
CAUTION
This project uses traffic captured from a real malware attack. It may set off virus scanners and possibly even infect old, unpatched Windows machines.Don't do this project on a real Windows machine in normal use. Use your Windows virtual machine instead.
In this case we are using a fairly old Windows malware sample, so it's OK to use a Mac or Linux machine.
Don't use a regular Windows machine for this project, especially one used for other work, such as company machine at a workplace. However, using Windows as the host for a virtual machine is fine.
https://www.malware-traffic-analysis.net/2017/12/23/index.html
On this page, click the 2017-12-23-traffic-analysis-exercise.pcap.zip link.
infected
On the File tab, click the "Choose file" button, as shown below.

Navigate to the 2017-12-23-traffic-analysis-exercise.pcap file you unzipped and double-click it.
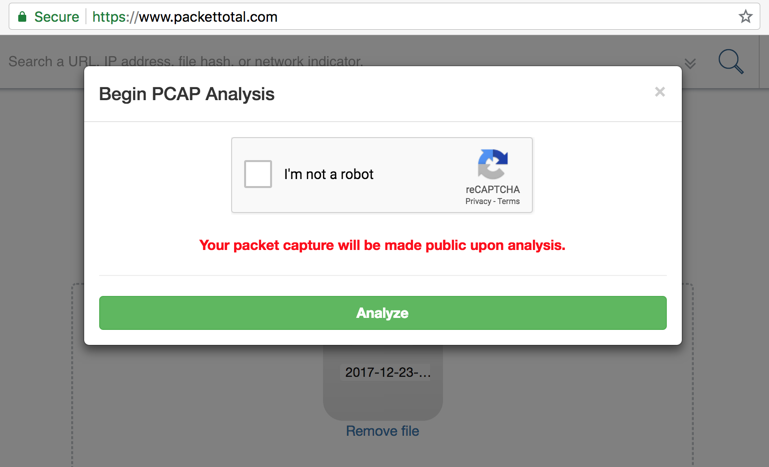
A "Begin PCAP Analysis" box pops up, as shown below, warning that the packet capture file will be made public after analysis.
That's a problem for real network data, but not for us, so check the box and click Analyze.
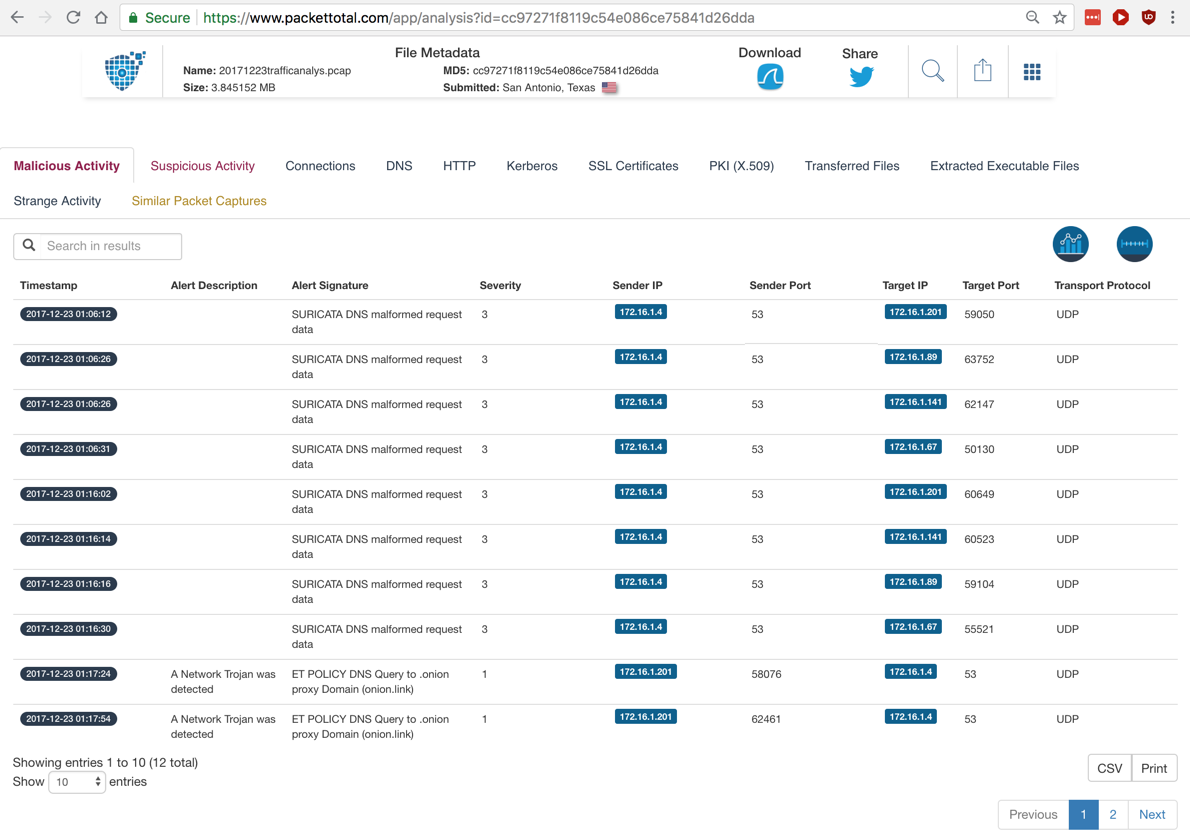
The first one may be malware traffic, but there's no further detail available here.
The second one indicates use of Tor, which is probably malicious activity also.
There are two alerts here too. The first one looks serious: a known malware hash value.
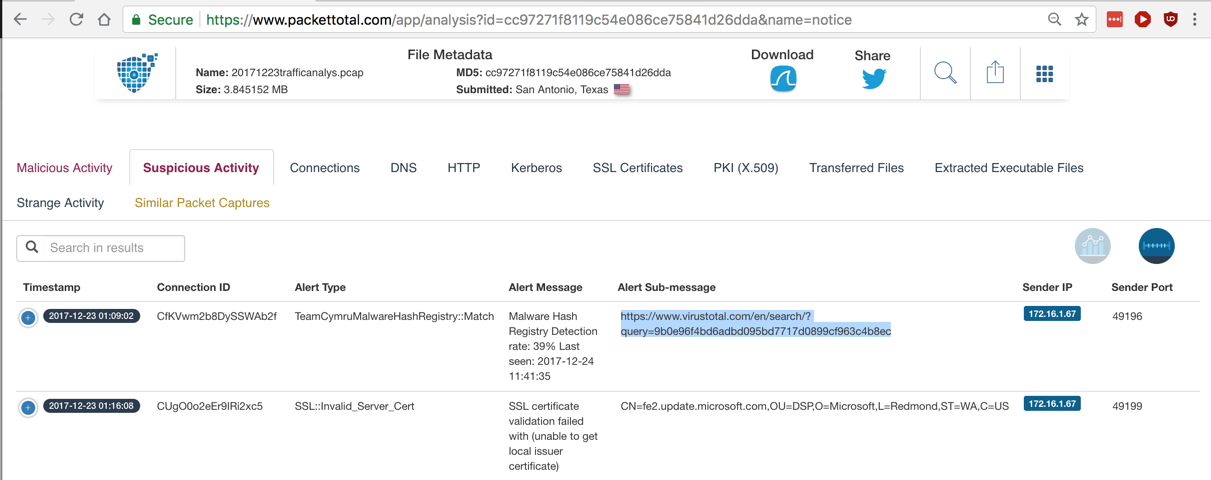
Highlight the VirusTotal URL from the alert, highlighted in the image below, copy it, and open that page.
