Boss of the SOC v1: Threat Hunting with Splunk (80 pts + 245 extra)
Submitting Projects
CCSF students must do these things to get credit:
- Perform the project steps until you find a flag
- Capture a whole-desktop image showing the flag
- Outline or highlight the flag in the image
- Submit the image in the appropriate Project in Canvas
- Type the flag into the text field
If you prefer, you can use the automated scoring system
at the bottom of the Projects page, but
DO NOT SUBMIT THE SAME PROJECT
IN BOTH CANVAS AND THE AUTOMATED SYSTEM.
|
What You Need for this Project
- A computer with a Web browser.
Purpose
To practice threat hunting, using
the
Boss of the SOC (BOTS) Dataset.
Connecting to My Splunk Server
Go
here:
https://splunk.samsclass.info
or here:
https://splunk2.samsclass.info
Log in as student1 with a password of student1
The Splunk main page opens, as shown below.
At the top left, click "Search & Reporting".
The "Search" page opens,
as shown below.
Introduction to Splunk & the BOTS Data
Sampling the Data
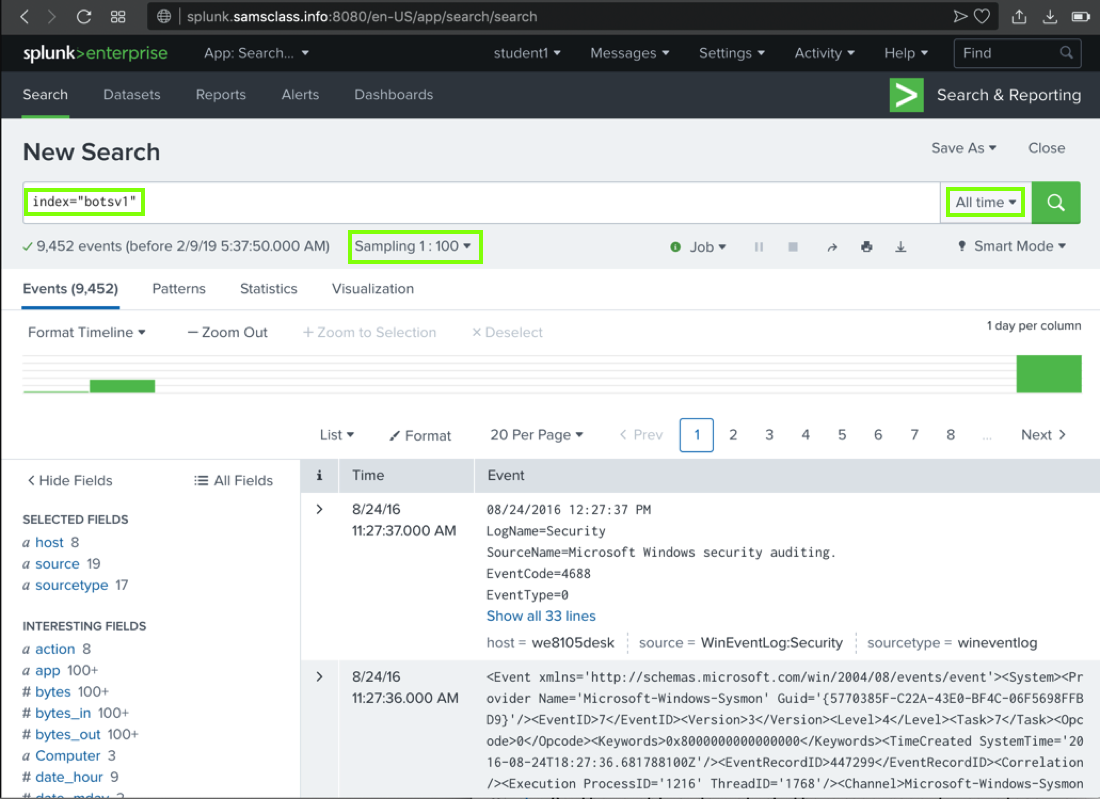
In the Search box, type
index="botsv1"
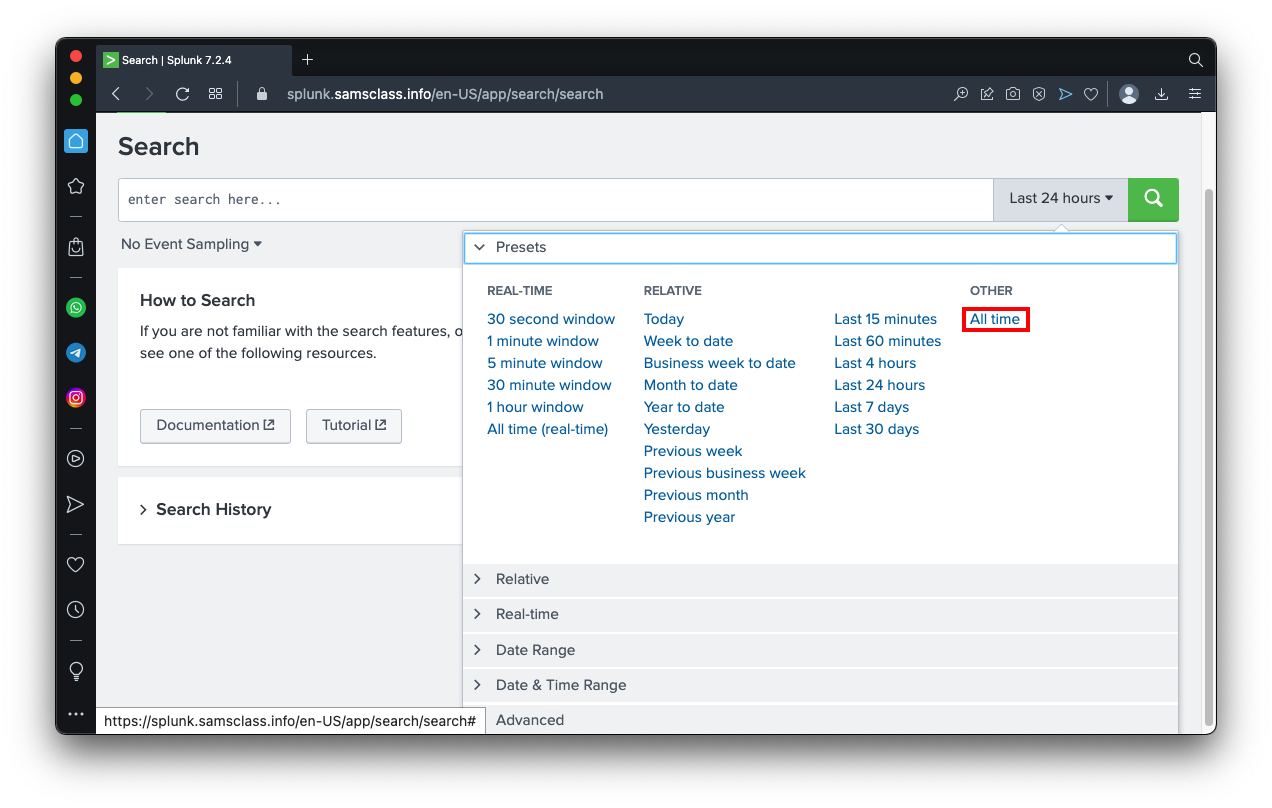
On the right side, click the "Last 24 hours" box and click "All time",
outlined in red in the image below.
On the left side, under the Search box, click "No Event Sampling" and click "1: 100"
On the right side, click the green magnifying-glass icon
The search finishes within a few seconds, and finds
approximately 9,452 results,
as shown below.
(The number varies because
the sampling is random.)
There are actually 100x as many events, but we are only
looking at 1% of them for now.
