Proj 15. SSDT Hooking (0 pts + 15 pts extra)
What You Need
- The Windows Server 2008 VM handed out by your instructor.
This project can be done on other machines, including Windows 10, but
first you'll need to
install Windbg and LiveKD
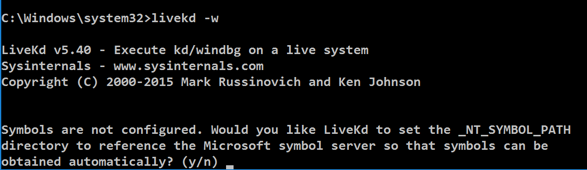
Starting LiveKd
In a Command Prompt window, execute this command:
livekd -w
When Livekd starts, it asks you
whether to set the _NT_SYMBOL_PATH
automatically, as shown below.
Type y and press Enter.
Livekd asks "Enter the folder to which symbols download". Press Enter to accept the default option.
Windbg launches, as shown below.
Introduction to the SSDT
The
System Service Descriptor Table (SSDT)
is a data structure
containing pointers to kernel
routines.
Changing SSDT values is called hooking
and is commonly used by antivirus products
and rootkits to modify system behavior.
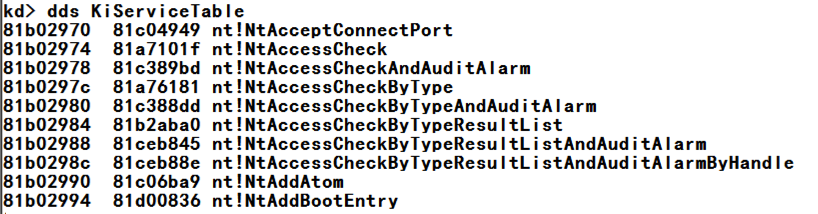
Observing a Clean SSDT
At the bottom of the Command window,
in the command bar, execute this command
to display the start of the SSDT:
dds KiServiceTable
You see the start of the SSDT,
as shown below. There are pointers
here for many kernel routines.
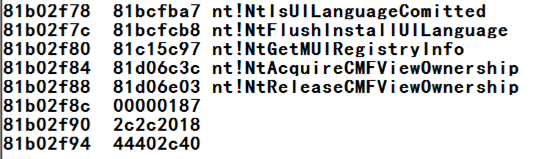
Execute this command
to display the first 18a (hexadecimal)
pointers in the SSDT:
dds KiServiceTable L 18a
You see the end of the SSDT,
as shown below.
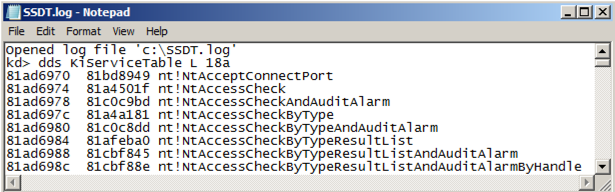
Saving a Log File
You need to save a record of the original,
clean, SSDT.
At the bottom of the Command window,
in the command bar, execute these commands:
.logopen c:\SSDT.log
dds KiServiceTable L 18a
.logclose
In Windows Explorer, navigate to the
C:\SSDT.log file and open
it. It should contain all the SSDT
pointers,
as shown below.
Installing SSDT Hook
Download
SSDTHook.zip
SHA-256: b7ac23d93c0d57a2683ba9391a62987fa363be0b1c9f079349fb90cca7555d77
Unzip it and navigate to the release
folder, as shown below.
Double-click the loader.exe file.
A black command prompt box opens and immediately
closes. This has installed the SSDT hooks.
Examining the SSDT Again
Close the Command Prompt running livekd.
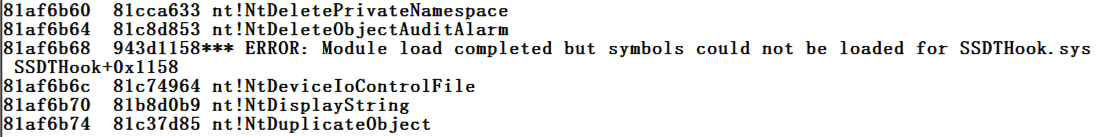
Launch livekd again, and examine the SSDT
again. Now there is an obvious change
at address 81af6b68
as shown below.
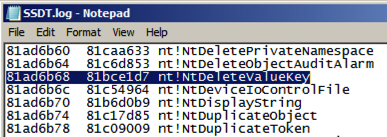
Look in your saved SSDT.log file.
The addresses have changed, but the order of
functions is the same, so you can see that
the hooked function is
nt!NtDeleteValueKey
as shown below.
Find the other hooks to answer the question below.
15.1: Function Name (10 pts)
The first function hooked is
NtDeleteValueKey
Find the name of the fourth hooked function.
Use the form
below to record your score in Canvas.
Unloading the SSDT Hook
The SSDTHook program is not malicious,
just a programming exercise,
so restarting the machine will unload the driver
and restore the SSDT to a clean state.
15.2: Zone Alarm (15 pts extra)
Installing Zone Alarm
Download
zaSuiteSetup_80_298_035_en.exe
SHA-256: 93fb6afaa7961950caa08c89a188b2f37321772821941692a7928f7c796f083a
Install it, with these selections:
- "Install on Unsupported OS?" Yes
- "Installation" Next
- "ZoneAlarm Registration" Uncheck both boxes, Next
- "License Agreement" Check the box, Install
- If a box warns you that this installation will replace MailFrontier Anti-spam software, click OK
- "Please choose your program control security setting" -- accept the default option of "Auto-learn" and click Next
- Click "Do not participate in DefenseNet" and click Next
- Accept the default selection of "Yes - Enable Anti-virus protection" and click Next
- Accept the default selections of "Set up my programs (default)" and "Automatically configure my network settings" and click Next
- Wait for the scan to complete, click Next
- Click "Restart Computer"
Find the name of the fourth hooked function.
Use the form
below to record your score in Canvas.
References
Common WinDbg Commands (Thematically Grouped)
!process
Special Command: Displaying Memory Data Using the d* Command and Its Variations
dds, dps, dqs (Display Words and Symbols)
My first SSDT hook driver
Posted 7-17-17 by Sam Bowne
Integrated with Canvas 9-25-18







