sudo apt update
sudo apt install squid -y
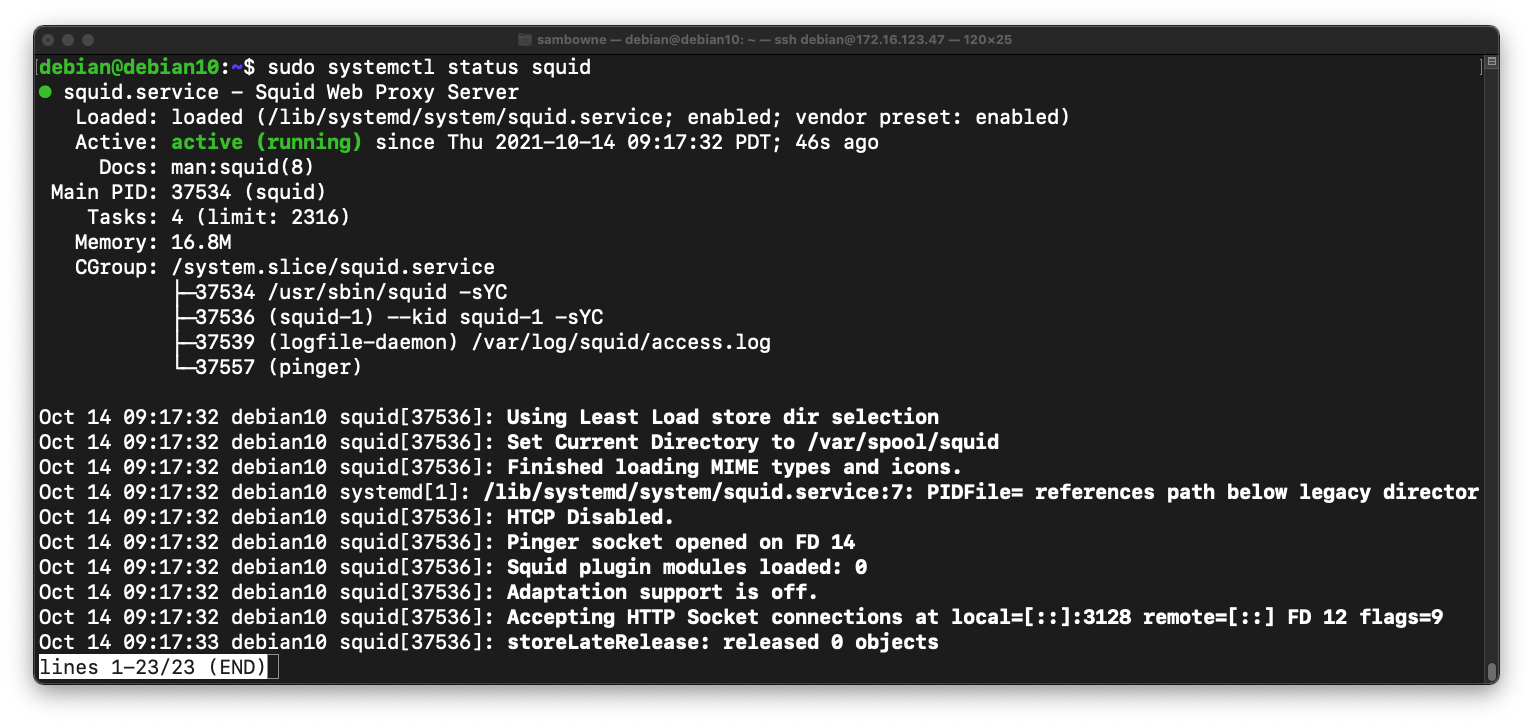
sudo systemctl status squid
To exit the status page, press q

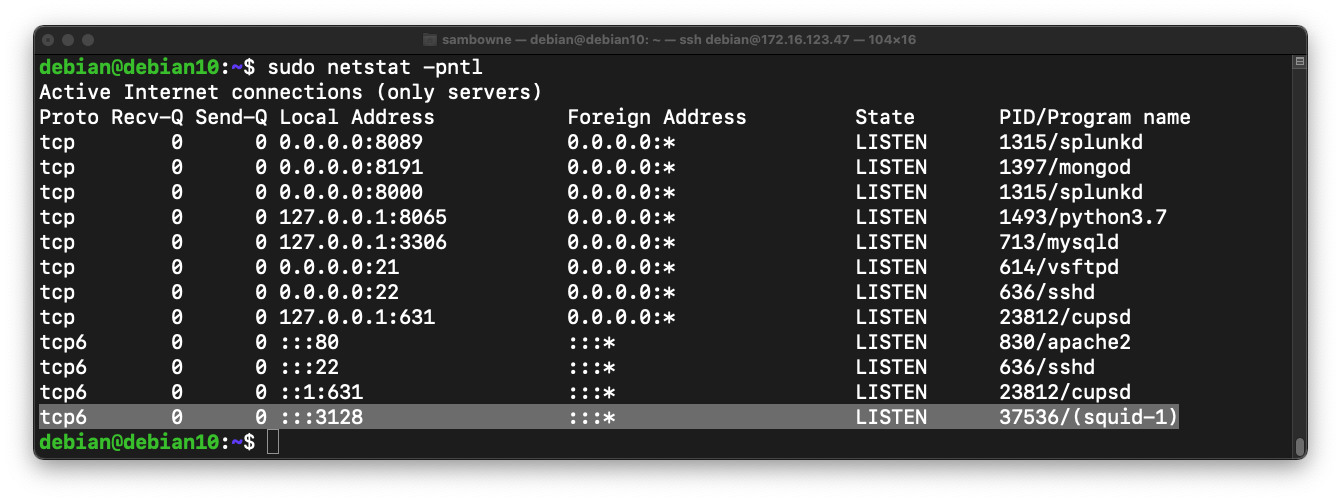