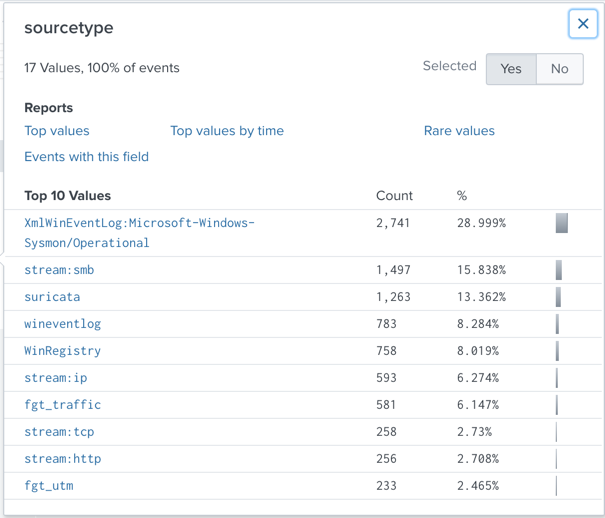
Viewing Sourcetypes
On the lower left, in the "SELECTED FIELDS" list,
click the blue sourcetype link.
A "sourcetype" box pops up, showing the
"Top 10 Values" of this field,
as shown below.
Notice these items:
sourcetype
| | Sensor
|
|---|
| XmlWinEventLog:Microsoft-Windows-Sysmon/Operational | | "Sysmon", a Windows monitoring tool from Microsoft |
| stream:smb,stream:ip,stream:tcp,stream:http | | "Splunk Stream", which monitors live network traffic |
| suricata | | The Suricata Intrusion Detection System (IDS) |
| wineventlog and WinRegistry | | Windows OS |
| fgt_traffic and fgt_utm | | Fortigate firewalls |
Note: because the sampling is random, you may see
different items near the bottom of this list.
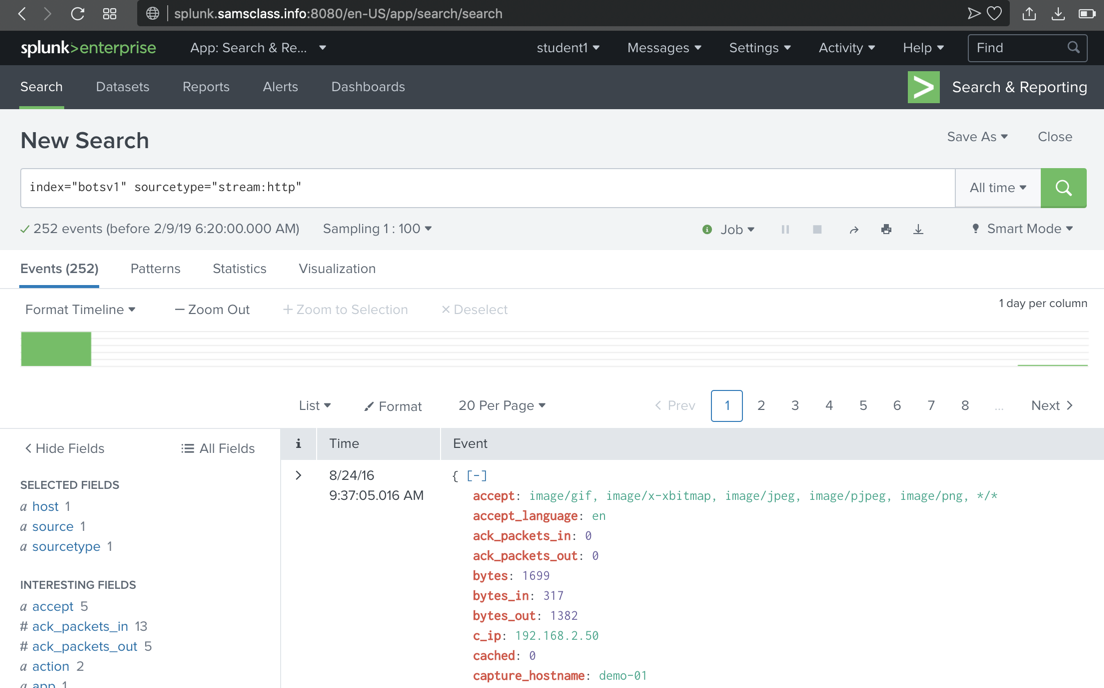
Viewing stream:http Events
In the "sourcetype" box,
in the "Top 10 Values" list,
near the bottom,
if it is visible,
click stream:http
Splunk adds
sourcetype="stream:http"
to
the search and finds approximately 252 results,
as shown below.
