https://colab.research.google.com/If you see a blue "Sign In" button at the top right, click it and log into a Google account.
From the menu, click File, "New notebook".
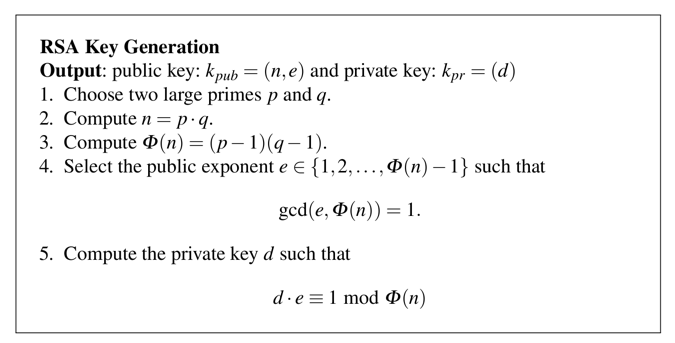
In Colab, execute this command:
!openssl genrsa 512

To parse it, you need to save it in a file and use the "rsa" command.
Execute these commands to generate a "key.pem" file, view it, and parse it.
!openssl genrsa -out key.pem 512
!cat key.pem
!openssl rsa -in key.pem -text
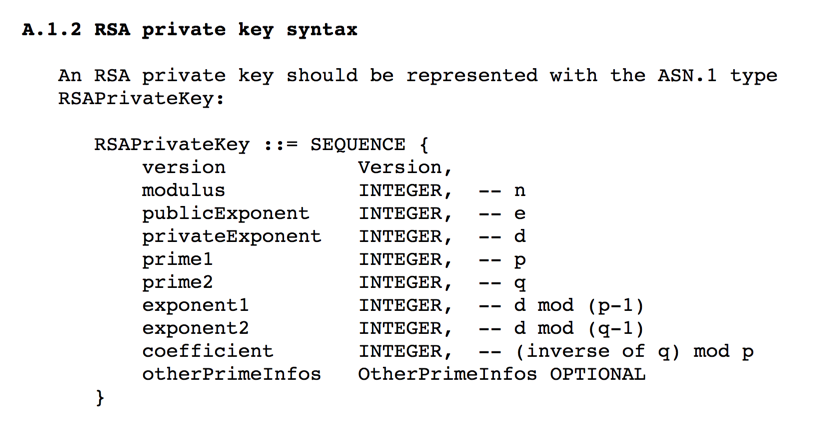
The important fields are as labelled below in red.

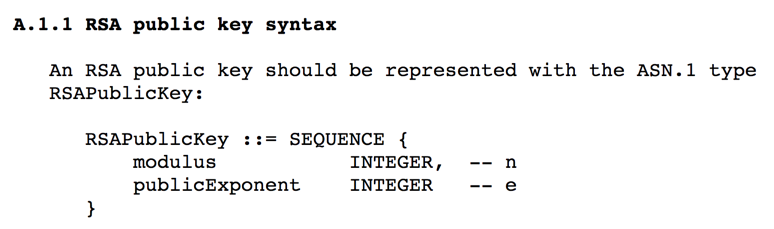
Execute this command to generate the public key from your "key.pem" file.
!openssl rsa -in key.pem -pubout

Execute these commands to save the public key in a "public.pem" file, print it out, and parse it:
!openssl rsa -in key.pem -out public.pem -pubout
!cat public.pem
!openssl rsa -pubin -text < public.pem

Execute these commands to make a 2048-bit private key and display it.
!openssl genrsa -out key2.pem 2048
!cat key2.pem

Execute these commands to see the public key.
!openssl rsa -in key2.pem -out public2.pem -pubout
!openssl rsa -pubin -text < public2.pem

Execute these commands to generate a 2048-bit encrypted private key file. Enter a password, such as P@ssw0rd, when prompted to.
!openssl genrsa -out key3.pem -aes256 2048
!cat key3.pem

Whenever you use this private key file, you'll need to supply the password.
Execute this command to display the public key.
!openssl rsa -in key3.pem -pubout

C 403.1: Find p (5 pts)
Find p from the key below.The flag is p in hex, like this:
7610158A
C 403.2: Find Public Key (5 pts)
Find the Public Key from the key below.The flag is the public key in Base64, like this:
i810CAwEAAQ==
C 403.3: Find q (10 pts extra)
Find q from the key below. Portions of the key have been redacted, as shown in bold below.The flag is q in hex, like this:
7610158A
C 403.4: Find p (20 pts extra)
Find p from the key below. Portions of the key have been redacted, as shown in bold below.The flag is p in hex, like this:
EBD8272C95DB4A88139000001C56D338219B69AA55D5D94F331607FAFCB9CF9B