http://virustotal.github.io/yara/
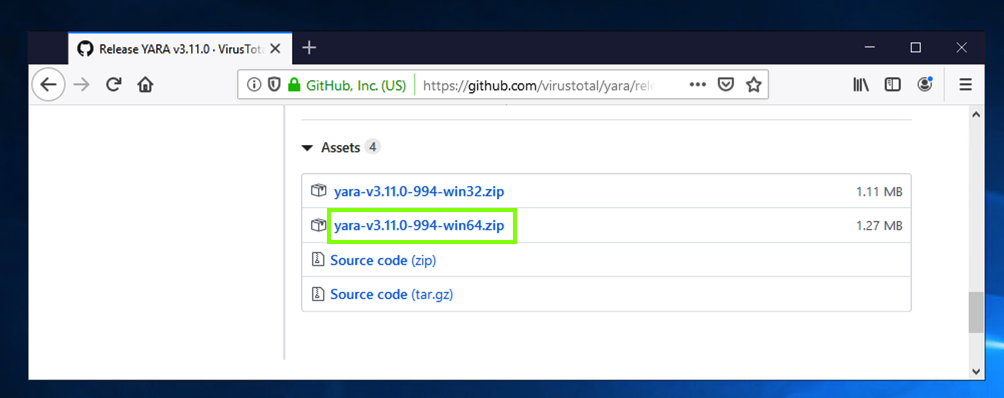
On the right side, click the "Download Latest Release" button.
On the next page, at the bottom, click the win64 version, as shown below.

Save the file. Right-click the downloaded file, click "Extract All...", Extract.
A folder with two files appears, as shown below.
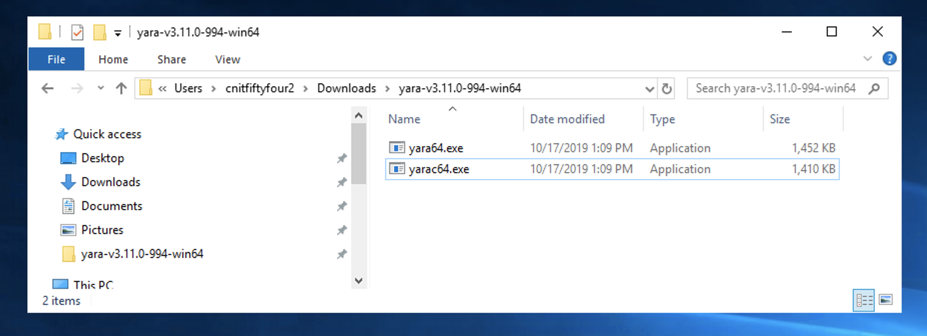
Drag both files to the left pane and drop them on Downloads.
In the left pane, click Downloads.
The files appear, as shown below.
In the Command Prompt window, execute these commands:
cd Downloads
notepad test.yar
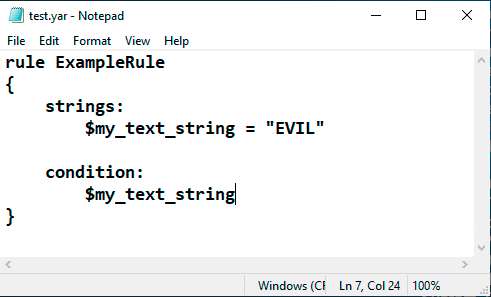
In Notepad, enter this text, as shown below.
rule ExampleRule
{
strings:
$my_text_string = "EVIL"
condition:
$my_text_string
}
In Notepad, click File, Save.
Close the Notepad window.
