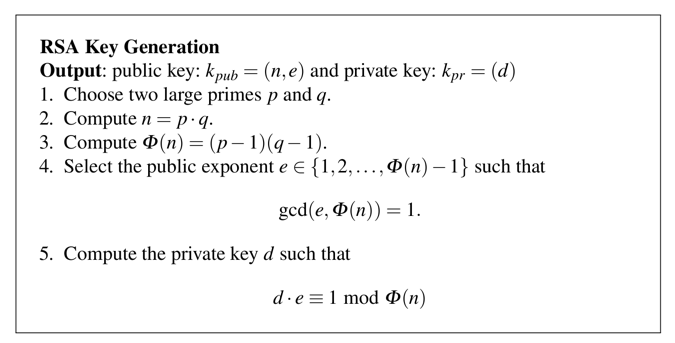
python3
p = 7
q = 23
n = p * q
print(p, q, n)
phin = (p-1) * (q-1)
print(p, q, n, phin)
Let's use e = 5
(d * e) mod phin = 1First let's set e and perform a simple multiplication.
Execute these commands. As shown below, 20 * 5 is 100, as you'd expect.
e = 5
print(20 * e)
Now let's use modular arithmetic, with a modulus of phin, that is, 132. In Python, we use a % character to indicate a modulus.
Modulus 132 means there is no number larger than 131. Adding 1 to 131 makes it roll back to 0. The numbers are on a ring, as shown below.
Execute these commands. As shown below, 132 modulus phin is zero.
print(100 % phin)
print(130 % phin)
print(131 % phin)
print(132 % phin)
Now let's calculate the result for values of d from 20 through 25.
Execute these commands:
print((20 * e) % phin)
print((21 * e) % phin)
print((22 * e) % phin)
print((23 * e) % phin)
print((24 * e) % phin)
print((25 * e) % phin)
print((26 * e) % phin)
print((27 * e) % phin)
We'll have to use larger values and try to hit 1 the next time we go around the ring.
Execute these commands:
print((50 * e) % phin)
print((51 * e) % phin)
print((52 * e) % phin)
print((53 * e) % phin)
She publishes her public key to the cloud.
Cueball wants to send Meghan this message:
Hi!
So the message is:
72 105 33
Execute these commands:
print(72 ** e % n)
print(105 ** e % n)
print(33 ** e % n)
Execute these commands:
d = 53
print(151 ** d % n)
print(119 ** d % n)
print(157 ** d % n)
C 401.1: Cueball's Keys (15 pts)
Cueball will use these values:Calculate Cueball's public and private keys.The flag is Cueball's Public Key, like this: (161,5)
C 401.2: Message to Cueball (15 extra)
Meghan sends this message to Cueball. Decrypt it.460, 364, 144, 153, 501, 402, 19, 311, 501, 280, 501, 80, 153, 382, 296, 153, 311
Hint: use the chr() and ord() functions
The flag is the decrypted message.