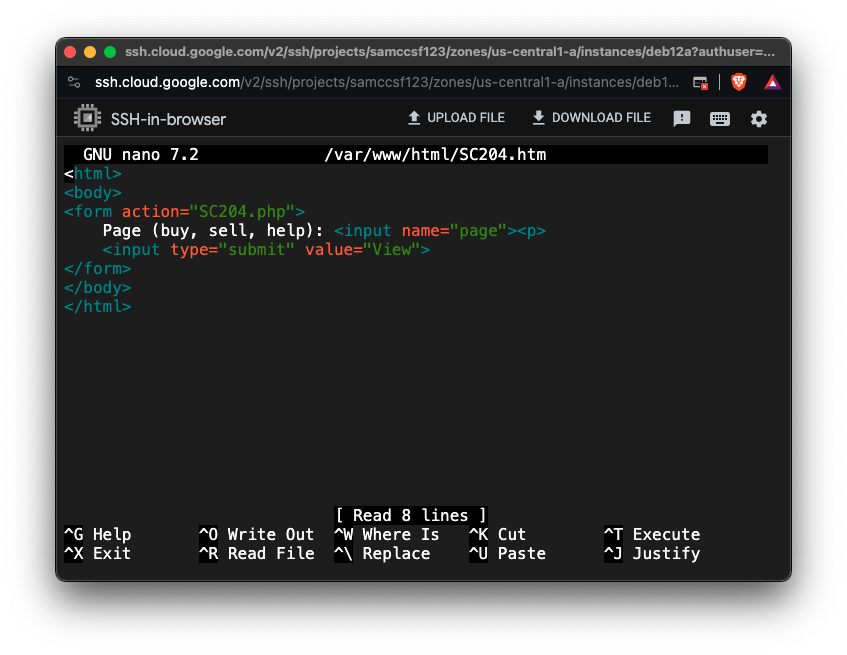
sudo nano /var/www/html/SC204.htm
<html>
<body>
<form action="SC204.php">
Page (buy, sell, help): <input name="page"><p>
<input type="submit" value="View">
</form>
</body>
</html>

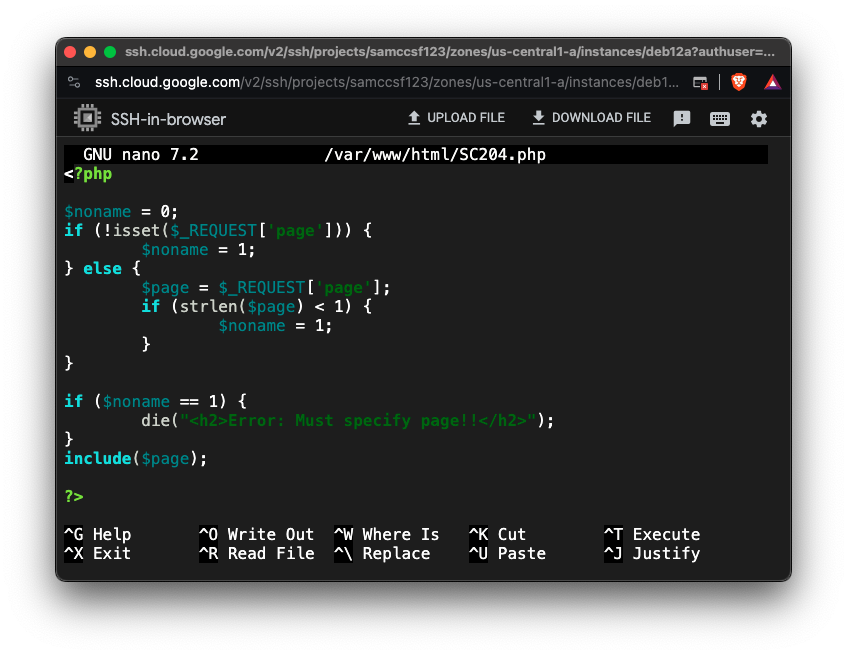
sudo nano /var/www/html/SC204.php
<?php
$noname = 0;
if (!isset($_REQUEST['page'])) {
$noname = 1;
} else {
$page = $_REQUEST['page'];
if (strlen($page) < 1) {
$noname = 1;
}
}
if ($noname == 1) {
die("<h2>Error: Must specify page!!</h2>");
}
include($page);
?>
Save the file with Ctrl+X, Y, Enter.
