sudo apt update
sudo apt install cmake make gcc g++ flex bison -y
sudo apt install libpcap-dev libssl-dev python-dev swig zlib1g-dev -y
sudo apt install zlib1g-dev wget curl -y
curl -fsSL https://download.opensuse.org/repositories/security:zeek/Debian_12/Release.key | \
gpg --dearmor | sudo tee /etc/apt/trusted.gpg.d/security_zeek.gpg > /dev/null
echo 'deb http://download.opensuse.org/repositories/security:/zeek/Debian_12/ /' | \
sudo tee /etc/apt/sources.list.d/security:zeek.list
sudo apt update
sudo apt install zeek-lts -y
cd
echo "export PATH=/opt/zeek/bin:$PATH" >> .bashrc
source .bashrc
sudo /opt/zeek/bin/zeek -i ens4 -C &
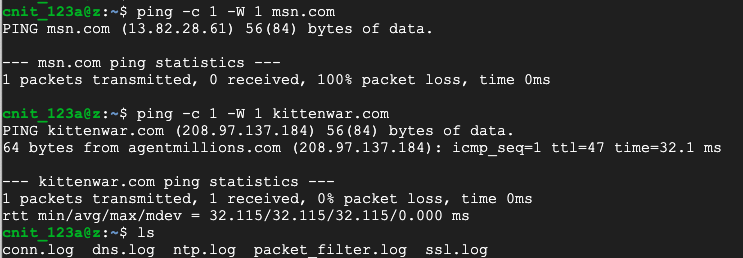
ping -c 1 -W 1 msn.com
ping -c 1 -W 1 kittenwar.com
ls

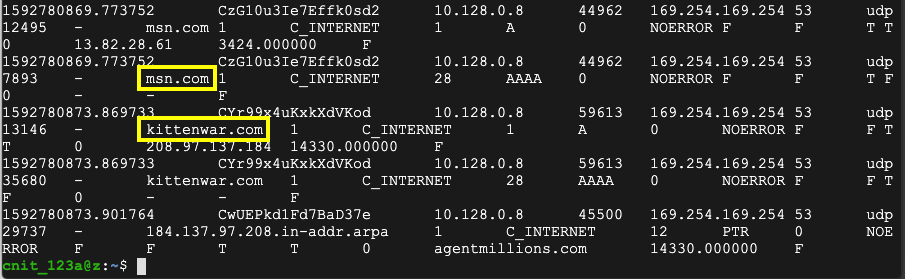
cat dns.log
wget http://ad.samsclass.info
Flag IR 351.1: HTTP Log (5 pts)
On your Linux server, in an SSH session, execute this command:The flag is covered by a green rectangle in the image below.
sudo nano /opt/zeek/share/zeek/base/protocols/http/main.zeek
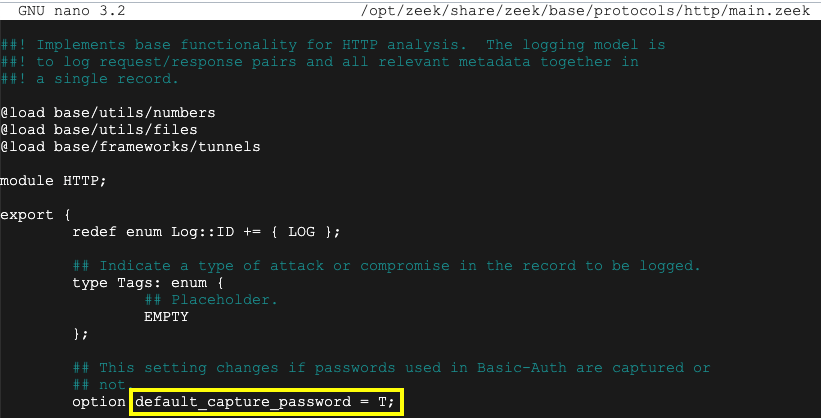
Press Ctrl+X, Y, Enter to save the file.
On your Linux server, in an SSH session, execute these commands to download a PCAP file to examine and process it with Zeek:
sudo rm http.log
wget https://samsclass.info/152/proj/http-basic.pcap
sudo /opt/zeek/bin/zeek -r http-basic.pcap -C
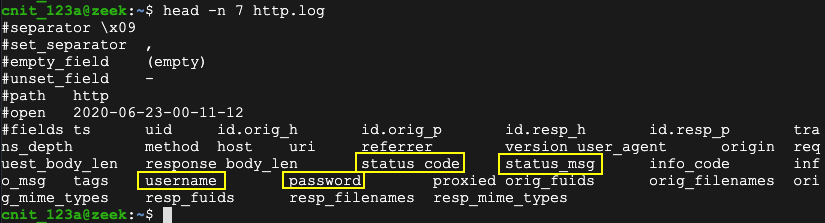
head -n 7 http.log
username password status_code status_msgas shown below.
Zeek provides a zeek-cut utility to make it easier to pick out fields like that.
Flag IR 351.2: HTTP Password (5 pts)
On your Linux server, in an SSH session, execute this command:The flag is the password for the successful login, covered by a green rectangle in the image below.
Flag IR 351.3: HTTP PIN (10 pts)
On your Linux server, in an SSH session, execute this command:The flag is the password for the successful login.
nano notice_ssh_guesser.zeek
@load protocols/ssh/detect-bruteforcing
redef SSH::password_guesses_limit=10;
hook Notice::policy(n: Notice::Info)
{
if ( n$note == SSH::Password_Guessing )
add n$actions[Notice::ACTION_EMAIL];
}
Flag IR 351.4: SSH Brute Force Alert (5 pts)
On your Linux server, in an SSH session, execute this command:The flag is covered by a green rectangle in the image below.