Execute the steps below on your Windows machine.
Otherwise, follow the appropriate steps below for your Windows version:
Windows 10
1. Next to the Start button, search for "Defender". Open "Windows Security settings" or "Windows Defender settings".
2. Click "Virus & threat protection".
3. Under "Virus & threat protection settings", click "Manage settings".
4. Turn off "Tamper Protection".
5. Under Exclusions, click "Add or remove exclusions". Click "Add an exclusion", Folder. Double-click C:\. Click "Select Folder". At the top left, click the back-arrow.
6. Turn off "Cloud-delivered protection" and "Automatic sample submission".
Windows 11
1. Next to the Start button, search for "Virus". Open "Virus & threat protection".
2. Under "Virus & threat protection settings", click "Manage settings".
3. Turn off "Tamper Protection".
4. Under Exclusions, click "Add or remove exclusions". Click "Add an exclusion", Folder. Double-click C:\. Click "Select Folder". At the top left, click the back-arrow.
5. Turn off "Cloud-delivered protection" and "Automatic sample submission".
1. Download this file: https://samsclass.info/152/proj/pup4.zip
2. Open your Downloads folder. Right-click pup4.zip. Click "Extract All...". Click Extract. Use the password "malware".
3. Open the pup4 folder. Right-click pup4.exe and click "Run as administrator". If a "Windows protected your PC" box pops uo, click "More info" and click "Run anyway". If a "User Account Control" box pops up, click Yes.
4. Move the pup4message.exe file to C:\
5. Return to your Downloads folder. Delete pup4.zip and the pup4 folder. Empty the Recycle Bin.
6. Restart your Windows virtual machine. If an "Open File - Security Warning" box pops up, uncheck the "Always ask before opening this file" box and click Run.
7. If you see a box saying "The code execution cannot proceed becauee VCRUNTIME140.dll was not found", open a Web browser, search for "Microsoft Visual C++ Redistributable download" and install the latest version for x86, even if you are running Windows on Apple ARM64.
Then restart your virtual machine again.
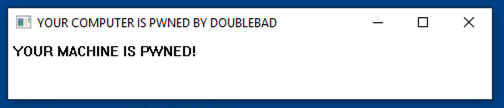
8. If you are using Windows 10, an irritating message pops up, as shown below.
9. If you are using Windows 11, the message may fail to pop up. To unblock it, open Task Manager, go to the Startup tab, and unblock c:\pup4message.exe. Then restart your machine again.

T1204.002: User Execution: Malicious File
T1547.001: Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder
T1562.001: Impair Defenses: Disable or Modify Tools
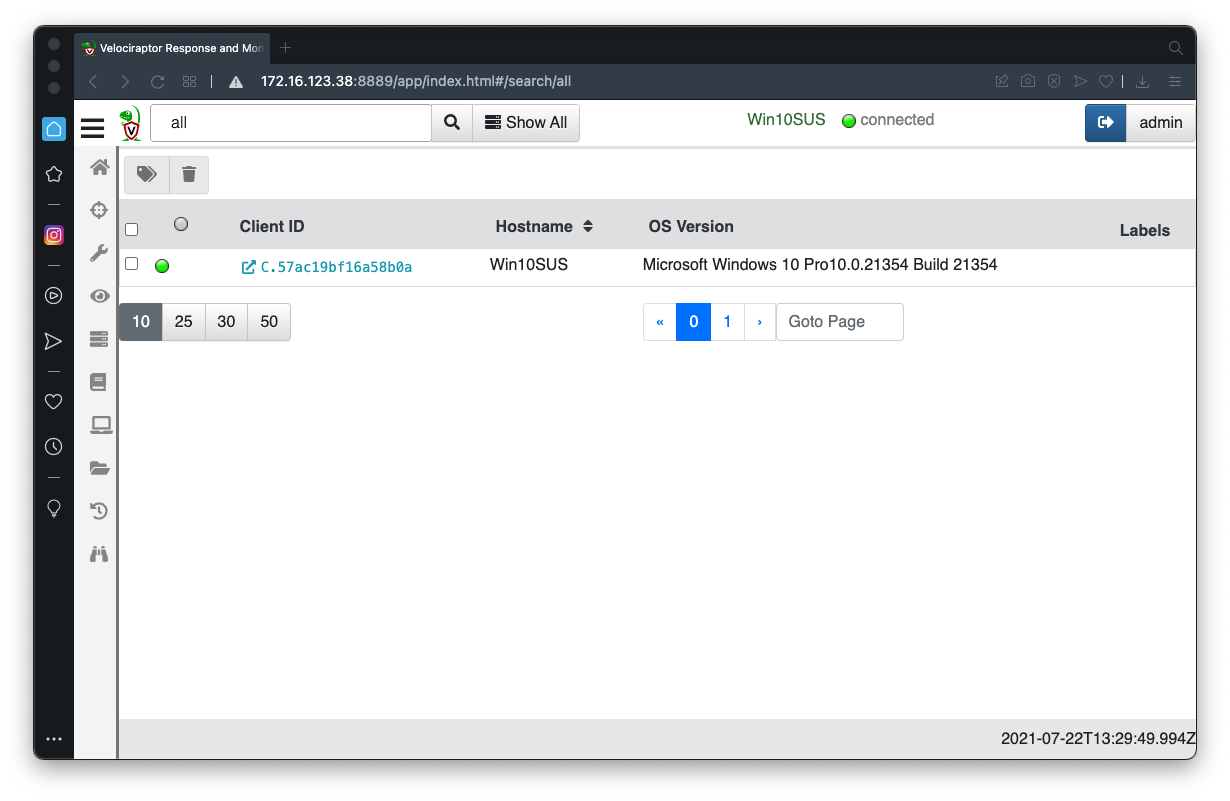
In the Velociraptor GUI, at the top left, click the down-arrow next to the search box. Click "Show All".