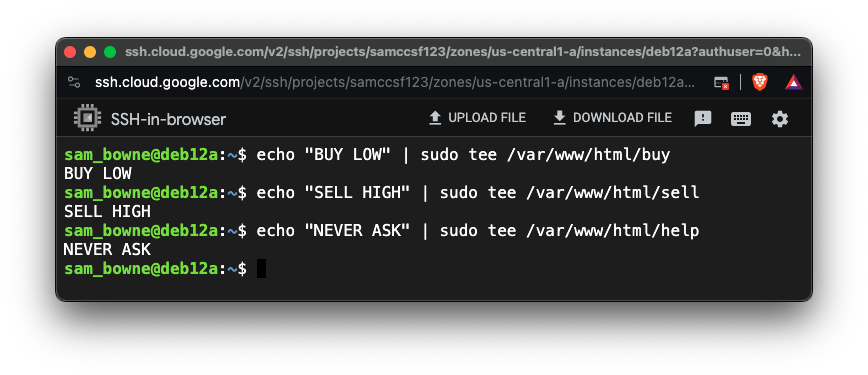
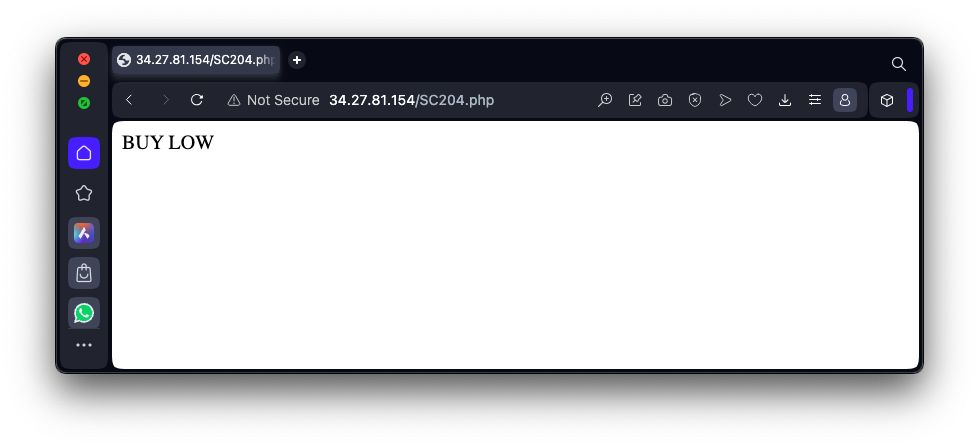
echo "BUY LOW" | sudo tee /var/www/html/buy
echo "SELL HIGH" | sudo tee /var/www/html/sell
echo "NEVER ASK" | sudo tee /var/www/html/help
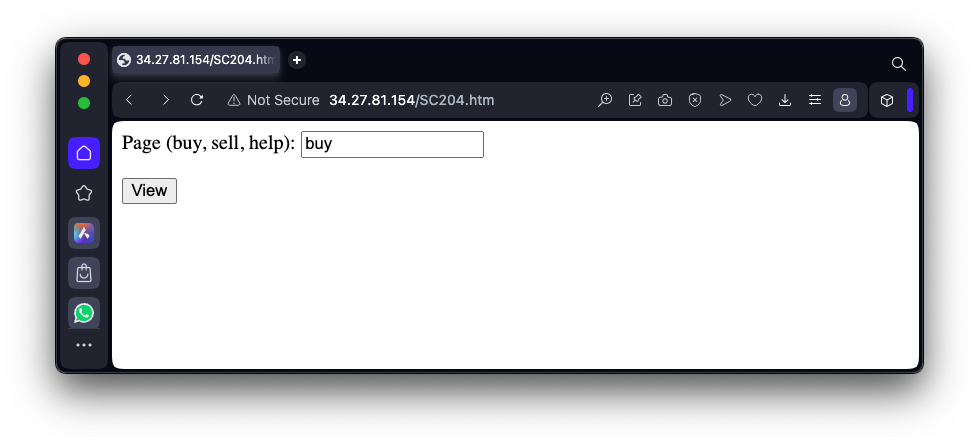
http://35.222.29.122/SC204.htmEnter a Page of buy into the form, as shown below, and click the View button.
https://samlols.samsclass.info/SC/SC204.htmEnter the URL to your PHP page in the form for flag SC 204.1, as shown below, and click the Submit button.
