sudo apt update
sudo apt install -y mariadb-server mariadb-client php-mysqli
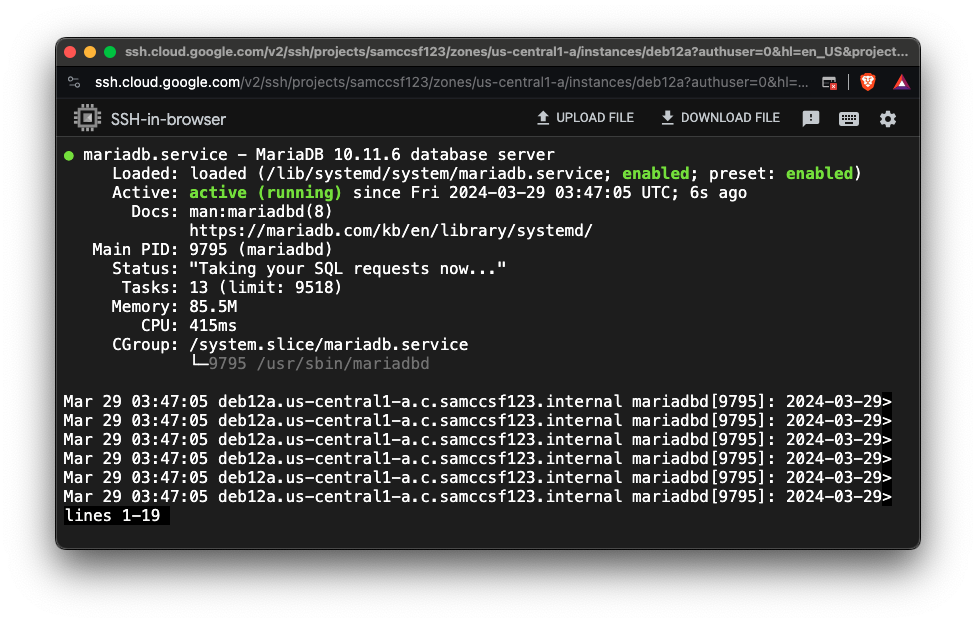
sudo systemctl status mariadb

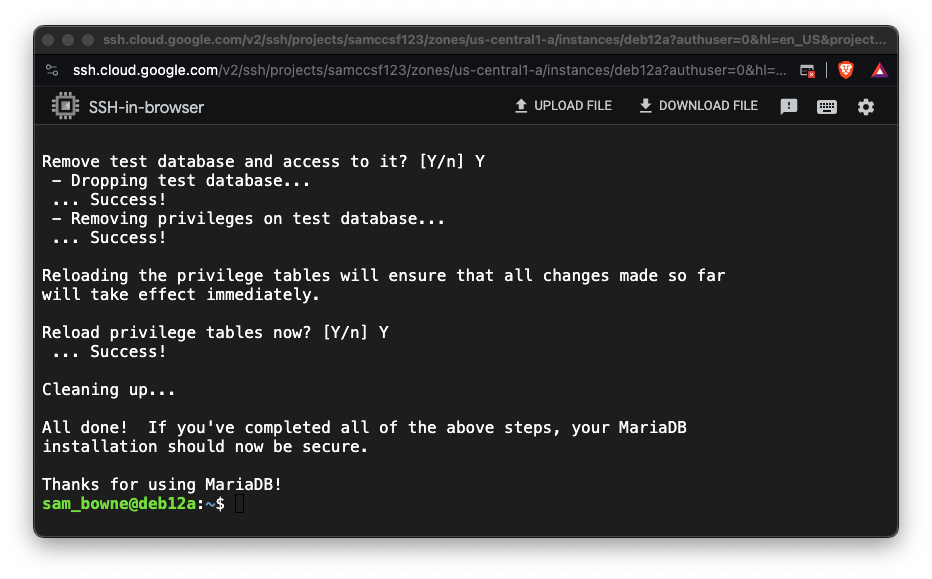
sudo mysql_secure_installation
sudo mysql -u root -p
At the MariaDB prompt, execute these commands, as shown below:
CREATE DATABASE acmeDB;
CREATE USER 'localadmin'@localhost IDENTIFIED BY 'P@ssw0rd1';
GRANT ALL PRIVILEGES ON acmeDB.* TO 'localadmin'@localhost;
FLUSH PRIVILEGES;
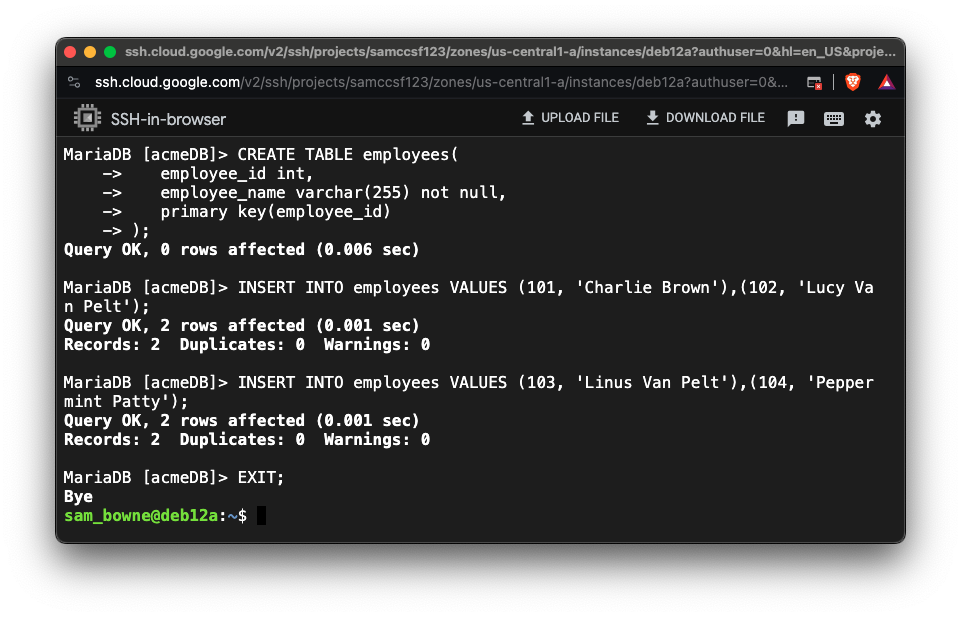
USE acmeDB;
CREATE TABLE employees(
employee_id int,
employee_name varchar(255) not null,
primary key(employee_id)
);
INSERT INTO employees VALUES (101, 'Charlie Brown'),(102, 'Lucy Van Pelt');
INSERT INTO employees VALUES (103, 'Linus Van Pelt'),(104, 'Peppermint Patty');
EXIT;
We want them, however, to create a vulnerable app.
On your cloud Linux server, edit your configuration file, with a command like this:
sudo nano /etc/php/8.2/apache2/php.ini
extension=mysqli