sudo netstat -pntl
sudo cp /etc/squid/squid.conf /etc/squid/squid.conf.orginal
sudo nano /etc/squid/squid.conf
http_access allow localhost
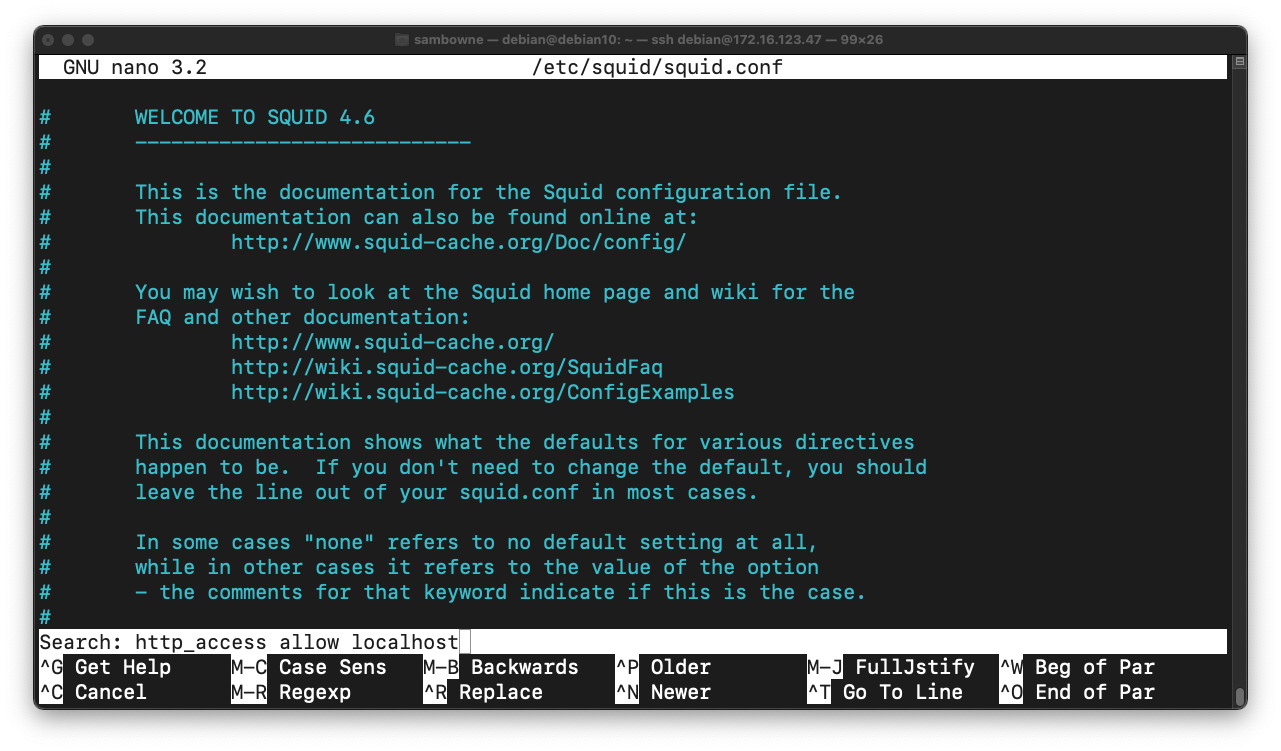
