Right-click an empty portion of the SO desktop and click Applications, "Terminal Emulator".
In the Terminal window, execute the ifconfig command. Make a note of your IP address. You'll need it later.
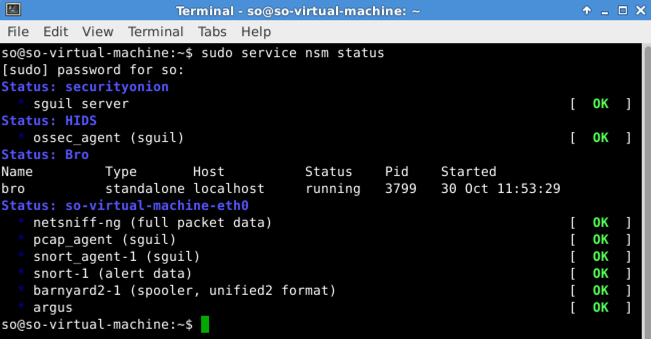
sudo service nsm status
You should see several services, all with OK status, as shown below.

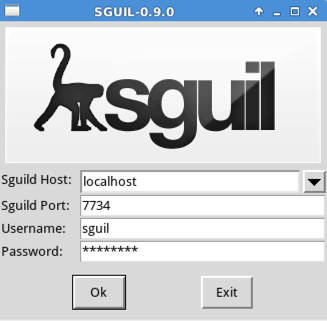
Log in with a username of sguil and a password of password as shown below.
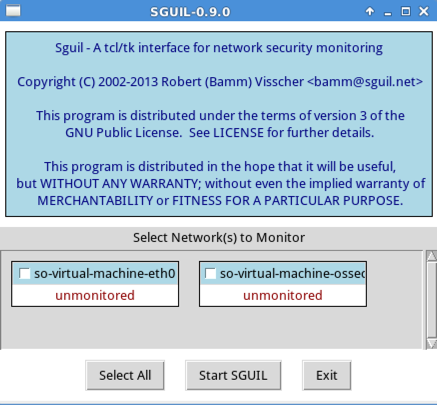
A box pops up asking which networks to monitor, as shown below.
Troubleshooting
If your password doesn't work, use this command to add another user named so2 with the password so2:sudo sguild-add-user so2 so2
Click "Select All" and click "Start SGUIL".
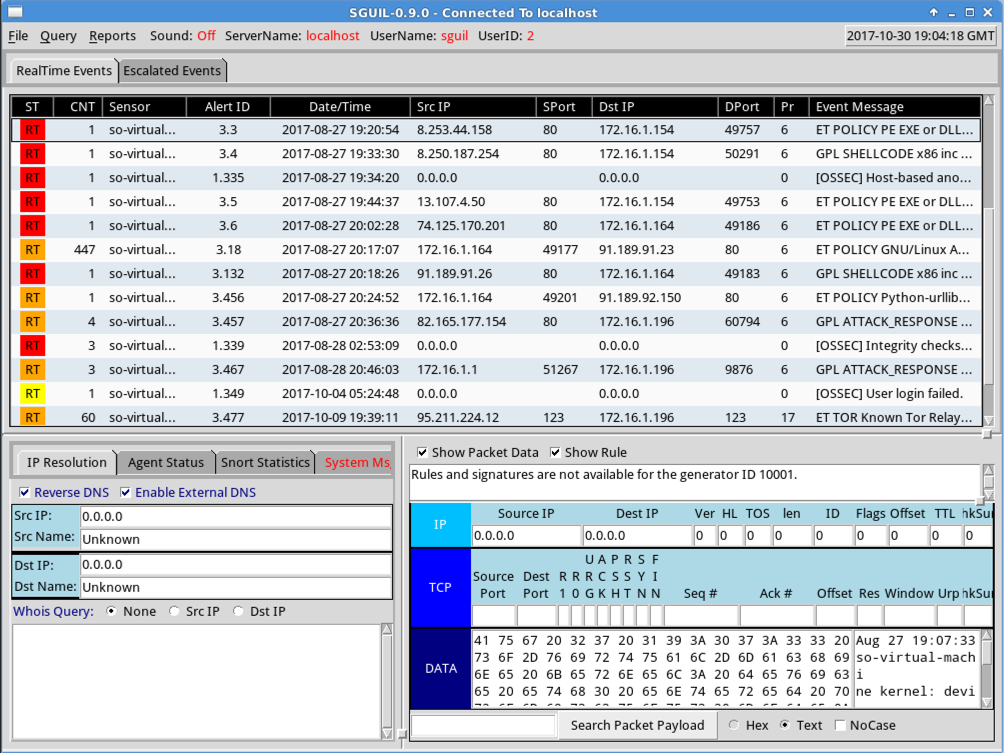
Squil opens. Click a row in the top section to highlight it, and click these three boxes:
To see alerts, we'll perform a simple, harmless attack: an Nmap scan.