If there is no stream:http item in
the list, just type it into the query.
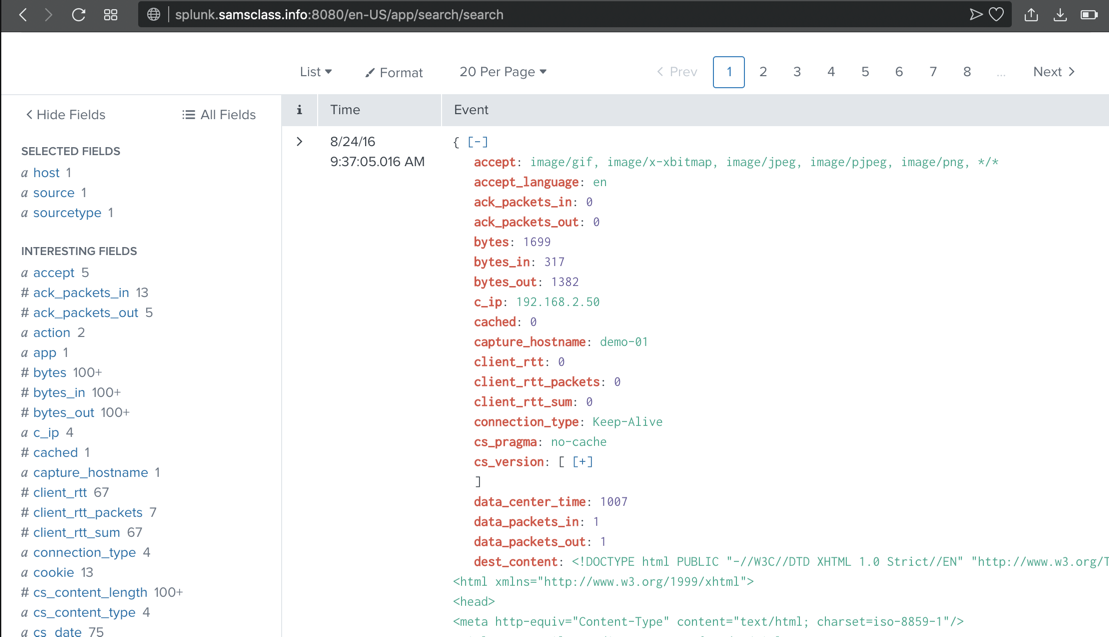
Scroll down to examine the most recent event.
Splunk has parsed this event into many fields,
shown in red, including c_ip,
the client IP address,
as shown below.
These fields are explained
here.
Viewing HTTP Events for imreallynotbatman.com
In the Search box, at the right end, add this text:
imreallynotbatman.com
251 events are found,
as shown below. (The sampling is
random, so you may not see the exact
events shown below.)
