https://samlols.samsclass.info/141/md5.htm
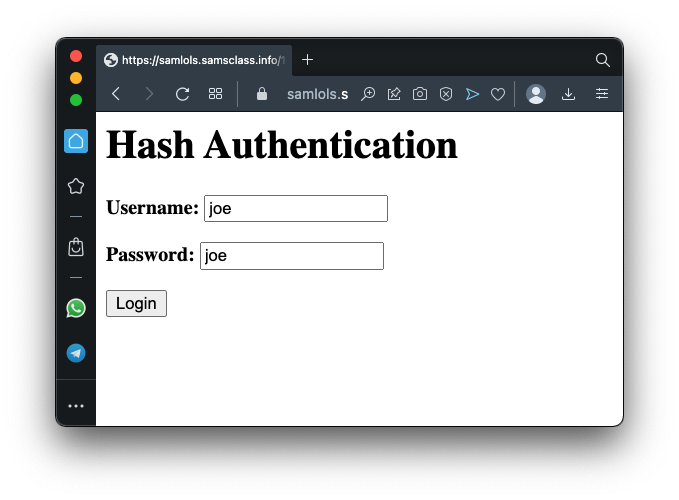
Log in with the default username and password, as shown below.
You log in as Joe, as shown below.
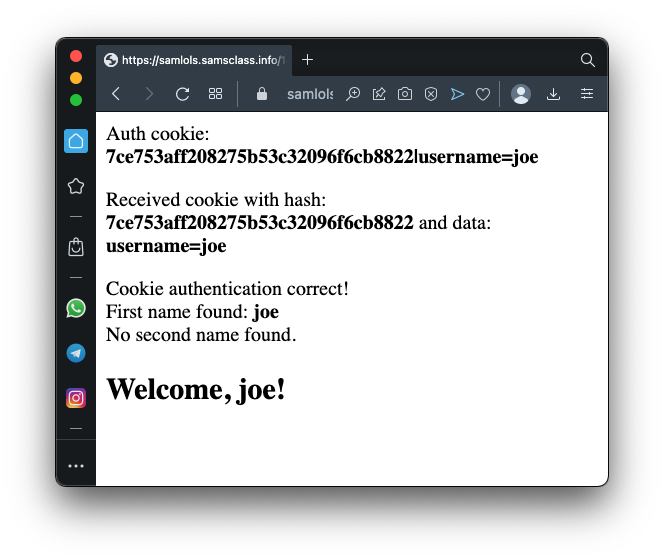
When joe logs in, a cookie is set with this data:
7ce753aff208275b53c32096f6cb8822|username=joeThe start of that cookie is the MD5 hash of this string, where secret is a 12-letter secret phrase that stays on the server and is not visible to the user.
secretusername=joeOur goal is to forge an authentation cookie and log in as administrator.
https://portswigger.net/burp/communitydownload
