CAUTION
This project uses traffic captured from a real malware attack. It may set off virus scanners and possibly even infect old, unpatched Windows machines.Don't do this project on a real Windows machine in normal use. Use your Windows virtual machine instead.
In this case we are using a fairly old Windows malware sample, so it's OK to use a Mac or Linux machine.
Don't use a regular Windows machine for this project, especially one used for other work, such as company machine at a workplace. However, using Windows as the host for a virtual machine is fine.
https://www.malware-traffic-analysis.net/2014/12/15/index.html
On this page, click the 2014-12-15-traffic-analysis-exercise.pcap.zip link, as shown below.

infected
On the File tab, click the "Choose file" button, as shown below.
Navigate to the 2014-12-15-traffic-analysis-exercise.pcap file you unzipped and double-click it.
VirusTotal reports that this file triggers Snort and Suricata alerts, as shown below.
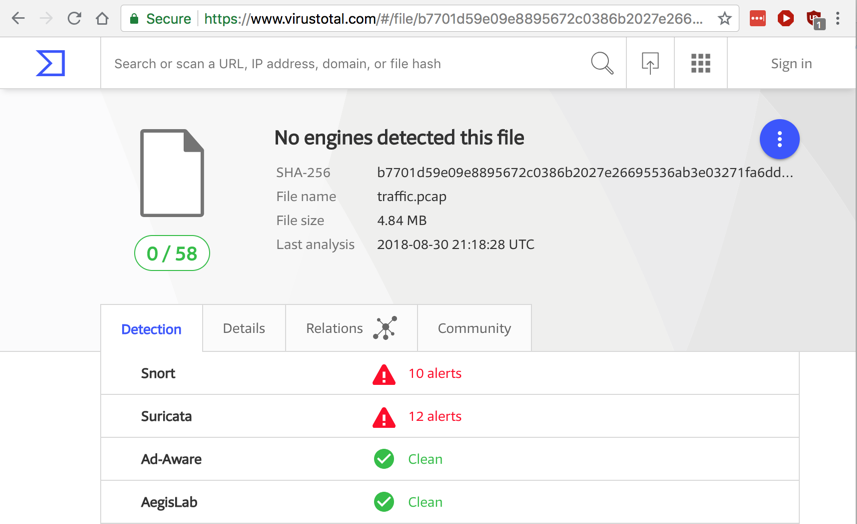
In VirusTotal, click the Details tab.
Scroll down to the "Snort Alerts" and "Suricata Alerts" section.
Expand the last three sections, as shown below.
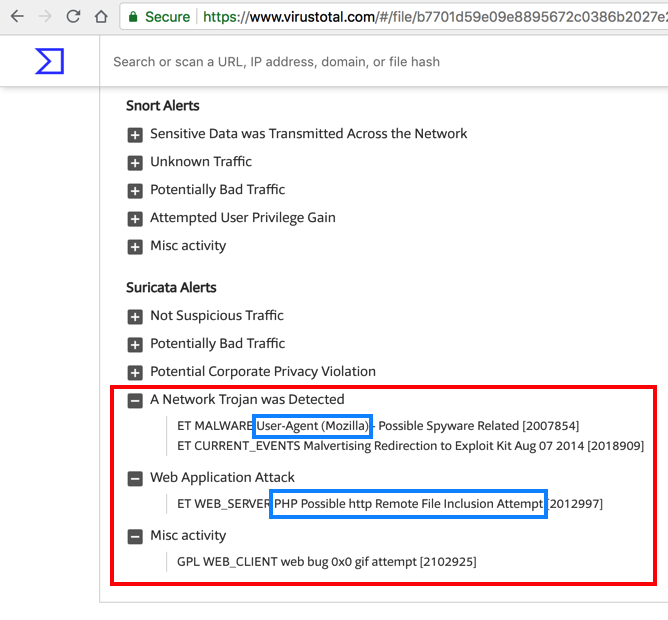
Several suspicious things were detected:
Launch Wireshark.
From the Wireshark menu bar, click File, Open.
Navigate to the 2014-12-15-traffic-analysis-exercise.pcap file you unzipped and double-click it.
In Wirehark, at the top, ehter this filter into the filter bar:
http
Press Enter to filter the traffic.
In the middle pane, expand "Hypertext Transfer Protocol".
Right-click the User-Agent line and click "Apply as Column", as shown below.