Press Enter. Press Ctrl+W. Press Enter again.
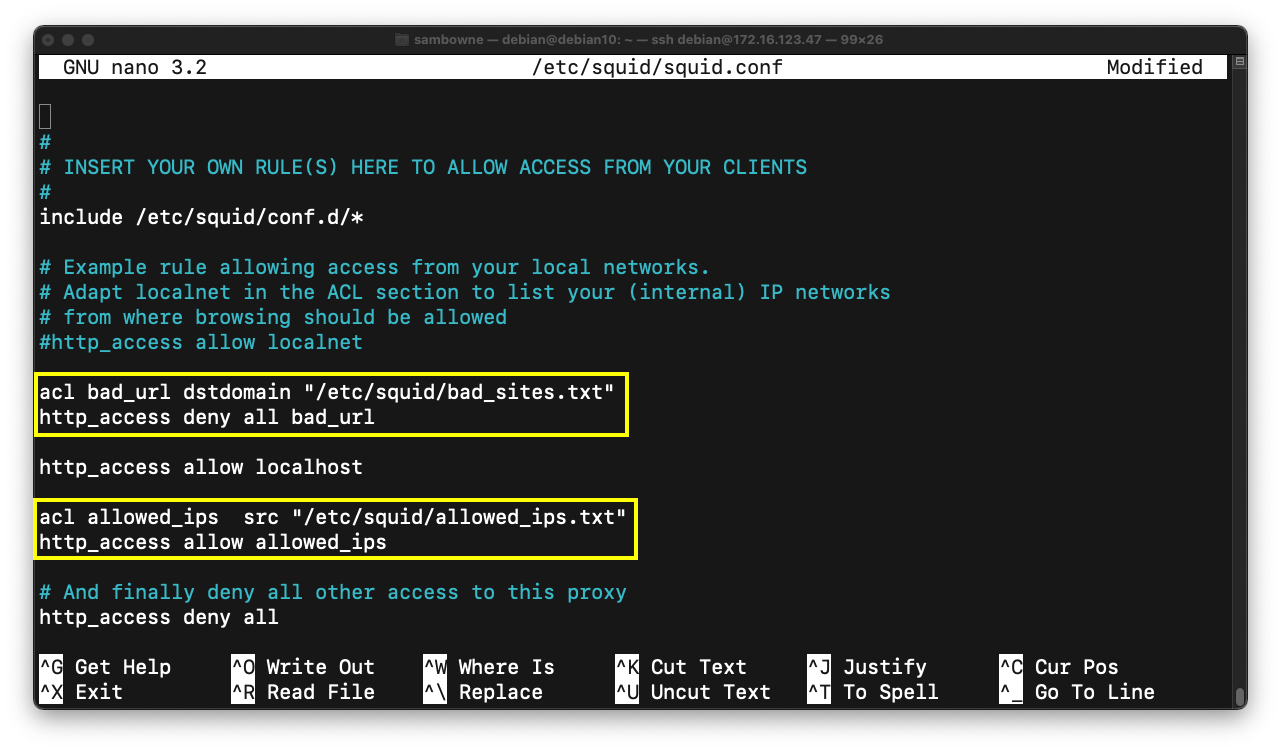
You see a message saying "INSERT YOUR OWN RULE(S) HERE", as shown below.