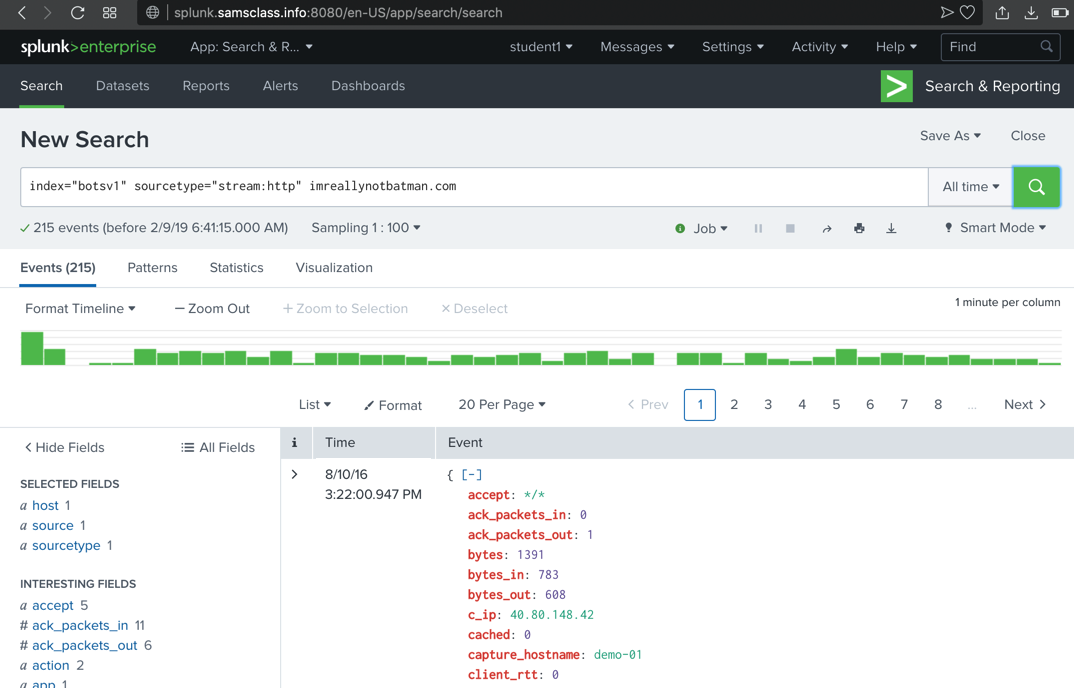
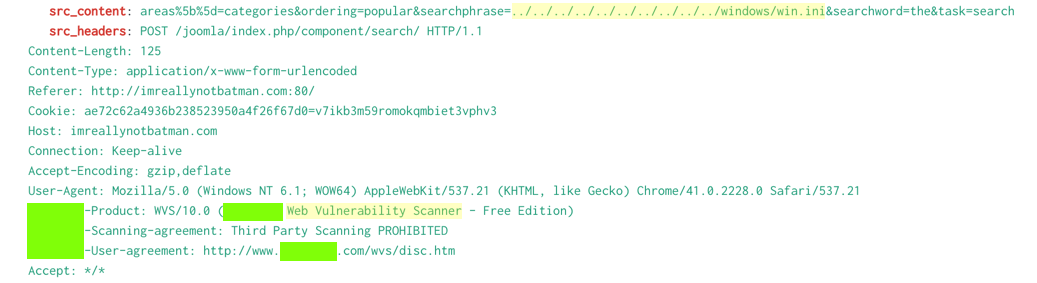
Scroll through the first few events found,
and note these items,
highlighted in the image below.
- You may see obvious attack URLs, such as the directory traversal path containing ../../../../ shown below.
- Many header fields reference a Web Vulnerability Scanner
Take Notes
Tip: take notes of the flags you find as you go.
Several flags require you to use information from a previous challenge.
|
Level 1: Finding Attack Servers (20 pts + 15 extra)
BOTSv1 1.1: Scanner Name (5 pts)
Find the brand name of the vulnerability scanner, covered
by a green box in the image above.
BOTSv1 1.2: Attacker IP (5 pts)
Find the attacker's IP address.
BOTSv1 1.3: Web Server IP (5 pts)
Find the IP address of the web server serving "imreallynotbatman.com".
BOTSv1 1.4: Defacement Filename (10 pts)
Find the name of the file used to deface the web server serving "imreallynotbatman.com".
Hints:
- It was downloaded by the Web server, so the server's IP is a client address, not a destination address.
- Remove the filter to see all 9 such events. Examine the uri values.
BOTSv1 1.5: Domain Name (10 pts)
Find the fully qualified domain name (FQDN) used by the staging server hosting the defacement file.
Hints:
- Examine the 9 events from the previous challenge. Look at the url values.
