Purple Team 4: Analyzing a Ransomware Attack with Splunk
What You Need for this Project
- A computer with a Web browser.
Purpose
To practice threat hunting, using
the
Boss of the SOC (BOTS) Dataset.
Connecting to My Splunk Server
Go
here:
https://splunk.samsclass.info
or here:
https://splunk2.samsclass.info
Log in as student1 with a password of student1
The Splunk main page opens, as shown below.
At the top left, click "Search & Reporting".
The "Search" page opens,
as shown below.
Challenges
4.1: IP Address (5 pts)
What was the most likely IP address of we8105desk on 24AUG2016?
Hints:
- Search for we8105desk -- you find 181,012 events.
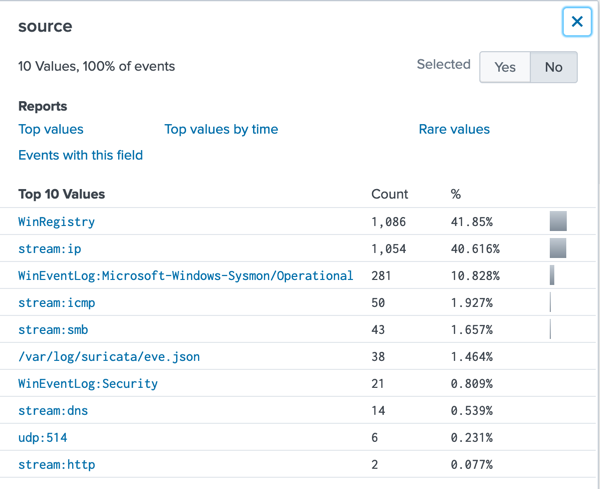
- Examine the source field -- there are 10 values.
- Explore source types associated with login, with a small number of events. Find events on that day and look at their IP addresses.
4.2: Signature (5 pts)
Amongst the Suricata signatures that detected the Cerber malware, which one alerted the fewest number of times? Submit ONLY the signature ID value as the answer. (No punctuation, just 7 integers.)
Hints:
- Search for Cerber -- you find 21,596 events.
- Examine the source field -- there are 4 values.
- Explore the source type associated with Suricata.
4.3: FQDN (15 pts)
What fully qualified domain name (FQDN) does the Cerber ransomware attempt to direct the user to at the end of its encryption phase?
Hints:
- Examine the five Suricata alerts about Cerber. View them as "raw text" in time order.
- Find a time delay and the domain lookup events after it. Note the time of those events.
- Search events near that time. Examine the source values, as shown below. Examine Suricata events (which are more numerous than alerts).
4.4: Suspicious Domain (15 pts)
What was the first suspicious domain visited by we8105desk on 24AUG2016?
Hints:
- Find the Suricata events on that day. There are 86,579 of them.
- Examine the src_ip field. Restrict your query to the desired value.
- Examine the event_type field. Restrict your query to events that load Web pages. There are 38 of them.
- Examine the hostnames visited. There are ten of them. Investigate them with Google and find the one that's known to be malicious.
4.5: VB Script (15 pts)
During the initial Cerber infection a VB script is run. The entire script from this execution, pre-pended by the name of the launching .exe, can be found in a field in Splunk. What is name of the first function defined in the VB script?
Hints:
- Search for events with both a VB filename extension and an .exe extension.
- Read the events to identify normal ones and find the suspicious ones.
4.6: VB Script (15 pts)
During the initial Cerber infection a VB script is run. The entire script from this execution, pre-pended by the name of the launching .exe, can be found in a field in Splunk. What is the length in characters of the value of this field?
Hint:
- Find the length of the Splunk field, not the length of the script itself.
This may be helpful.
4.7: USB key (15 pts)
What is the name of the USB key inserted by Bob Smith?
Hints:
- You want a "Volume Name" as discussed here.
4.8: Server Name (5 pts)
Bob Smith's workstation (we8105desk) was connected to a file server during the ransomware outbreak. What is the domain name of the file server?
Hints:
4.9: IP Address (15 pts)
Bob Smith's workstation (we8105desk) was connected to a file server during the ransomware outbreak. What is the IP address of the file server?
Hints:
- Search for the server's name. Examine the source of those events. Look for source types that record raw network data and would therefore include IP addresses.
4.10: PDFs (20 pts)
How many distinct PDFs did the ransomware encrypt on the remote file server?
Hints:
- Search for .pdf
- Restrict your search for the suspicious app
- Find all unique filenames. Remove filenames outside the time range of the attack.
4.11: Process ID (15 pts)
The VBscript found above launches 121214.tmp. What is the ParentProcessId of this initial launch?
Hints:
- Search for 121214.tmp -- you find 190 events.
- Examine the EventDescription field and focus on the one most closely related to the question.
- Examine the CommandLine field.
4.12: Text Files (15 pts)
The Cerber ransomware encrypts files located in Bob Smith's Windows profile. How many .txt files does it encrypt?
Hints:
- Find all events including.txt and find the path to Bob's Windows profile.
- Add Bob's Windows profile path to the search. To search for a backslash, enter two backslashes.
- Examine the file paths and remove the ones outside Bob's profile.
4.13: File Name (15 pts)
The malware downloads a file that contains the Cerber ransomware cryptor code. What is the name of that file?
Hints:
- Search for HTTP downloads from the Cerber-related domain you found above.
- The filename has a surprising extension. Research that filename outside Splunk to verify that it's related to Cerber.
4.14: Obfuscation (10 pts)
Now that you know the name of the ransomware's encryptor file, what obfuscation technique does it likely use?
Hints:
- Research the file using online resources, outside Splunk, to find this.
Posted 4-27-19 3:41 pm
Scoring engine removed for WCIL 5-20-19



