
sudo nano /var/www/html/SC202.htm
<html>
<body>
<form action="SC202.php">
IP: <input name="ip"><p>
<input type="submit" value="Ping">
</form>
</body>
</html>

sudo nano /var/www/html/SC202.php
<?php
if (!isset($_REQUEST['ip'])) {
die("<h2>Error: No ip specified!</h2>");
}
$ip = $_REQUEST['ip'];
$cmd = "ping -c 2 $ip 2>&1";
system($cmd);
?>
Save the file with Ctrl+X, Y, Enter.

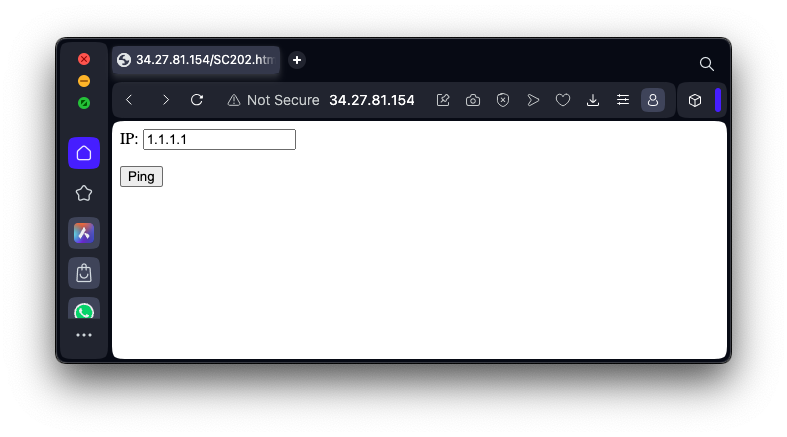
http://35.222.29.122/SC202.htmEnter 1.1.1.1 into the form, as shown below, and click the Ping button.
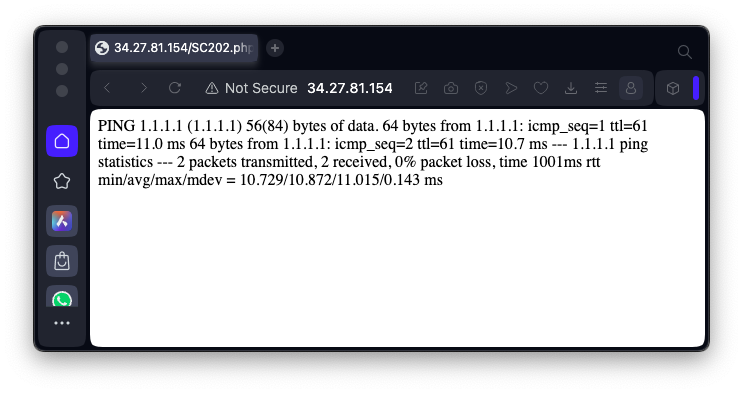
https://samlols.samsclass.info/SC/SC202.htmEnter the URL to your PHP page in the form for flag SC 202.1, as shown below, and click the Submit button.
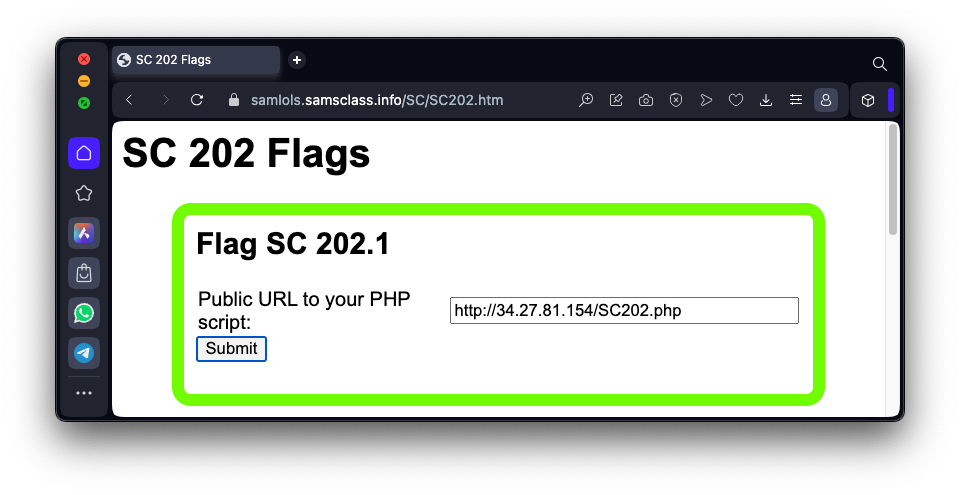
Flag SC 202.1: Ping (5 pts)
The flag appears, as shown below.