Level 2: Identifying Threat Actors (20 pts + 30 extra)
BOTSv1 2.1: Staging Server IP (10 pts)
In Level 1, you found the staging server domain name (used to host the defacement file). Find that server's IP adddress.
Hints:
- Search for HTTP GET events containing the target FQDN.
BOTSv1 2.2: Leetspeak Domain (10 pts)
Use a search engine (outside Splunk) to find other domains on the staging server. Search for that IP address. Find a domain with an name in Leetspeak (like "1337sp33k.com").
Alienvault is useful.
BOTSv1 2.3: Brute Force Attack (15 pts)
Find the IP address performing a brute force attack against "imreallynotbatman.com".
Hints:
- Find the 15,570 HTTP events using the POST method.
- Exclude the events from the vulnerability scanner.
- Examine the form_data of the remaining 441 events.
- To make a useful table, add this to your query:
| table _time, form_data
BOTSv1 2.4: Uploaded Executable File Name (15 pts)
Find the name of the executable file the attacker uploaded to the server.
Hints:
- Find the 15,570 HTTP events using the POST method.
- Exclude the events from the vulnerability scanner.
- Search for common Windows executable filename extensions.
Level 3: Using Sysmon and Stream (20 pts + 30 extra)
BOTSv1 3.1: MD5 (10 pts)
In Level 2, you found
the name of an executable file the
attackers uploaded to the server.
Find that file's MD5 hash.
Hints:
- Read about Sysmon Event IDs
- Find events from Sysmon for process creation.
- Examine cmdline to find the correct event.
BOTSv1 3.2: Brute Force (10 pts)
What was the first brute force password used?
Hints:
- Start with 1:10 sampling.
- Find events containing "login".
- Find top values of "url".
- Examine the "form_data" values to identify the brute force attack.
BOTSv1 3.3: Correct Password (10 pts)
What was the correct password found in the brute force attack?
Hints:
- Find the events with the "form_data" values indicating a login attempt.
- There are two different "http_user_agent" values.
BOTSv1 3.4: Time Interval (10 pts)
How many seconds elapsed between the time the brute force password scan identified the correct password and the compromised login? Round to 2 decimal places.
Hints:
- HINT: Find the two events with the correct password in the "form_data" field.
BOTSv1 3.5: Number of Passwords (10 pts)
How many unique passwords were attempted in the brute force attack?
Hints:
- Examine http_user_agent values.
Level 4: Analyzing a Ransomware Attack (20 pts + 160 extra)
BOTSv1 4.1: IP Address (5 pts)
What was the most likely IP address of we8105desk on 24AUG2016?
Hints:
- Search for we8105desk -- you find 181,012 events.
- Examine the source field -- there are 10 values.
- Explore stream sources with protocols used in
Active Directory logins.
- Find events on that day and look at their IP addresses.
BOTSv1 4.2: Signature ID (5 pts)
Amongst the Suricata signatures that detected the Cerber malware, which one alerted the fewest number of times? Submit ONLY the signature ID value as the answer. (No punctuation, just 7 integers.)
Hints:
- Search for Cerber -- you find 21,596 events.
- Examine the source field -- there are 4 values.
- Explore the source type associated with Suricata.
BOTSv1 4.3: FQDN (15 pts)
What fully qualified domain name (FQDN) does the Cerber ransomware attempt to direct the user to at the end of its encryption phase?
Hints:
New process: Aug 2, 2021:
- Find events with a sourcetype of suricata
- Restrict the search to events with "alert signature" containing "Onion domain lookup"
- Restrict the time to within one second of those events
- Look in the "stream:dns" events, in the "query" field
Old process:
- Examine the five Suricata alerts about Cerber. View them as "raw text" in time order.
- Find a time delay and the domain lookup events after it. Note the latest time of those events.
- Use the "Date time range" option of Search to narrow the time range to just a few seconds before the Suricata alert. Check to make sure you can still find the Suricata alerts. You may have to adjust the time by am hour or two to compensate for time zone differences.
- Search all events in that small time range. Examine Suricata events. Look at dns-related fields.