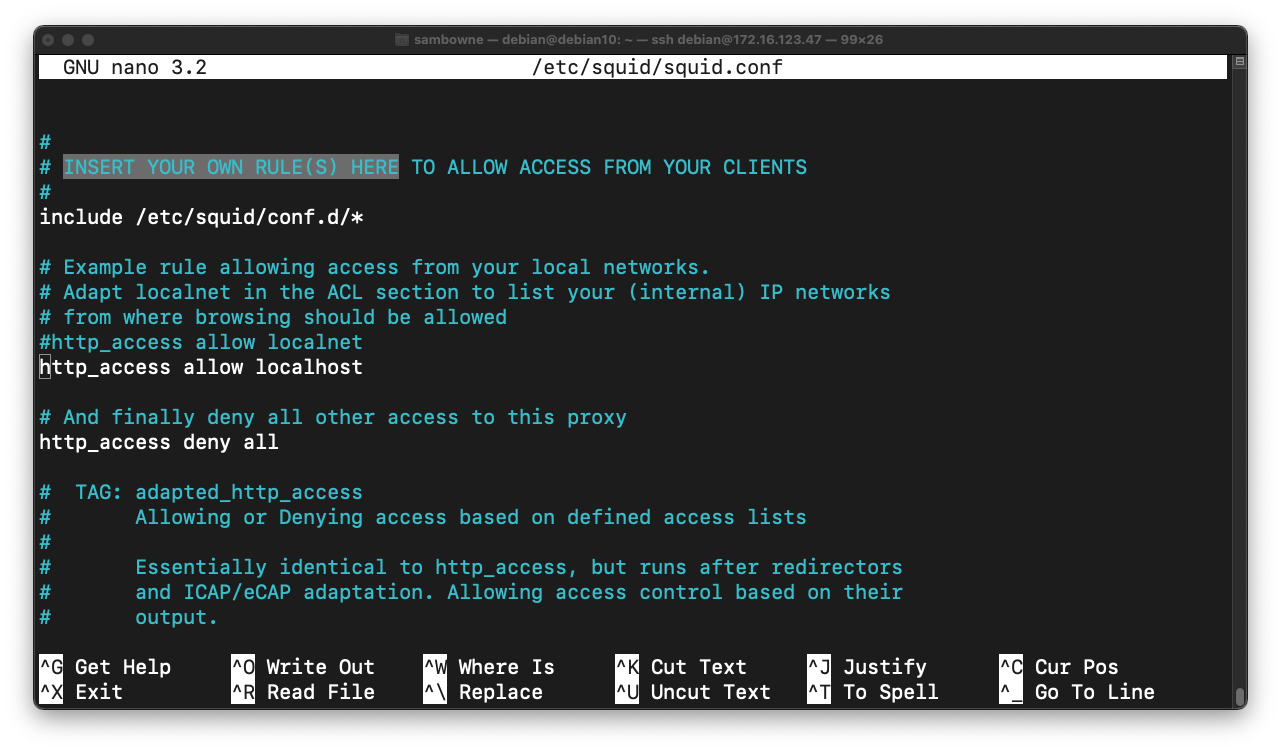
Above the "http_access allow localhost" line, insert these two lines, outlined in yellow in the image below.