On your host computer, scan the SO virtual machine with nmap, as shown below. Replace the IP address with the IP address of your SO machine.
If you don't have Nmap, get it here:
https://nmap.org/download.html
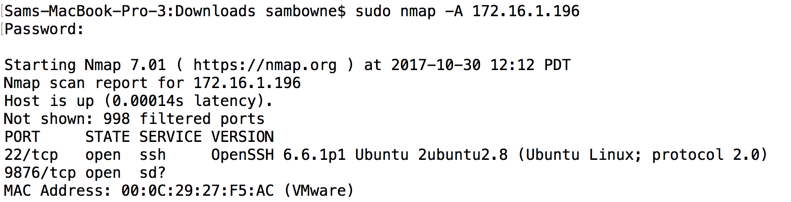
Sguil shows several events, as shown below.
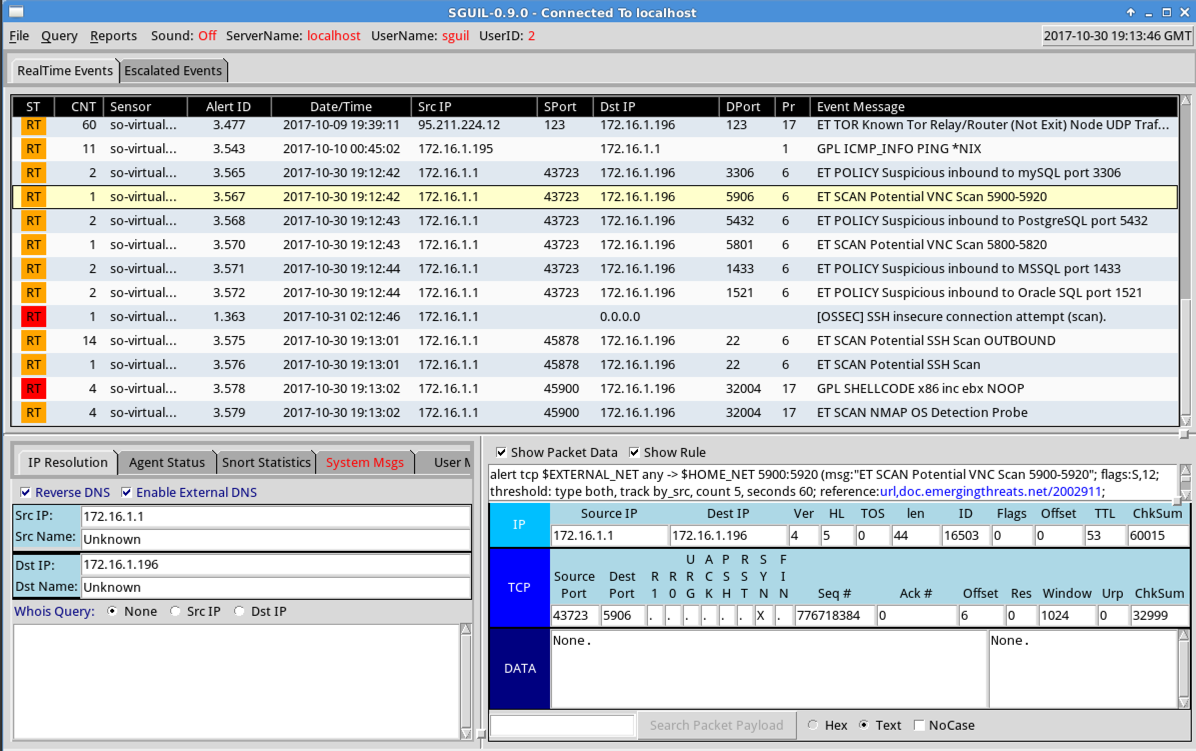
The Query Builder opens, as shown below.