Click Next. Click "Start Burp".
Click the Proxy tab.
Make sure "Intercept is off", as shown below.
Click the "Open Browser" button.
In the new browser that opens, go to
https://samlols.samsclass.info/141/md5.htm
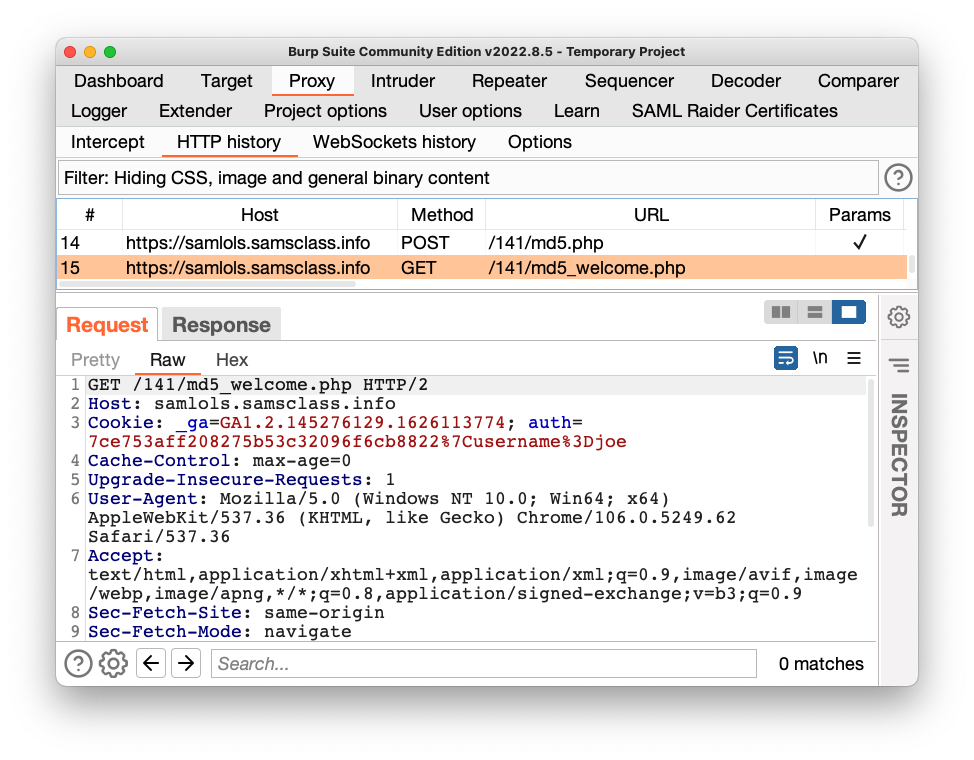
Log in with the default username and password.In Burp, on the Proxy tab, click the "HTTP history" sub-tab.
Find the GET request that loaded the welcome page, highlighted in the image below.
Click the Repeater tab.
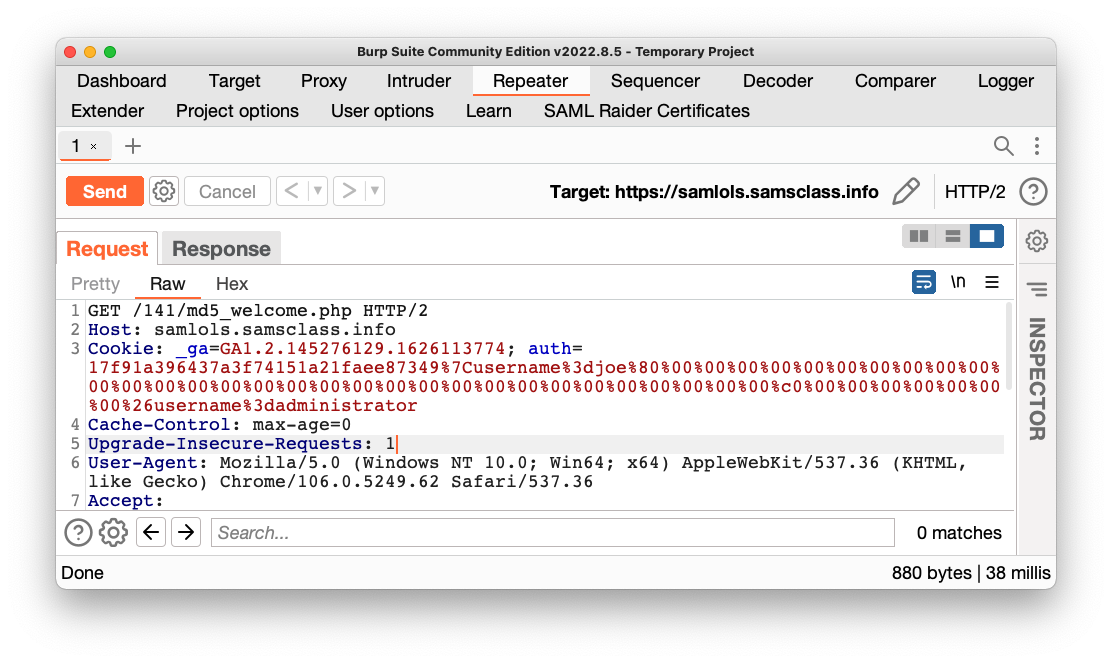
On the Repeater tab, notice the cookie value, highlighted in the image below.
