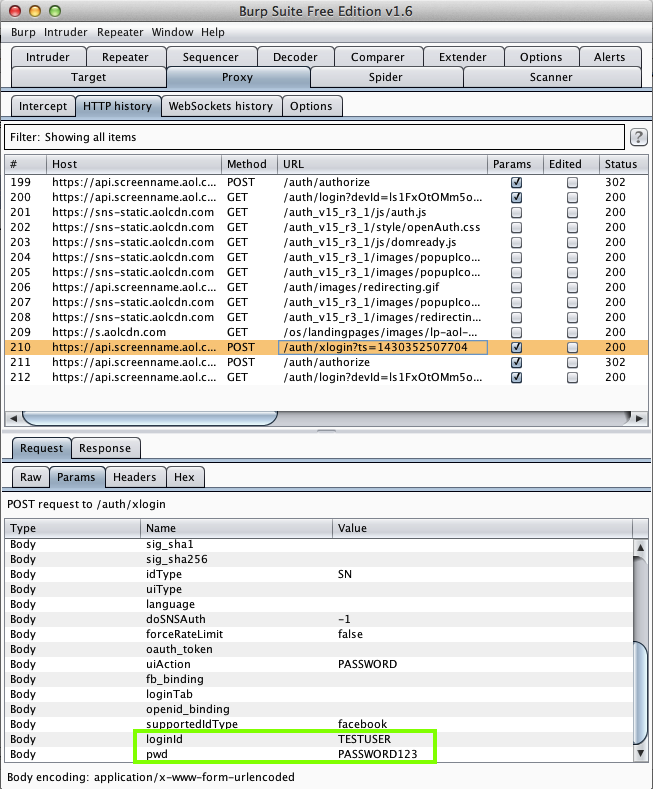
DMV NOW (California DMV) (500,000 Downloads)
Here's the app:

Sending test credentials:
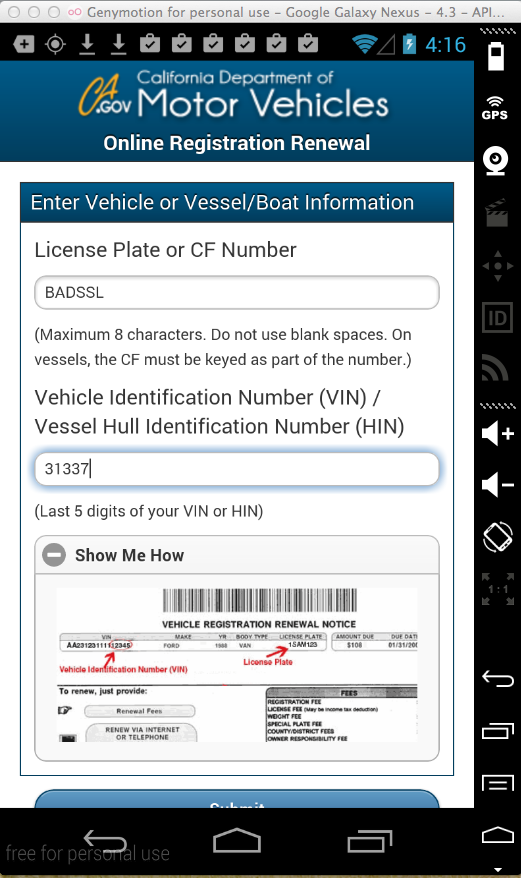
Harvesting them from Burp via MITM attack:
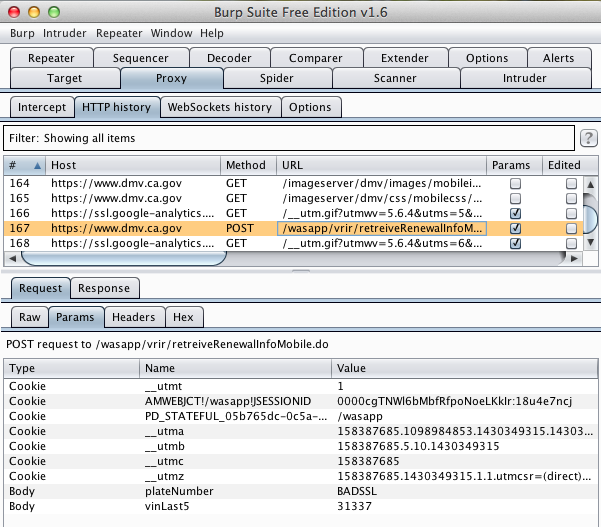
Equifax (100,000 Downloads)
Here's the app:

Sending test credentials:
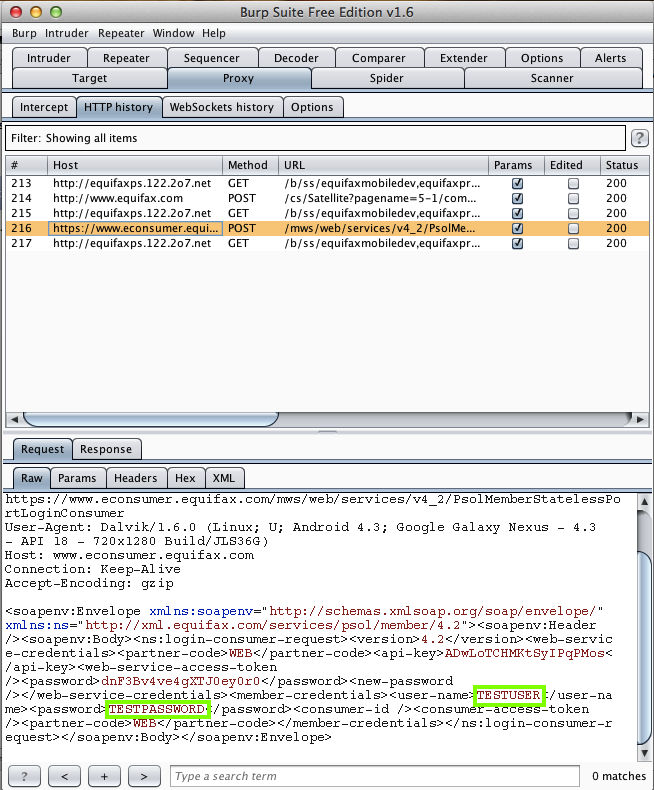
Harvesting them from Burp via MITM attack:
Floating Browser (100,000 Downloads)
Here's the app:
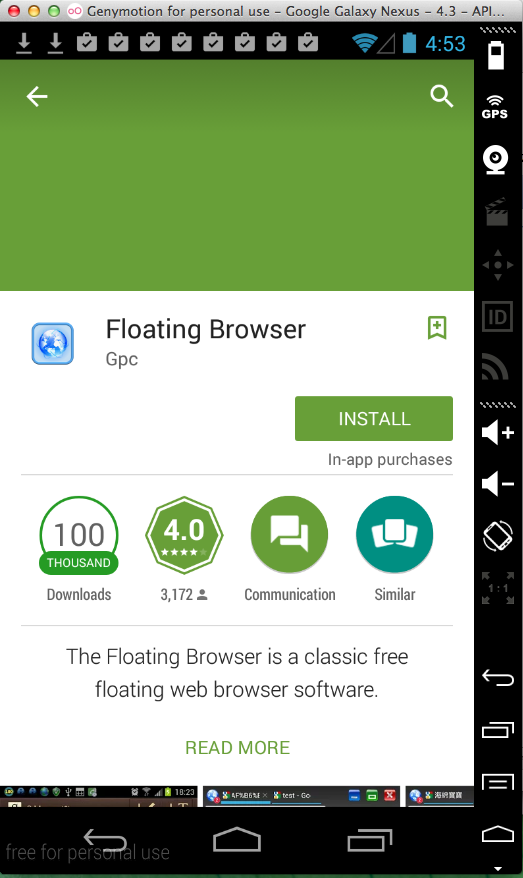
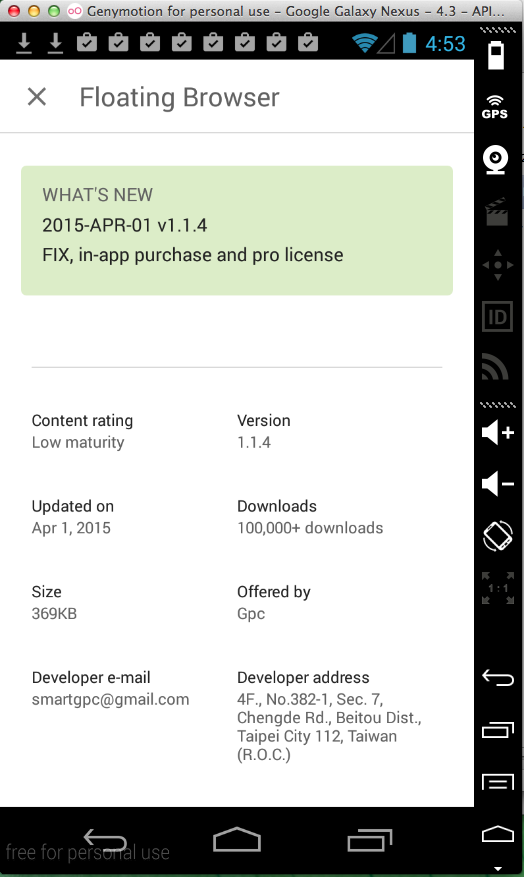
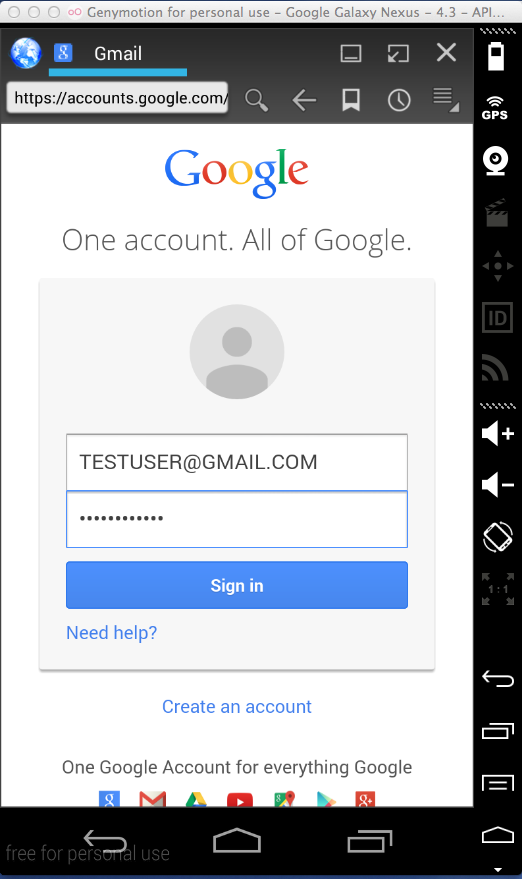
Sending test credentials:
Harvesting them from Burp via MITM attack:
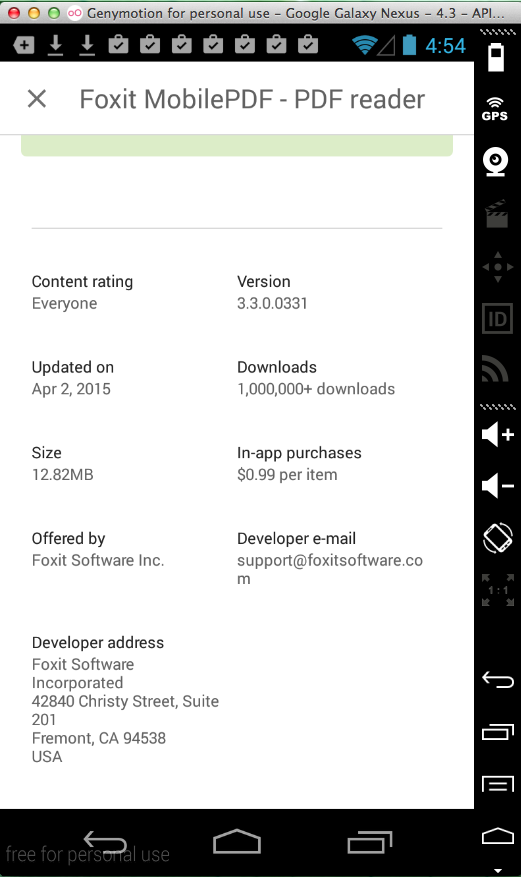
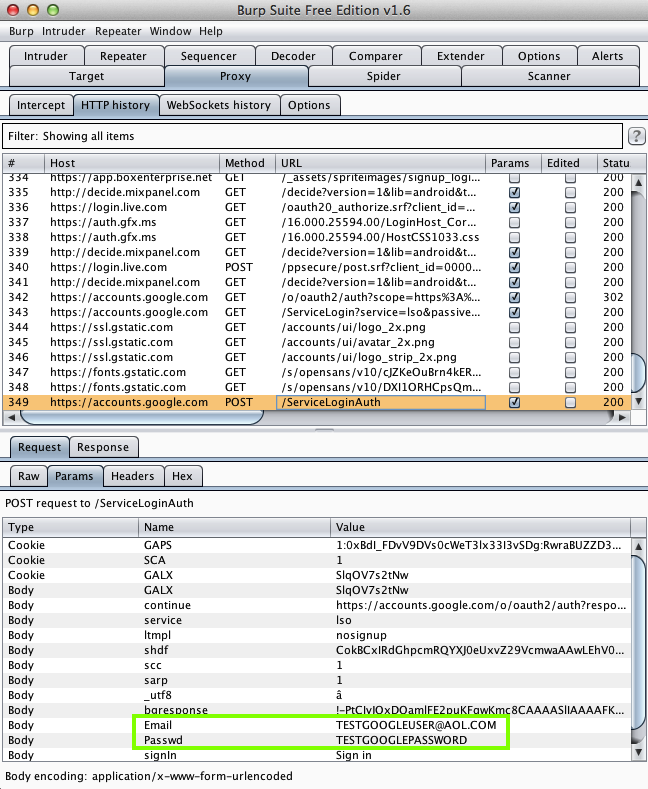
Foxit MobilePDF - PDF reader (1 Million Downloads)
Foxit MobilePDF - PDF reader (1 Million Downloads)SSL MITM; exposes credentials
Here's the app:

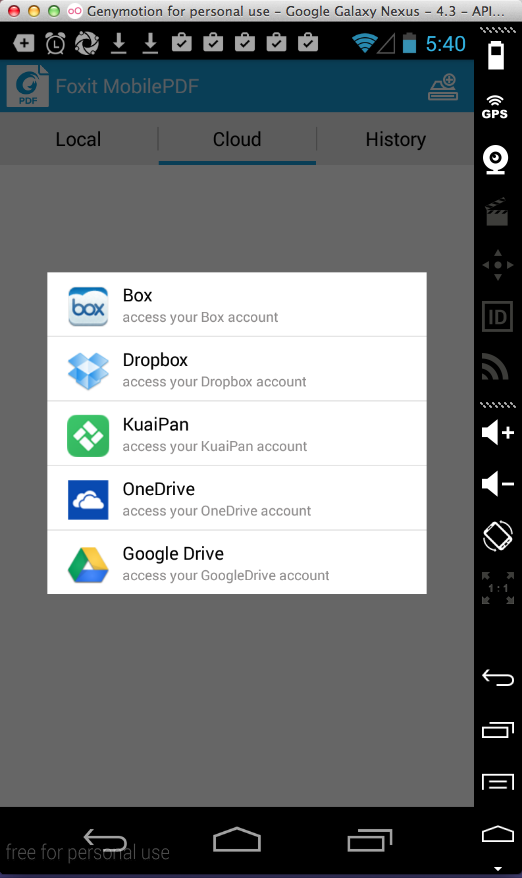
It offers to connect to several
cloud services:
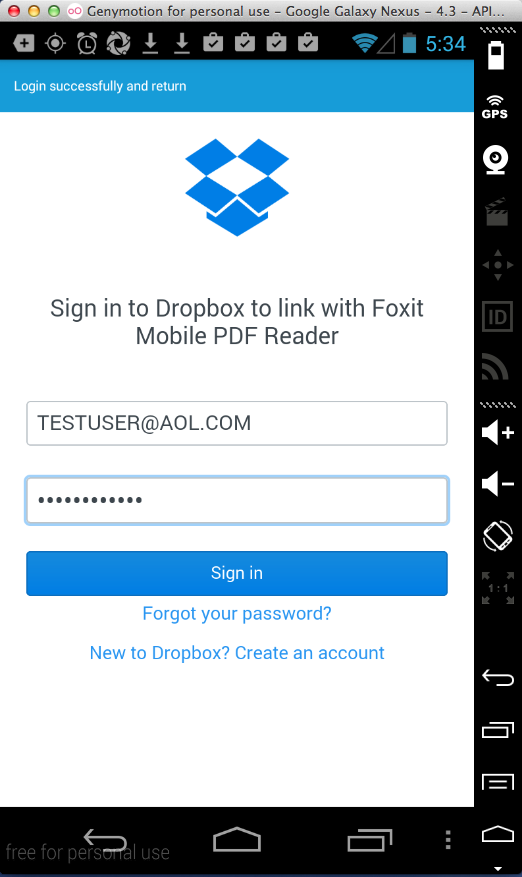
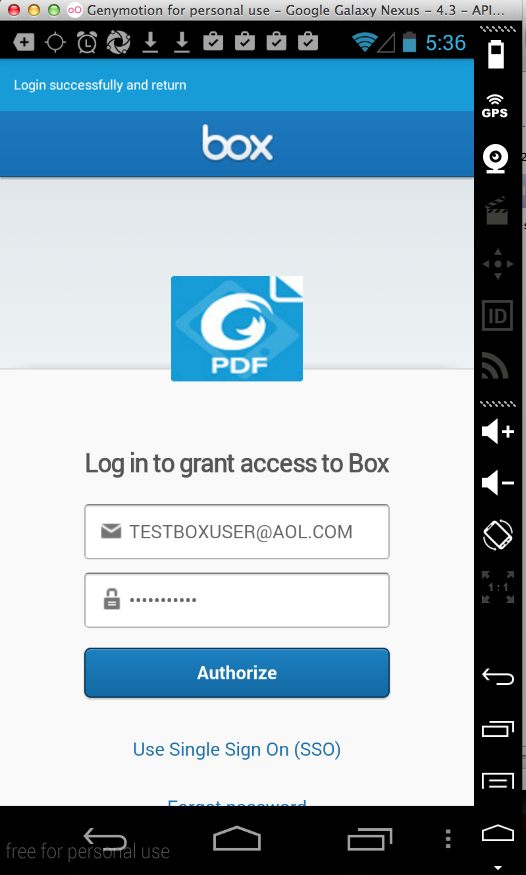
And it leaks credentials for every one
I tested: DropBox, Box, Microsoft, and Google.
Harvesting them from Burp via MITM attack:

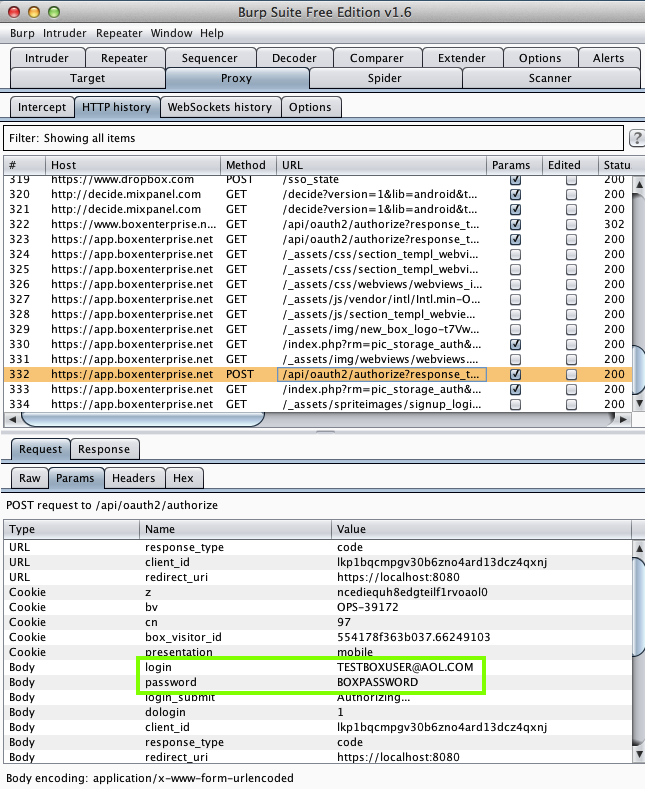
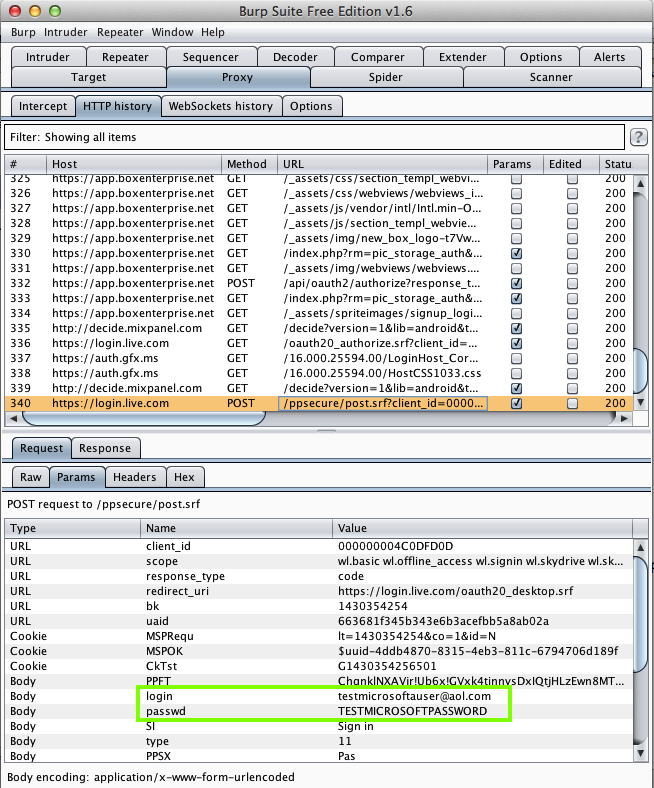
On 5-23-15 I noticed that there's
a new version:
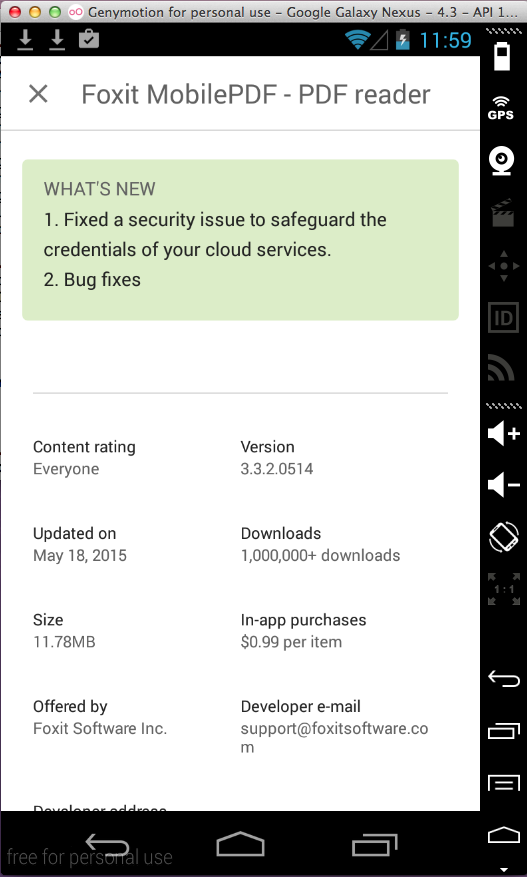
And the problem is indeed fixed!
GittiGidiyor (eBay) (1 Million Downloads)
Here's the app:

Sending test credentials:
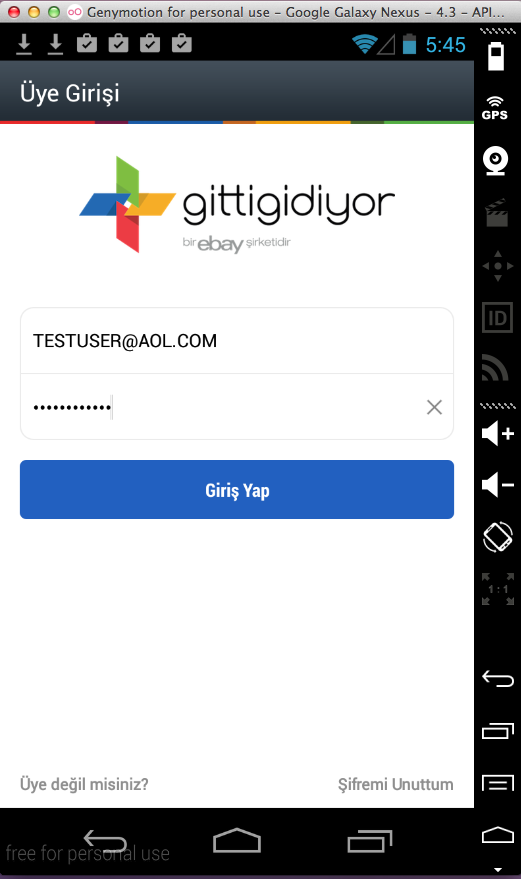
Harvesting them from Burp via MITM attack:
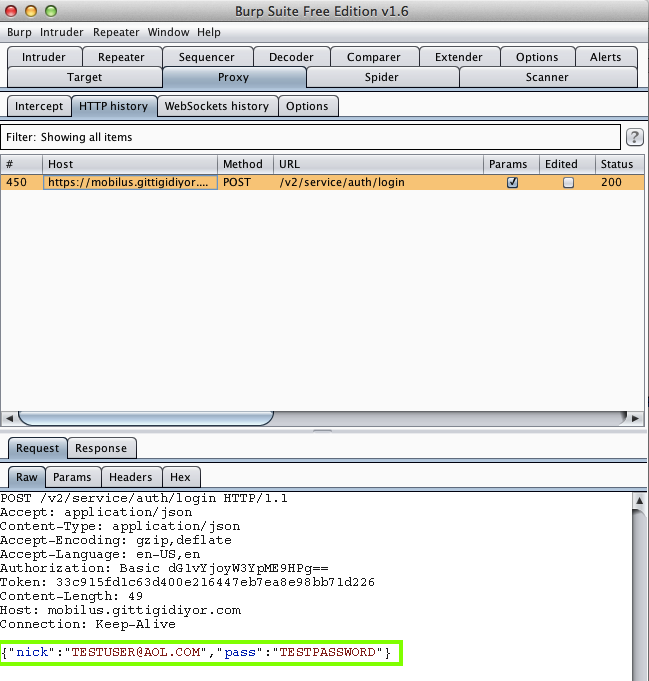
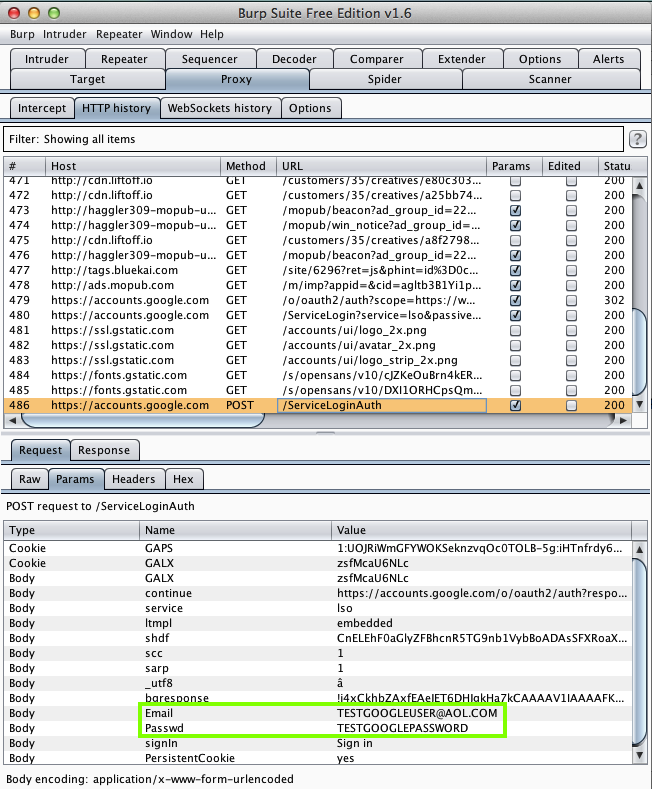
IM+ (100,000 Downloads)
Here's the app:

It offers to connect to several services:
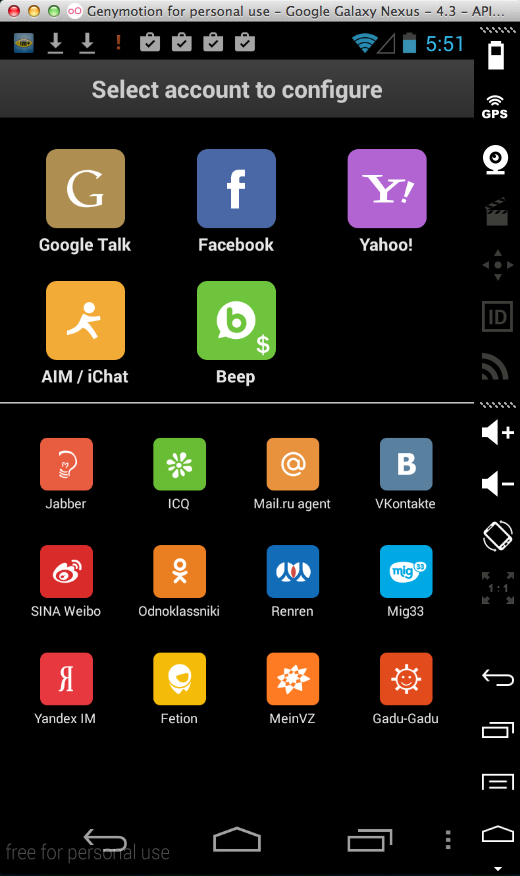
Most aren't vulnerable to an MITM
attack, but Google is.
Sending test credentials:
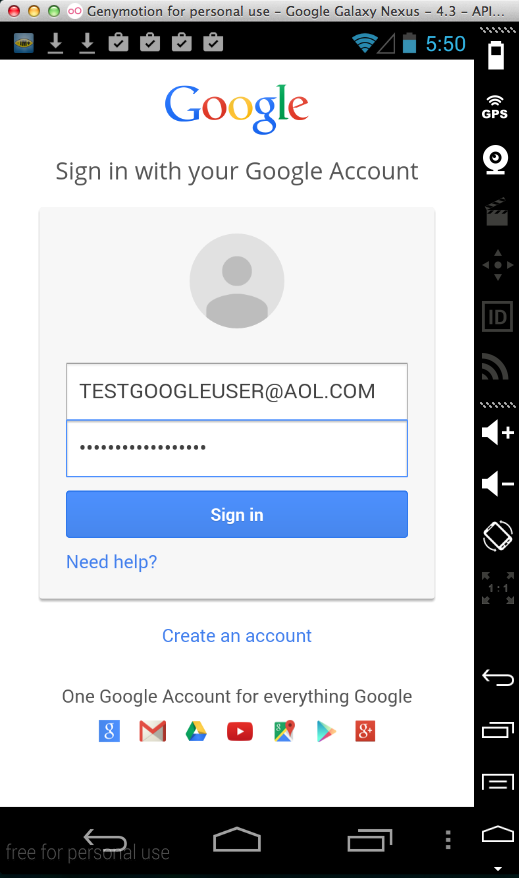
Harvesting them from Burp via MITM attack:
InstaG (1 Million Downloads)
Here's the app:

Sending test credentials:
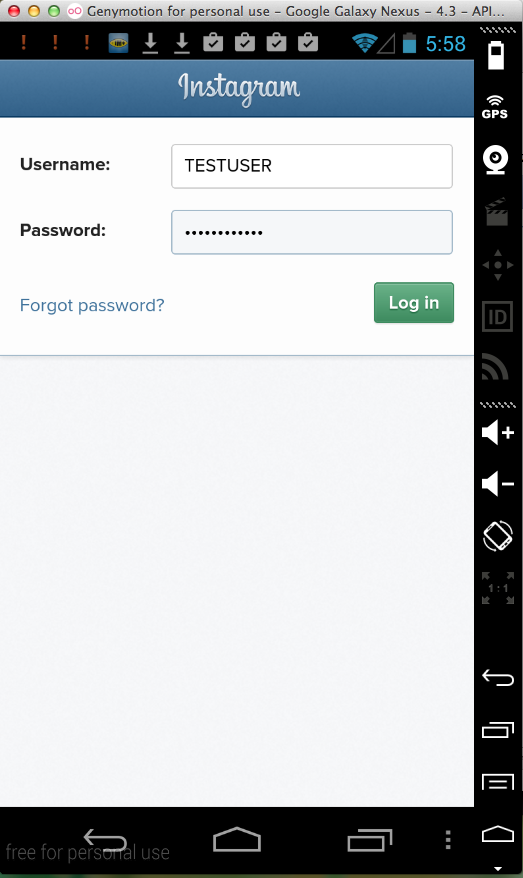
Harvesting them from Burp via MITM attack:
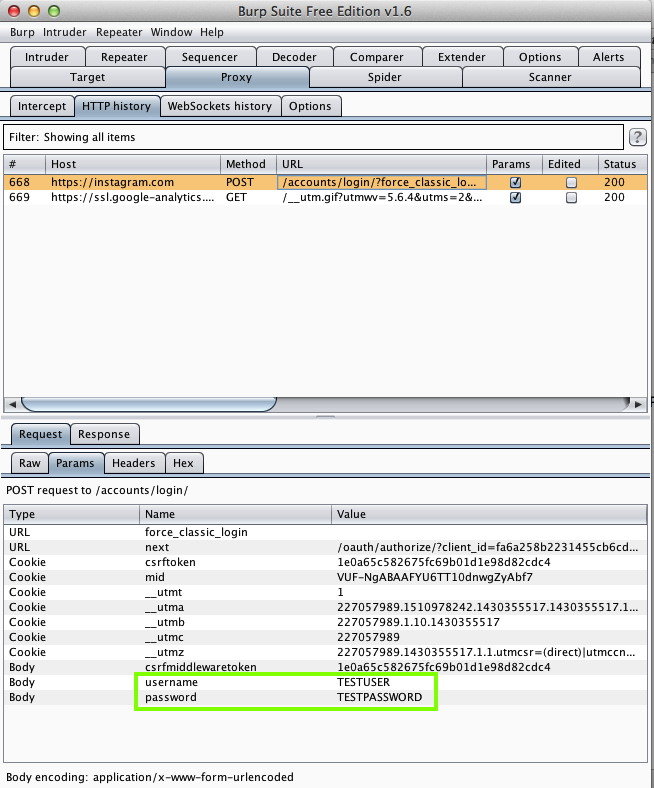
InstaMessage (1 Million Downloads)
Here's the app:

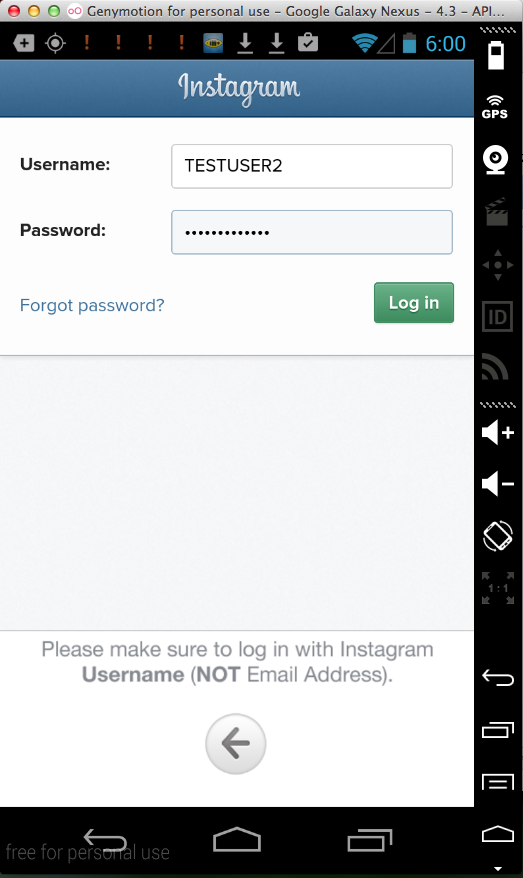
Sending test credentials:
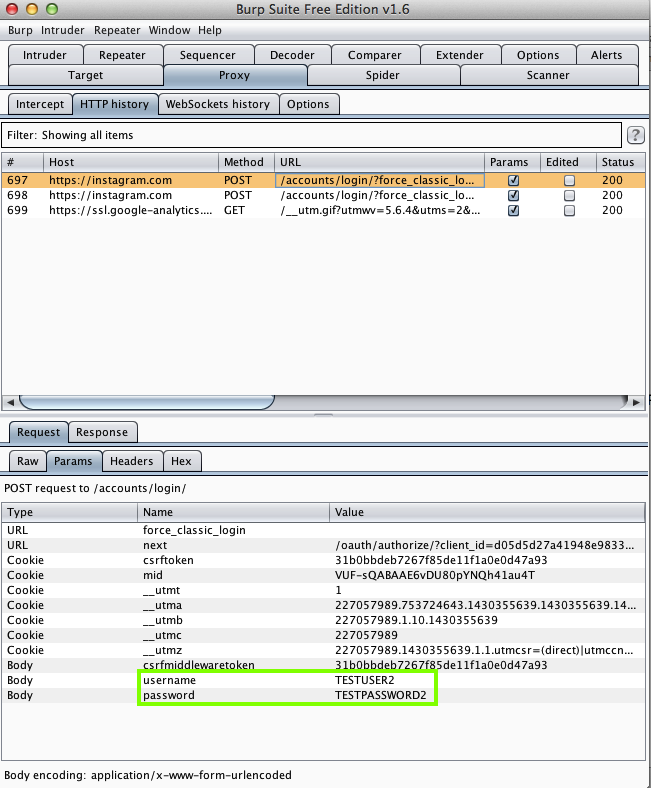
Harvesting them from Burp via MITM attack:
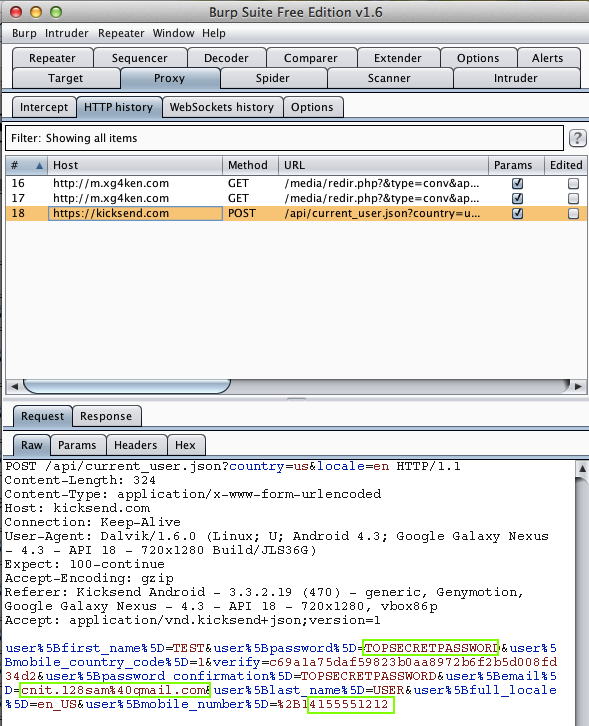
KickSend (500,000 Downloads)
Here's the app:
Sending test credentials:
Harvesting them from Burp via MITM attack:
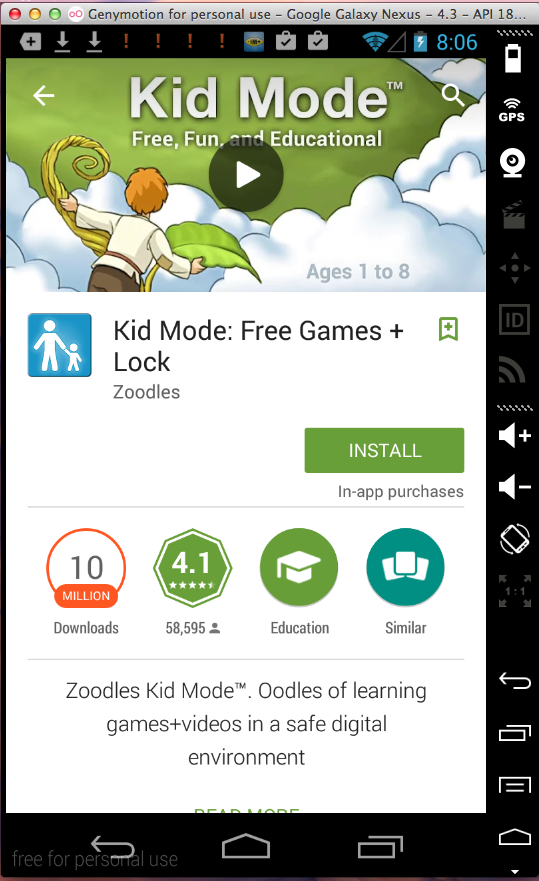
Kid Mode (1 Million Downloads)
Here's the app:
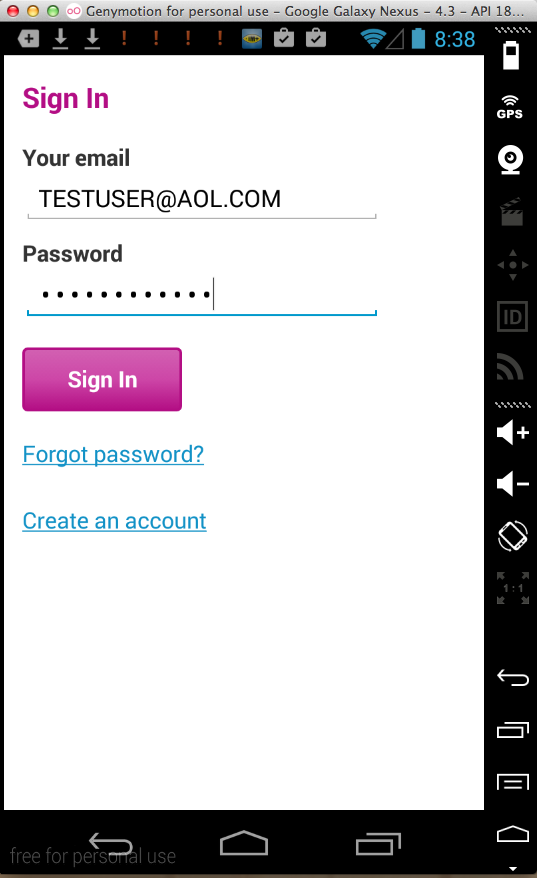
Sending test credentials:
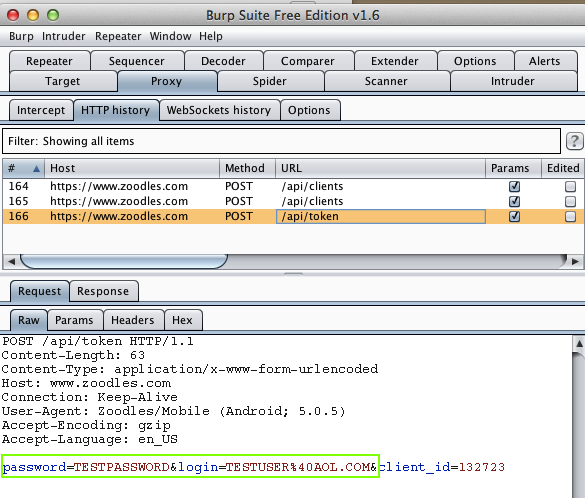
Harvesting them from Burp via MITM attack:
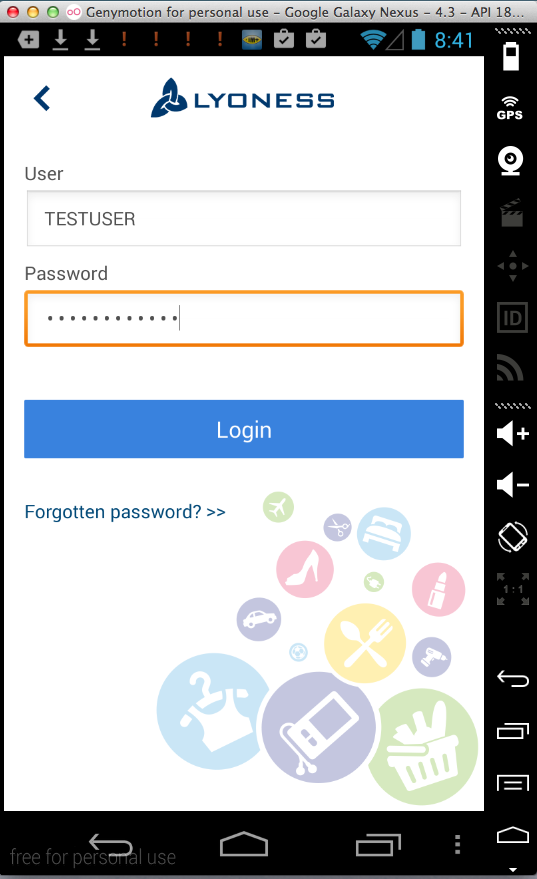
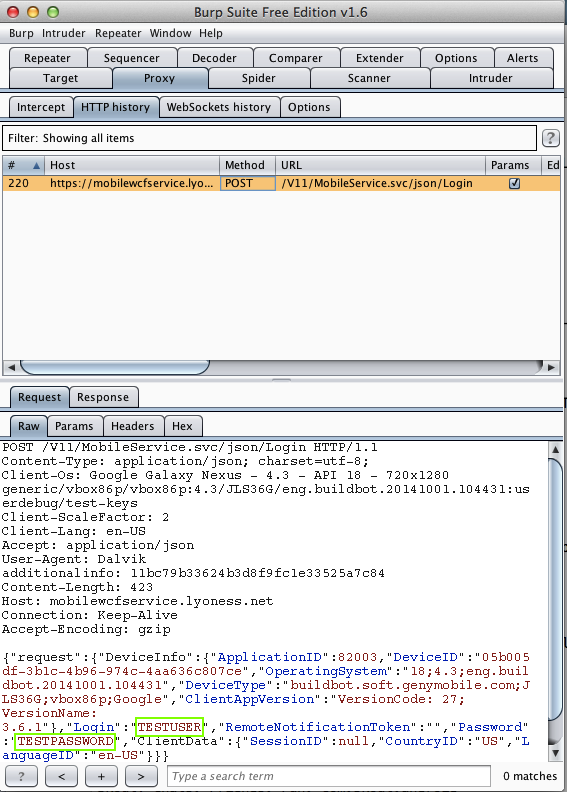
Lyoness (100,000 Downloads)
Here's the app:

Sending test credentials:
Harvesting them from Burp via MITM attack:
Mini Online Shopping (1 Million Downloads)
Here's the app:

Sending test credentials:
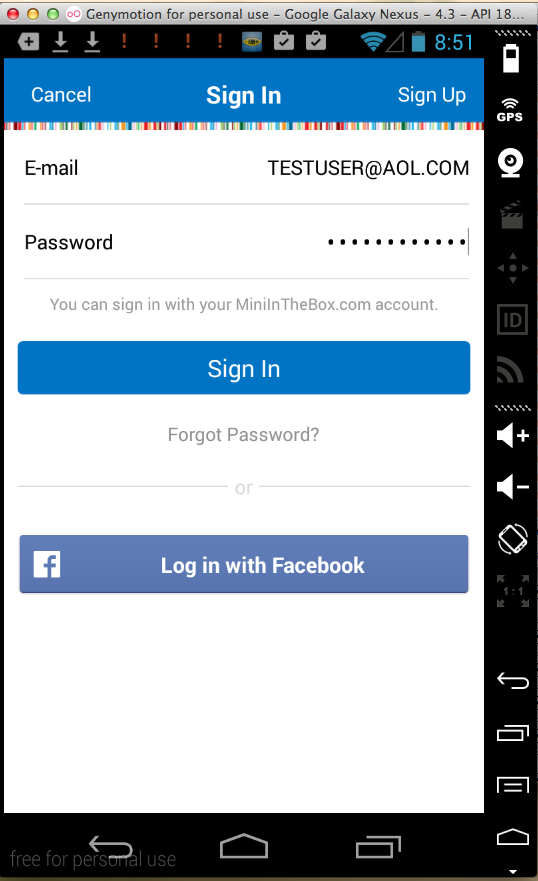
Harvesting them from Burp via MITM attack:
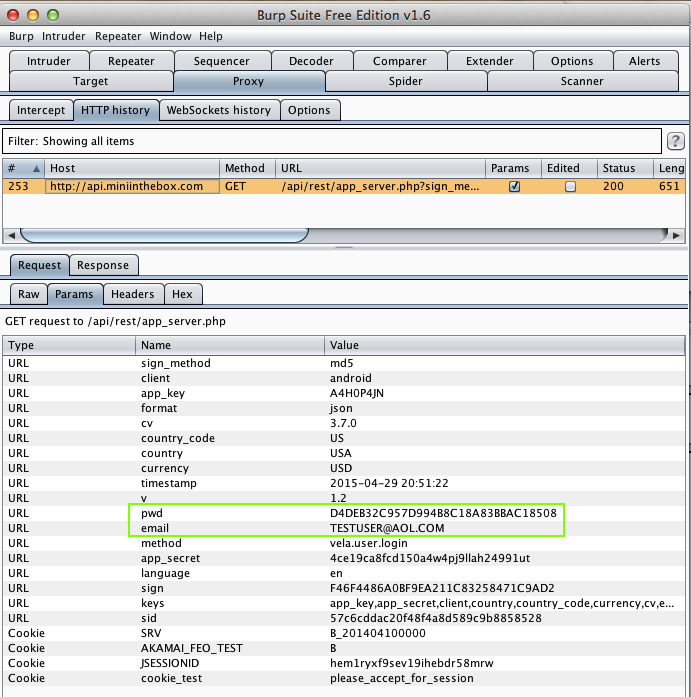
NBA (5 Million Downloads)
Here's the app:
Sending test credentials:
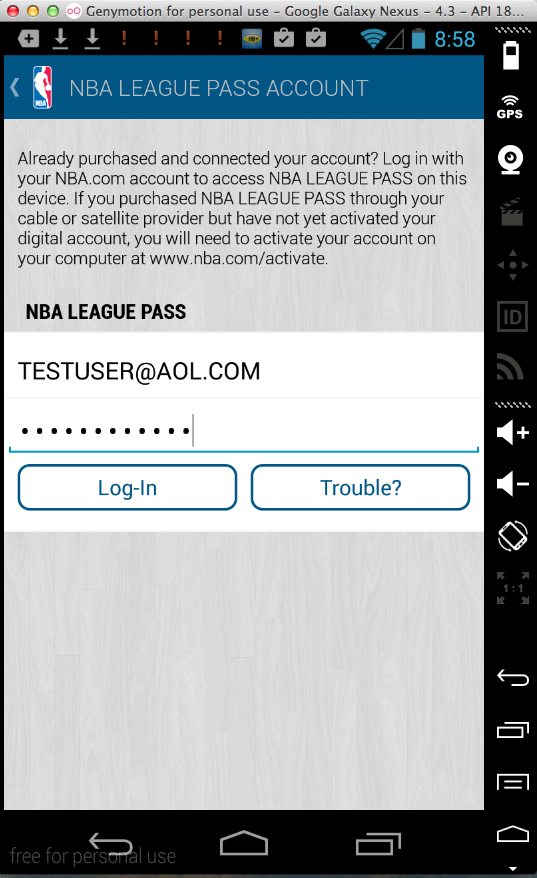
Harvesting them from Burp via MITM attack:
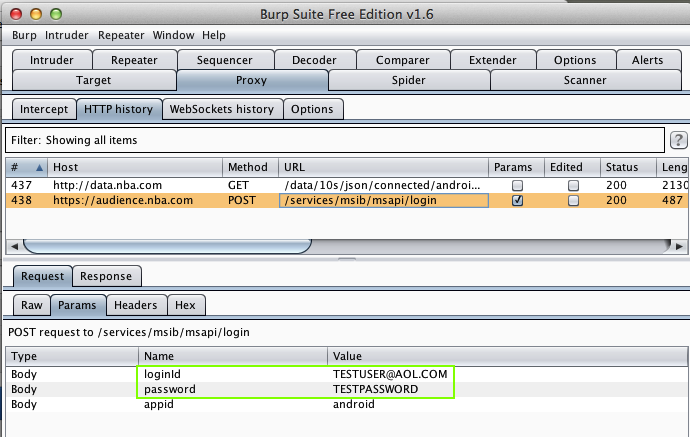
InstaRepost (1 Million Downloads)
Here's the app:

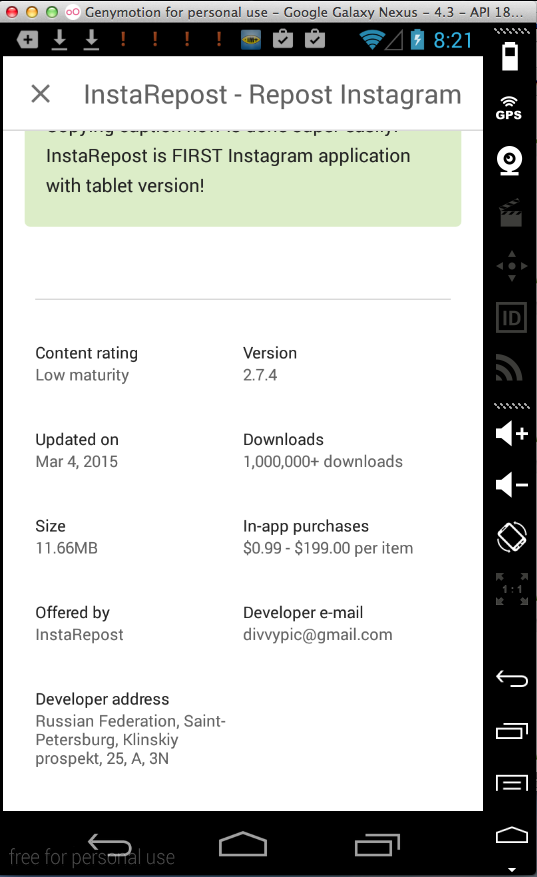
Sending test credentials:
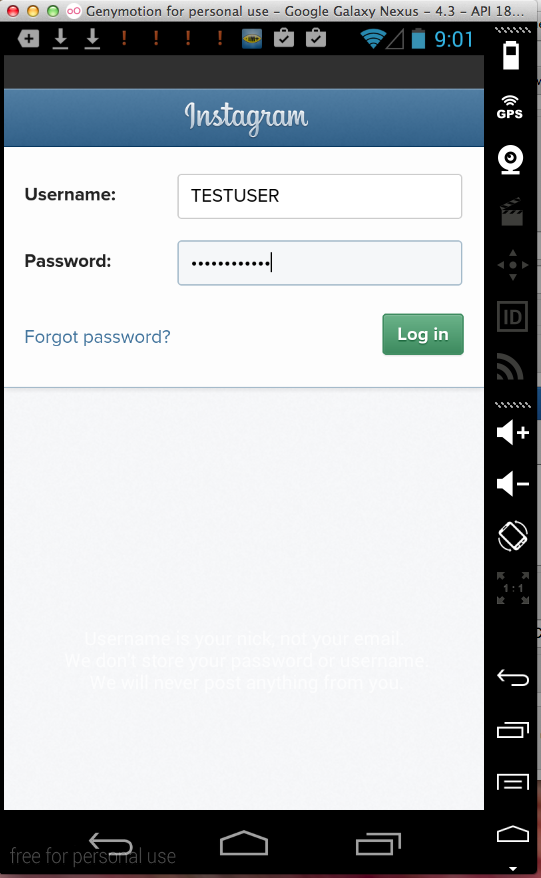
Harvesting them from Burp via MITM attack:
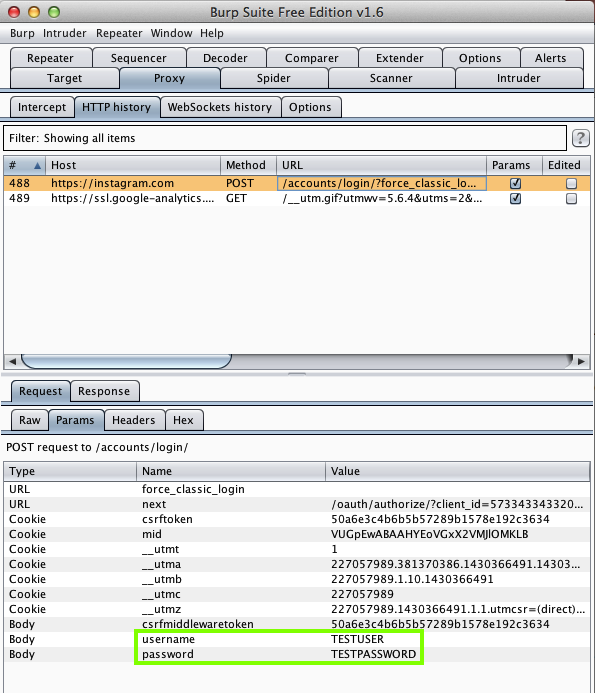
Pizza Hut (5 Million Downloads)
Here's the app:

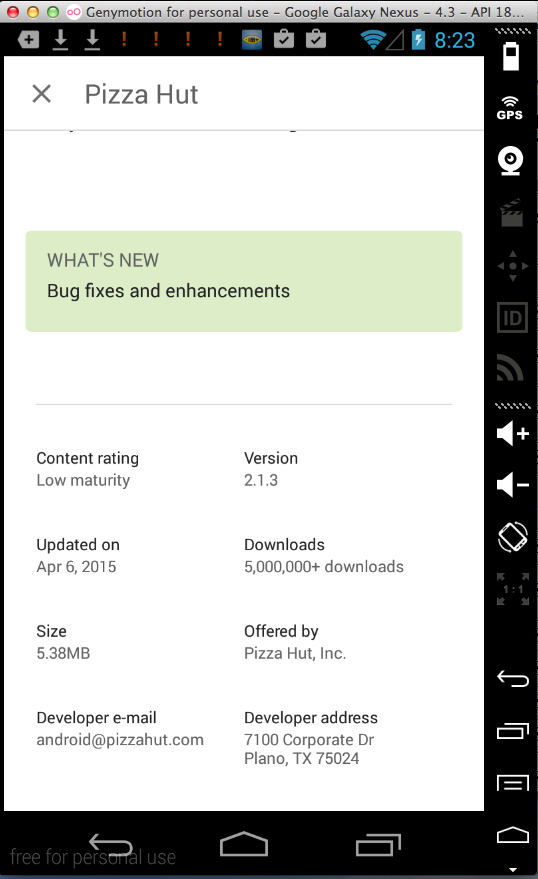
Sending test credentials:

Harvesting them from Burp via MITM attack:
Vulnerable Medical Android Apps
The fact that these apps are in use
implies (but does not prove) HIPAA
violations, since they break HTTPS and
expose their data.
The designers have chosen to leave the apps
insecure months after CERT warned them of
the insecurity.
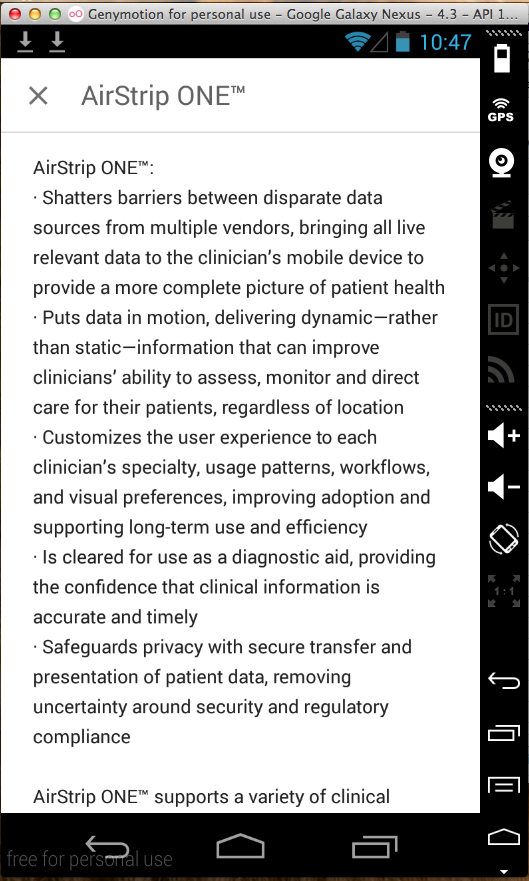
AirStrip ONE (100 Downloads)
This app gathers sensitive
medical data from multiple
sources and and presents it to clinicians.
Each instance of the app apparently
exposes the medical data of multiple
patients.

Sending test credentials:
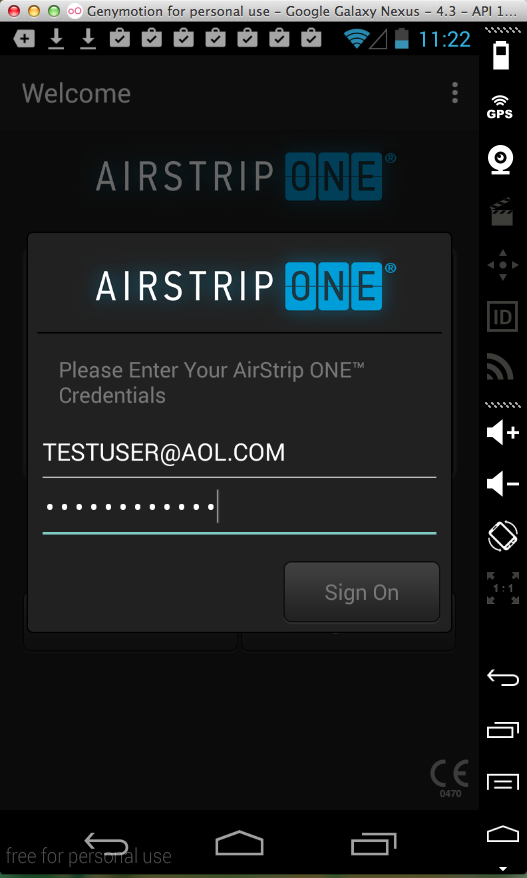
Harvesting them from Burp via MITM attack:
I wasn't able to test the actual
transmission of medical data, but it
is presumably also exposed to a
MITM attack.
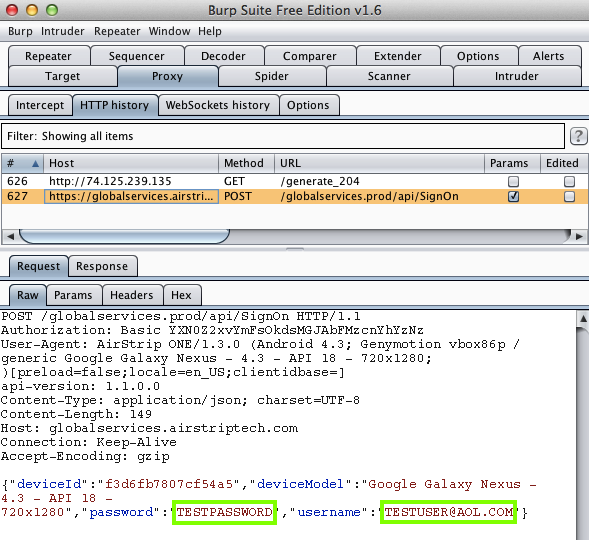
DCGA Medicals (500 Downloads)
Here's the app:
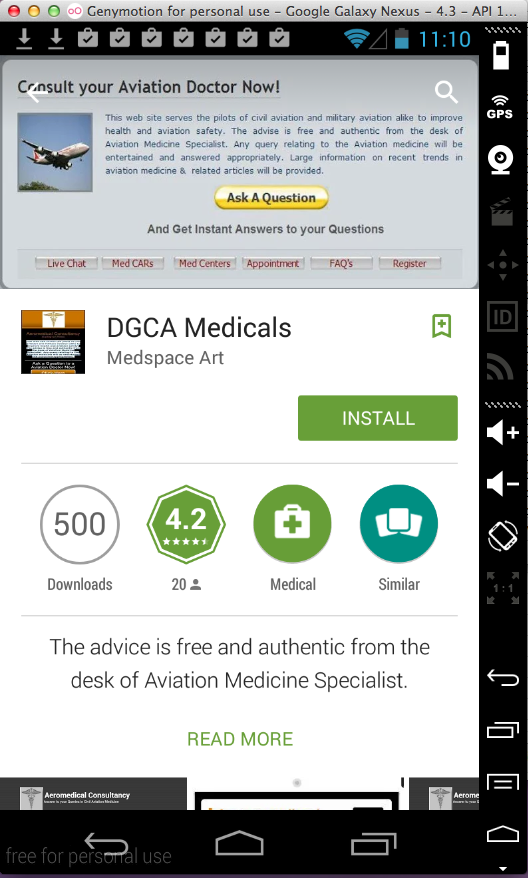
Sending test credentials:
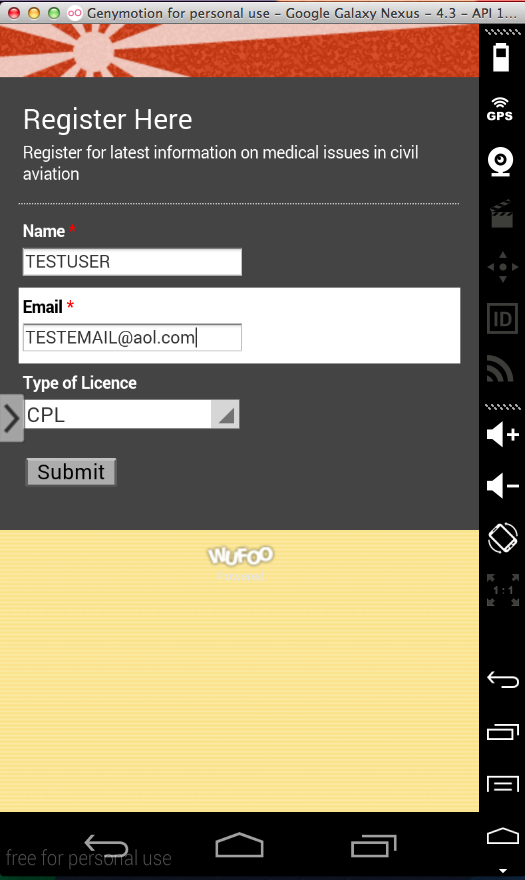
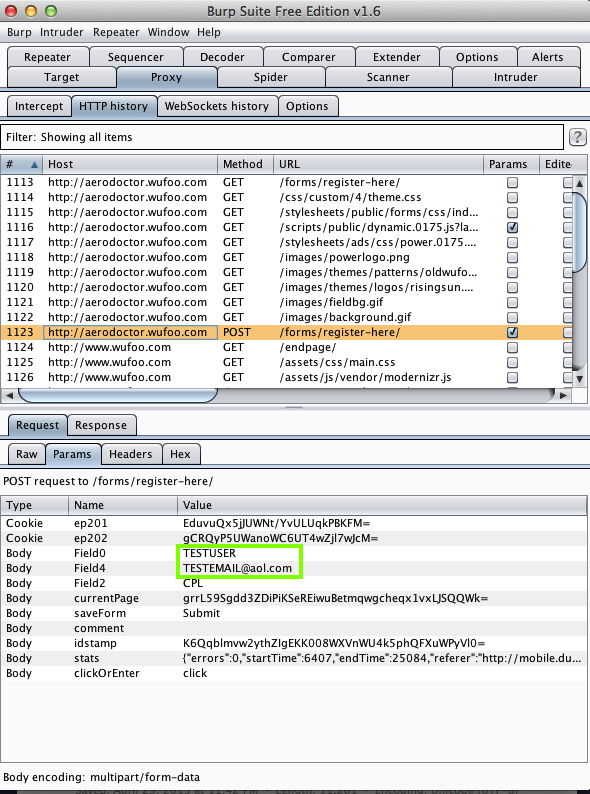
Harvesting them from Burp via MITM attack:
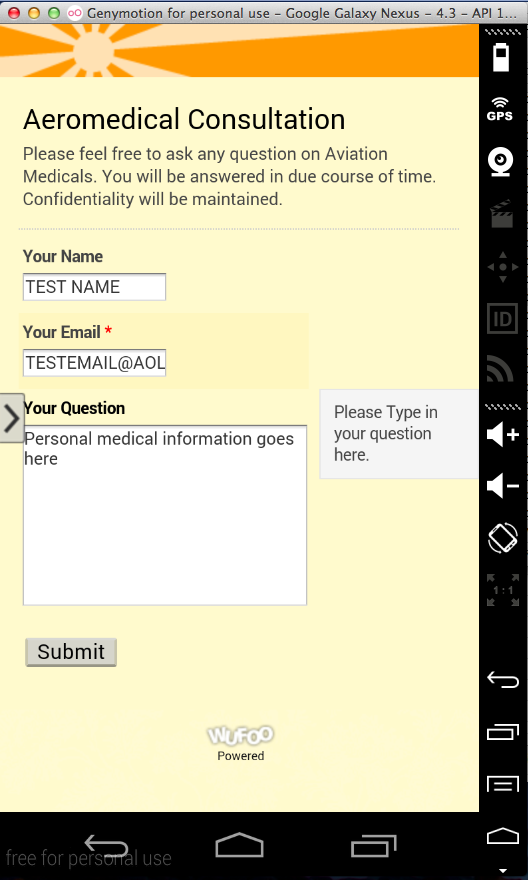
Sending a medical question:
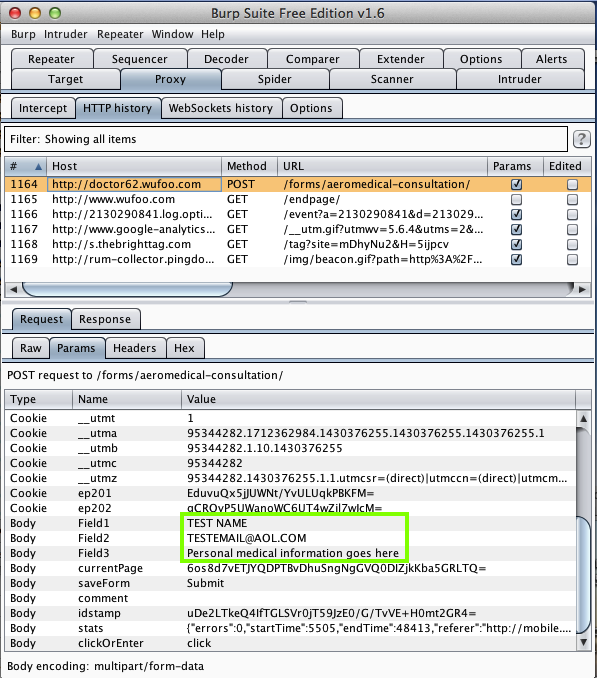
Harvesting personal medical data via MITM attack:
Epiclinic (5 Downloads)
Here's the app:

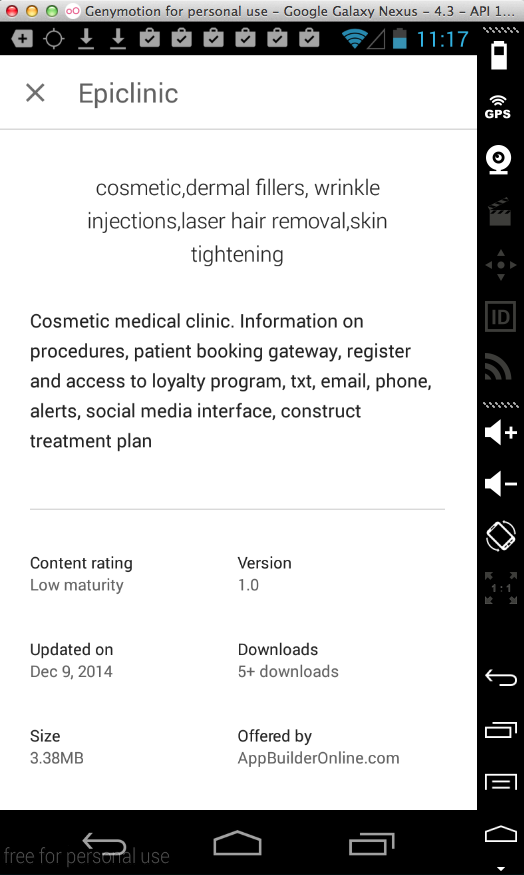
Sending test credentials:
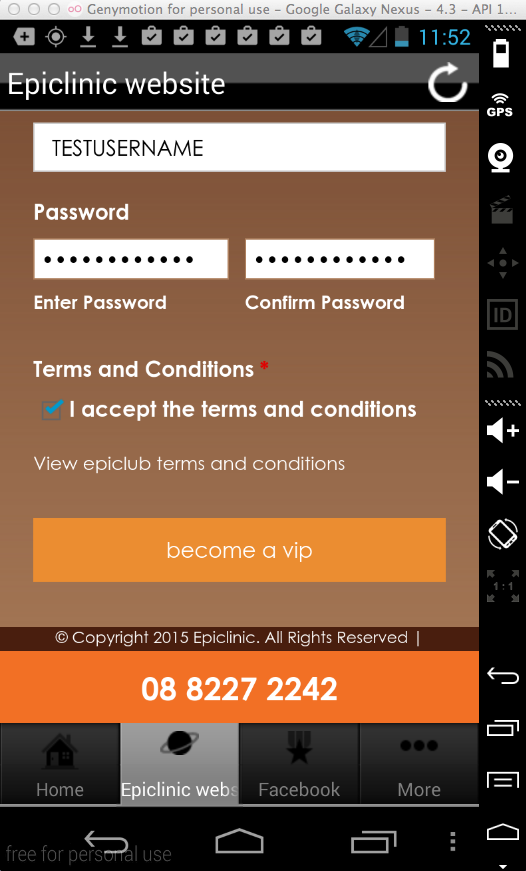
Harvesting them from Burp via MITM attack:
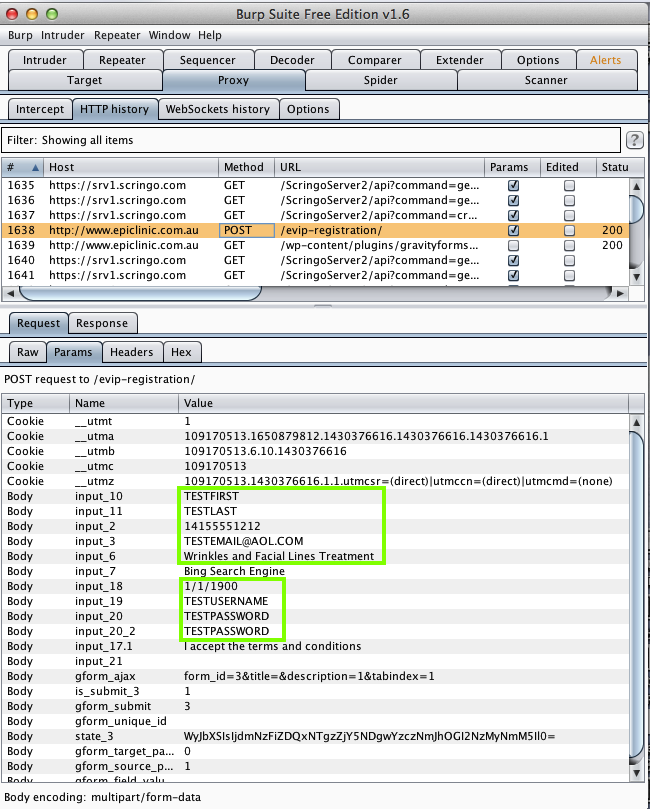
Medical Apps
EyeXam (5000 Downloads)
Here's the app:

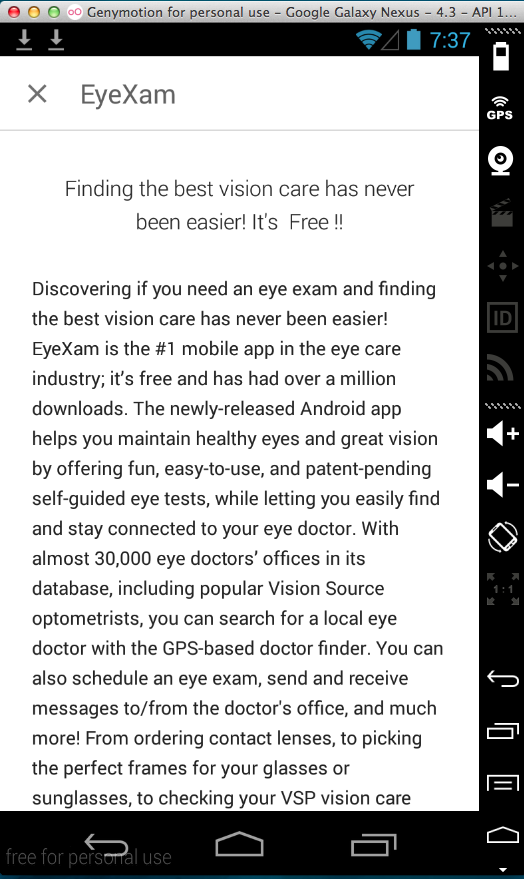
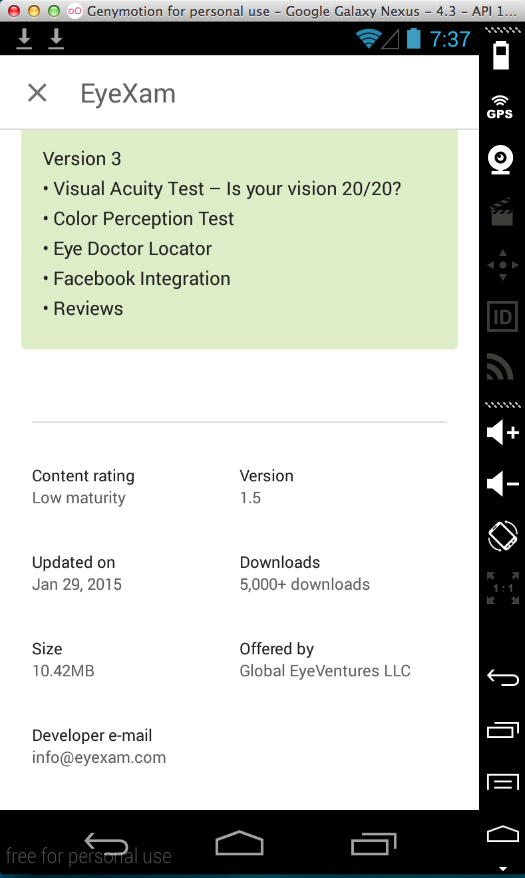
Sending test credentials:
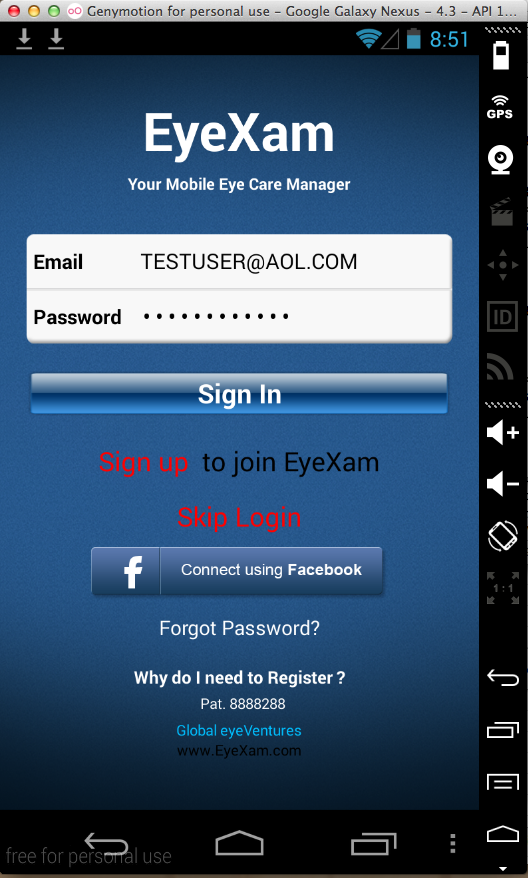
Harvesting them from Burp via MITM attack:
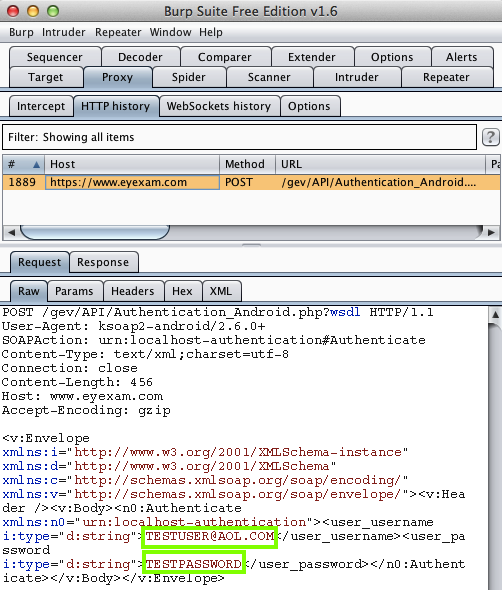
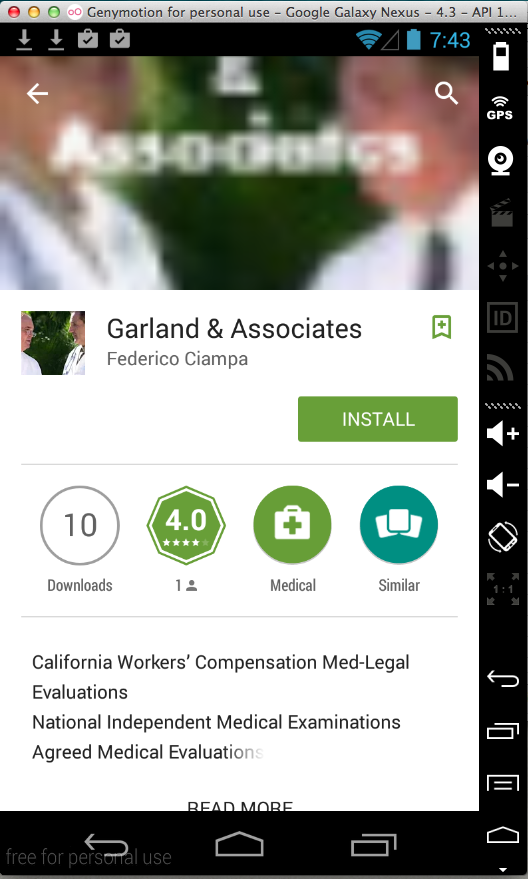
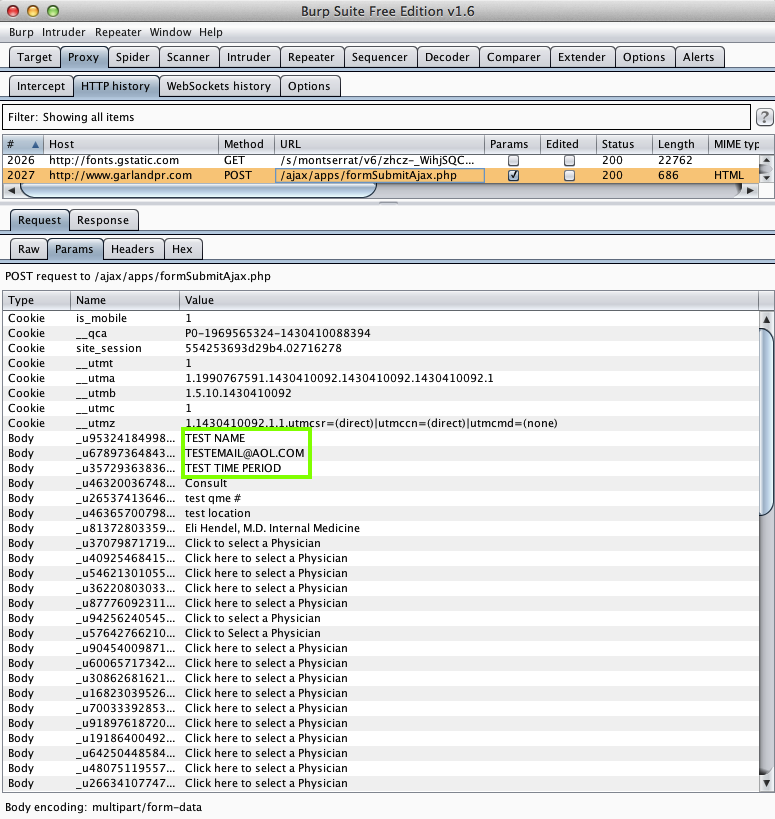
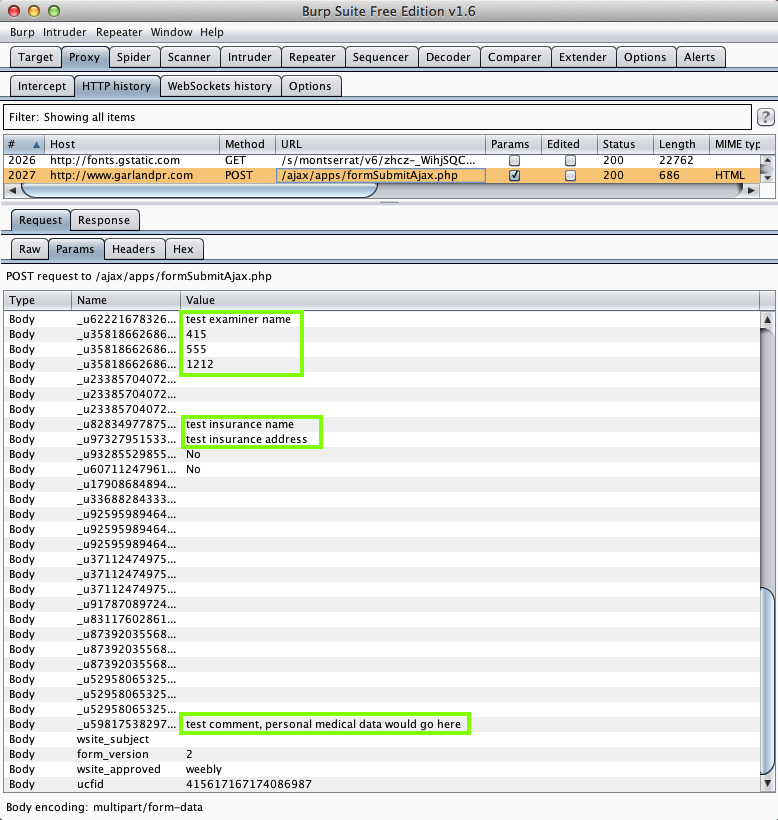
Garland & Associates (10 Downloads)
Here's the app:
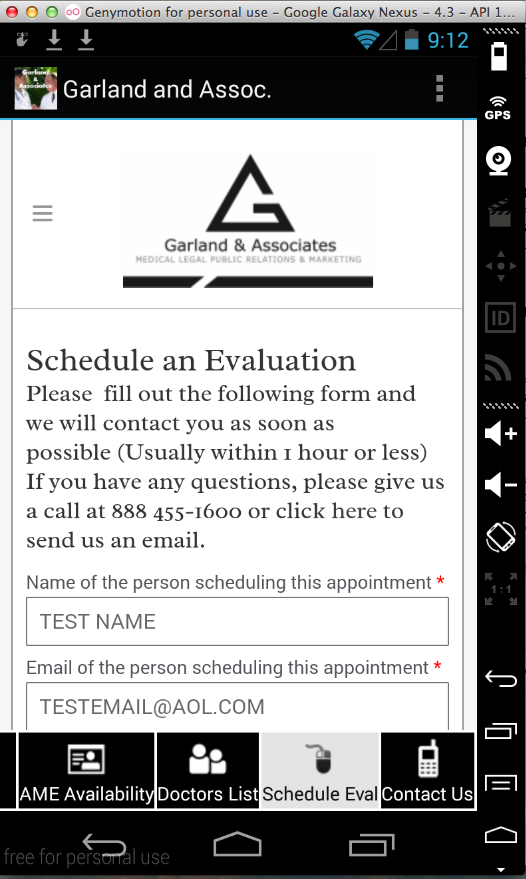
You put your personal medical data in here:
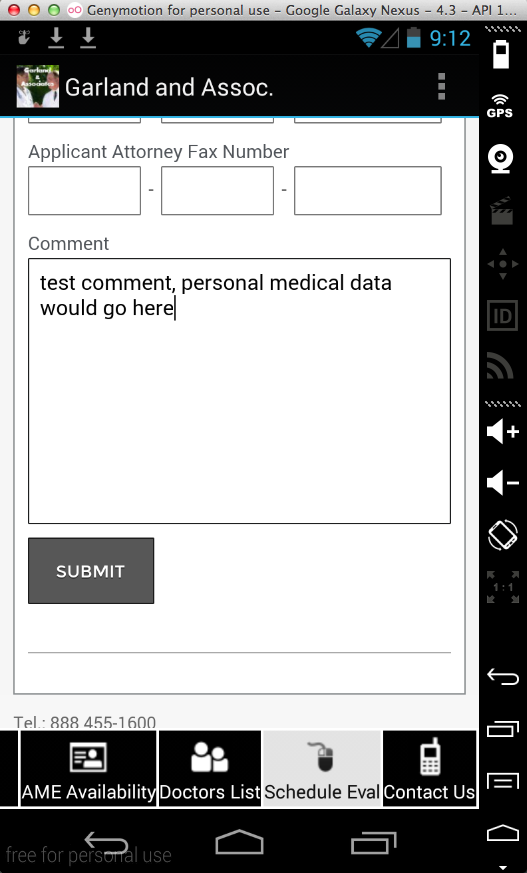
And an attacker in the middle gets it here:
GenieMD (10,000 Downloads)
Vendor Response
GenieMD Tweeted me, saying HIPAA
does not apply to them.:
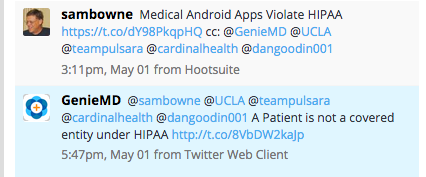
Here are the rules. GenieMD may be
correct, it's not clear to me.