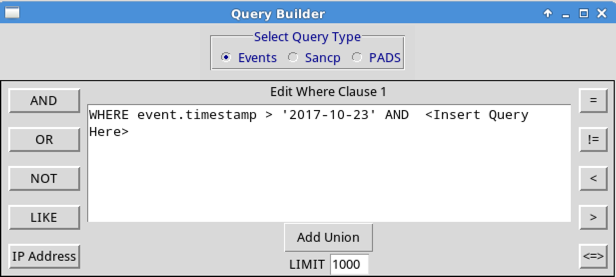
Replace "
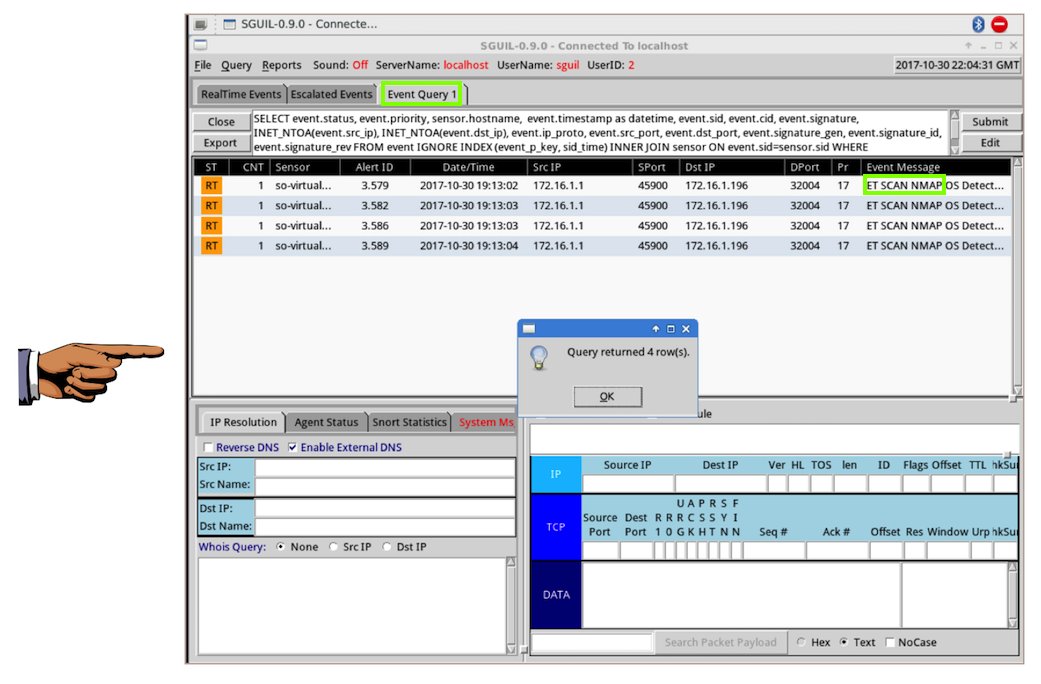
Several results are found, labelled
"nmap",
as shown below.
In the "Query returned 4 row(s)" box, click
OK.
Capture a whole-desktop image and save it as
"Proj 7a from YOURNAME".
YOU MUST SEND IN A WHOLE-DESKTOP IMAGE FOR FULL CREDIT
Click Transcript.
A message says "Transcripts can only
be generated for TCP data."