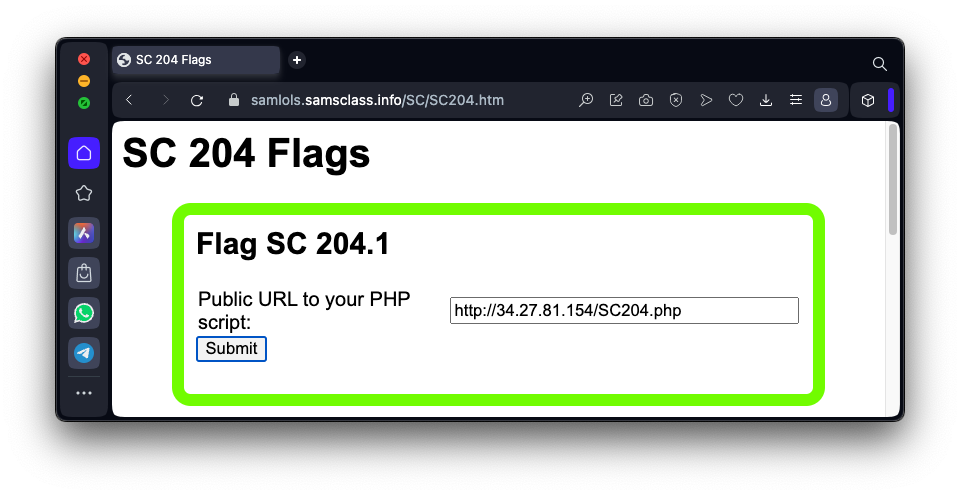
Flag SC 204.1: Database Functionality (5 pts)
The flag appears, as shown below.
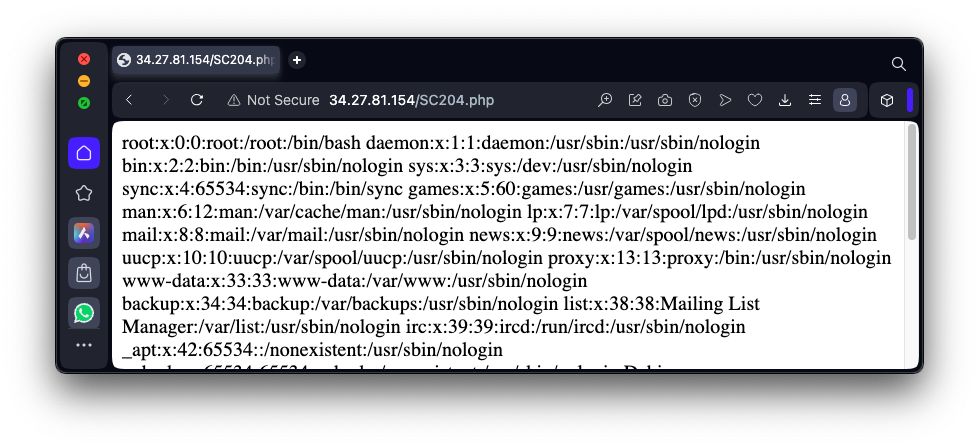
http://35.222.29.122/SC204.htmEnter this page into the form:
../../../etc/passwdas shown below, and click the View button.
Note: "/etc/passwd" caused the PHP server to hang at Collin College in July, 2024, because the campus network filtered it out. If that happens, use /etc/group instead.

This demonstrates a file inclusion vulnerability--the user's input can reference files that were not intended to be displayed.
../I recommend using the str_replace function. Test your script on your own HTML form.
When it's working, run the test in the box below to get the flag.
Flag SC 204.2: Removing Bad Characters (10 pts)
In a Web browser, open this page:
https://samlols.samsclass.info/SC/SC204.htmEnter the URL to your PHP page in the form for flag SC 204.2 and submit the form. If your code is correct, the flag will appear.
http://35.222.29.122/SC204.htmEnter this page into the form:
/etc/passwdThe next page shows the passwd file, because removing "../" doesn't stop this attack.
When it's working, run the test in the box below to get the flag.
Flag SC 204.3: Real Path (20 pts)
In a Web browser, open this page:
https://samlols.samsclass.info/SC/SC204.htmEnter the URL to your PHP page in the form for flag SC 204.3 and submit the form. If your code is correct, the flag will appear.
Posted 3-29-24
/etc/group tip added 7-18-24