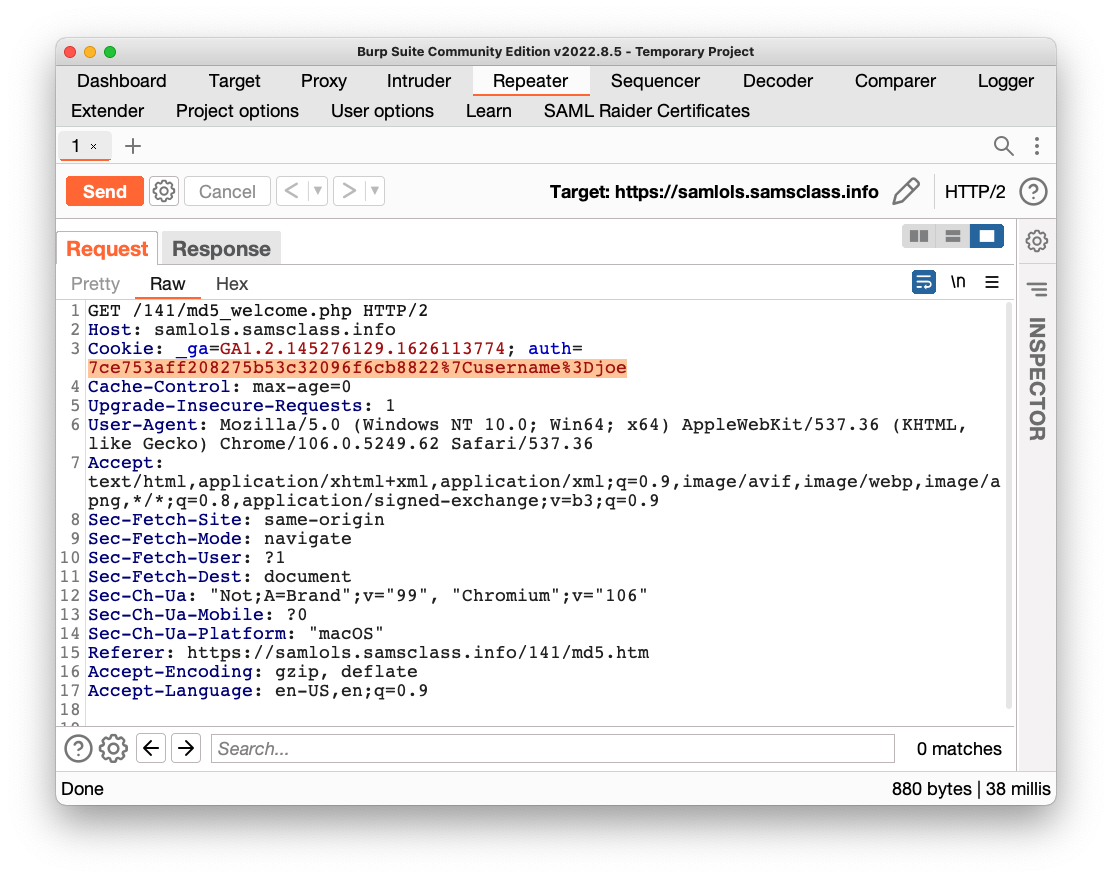
Highlight the cookie value, as shown above. Right-click the highlighted value and click "Send to Decoder".
Click the Decoder tab.
At the top right, in the "Decode as..." box, click and select URL.
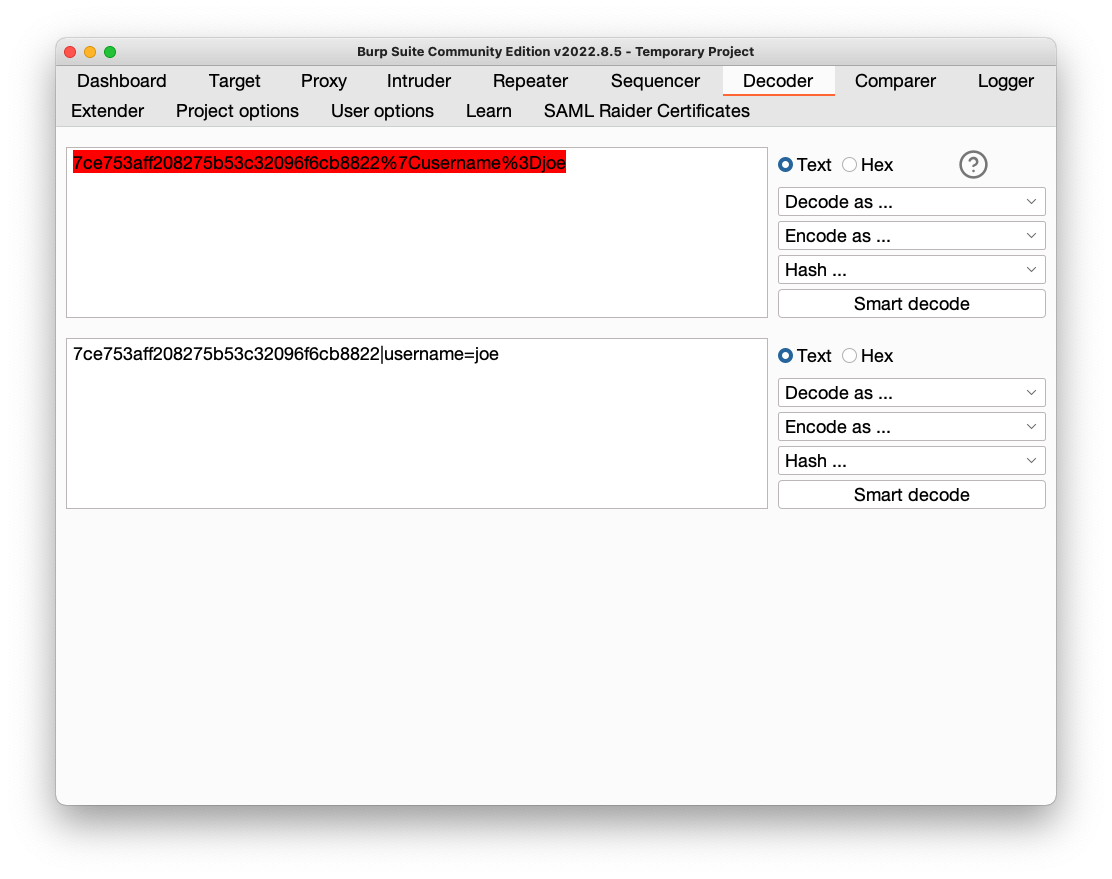
URL-decoded text appears in a lower pane, as shown below.
This data includes two items we need to forge the hash: the original signature and the data.
sudo apt update
sudo apt install git build-essential libssl-dev -y
git clone https://github.com/sambowne/hash_extender.git
cd hash_extender
make
./hash_extender
./hash_extender -d "username=joe" \