sudo service apache2 restart
sudo nano /var/www/html/SC203.htm
<html>
<body>
<form action="SC203.php">
ID: <input name="id">
Name: <input name="name"><p>
<input type="submit" value="Search">
</form>
</body>
</html>

sudo nano /var/www/html/SC203.php
<?php
$noname = 0;
if (!isset($_REQUEST['name'])) {
$noname = 1;
} else {
$name = $_REQUEST['name'];
if (strlen($name) < 1) {
$noname = 1;
}
}
$noid = 0;
if (!isset($_REQUEST['id'])) {
$noid = 1;
} else {
$id = $_REQUEST['id'];
if (strlen($id) < 1) {
$noid = 1;
}
}
if (($noname == 1) and ($noid==1)) {
die("<h2>Error: Must specify either name or id!!</h2>");
}
$servername = "localhost";
$username = "localadmin";
$password = "P@ssw0rd1";
$db = "acmeDB";
// Create connection
$conn = mysqli_connect($servername, $username, $password,$db);
// Check connection
if (!$conn) {
die("Connection failed: " . mysqli_connect_error());
}
echo "Connected successfully!";
// Search the database
if ($noname == 0) {
$result = mysqli_query($conn, "SELECT * FROM employees WHERE employee_name='$name'");
} else {
$result = mysqli_query($conn, "SELECT * FROM employees WHERE employee_id=$id");
}
echo "<h2>Results</h2>";
while ($row = $result->fetch_row()) {
printf("%s %s<br>\n", $row[0], $row[1]);
}
?>
Save the file with Ctrl+X, Y, Enter.