BOTSv1 4.4: Suspicious Domain (15 pts)
What was the first suspicious domain visited by we8105desk on 24AUG2016?
Hints:
- Find the Suricata events on that day. There are 86,579 of them.
- Examine the src_ip field. Restrict your query to the desired value.
- Examine the event_type field. Restrict your query to events that load Web pages. There are 38 of them.
- Examine the hostnames visited. There are ten of them. Investigate them with Google and find the one that's known to be malicious.
BOTSv1 4.5: VB Script (15 pts)
During the initial Cerber infection a VB script is run. The entire script from this execution, pre-pended by the name of the launching .exe, can be found in a field in Splunk. What is name of the first function defined in the VB script?
Hints:
- Search for events with both a filename extension for VB script and an .exe extension. There are 16 of them.
- Examine the body field. Find the malicious one.
BOTSv1 4.6: Field Length (15 pts)
During the initial Cerber infection a VB script is run. The entire script from this execution, pre-pended by the name of the launching .exe, can be found in a field in Splunk. What is the length in characters of the value of this field?
Hint:
- Find the length of the Splunk field, not the length of the script itself.
This may be helpful.
- There are three events with fields that match this description. Use the longest length of those three fields. The longer ones contain the same script, but ampersands are HTML-encoded which makes the field longer.
BOTSv1 4.7: USB key (15 pts)
What is the name of the USB key inserted by Bob Smith?
Hints:
- Find events with SourceType of WinRegistry
- Search for "FriendlyName", as shown here.
BOTSv1 4.8: Server Name (5 pts)
Bob Smith's workstation (we8105desk) was connected to a file server during the ransomware outbreak. What is the domain name of the file server?
Hints:
- Examine SMB stream data for Bob's workstation during the outbreak
- Find events with a "path" by adding path="*" to the query
- The server name resembles Bob's workstation name.
BOTSv1 4.9: IP Address (15 pts)
Bob Smith's workstation (we8105desk) was connected to a file server during the ransomware outbreak. What is the IP address of the file server?
Hints:
- Search for the server's name. Examine the source of those events. Look for source types that record raw network data and would therefore include IP addresses.
BOTSv1 4.10: PDFs (20 pts)
How many distinct PDFs did the ransomware encrypt on the remote file server?
Hints:
- Search for .pdf
- Restrict your search for the "unknown" app
- Find all unique filenames. Remove filenames outside the time range of the attack.
BOTSv1 4.11: Process ID (15 pts)
The VBscript found above launches 121214.tmp. What is the ParentProcessId of this initial launch?
Hints:
- Search for 121214.tmp -- you find 190 events.
- Examine the EventDescription field and focus on the one most closely related to the question.
- Examine the CommandLine field.
BOTSv1 4.12: Text Files (15 pts)
The Cerber ransomware encrypts files located in Bob Smith's Windows profile. How many .txt files does it encrypt?
Hints:
- Find all events including.txt and find the path to Bob's Windows profile.
- Add Bob's Windows profile path to the search. To search for a backslash, enter two backslashes.
- Examine the file paths and remove the ones outside Bob's profile.
BOTSv1 4.13: File Name (15 pts)
The malware downloads a file that contains the Cerber ransomware cryptor code. What is the name of that file?
Hints:
- Search for HTTP downloads from the suspicious domain you found in flag BOTSv1 4.4 above.
- The filename has a surprising extension. Research that filename outside Splunk to verify that it's related to Cerber.
BOTSv1 4.14: Obfuscation (10 pts)
Now that you know the name of the ransomware's encryptor file, what obfuscation technique does it likely use?
Hints:
- Research the file using online resources, outside Splunk, to find this.
Scores from Pacific Hackers 5-11-19
Scores archived Jan 2020
Scores archived Jan 21, 2022
Scores archived Jan 19, 2024
Scores archived Aug 23, 2025
Alienvault hint added 6-10-25
Scoreboard archived and removed 8-23-25
Scoring info box added at top 8-28-25