Click your client's Client ID, which appears in green text, as shown below.
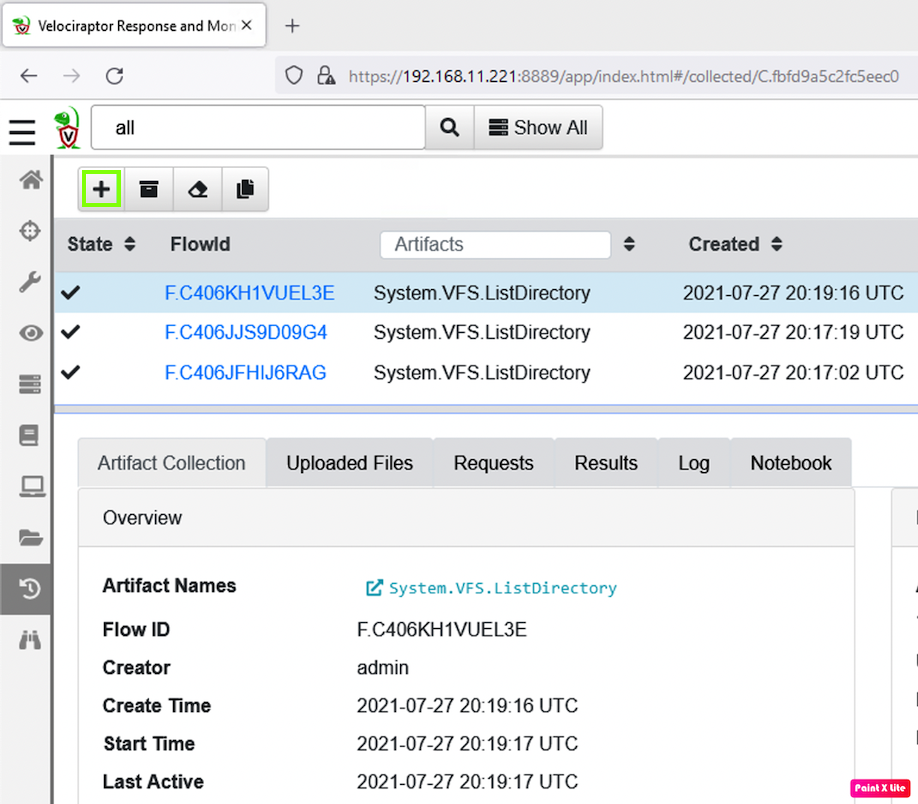
At the top left, click the plus-sign, outlined in green in the image below.
Use the search box to find this collector, as shown below.