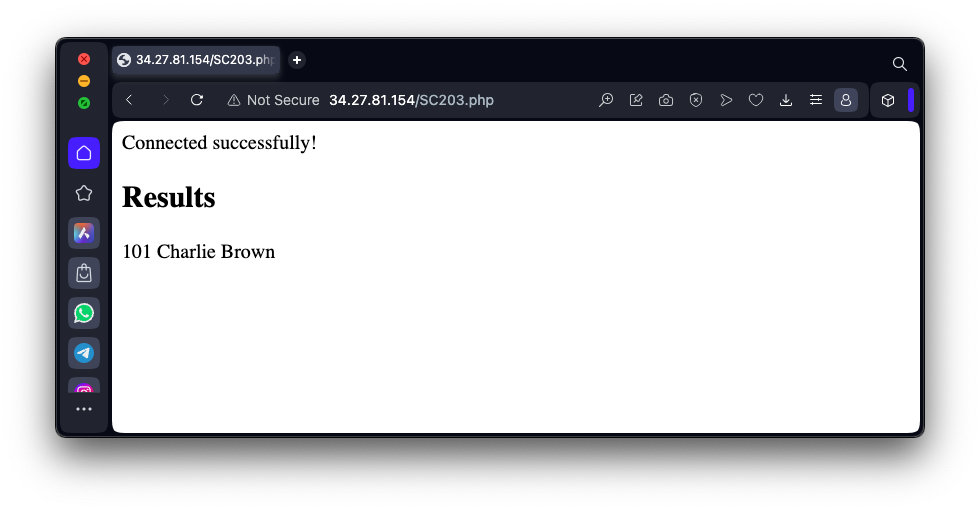
http://35.222.29.122/SC203.htmEnter a Name of Charlie Brown into the form, as shown below, and click the Search button.

https://samlols.samsclass.info/SC/SC203.htmEnter the URL to your PHP page in the form for flag SC 203.1, as shown below, and click the Submit button.

Flag SC 203.1: Database Functionality (5 pts)
The flag appears, as shown below.
http://35.222.29.122/SC203.htmEnter this name into the form:
x'as shown below, and click the Submit button.
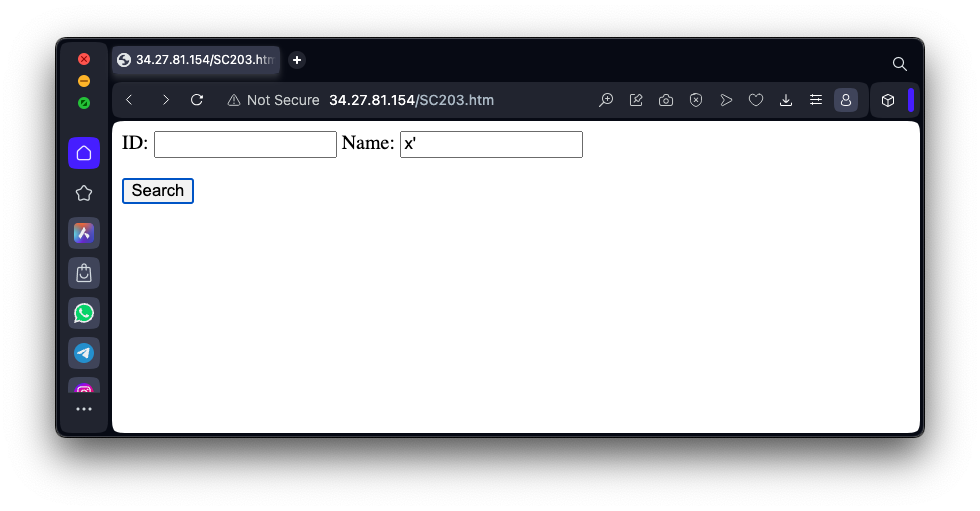
This demonstrates a SQL injection vulnerability--the user's input can contain SQL commands that are executed.

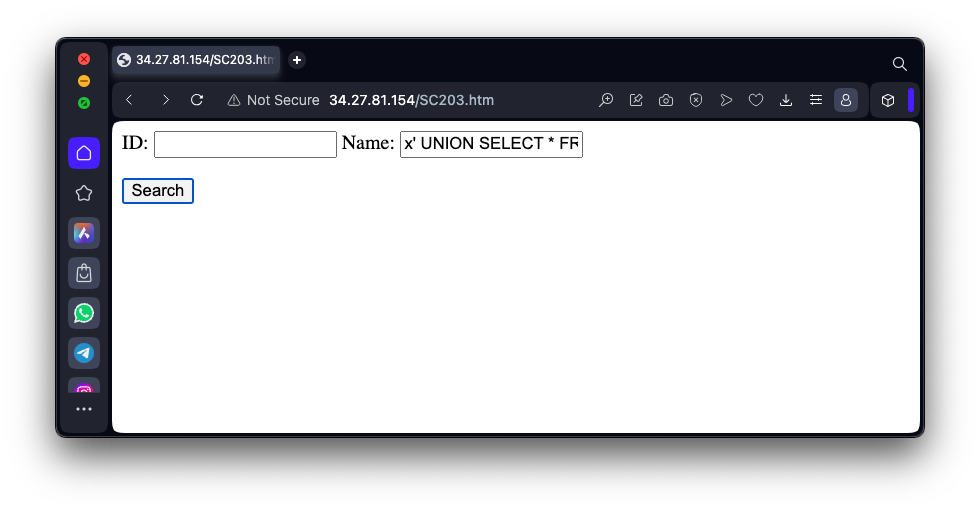
x' UNION SELECT * FROM employees #as shown below, and click the Submit button.

