https://oasis-open.github.io/cti-documentation/
Read the description of STIX, as shown below.

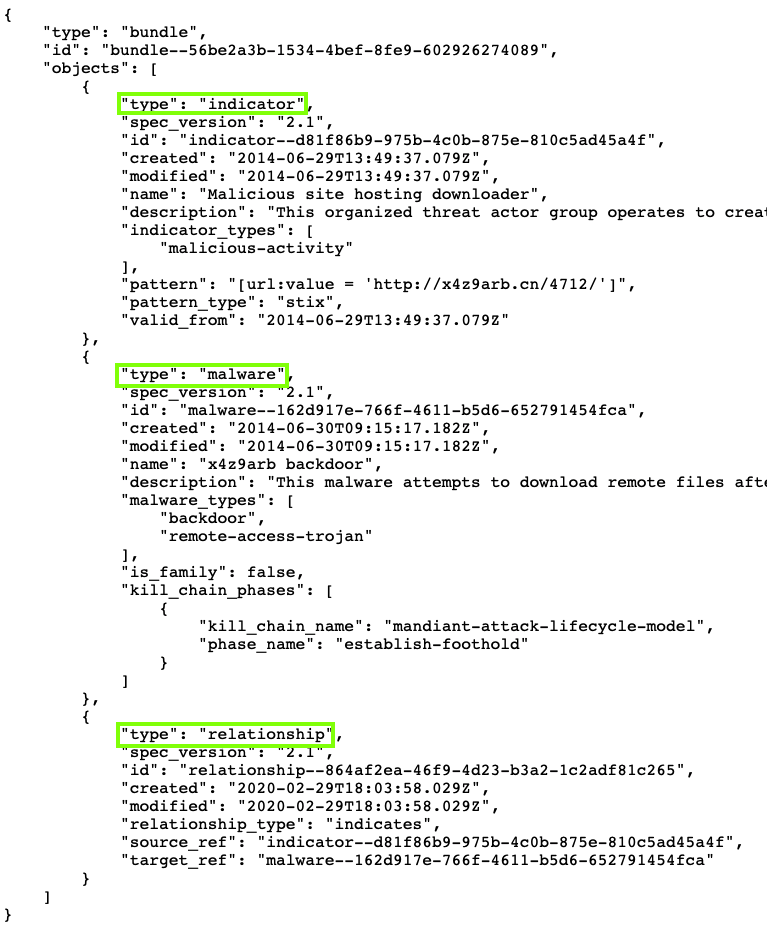
There are three objects, with types of indicator, malware, relationship, outlined in green in the image below.
The indicator has a pattern that can be used to detect this event, a URL in this case.
The malware has a malware_types property indicating its action, and a kill_chain_phase property indicating when an attacker uses it.
The relationship connects the indicator to the malware.
https://oasis-open.github.io/cti-stix-visualization/
In the second field, paste in this URL, as shown below:
https://raw.githubusercontent.com/oasis-open/cti-documentation/master/examples/example_json/indicator-for-malicious-url.json
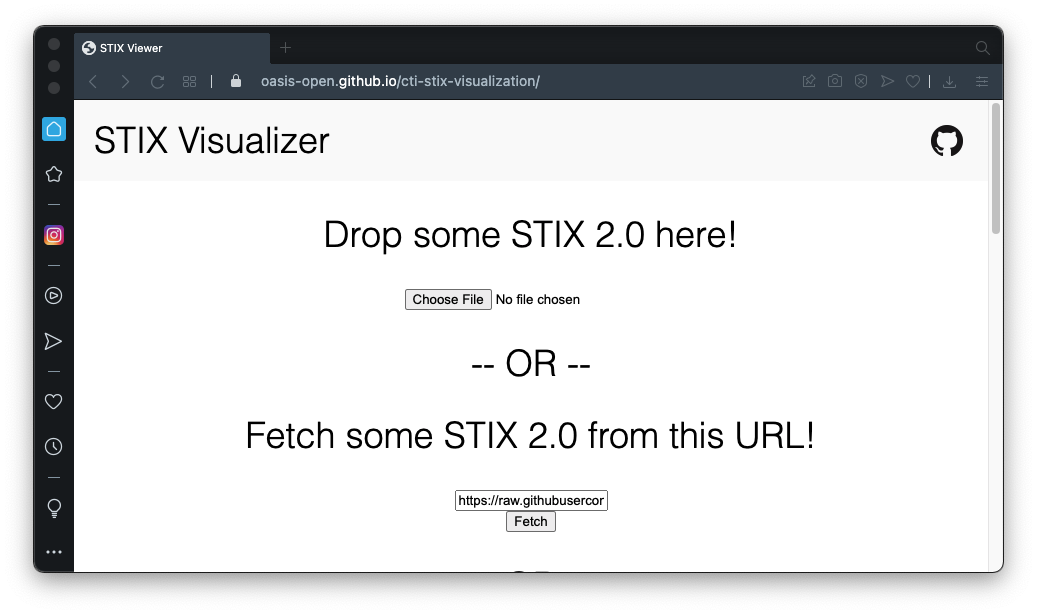
Click the Fetch button.