Here's the app:

You are supposed to enter in
personal medical data.
It hasn't been updated since
last year:
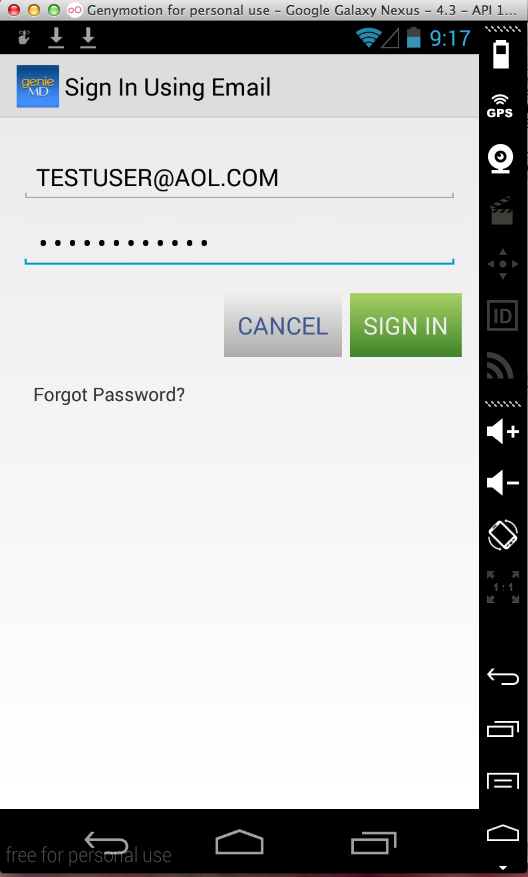
Sending test credentials:
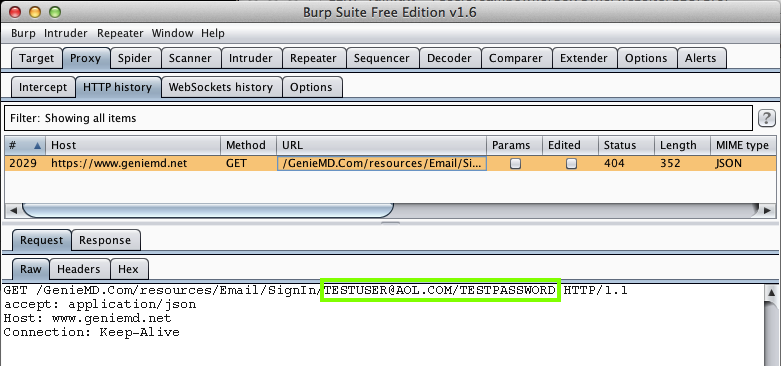
Harvesting them from Burp via MITM attack:
Liver Health - Hepatitis C (500 Downloads)
This is a very strange app from the
NYC Department of Health. It breaks HTTPS,
but seems not to send any data that makes
sense through the broken HTTPS.

It has a questionnaire asking very
sensitive questions:
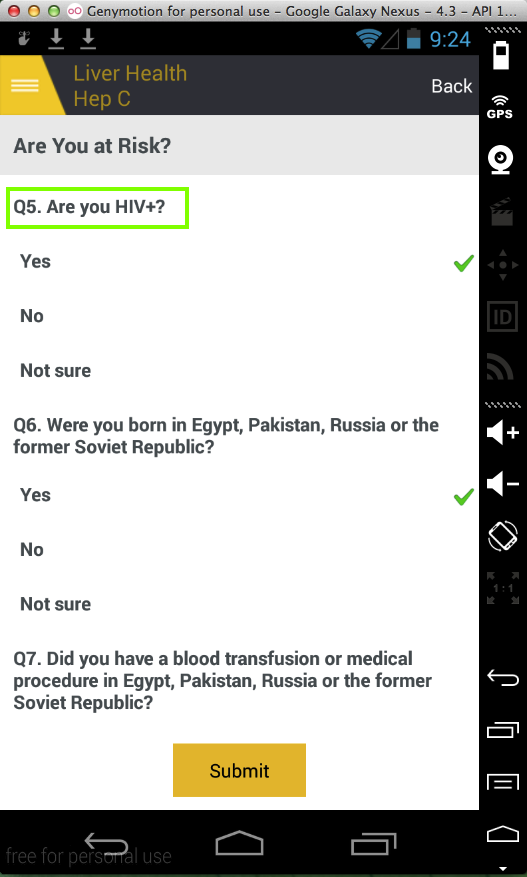
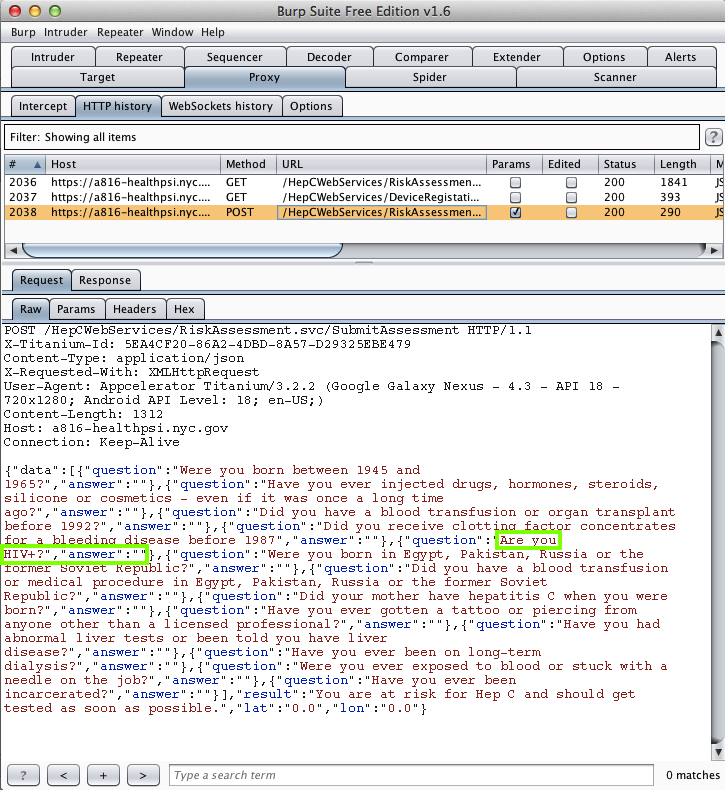
It then sends the questions, but not the
answers, up to the server insecurely,
so the MITM attacker can see them.
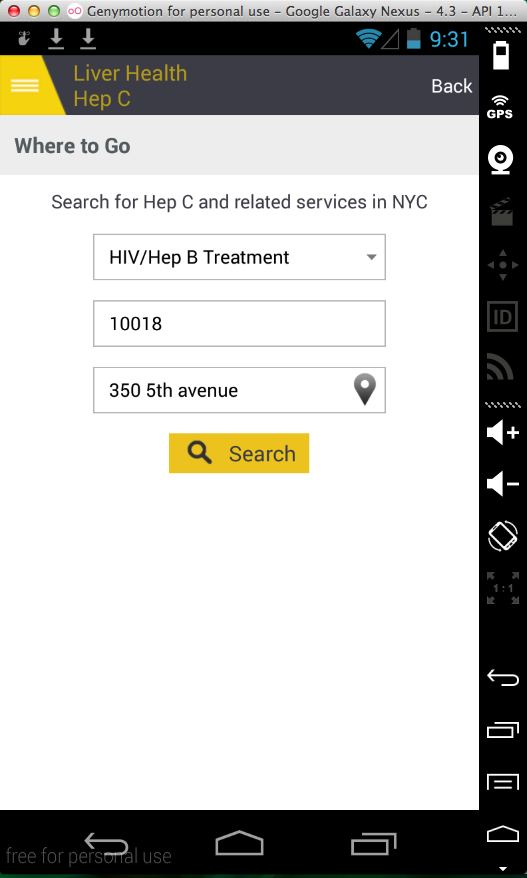
It asks you to search for a clinic, entering
your address:
It sends a latitude and longitude,
which the MITM attacker can see:
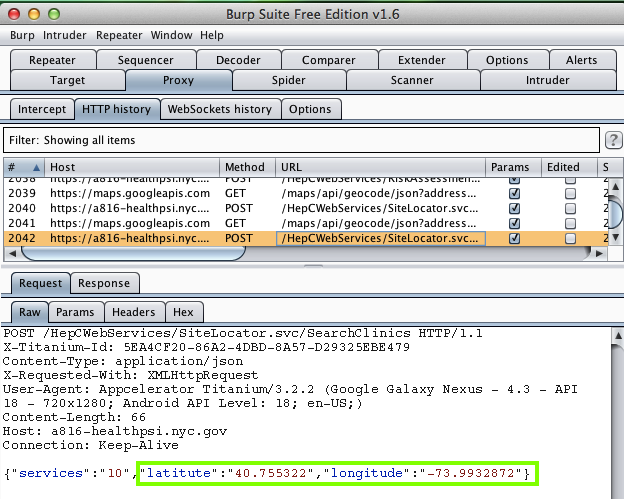
However, the latitude and longitude is
far away from the address I entered:
LowestMed Corporate Rx (1000 Downloads)
Here's the app:

Sending test credentials:
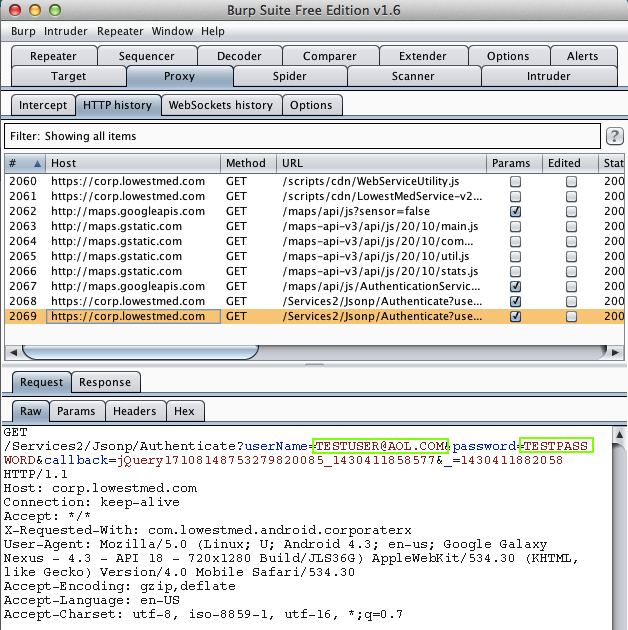
Harvesting them from Burp via MITM attack:
Order Mvi (50 Downloads)
Here's the app--it explicitly claims
to be HIPAA compliant!
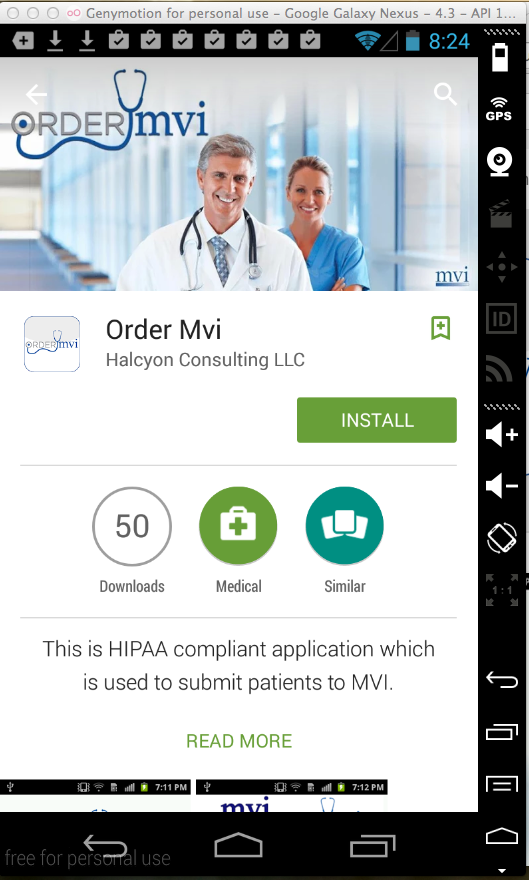
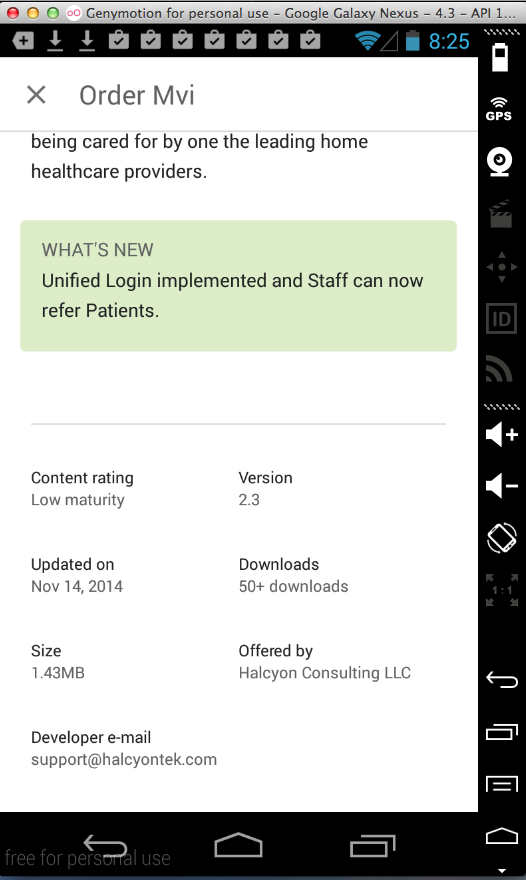
Sending test credentials:
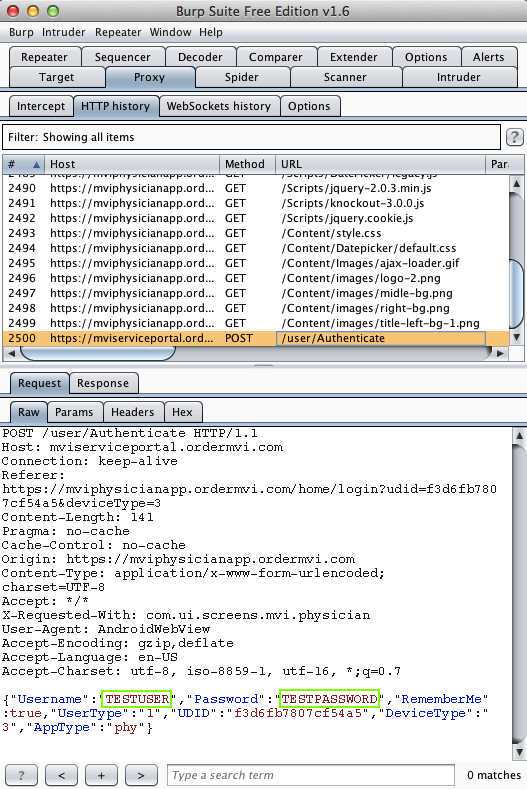
Harvesting them from Burp via MITM attack:
Pain Timer (50 Downloads)
Here's the app:
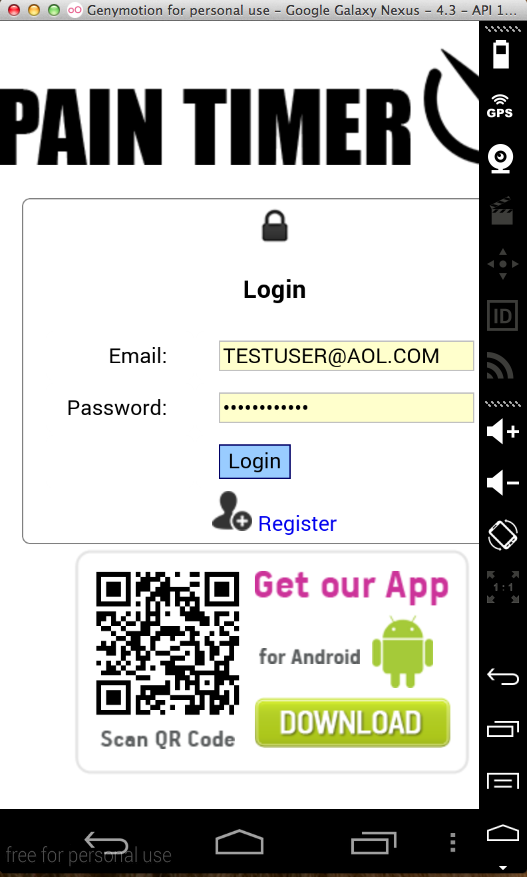
Sending test credentials:
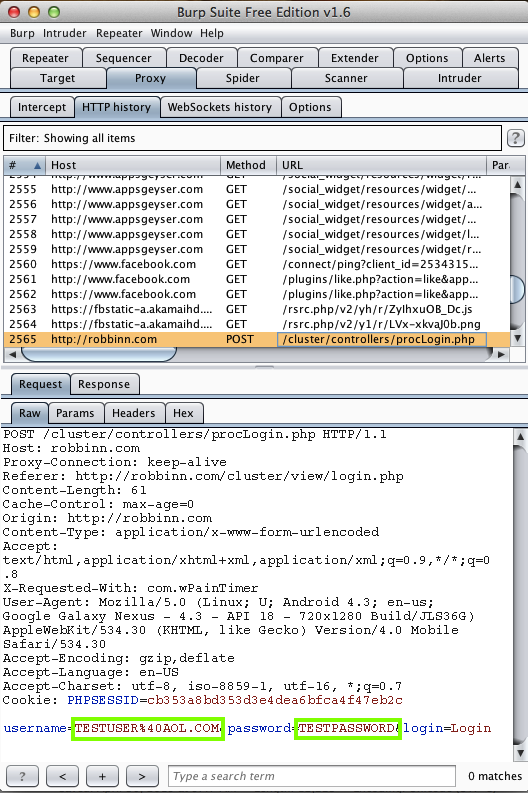
Harvesting them from Burp via MITM attack:
Pharmacy Health Connect (1000 Downloads)
Here's the app:

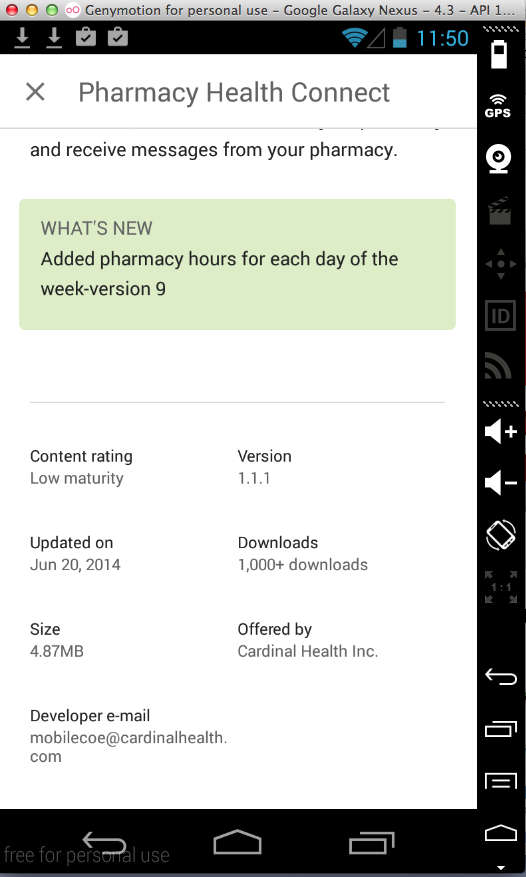
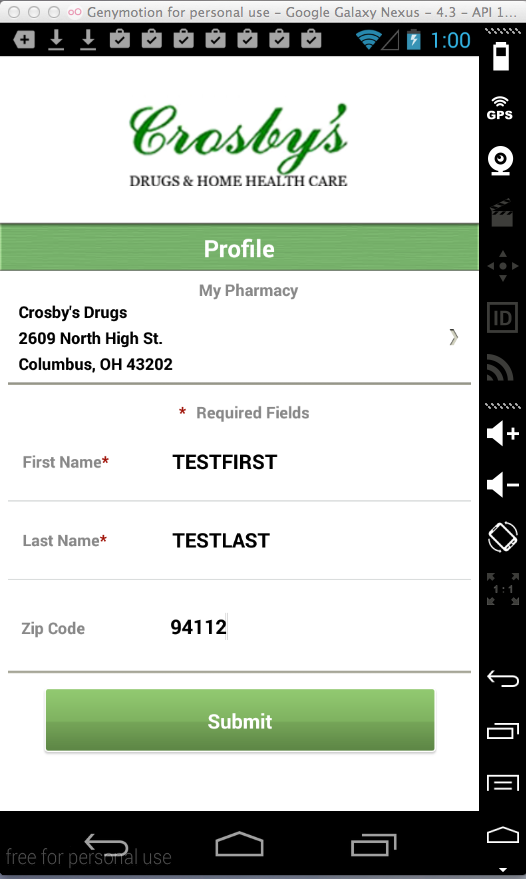
Sending test PII:
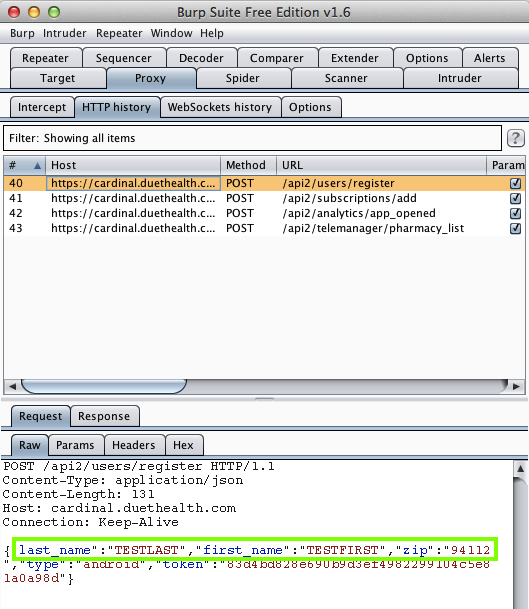
Harvesting them from Burp via MITM attack:
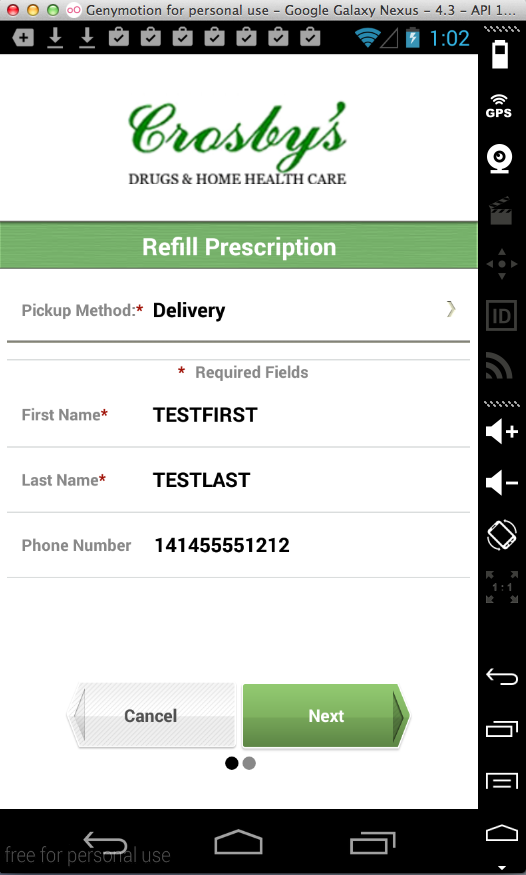
Sending a prescription number:
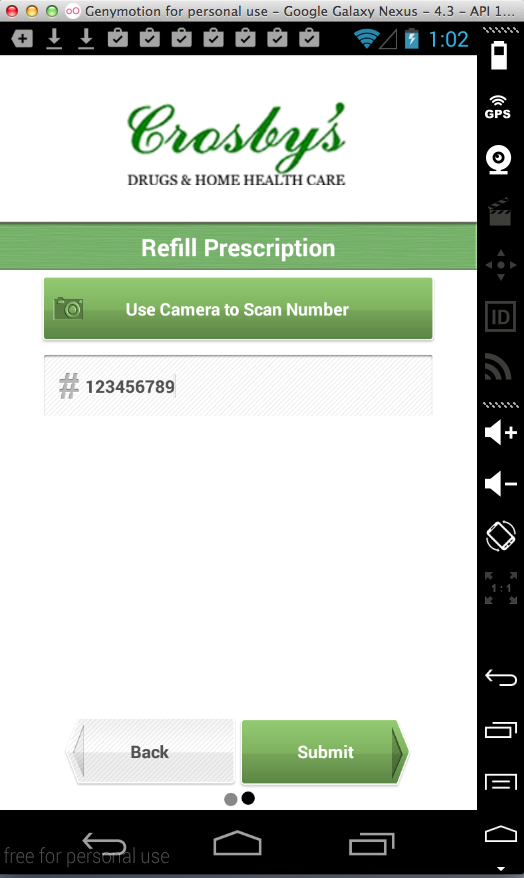
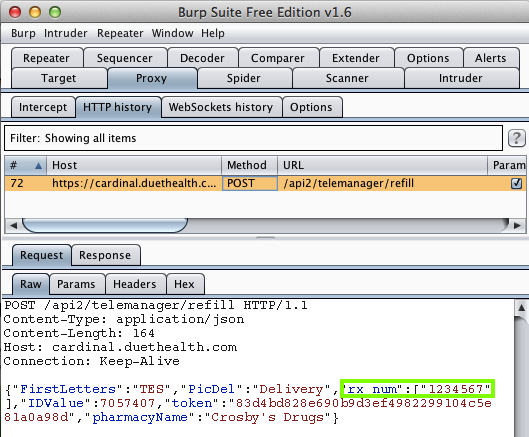
Harvesting the data from Burp via MITM attack:
Pulsara (100 Downloads)
Here's the app:

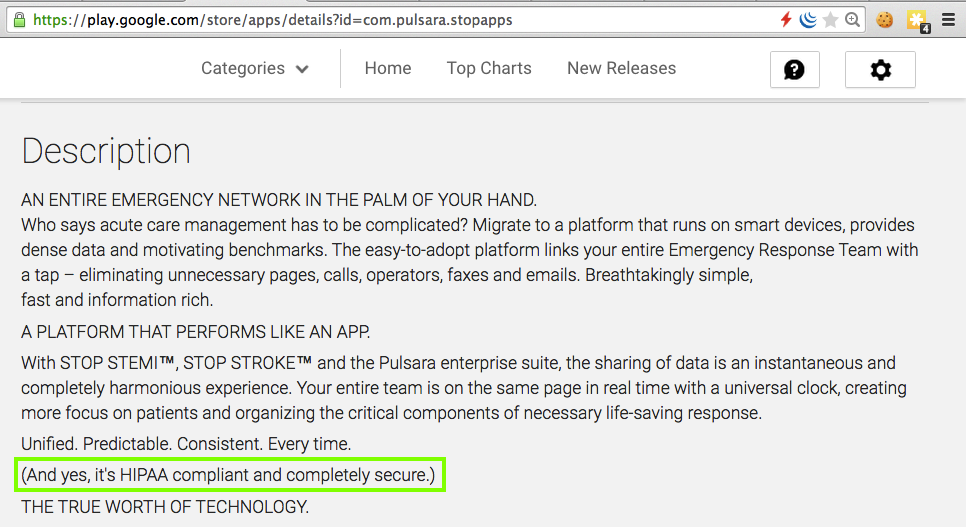
You'll be glad to know this app is
"HIPAA compliant"!
Sending test credentials:

Harvesting them from Burp via MITM attack:
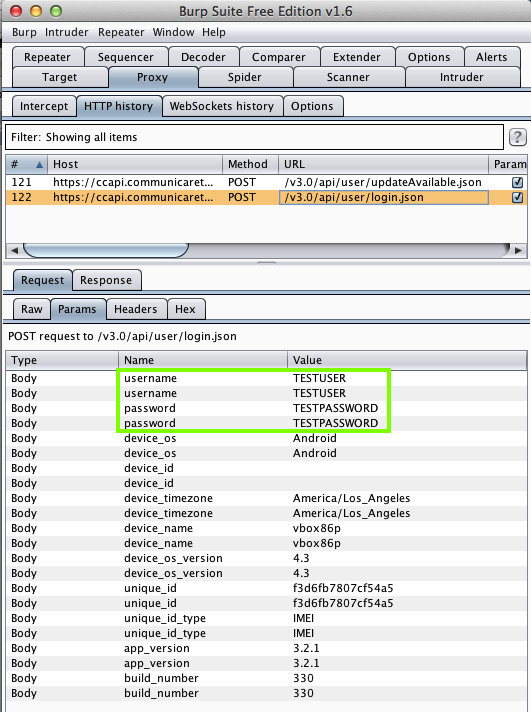
RCEMS Field Guide (1000 Downloads)
Here's the app:
Sending test credentials:
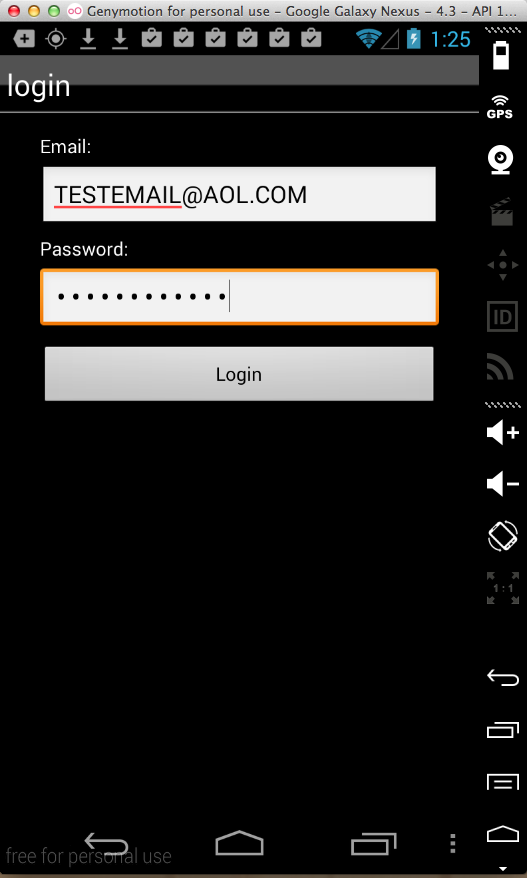
Harvesting them from Burp via MITM attack:
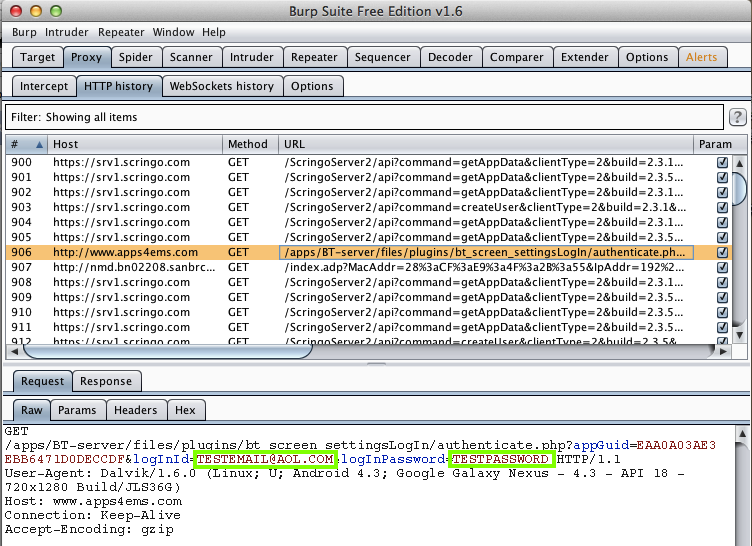
RCP Sacramento (500 Downloads)
Here's the app:

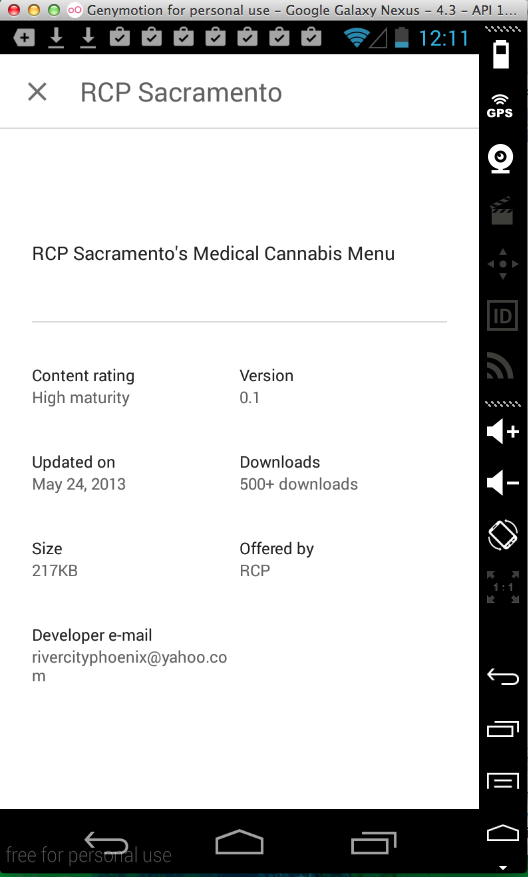
Sending test credentials:
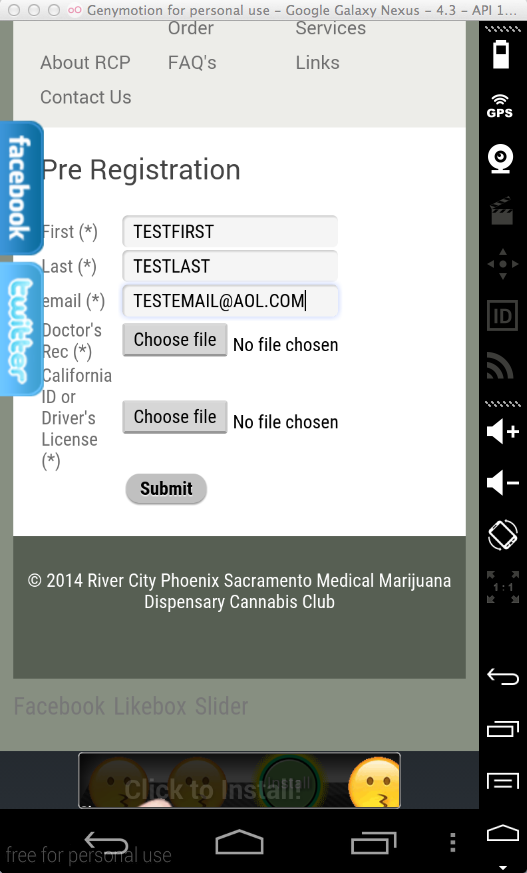
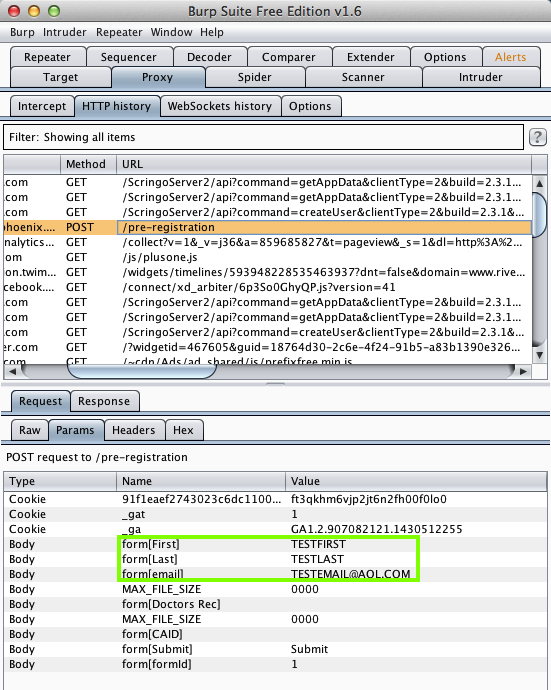
Harvesting them from Burp via MITM attack:
Rx Refills (1000 Downloads)
Here's the app:

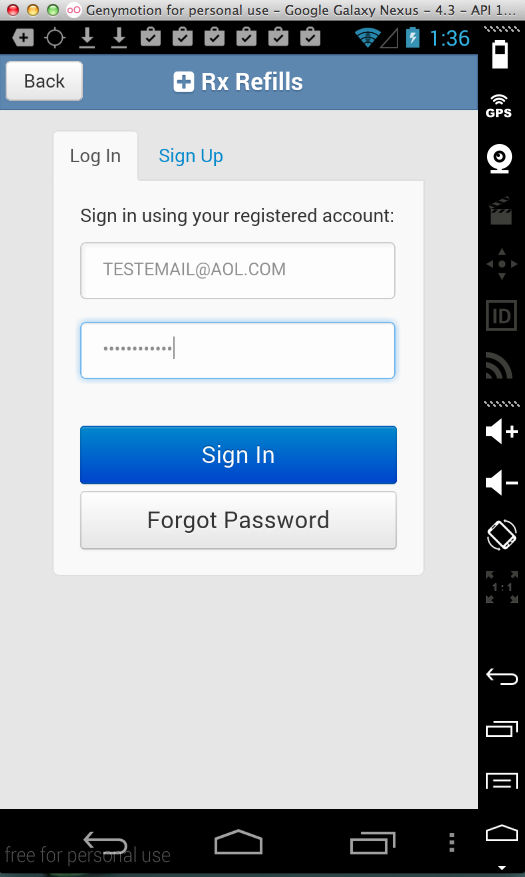
Sending test credentials:
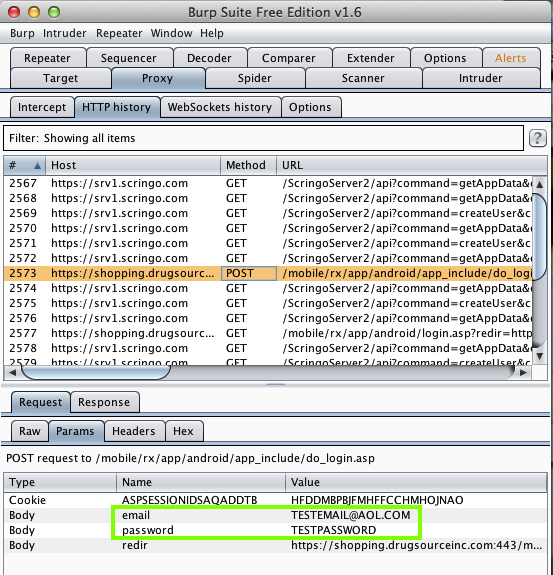
Harvesting them from Burp via MITM attack:
T-Res Fast Clinical Logging (1000 Downloads)
Here's the app:

Sending test credentials:
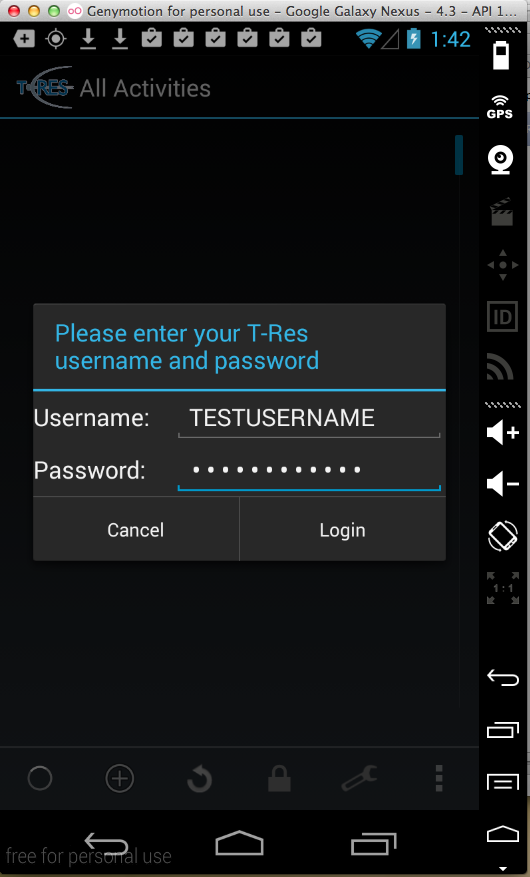
Harvesting them from Burp via MITM attack:
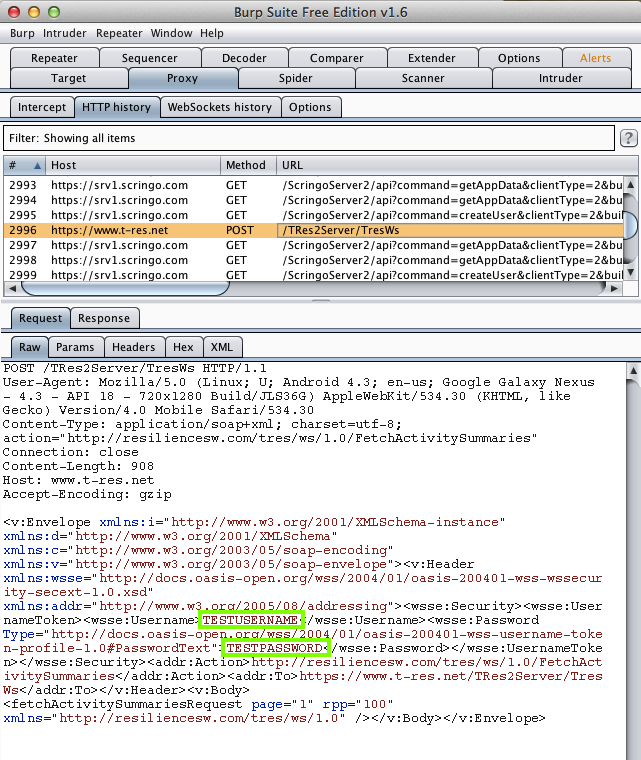
UCLA eIBD (100 Downloads)
Here's the app:
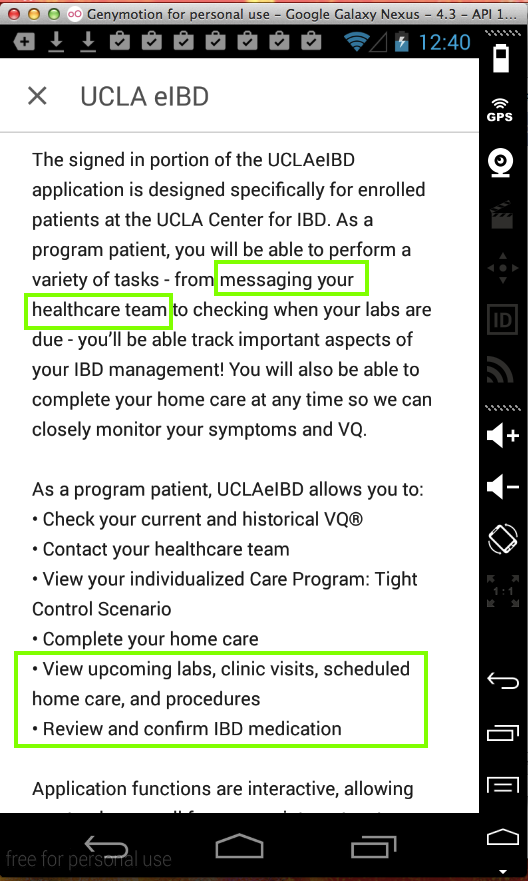
Patients are expected to
use this app for
"messaging your healthcare team"
and other actions using
private healthcare information:
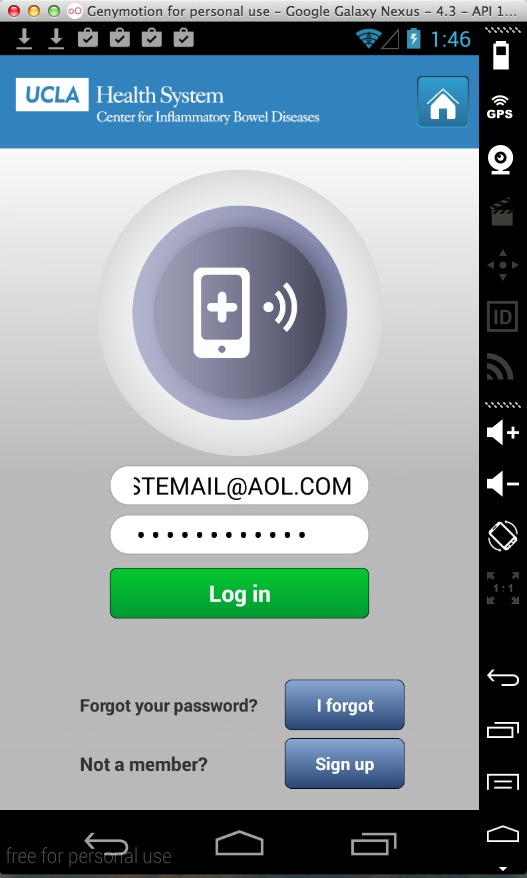
Sending test credentials:
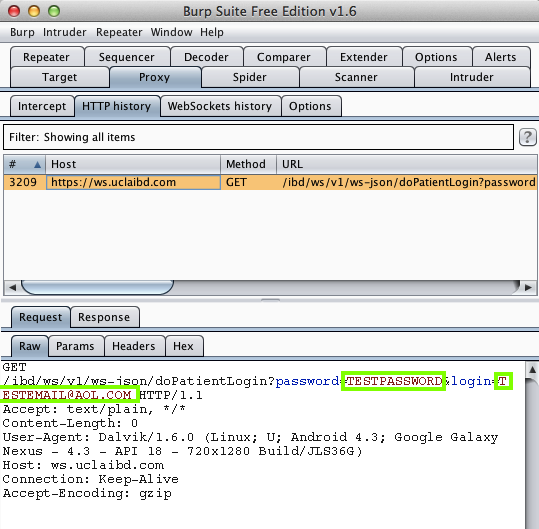
Harvesting them from Burp via MITM attack:
UCLA Health (1000 Downloads)
Here's the app:

This app is intended for patients to
use to "access your health records":
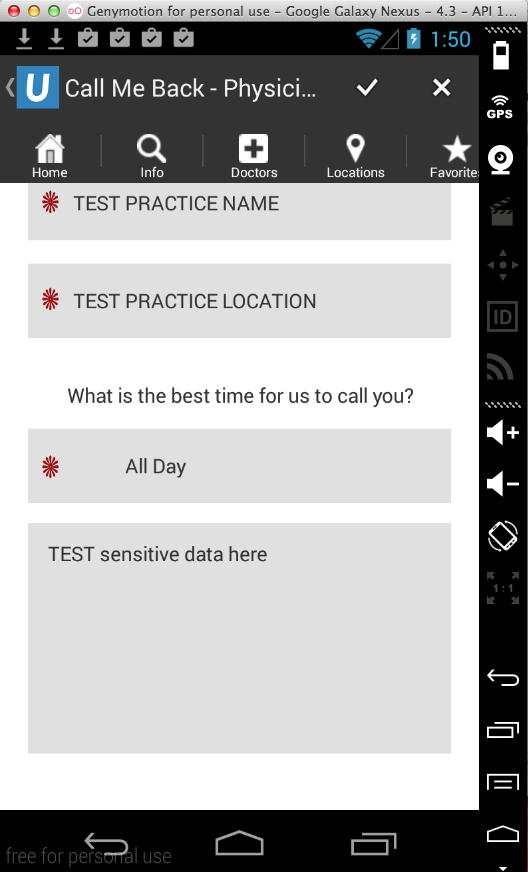
Entering sensitive data into the
app:
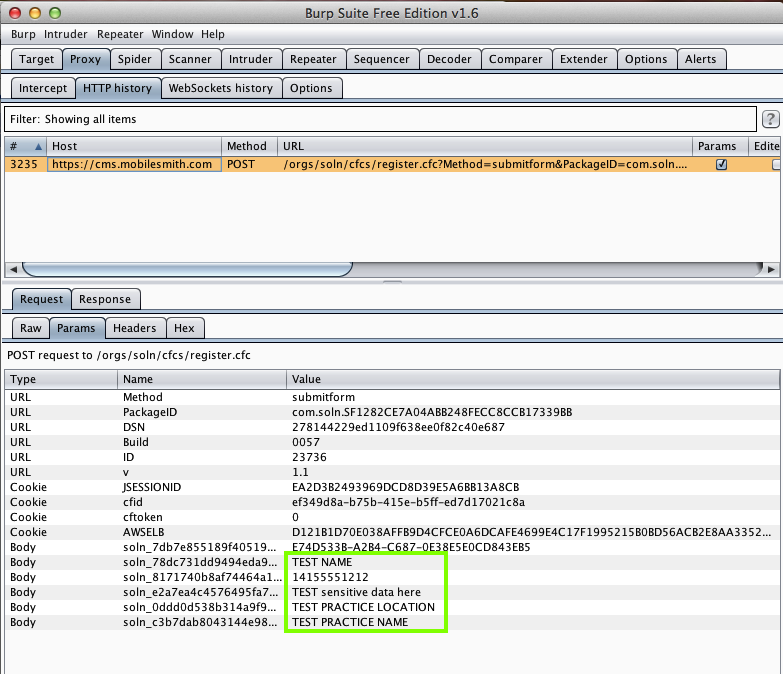
Harvesting it from Burp via MITM attack:
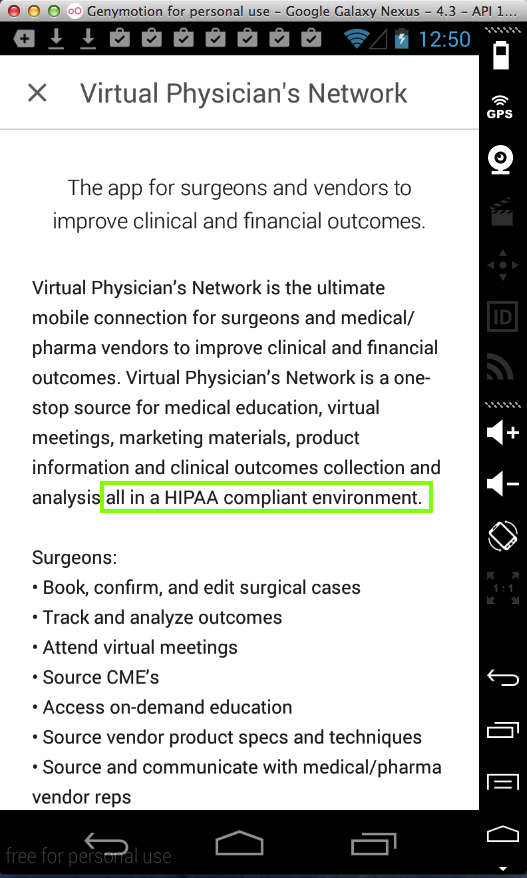
Virtual Physician's Network (1 Download)
Here's the app:
It explicitly claims to be
HIPAA compliant:
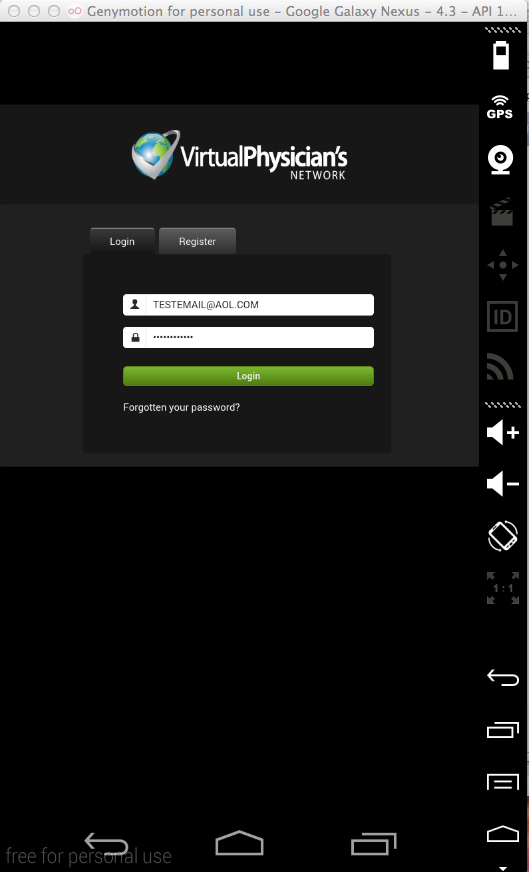
Sending test credentials:
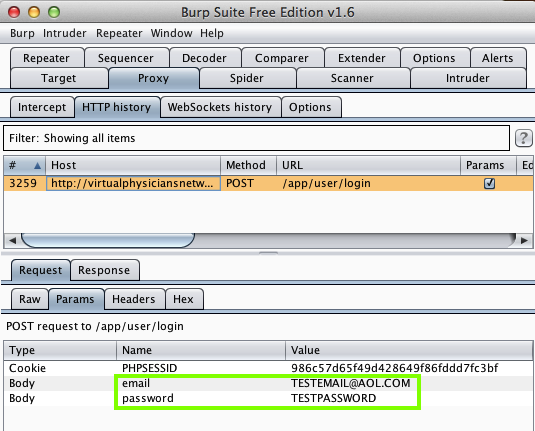
Harvesting them from Burp is
to easy--this app uses HTTP with
no encryption at all!
Posted 4-26-15 5:16 pm by Sam Bowne
More apps added 4-26-15 11:43 pm
More apps added & Somnote explanation changed from OAuth to hashing 4-27-15 1:54 am
On 4-29 at 6:44 PM I added several new items, alphabetically, from AMC through Instamessage (approximately).
Note that Snap Secure fixed the problem added 4-30-15 8:33 pm
Medical apps added 2:33 pm 5-1-15
GemieMD response added 5-2-15 6:53 am
FixIT fix added 5-23-15 12:05 pm
Incorrect Somnote image removed 6-4-15
Missing images added to Pharmacy Health Connect 6-9-15
|
















































































































































































































