These lines block access to domains in the "/etc/squid/bad_sites.txt" file.
acl bad_url dstdomain "/etc/squid/bad_sites.txt"
http_access deny all bad_url
These lines allow client machines in the "/etc/squid/allowed_ips.txt" file to use the proxy.
acl allowed_ips src "/etc/squid/allowed_ips.txt"
http_access allow allowed_ips
Save the file with Ctrl+X, Y, Enter.
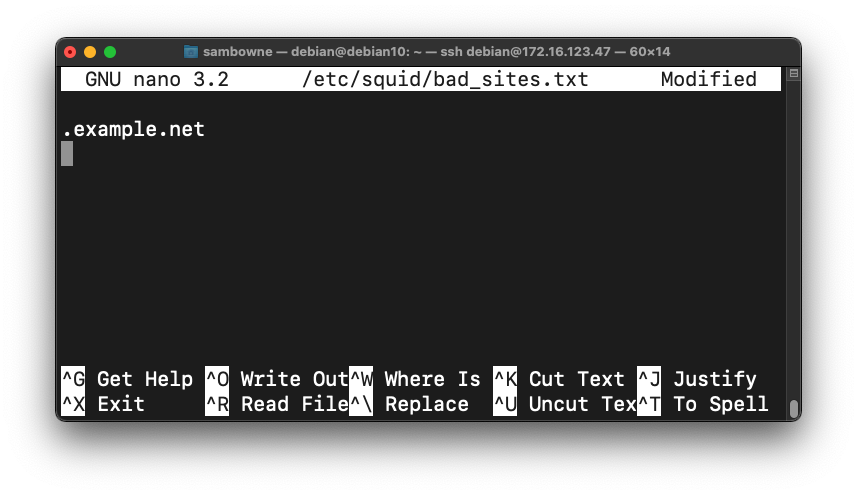