Right-click the Alert ID again and click
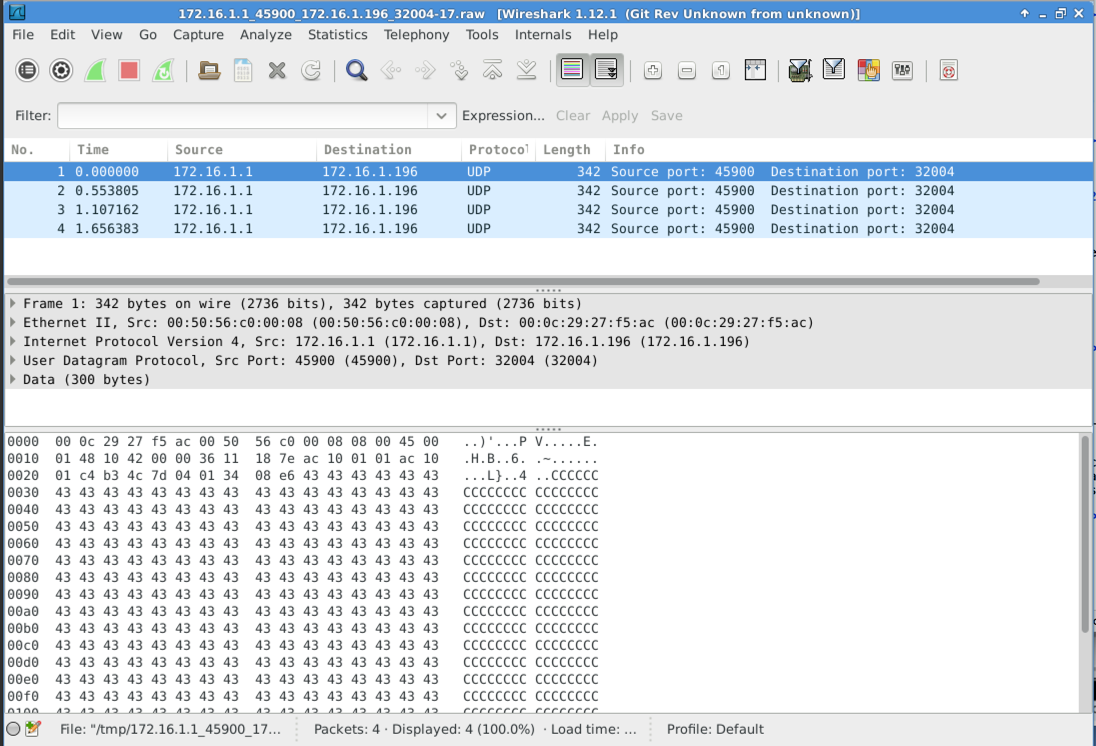
Wireshark.
Wireshark opens, showing the four packets,
as shown below. Notice that these packets
end with a lot of C characters.
Close Wireshark. Close Sguil.
Chromium opens with a message saying
"Your connection is not private".
Click ADVANCED.
Click "Proceed to localhost (unsafe)".
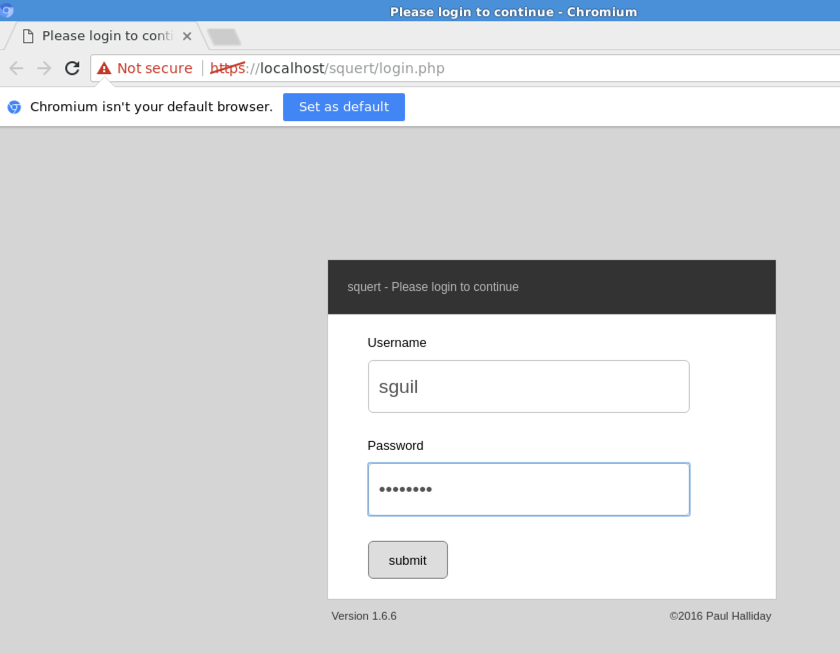
Log in with the username sguil and the
password password
as shown below.