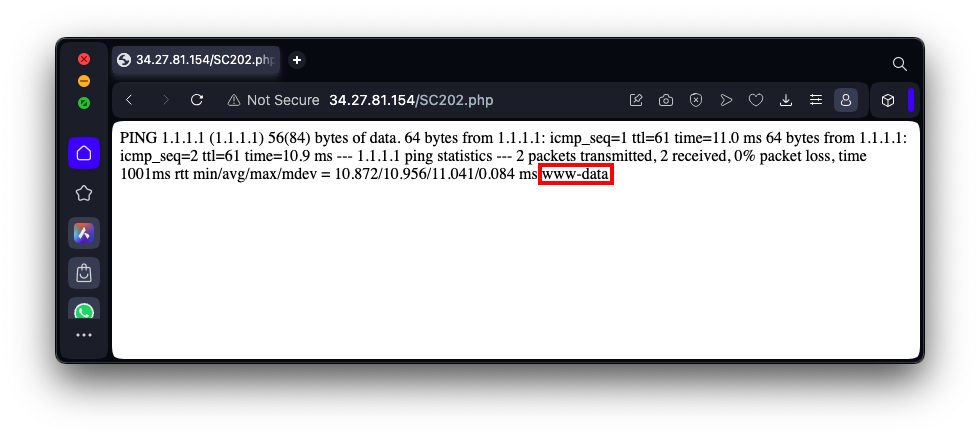
http://35.222.29.122/SC202.htmEnter this IP into the form:
1.1.1.1;whoamias shown below, and click the Submit button.
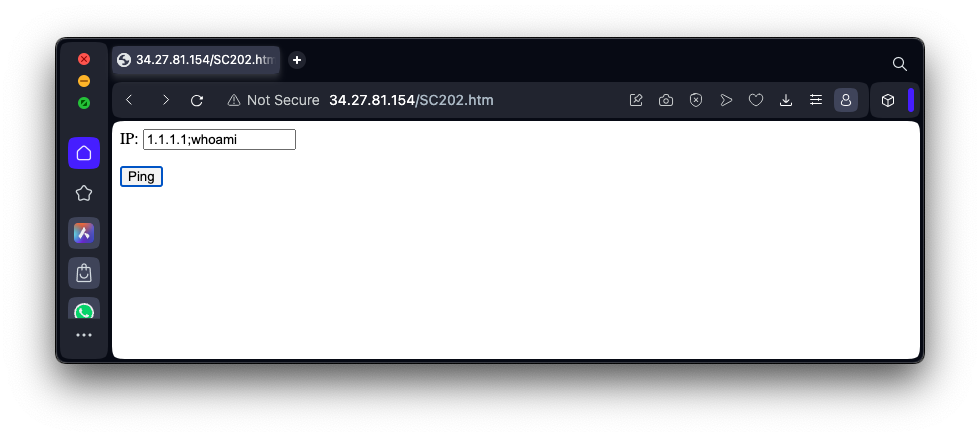
This is the name of the Apache user.
This demonstrates a code injection vulnerability--the user's input can contain shell commands that are executed.
; |I recommend using the str_replace function. Test your script on your own HTML form.
When it's working, run the test in the box below to get the flag.
Flag SC 202.2: Removing Bad Characters (10 pts)
In a Web browser, open this page:
https://samlols.samsclass.info/SC/SC202.htmEnter the URL to your PHP page in the form for flag SC 202.2 and submit the form. If your code is correct, the flag will appear.
When it's working, run the test in the box below to get the flag.
Hint: Use preg_replace
Flag SC 202.3: Allowing Only Good Characters (10 pts)
In a Web browser, open this page:
https://samlols.samsclass.info/SC/SC202.htmEnter the URL to your PHP page in the form for flag SC 202.3 and submit the form. If your code is correct, the flag will appear.
Posted 3-28-24
preg_replace hint added 7-18-24