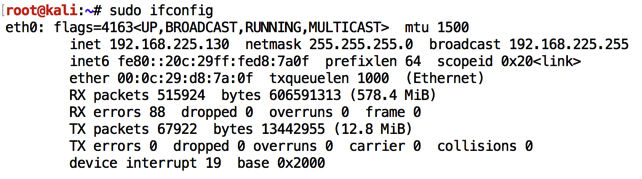
In a Terminal window, execute this command to find its IP address:
sudo ifconfig

sudo apt update
sudo apt install snort -y
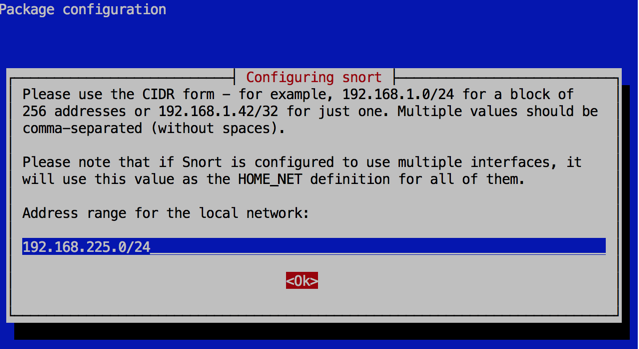
Enter your network's subnet, as shown below, press Tab to highlight OK and press Enter.
snort -c /etc/snort/snort.conf -i eth0 -A full
In the new window, execute this command:
tail -f /var/log/snort/alert
Open a Command Prompt and execute this command, replacing the IP address with the IP address of your Linux machine.
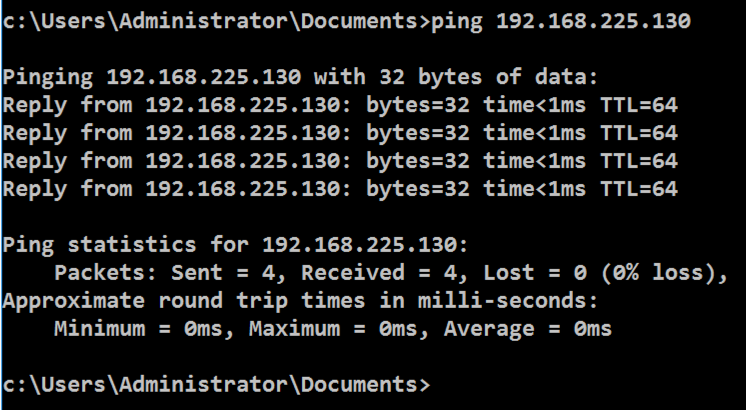
ping 192.168.225.130
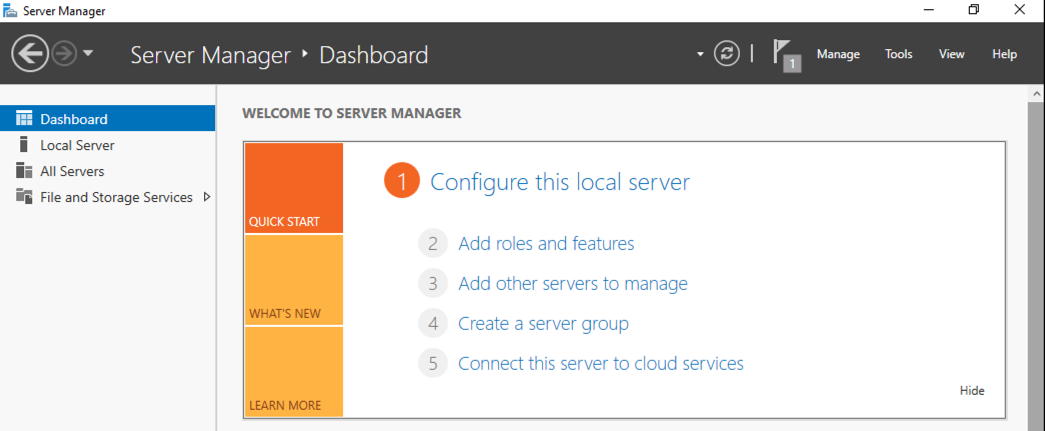
In Server Manager, click "2 Add roles and features", as shown below.