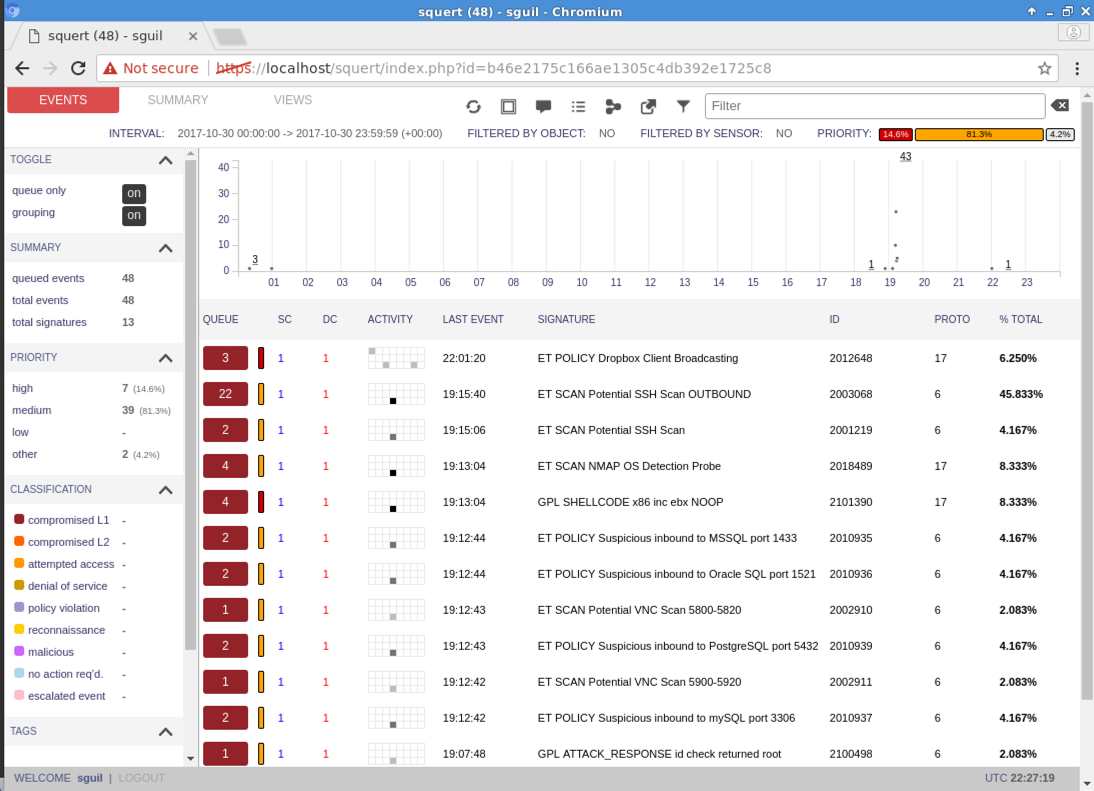
Squert shows a panel with a list of events,
as shown below.
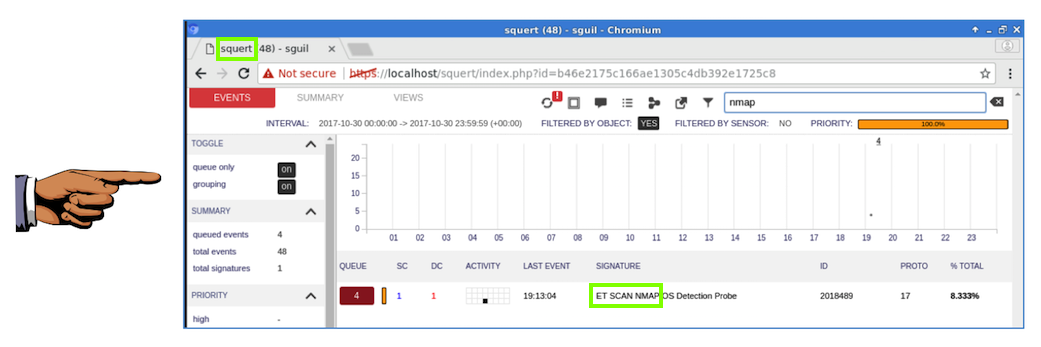
In the Filter box, at the top right, type
nmap and press Enter.