Windows.Sysinternals.Autoruns
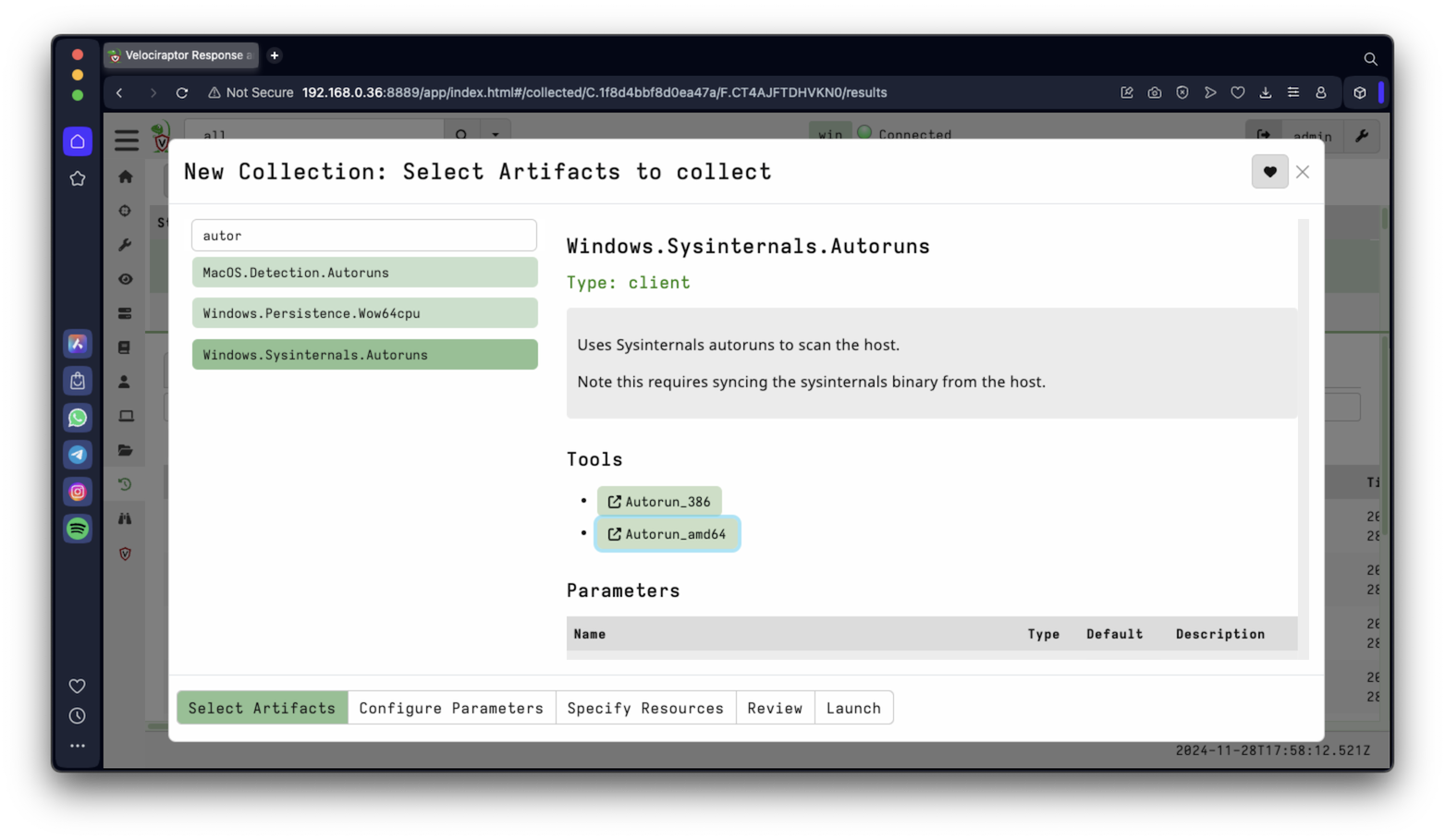
Launch the collector with the default parameters.
Windows on ARM
If you are using windows on ARM, you need to do these steps to prepare the correct executable in Velociraptor.On your host machine go to this URL:
https://learn.microsoft.com/en-us/sysinternals/downloads/autoruns
Download Autoruns.zip. Unzip it. Inside find the autorunsc64a.exe file.When you see the Velociraptor image shown above this box, on the right side, under Tools, click Autorun_amd64.
Click in the "Click to upload file" box, and navigate to the autorunsc64a.exe file, and click it.
Your screen should look like the image below.
Then launch the artifact collector as usual.
It finds a lot of records: 1355 when I did it.
In the top pane, click Windows.Sysinternals.Autoruns.
In the bottom pane, click the Results tab.
Download a CSV by clicking the button outlined in red in the image below.