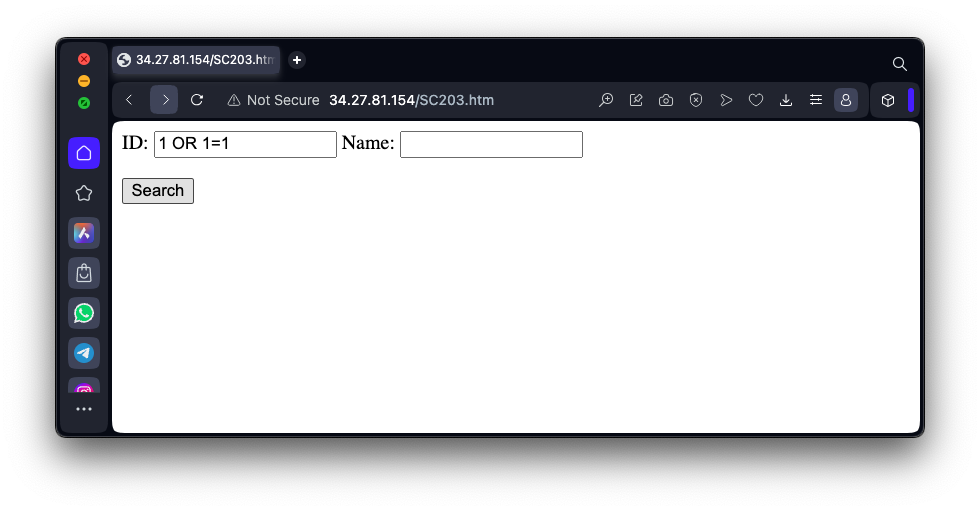
http://35.222.29.122/SC203.htmEnter this ID into the form:
1 OR 1=1as shown below, and click the Submit button.
Note: "1=1" caused the PHP server to hang, from Collin College in July, 2024, because the campus network filtered it out. If that happens, use 2=2 instead.
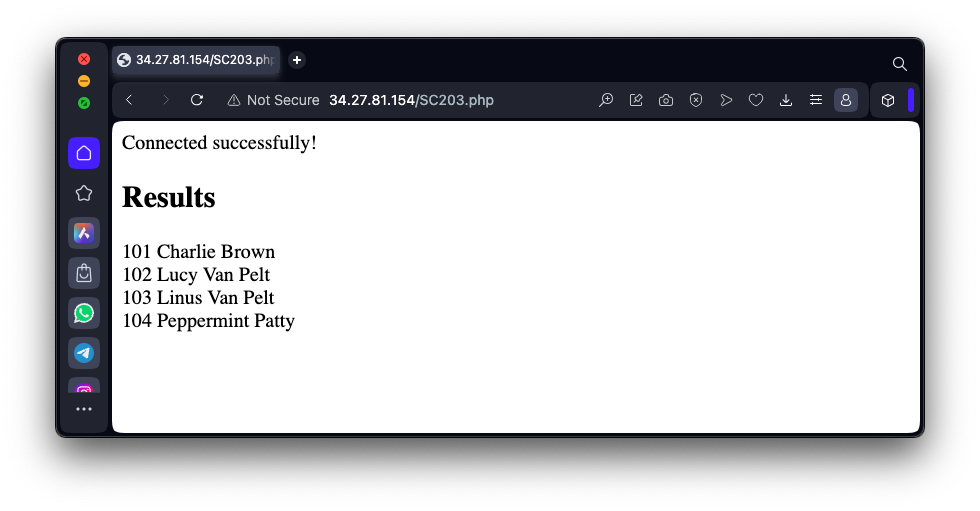
'I recommend using the str_replace function. Test your script on your own HTML form.
When it's working, run the test in the box below to get the flag.
Flag SC 203.2: Removing Bad Characters (10 pts)
In a Web browser, open this page:
https://samlols.samsclass.info/SC/SC203.htmEnter the URL to your PHP page in the form for flag SC 203.2 and submit the form. If your code is correct, the flag will appear.
I used this page as a guide.
In case that page vanishes, here are the two important figures:
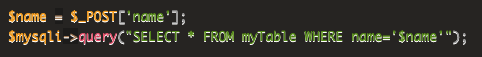

When it's working, run the test in the box below to get the flag.
Flag SC 203.3: Parameterized Queries (20 pts)
In a Web browser, open this page:
https://samlols.samsclass.info/SC/SC203.htmEnter the URL to your PHP page in the form for flag SC 203.3 and submit the form. If your code is correct, the flag will appear.
Posted 3-28-24
"2=2" tip added 7-18-24