Squert finds the NMAP scan,
as shown below.
Capture a whole-desktop image and save it as
"Proj 7b from YOURNAME".
YOU MUST SEND IN A WHOLE-DESKTOP IMAGE FOR FULL CREDIT
Close the browser.
Log in with the username sguil and the
password password.
ELSA opens,
as shown below.
Click "Syslog-NG (Program)".
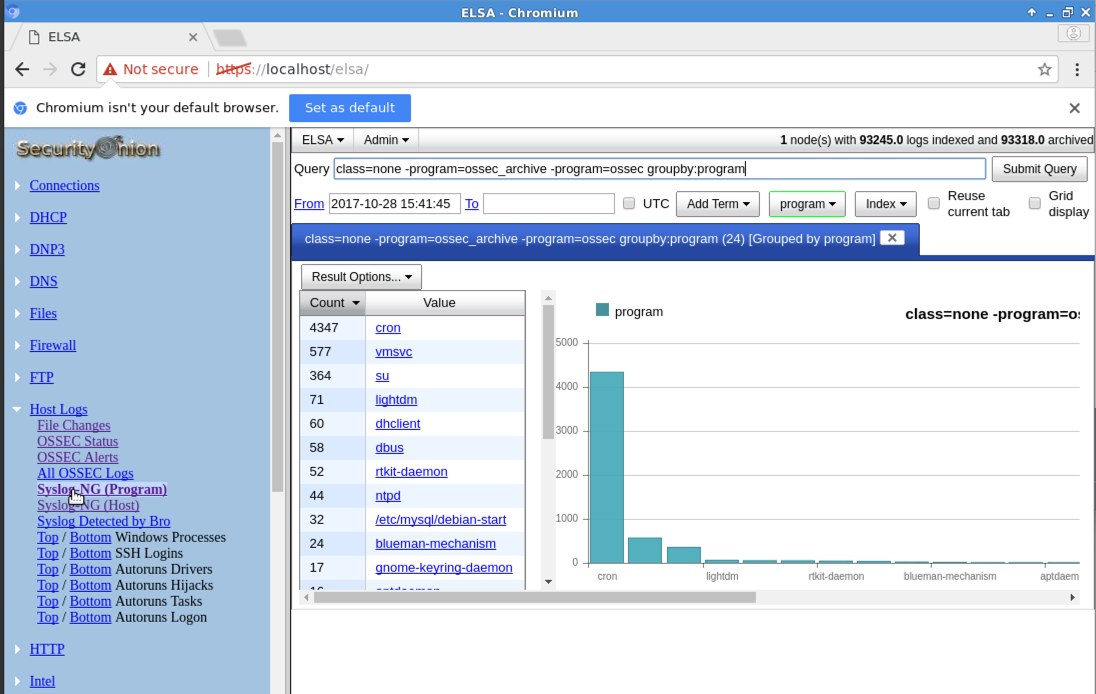
A chart of programs and the number
of times they were launched appears.
as shown below.
In the "Server IPs" line, click
Top.