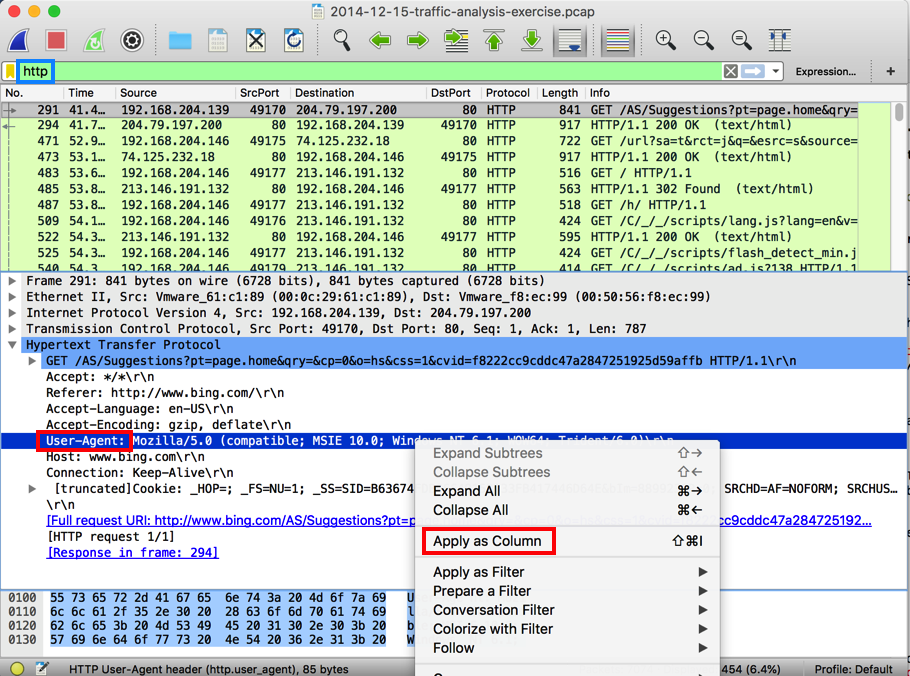
A column titled "User-Agent" appears in the packet list. Click the "User-Agent" column header to sort the rows, and scroll through them.
Most of the User-Agent strings are long or empty, which is normal, but three of them have the strange value of Mozilla.
Click one of the Mozilla lines and examine the HTTP request in the middle pane, as shown below.
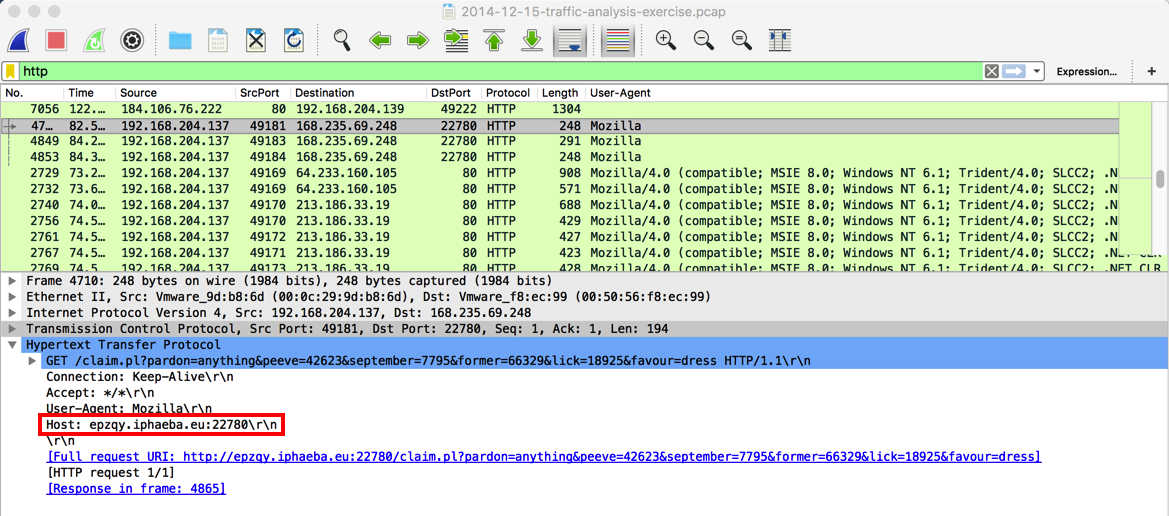
The URL is
epzqy.iphaeba.eu:22780
This is a suspicious URL: the domain name and hostname look like random letters, and the port is very unusual.Look at the "Full request URI" of these packets. The paths and parameters are random words, like "peeve", "delight", and "scholar". This looks like some sort of obfuscated data, possibly malware beacons.
Adjust the filter string to this value:
http && frame contains php
Press Enter to see only HTTP requests for PHP pages.