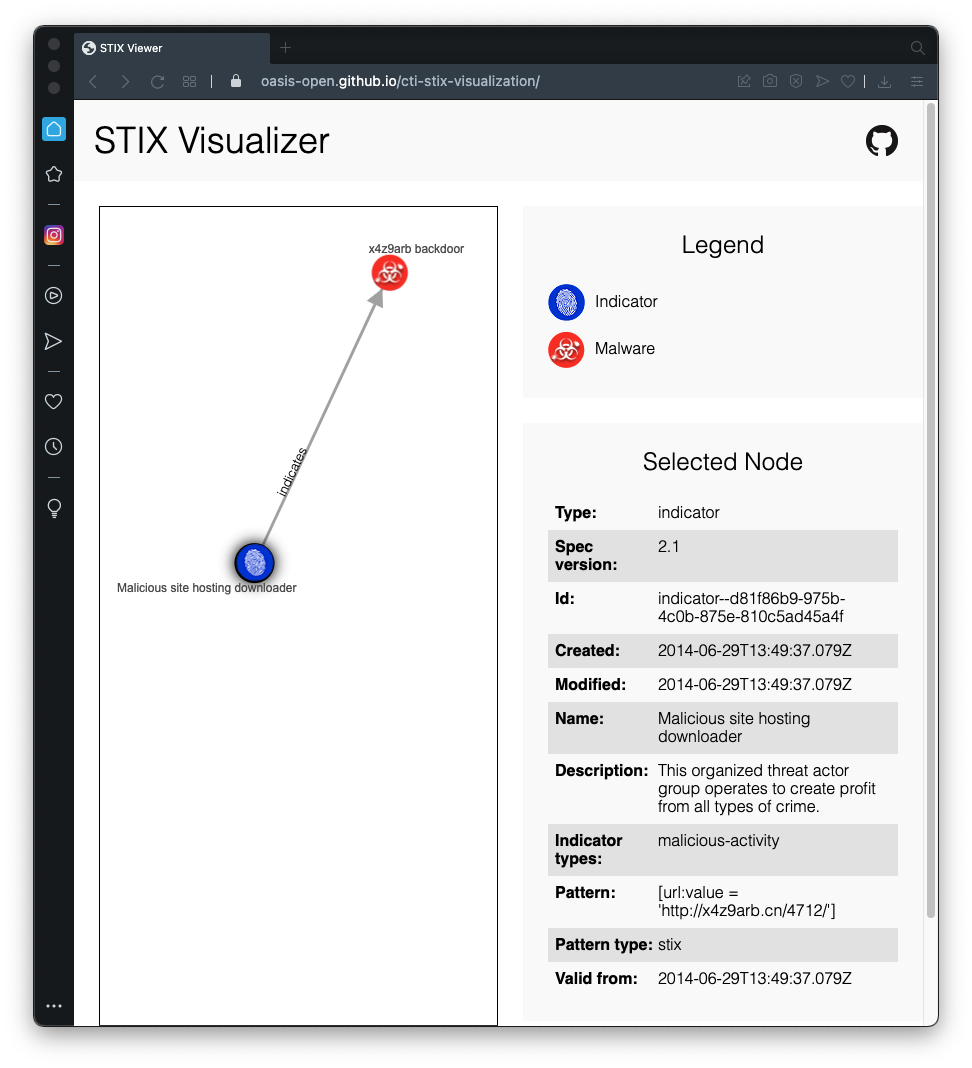
The STIX information appears in an interactive manner that is easier to read, as shown below.
IR 380.1: Threat Actor Type (10 pts)
Examine this STIX file in the visualizer.https://raw.githubusercontent.com/oasis-open/cti-documentation/master/examples/example_json/threat-actor-leveraging-attack-patterns-and-malware.jsonThe flag is covered by a green rectangle in the image below.
IR 380.2-5: APT1 (10 pts)
Examine this STIX file in the visualizer.https://oasis-open.github.io/cti-documentation/examples/example_json/apt1.jsonThis is a big chart from the original APT1, the 2010 report from Mandiant that shocked the world and launched the modern field of Incident Response.Find these flags. Each flag is worth 5 pts.
- IR 380.2 Examine the attack-pattern "Initial Compromise" and find APT1’s most commonly used technique.
- IR 380.3 Examine the tool "gsecdump". What is its Tool Types value?
- IR 380.4 Examine the identity "JackWang". What is his email address?
- IR 380.5 Examine the FQDN indicators. Which one ends in .net? The flag is that FQDN.
Posted 10-7-21
JSON URL fixed 11-1-21
Documentation URL fixed 7-13-22