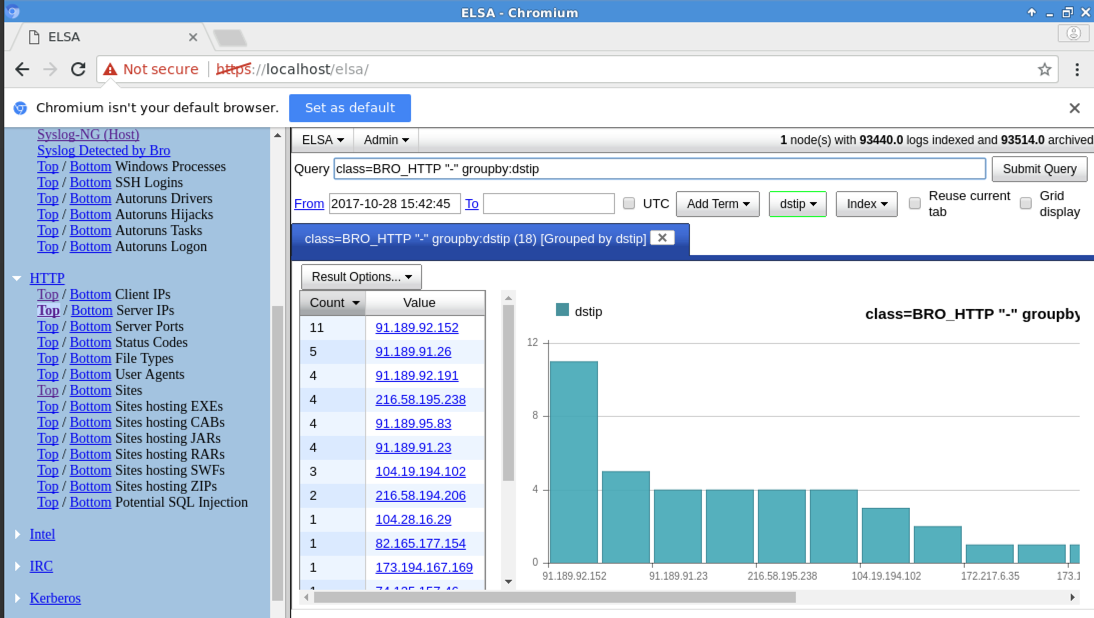
A chart of IPs
of times they were visited appears.
as shown below.
NMAP events are fouond, as shown below.
Capture a whole-desktop image and save it as
"Proj 7c from YOURNAME".
YOU MUST SEND IN A WHOLE-DESKTOP IMAGE FOR FULL CREDIT
Close the browser.
Send a Cc to yourself.
Posted 10-30-17 
Capturing Screen Image A
Make sure these required items are visible,
as shown above:
Pivoting to Full Content Data
At the top of Sguil, click the
"RealTime Events" tab.
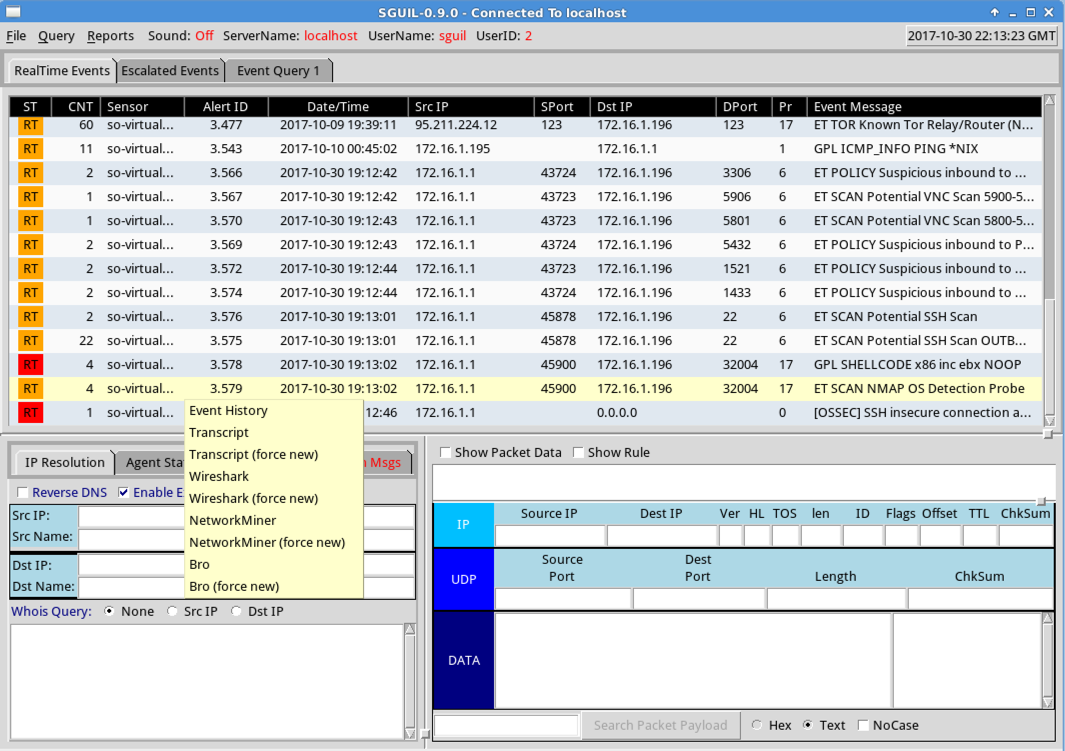
Scroll down to find the event labelled
"NMAP". Right-click the Alert ID in
that row. A context menu appears,
as shown below.
