
I saw that @rjacksix did an interesting project finding keylogger data on Pastebin, so I decided to search there myself and see what I could find.
I found several lists of vulnerable websites, with proof-of-concept URLs.
I am not willing to perform unauthorized scans of sites, for legal and ethical reasons. But in this situation I have thousands of sites which have already been scanned by others, and have had their vulnerabilities posted publicly. What is the best response?
It seemed to me that it would be good to alert these companies. And since the data was already public and already in the hands of unethical hackers, there is no reason to be concerned about sending information via unencrypted email about them.
I have been told that it is pointless to tell people about vulnerabilities with a "cold" email from a stranger. People have said that such alerts could result in me being blamed for attacking the sites, accused of being a spammer, etc.
But I am confident that alerting these companies is legal and ethical, so I decided to perform a research project to test that claim.
I located 23 vulnerable URLs. I visited each site and examined the "Contact Us" information to find a contact form or email address. I then sent each site a message like this:
You have a serious security problem on your Web site, and someone published it on Pastebin months ago. This is an open SQL injection:http://www.redacted.com...
I found it here:
http://pastebin.com/redacted
There are several others listed there.
You need to fix it immediately. SQL injection is very dangerous--hackers can use it to steal your data, change it, deface your website, steal your passwords and take control of the server, etc.
Feel free to contact me if I can be of assistance.
Sam Bowne
Professor, Computer Networking and Information Technology
City College San Francisco


8:33 am Weds., June 29, 2011
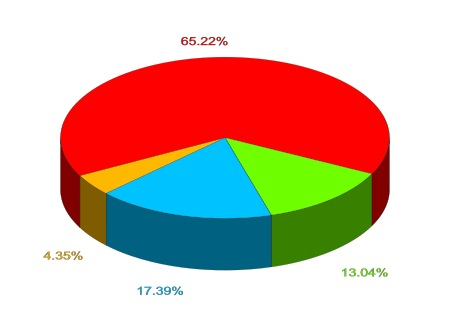
15 No reply, still vulnerable
1 Replied, still vulnerable
4 No reply, fixed
3 Replied, fixed
---
23 Total
So 7/23 sites are fixed. I regard this as encouraging, and I intend to continue alerting people. I will update this page with future developments.
All the replies were polite and appreciative. No one involved has complained to me at all.
Sam Bowne, sbowne@ccsf.edu