In the "Before you Begin" box, click Next.
In the "Installation Type" box, click Next.
In the "Server Selection" box, click Next.
In the "Server Roles" box, click Next.
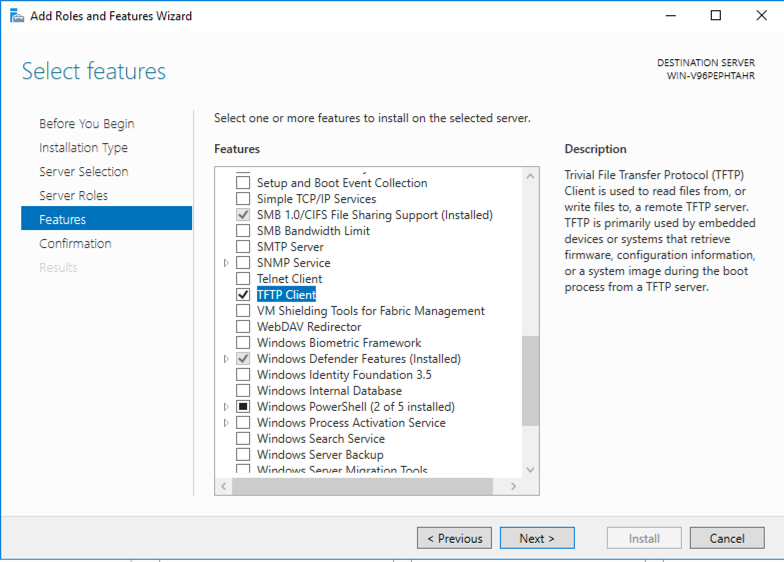
In the "Select features" box, check "TFTP Client", as shown below, and click Next.
In the "Confirm installation selections" box, click Install.
Wait a few seconds for the installation to finish.
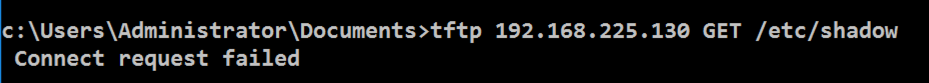
tftp 192.168.225.130 GET /etc/shadow
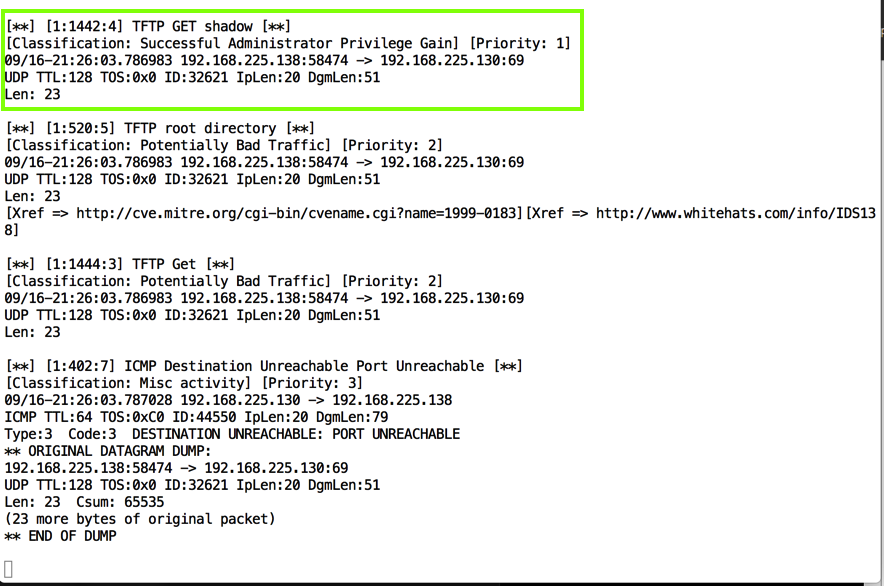
The Linux terminal should show a Snort alert detecting this traffic, as shown below.
less /etc/snort/snort.conf
Press the SPACEBAR to move down a screen at a time, and/or the up-arrow and down-arrow keys to move one line at a time, until you find the tftp.rules entry as shown below.