Task 2: Using Squert
On the SO desktop, double-click
Squert.
Capturing Screen Image B
Make sure these required items are visible,
as shown above:
Task 3: Using ELSA
Starting ELSA
On the SO desktop, double-click
ELSA.
Viewing Frequently-Used Programs
On the left side, click the triangle to
the left of "Host Logs".
Viewing Frequently-Visited Websites
On the left side, click the triangle to
the left of HTTP.
Finding NMAP Scans
At the top, in the Query bar,
erase all the text and enter
nmap. Click
"Submit query".
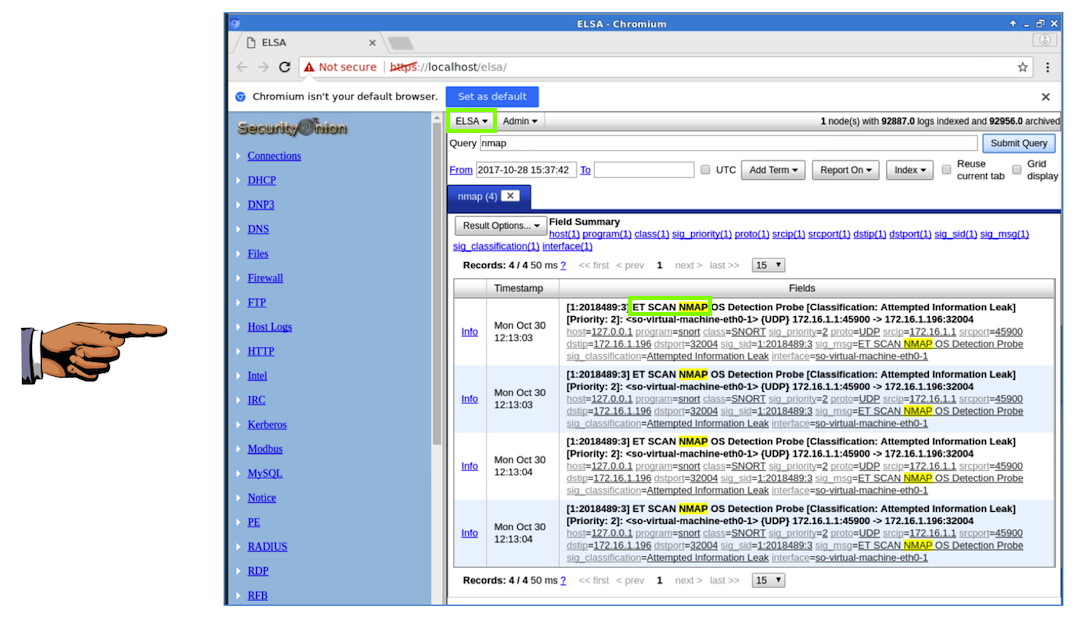
Capturing Screen Image C
Make sure these required items are visible,
as shown above:
Turning in Your Project
Email the images to cnit.50sam@gmail.com with a subject line of "Proj 7 From YOUR NAME", replacing "YOUR NAME" with your real name.
Minor typo fixed 11-21-17
Another typo 12-11-17
Tip added 12-12-17