http://samsclass.info/120/proj/p17-https.html
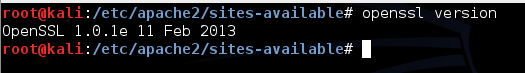
openssl version
Kali Linux uses a vulnerable version!

cd
wget http://samsclass.info/120/proj/hb1.pyx
mv hb1.pyx hb1.py
Troubleshooting
Note that the name of the file is hb and the numeral one, not the letter LIn S214, sometimes it attempts to connect via IPv6 and the download fails. If that happens, force it to use IPv4 with this command:
wget -4 http://samsclass.info/120/proj/hb1.pyx
cd
python hb1.py localhost
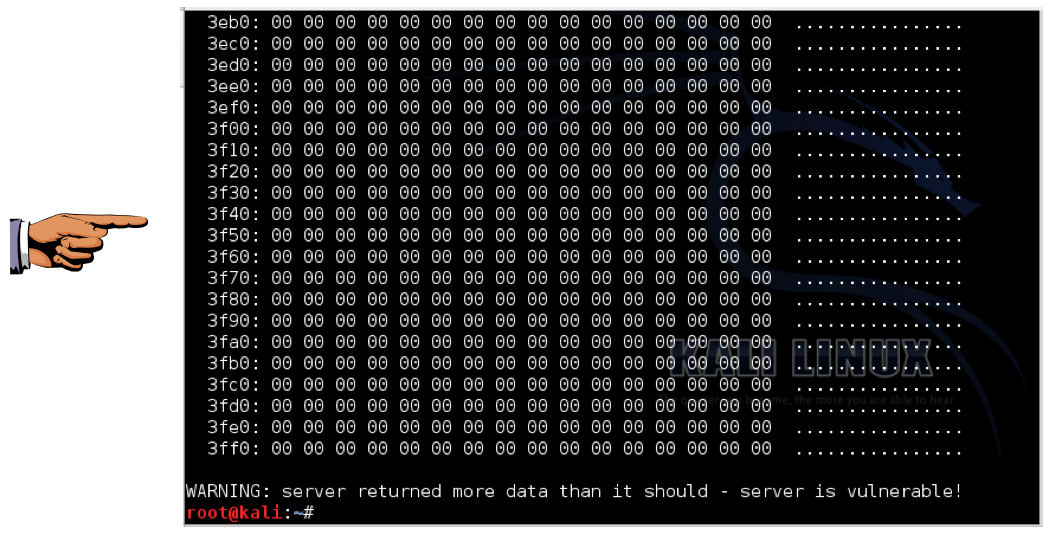
Save a WHOLE DESKTOP CAPTURE with a filename of "Proj 13a from YOUR NAME".
So, as is often the case, you need to download the source and compile it yourself.
(The .configure command is needed to tell OpenSSL to install into the directory Kali expects it to be in.)
wget http://www.openssl.org/source/openssl-1.0.1g.tar.gz
tar xzf openssl-1.0.1g.tar.gz
cd openssl-1.0.1g
./config --prefix=/usr --openssldir=/etc/ssl
make
make install
service apache2 restart
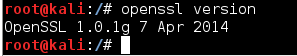
openssl version
cd
python hb1.py localhost
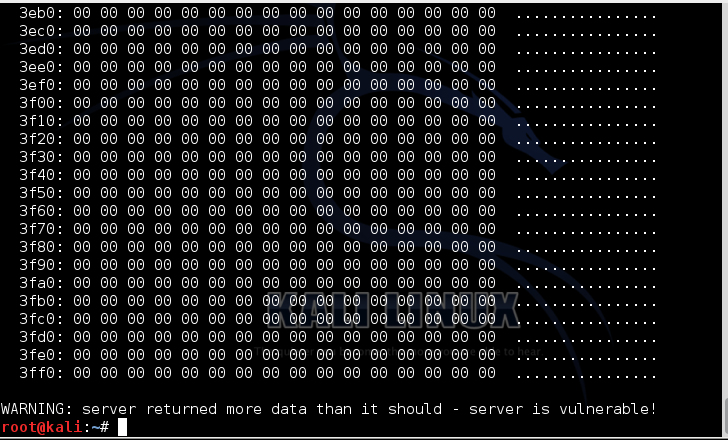
The server should no longer be vulnerable, but it is! Very disconcerting.
At this point, I went to Twitter to ask for help, and got this helpful message:
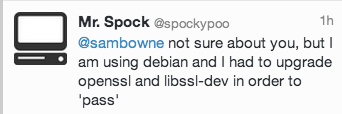
That was correct! Note: you should be on Twitter!
Unfortunately, you can't update libssl-dev until you update libssl, so there are two packages required.
In a Terminal window, execute these commands. When two old-style DOS-looking boxes pop up, click OK
wget http://ftp.us.debian.org/debian/pool/main/o/openssl/libssl1.0.0_1.0.1g-4_i386.deb
dpkg -i libssl1.0.0_1.0.1g-3_i386.deb
wget http://ftp.us.debian.org/debian/pool/main/o/openssl/libssl-dev_1.0.1g-4_i386.deb
dpkg -i libssl-dev_1.0.1g-3_i386.deb
Troubleshooting
If the wget commands don't work, it is likely that the version number has changed. Open a Web browser and go to this URL:http://ftp.us.debian.org/debian/pool/main/o/openssl/
Look at the packages carefully and see what the new version number is. The most likely change is that the number before "_i386" has increased to 5 or 6.
service apache2 restart
cd
python hb1.py localhost
Save a WHOLE DESKTOP CAPTURE with a filename of "Proj 13b from YOUR NAME".
Email the image to cnit.120@gmail.com with a subject of "Project 13 from YOUR NAME".
http://ubuntuforums.org/showthread.php?t=1672775
http://mariobrandt.de/archives/linux/upgrading-openssl-on-debian-6-squeeze-or-ubuntu-8-04-hardy-456/