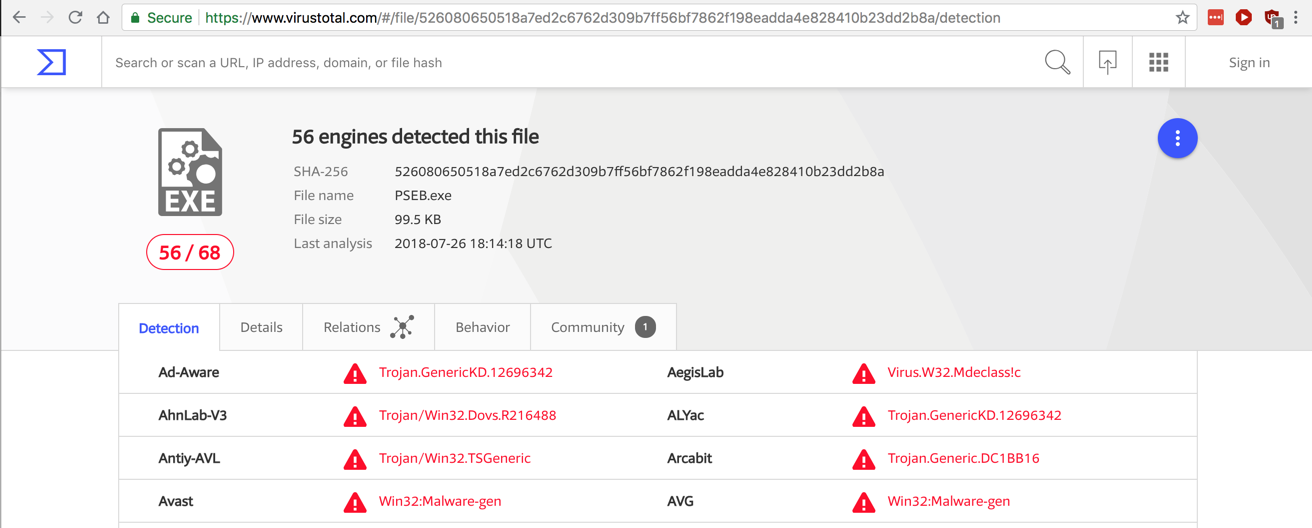
The file is detected as a Trojan, as shown below.
In VirusTotal, click the Behavior tab.
At the top left, click the round button and select the "Tencent HABO" sandbox, as shown below.
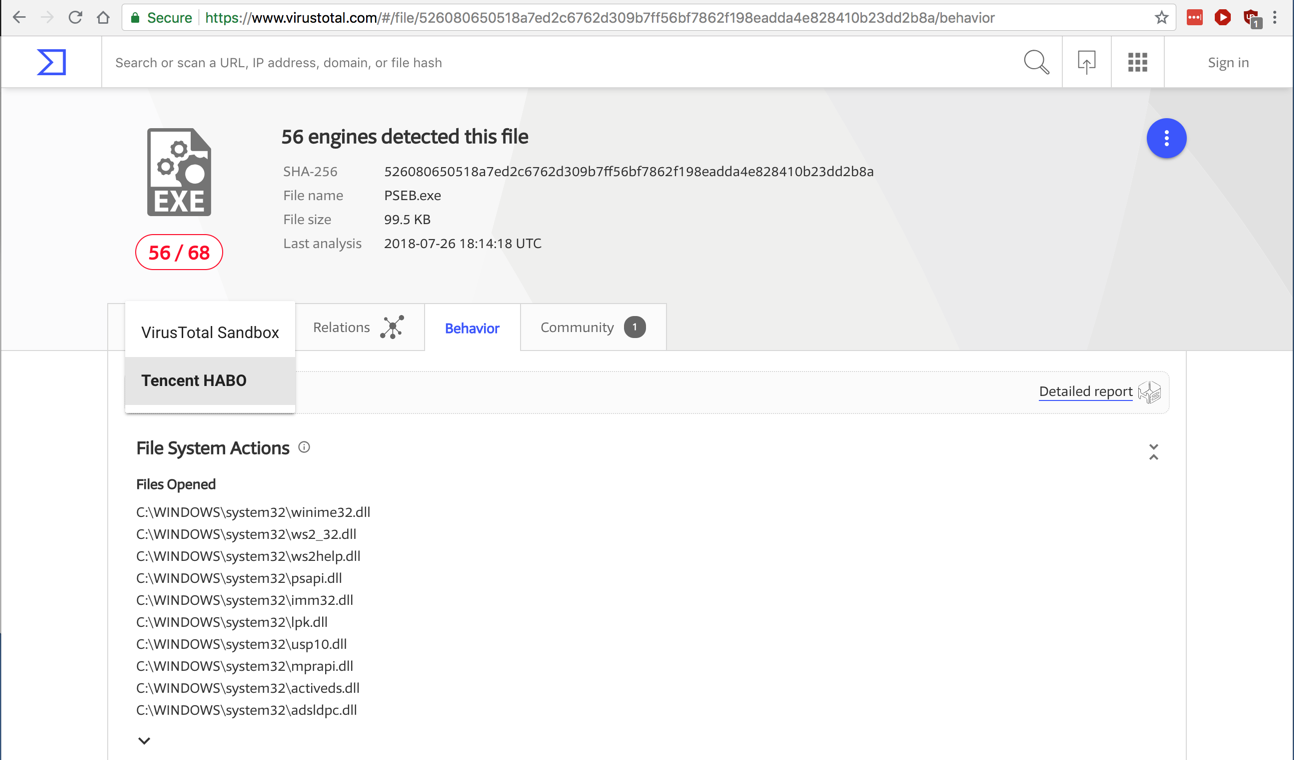
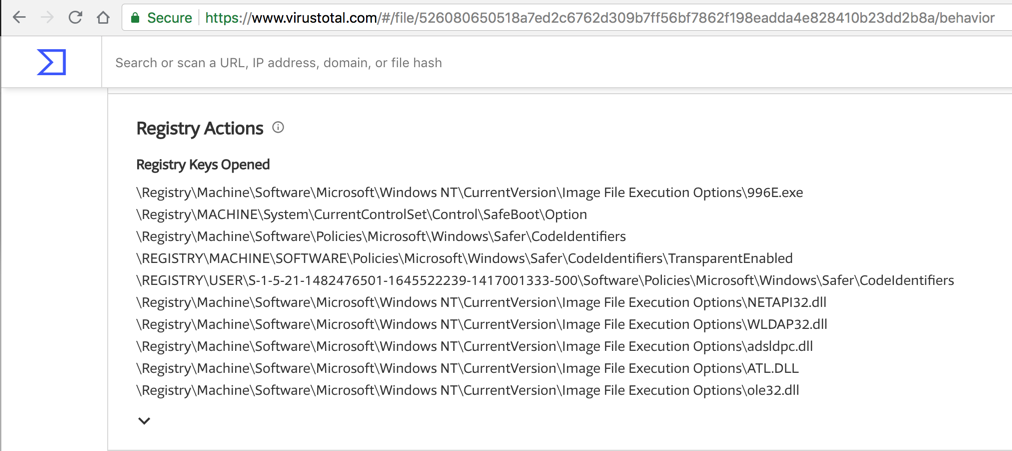