-s 7ce753aff208275b53c32096f6cb8822 \
-a "&username=administrator" -f md5 -l 12 \
--out-data-format=html
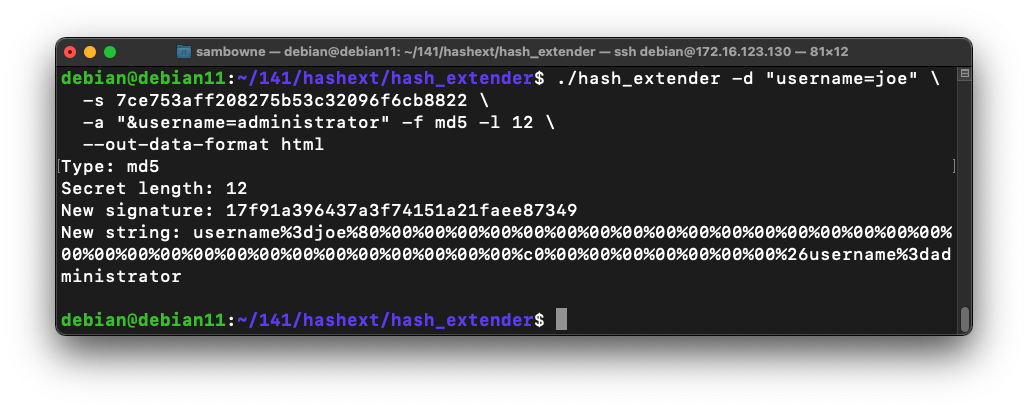
Don't delete the "%7C" character between the two values.
C 108.1 Flag (15 pts)
In Burp, click the Send button.Click the Response tab.
Scroll to the bottom to see the flag, outlined in green in the image below.
C 108.2 Different Secret (15 pts)
Log in here:https://samlols.samsclass.info/141/md5a.htm
Authenticate as administrator to see the flag.Hint: try other secret lengths.
Posted 10-6-22 by Sam Bowne
Minor corrections 10-12-22
Github changed to get fixed code 4-30-35