sudo nano /etc/squid/bad_sites.txt
.example.net
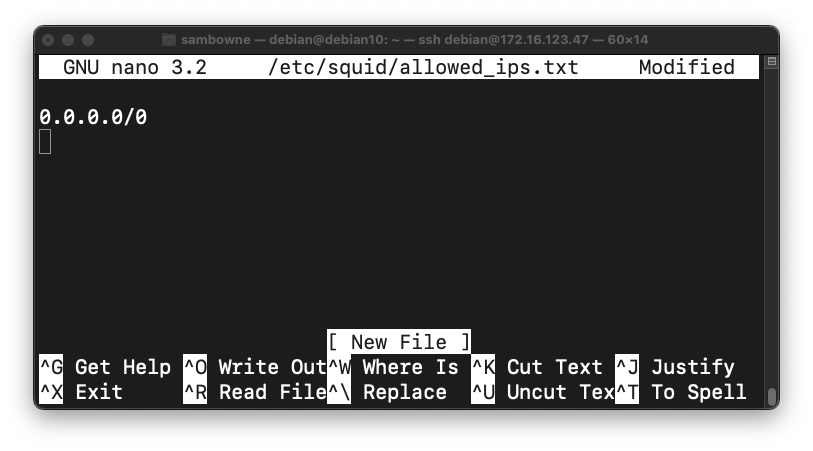
sudo nano /etc/squid/allowed_ips.txt
0.0.0.0/0
sudo systemctl restart squid
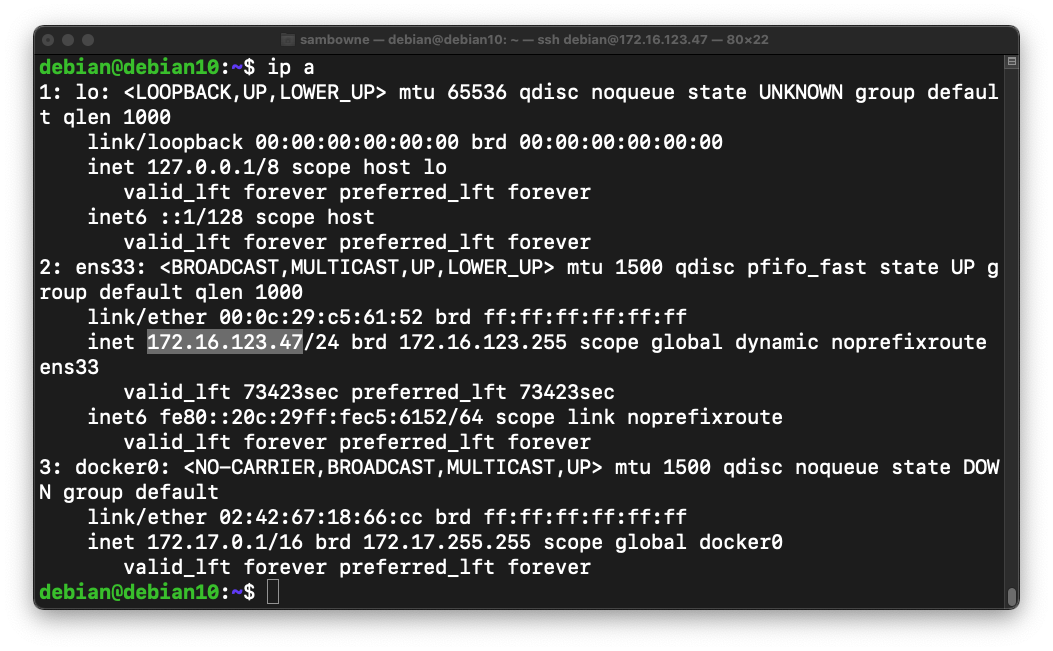
ip a
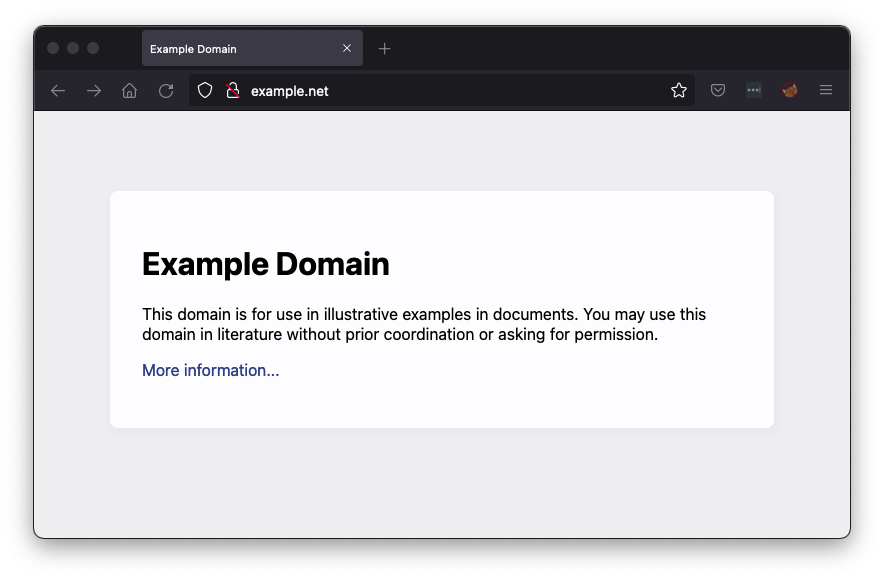
In Firefox, go to example.net
A simple Web page opens, as shown below.
In Settings, search for proxy.
On the "Network Settings" line, click the Settings... button.