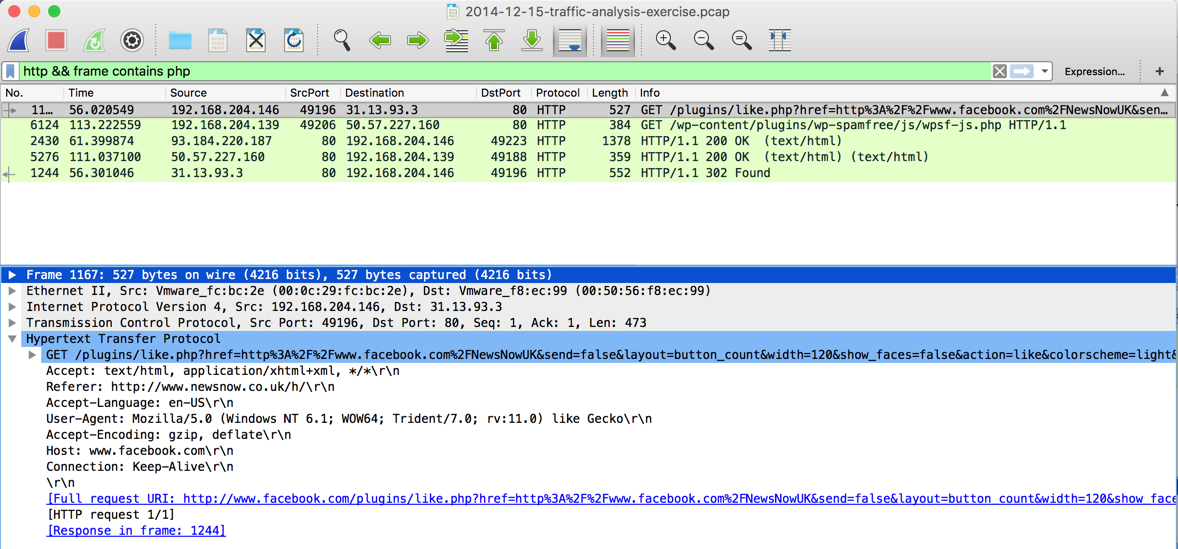
The only strange PHP request is the Facebook Like click shown below. This looks like a false positive--harmless traffic that triggered Suricata because of its structure.
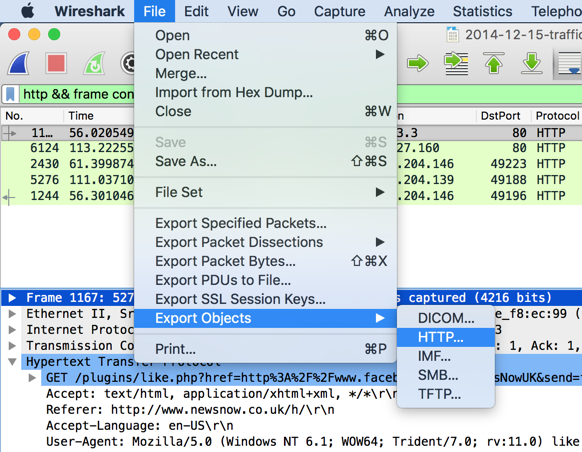
Click "Save All", as shown below.
Navigate to the Downloads, folder, create a new folder, and save the files inside it.
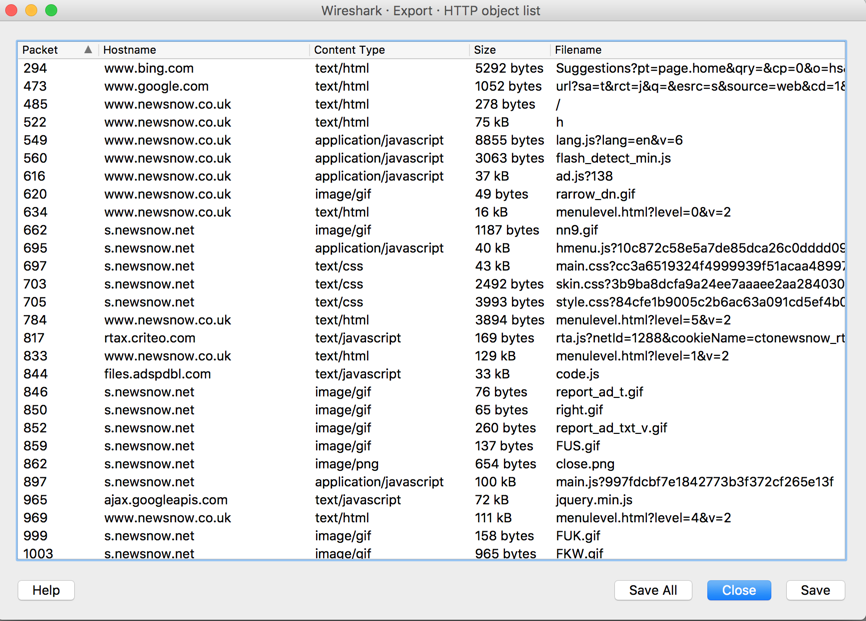
In your operating system's file explorer, open the folder you just created and examine the files.
None of these are malware--the actual malware in that file was transmitted witn encryption and Wireshark can't extract it.
However, just to record your success, find the charte_02.jpg image and double-click it to see the words on it.
The words are covered by a green rectangle in the image shown below.

Use the form below to record your score in Canvas.
If you don't have a Canvas account, see the instructions here.
Posted 9-17-18