Scroll down to see "Registry Actions", as shown below. These are useful Indicators of Compromise.
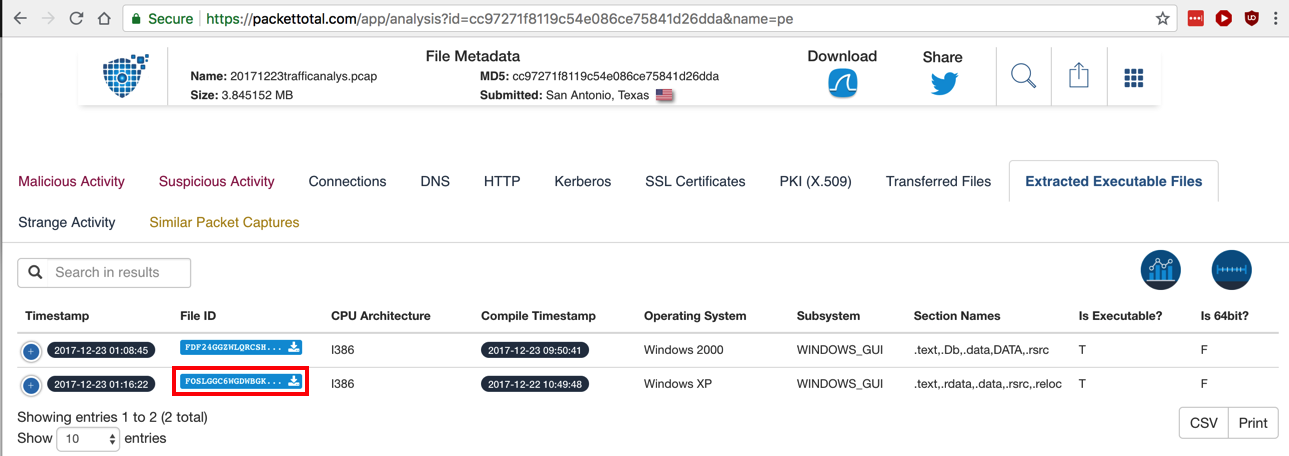
In the "File ID" column, click the little down-arrow on the right side of the second blue button to download the Windows XP executable.