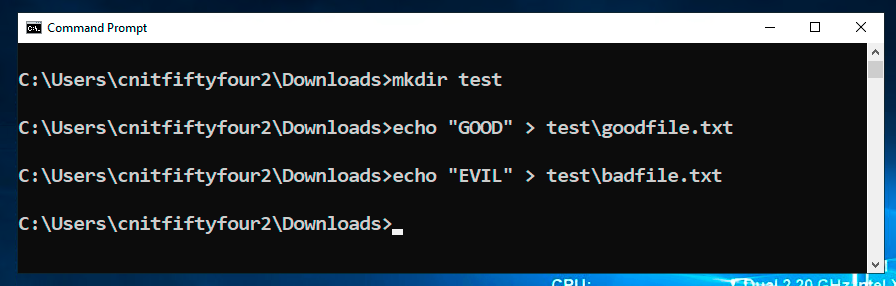
mkdir test
echo "GOOD" > test\goodfile.txt
echo "EVIL" > test\badfile.txt
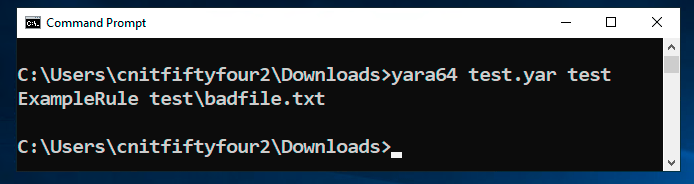
yara64 test.yar test
On your Windows machine, in a Web browser, go to
https://samsclass.info/126/proj/minesam.exe.zip
Save the minesam.exe.zip file in your Downloads folder.
Open File Explorer and navigate to your Downloads folder. Right-click the minesam.exe.zip file and click "Extract All", Extract.
A folder appears containing a minesam.exe file, as shown below.
https://raw.githubusercontent.com/Yara-Rules/rules/master/packers/packer_compiler_signatures.yar
A page containing a set of Yara rules to detect executable files and packers opens, as shown below.
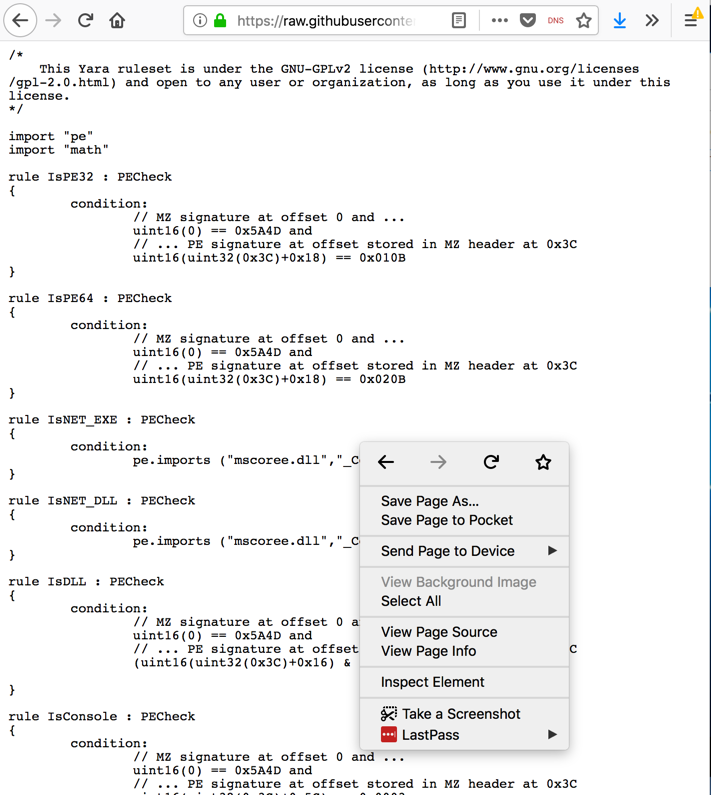
Right-click inside the Web page and click "Save Page As.... Save the page in your Downloads folder with its default name, which is packer_compiler_signatures.yar
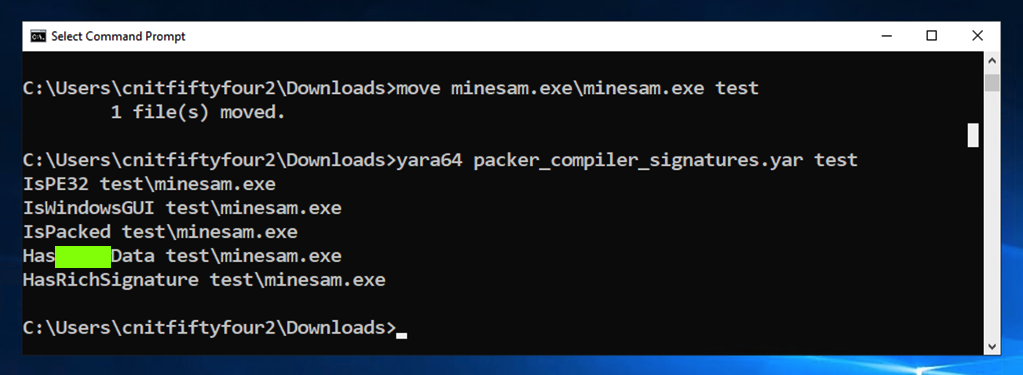
move minesam.exe\minesam.exe test
yara64 packer_compiler_signatures.yar test
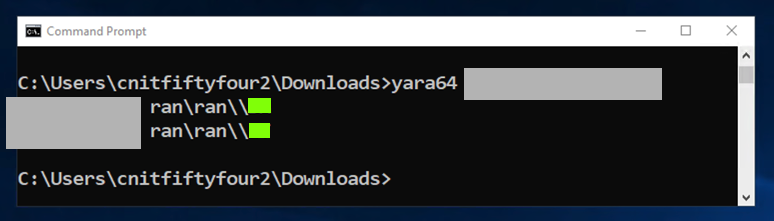