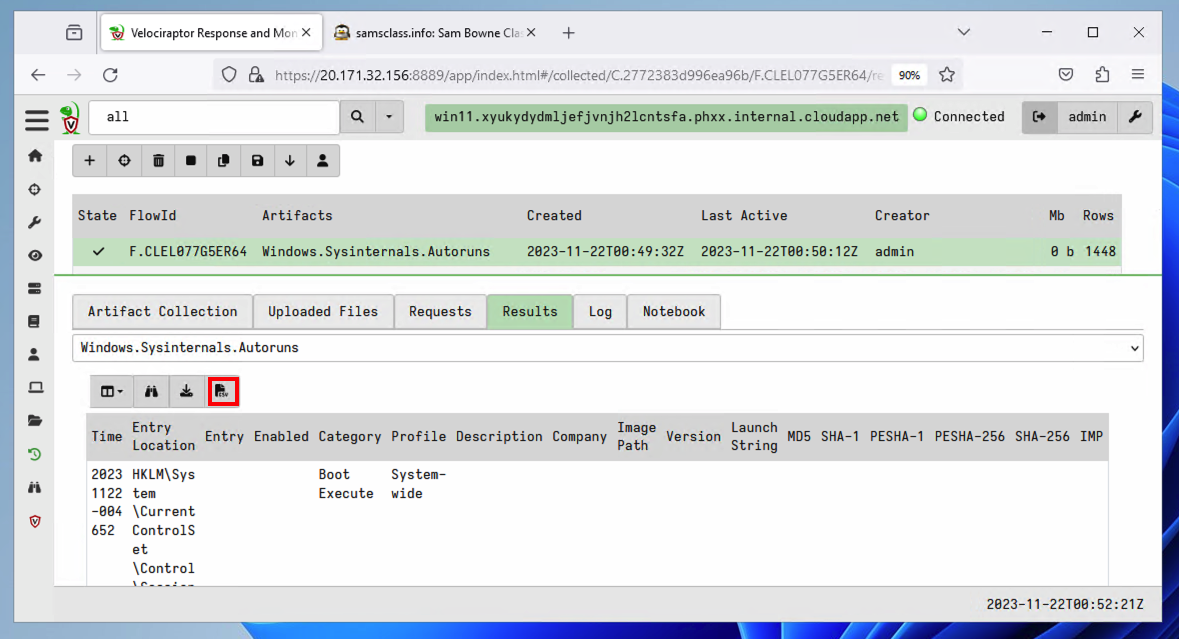
IR 372.1: Run Key (10 pts)
Open the CSV with Notepad or another text editor and find the Run key used to launch PUP4message.exe.The flag is covered by a green rectangle in the image below.
IR 372.2: MD5 of EXE (5 pts)
Launch this collector:Windows.System.PslistFind the MD5 hash of the EXE used to launch the process. From the previous flag, you know the executable is named PUP4message.exe, so configure a ProcessRegex of PUPThe flag is covered by a green rectangle in the image below.
IR 372.3: Process Memory (10 pts)
The purpose of this step is to verify that the "pup4message" process is actually creating the pop-up message.Launch this collector:
Windows.Memory.ProcessDumpConfigure a ProcessRegex of PUPAcquire the memory of the PUP's process. The acquired memory dump is on the "Uploaded Files" tab, and you can download it to your local system by clicking on the path below the header "vfs_path", as shown below.
Move the DMP to Debian for safe analysis, using drag-and-drop or the scp command.
Extract the Unicode strings containing "BAD", as shown below
To install strings, execute these commands:
The flag is covered by a green rectangle in the image below.
IR 372.4: Yara (5 pts)
The purpose of this step is to see if other EXE files on the target computer are also involved.Launch this collector:
Windows.Search.YaraFind all EXE files containing the Unicode string "PWNED", as shown below.
The flag is covered by a green rectangle in the image below.
Click your client's Client ID, which appears in green text.
At the top right, click the Shell button.
IR 372.5: Remediation (5 pts)
The purpose of this step is to remove the malware from the client.Launch these commands, one at a time:
TASKKILL /FI "IMAGENAME eq pup4message.exe"Click the "eye" icons to see the results of the commands.reg delete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run /v PUP4 /f
del c:\pup4message.exe
The flag is covered by a green rectangle in the image below.
IR 372.6: Remediation (5 pts)
The purpose of this step is to remove the malware from the client.Look at the Windows client. The pop-up message is still there! The Velociraptor shell doesn't seem to work for this purpose.
On the Windows client, in an Administrator Command Prompt, execute these commands, one at a time:
TASKKILL /FI "IMAGENAME eq pup4message.exe"The flag is covered by a green rectangle in the image below.reg delete HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run /v PUP4 /f
del c:\pup4message.exe
Posted 7-30-2021
Note about Microsoft Visual C++ 2015 Redistributable Update 3 RC added 10-30-21
Azure workaround added 11-4-21
Flag 4 instructions updated with warning about Velociraptor versions 10-24-22
Updated, warning added to flag 3 and removed from flag 4, 22-21-23
Video added 4-17-24
Minor error removed from flag 6 instructions 4-30-24
Updated for Windows 11 11-28-24
Typo fixed 12-10-24
Unblocking and autorunsc64a tips added 10-4-25