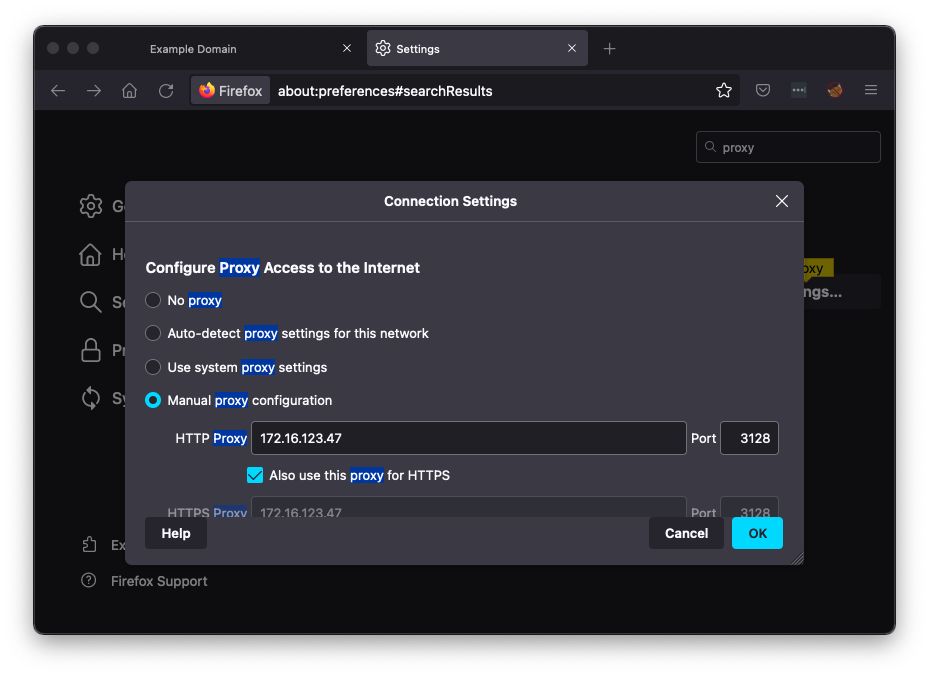
In the Connection Settings box, in the HTTP proxy field, enter your proxy's IP address and a Port of 3128, as shown below.
Then click OK.
IR 383.1: Message (10 pts)
In Firefox, return to the tab showing example.net. Refresh the page.Access is denied, as shown below.
The flag is covered by a green rectangle in the image below.
IR 383.2: Indicators of Attack (10 pts)
In IR 382, you collected URLs from Phishtank for the time range 2:00 - 2:10 on 2018-05-25. These are "Indicators of Attack" -- traffic to these domains indicate phishing attempts in progress.Generate a list of domain names from those URLs and put them into the /etc/squid/bad_sites.txt file, as shown below.
Hint: use "cut" to trim the URL down to just the domain names.
Restart Squid.
In Firefox, go to these URLs, one at a time. (Remove the spaces before and after the periods.):
lillynx .comTo see the flag, execute this command, which shows the squid logs. Find the last portion of the second request to "itruckinginc.com".
apps-secure . com
itruckinginc . comThe flag is covered by a green rectangle in the image below.
IR 383.3: Indicators of Compromise (10 pts)
In IR 382, you collected Command & Control IPs from Anomali for the date Oct 12, 2021. These are "Indicators of Compromise" -- traffic to these addresses indicate malware infections phoning home.Copy that list of IPs to /etc/squid/bad_ips.txt, as shown below.
Adjust the Squid configuration line to use the bad_ips.txt file, adding the two lines outlined in yellow in the image below.
Restart Squid.
In Firefox, go to these IPs, one at a time. (Remove the spaces before and after the periods.)
1 . 1 . 1 . 1To see the flag, execute this command,:
41 . 86 . 42 . 158The flag is covered by a green rectangle in the image below.
Posted 10-14-21