Check the box to verify that you are a human.
Click Verify.
Click "Download Potentially Malicious File".
A file downloads, named "extract-1513991782.382514-HTTP-FOSLGGC6wGdwbGkB3.raw".
Upload that file to VirusTotal.
Examine its behavior in the VirusTotal Sandbox, as shown below.
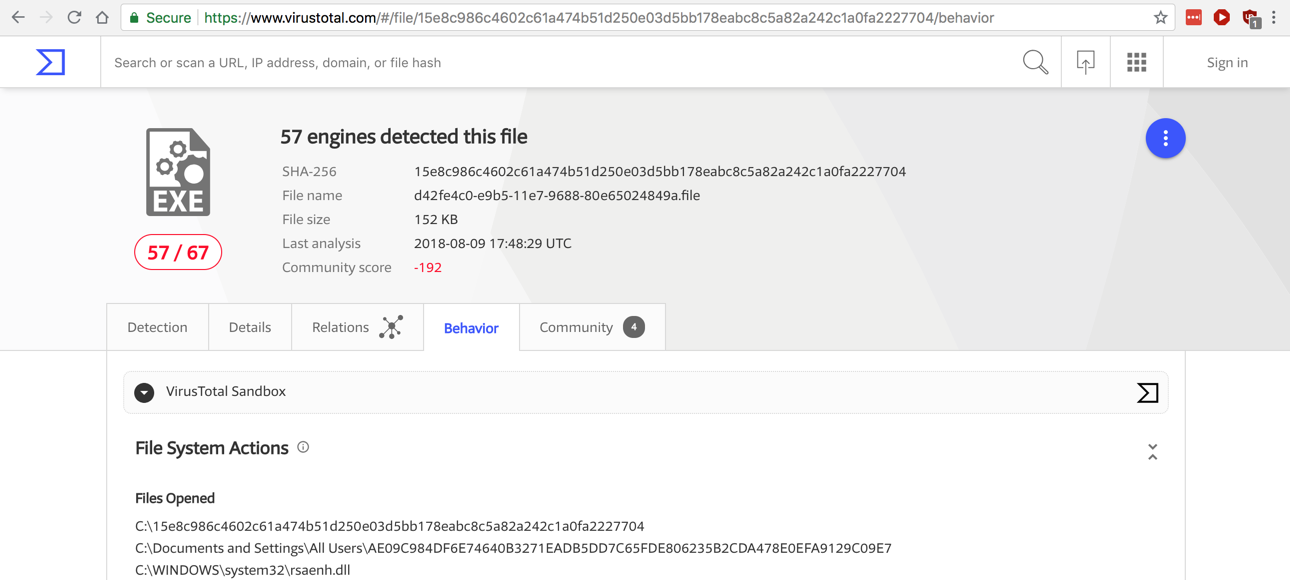
Scroll down to find the files written by this malware. Find the filename of the BMP file written to the root of C:, covered by a green box in the image below.
Use the form below to record your score in Canvas.
If you don't have a Canvas account, see the instructions here.
Posted 9-17-18
Filename fixed 10-29-18