The TFTP alerts come from this file. To see it, press Q to exit "less" and execute this command:
less /etc/snort/rules/tftp.rules
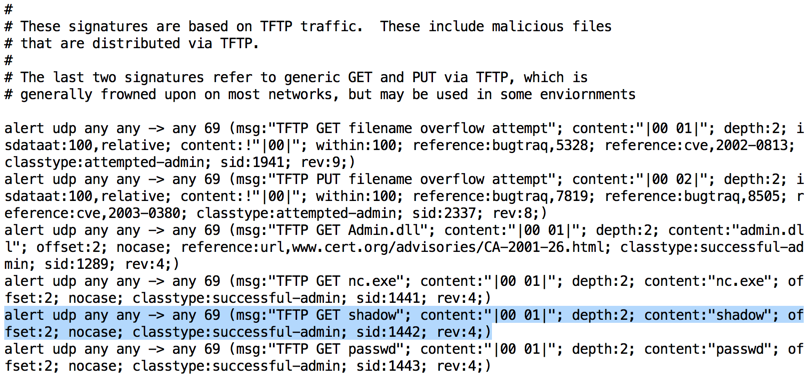
Notice the format of the rule--this is the famous "Snort Rule" format, used by many IDS products.
The pattern used by this rule is
content:"shadow"
which is a simple pattern match.
tftp 192.168.225.130 GET /theshadowknows
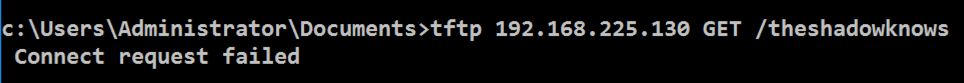
Snort sends an alert again, as shown below.
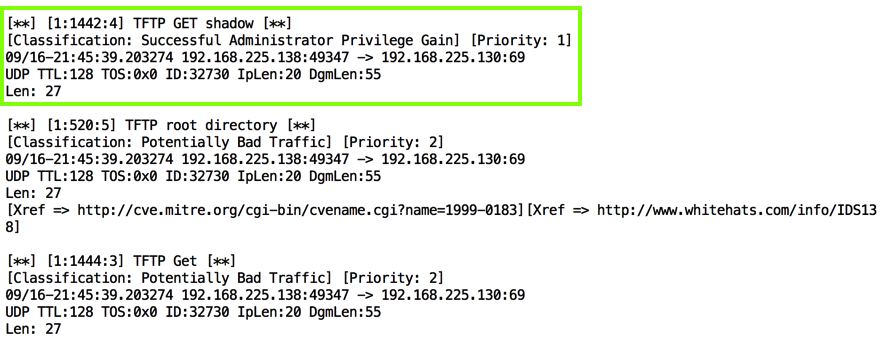
As you can see, this Snort rule is really stupid--it will trigger on any request containing the word "shadow". This is a simple, primitive form of defense.
tftp 192.168.225.130 GET AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
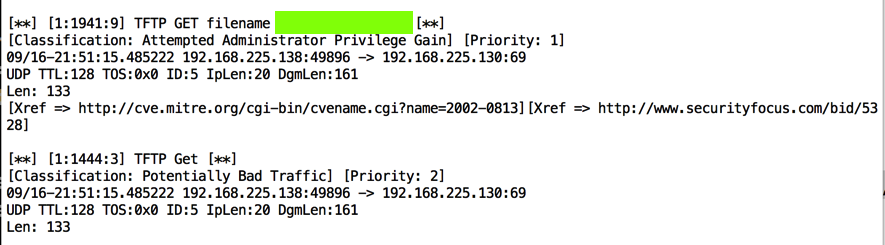
Use the form below to record your score in Canvas.
If you don't have a Canvas account, see the instructions here.
https://www.colasoft.com/packet_player/
Posted 9-16-18
tail command corrected 9-29-18