Unzip it. It contains 100 files with two letter names, such as AA.
Scan those files with Yara and find the files containing "EVIL".
If you are a CCSF student, capture a screen image like the one shown below, showing the two filennames.
If you are playing a CTF,
concatenate the two filenames, like this AABB,
to form the flag.
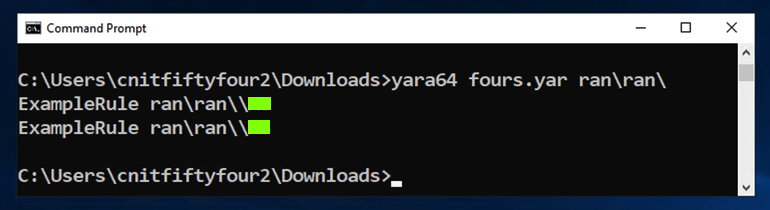
Scan those files with Yara and find the files containing three bytes of 0x04 in a row.
You may find this document helpful: " Writing YARA rules".
If you are a CCSF student, capture a screen image like the one shown below, showing the two filennames.
If you are playing a CTF,
concatenate the two filenames, like this AABB,
to form the flag.
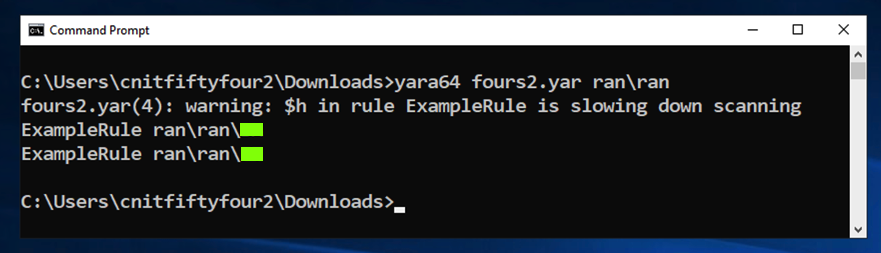
Scan those files with Yara and find the files containing this pattern:
If you are playing a CTF,
concatenate the two filenames, like this AABB,
to form the flag.
Posted 10-1-18
Visual C++ added 10-8-18
Ported to new scoring engine, and Visual C++ removed, 10-17-19
Flag numbers fixed 11-8-19
URL fixed 8-19-20
Video added 4-27-24