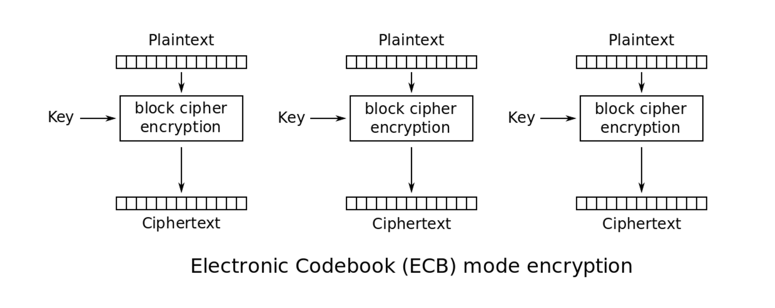
Plaintext SECRET MESSAGE!!Key SECRET KEY 128 BCiphertext 0f 7b c9 6e 06 c0 87 3f 15 8e 08 5c e3 81 6d bb
After importing the library, we assign values to plaintext and key and declare a new AES object. The AES object has an encrypt method that gives the same result as the online encryptor, as shown below.
from Crypto.Cipher import AES
plaintext = "SECRET MESSAGE!!"
key = "SECRET KEY 128 B"
cipher = AES.new(key, AES.MODE_ECB)
cipher.encrypt(plaintext).encode("hex")
SECRET MESSAGE!!SECRET MESSAGE!!SECRET MESSAGE!!
Changing the window width makes the repetitions easier to see.
The ciphertext begins with ae e2 4e as shown below.
Plaintext SECRET MESSAGE!!Key SECRET KEY 128 BIV 00 11 22 33 44 55 66 77 88 99 aa bb cc dd ee ff
from Crypto.Cipher import AES
plaintext = "SECRET MESSAGE!!"
key = "SECRET KEY 128 B"
iv = "00112233445566778899aabbccddeeff".decode("hex")
cipher = AES.new(key, AES.MODE_CBC, iv)
cipher.encrypt(plaintext).encode("hex")
SECRET MESSAGE!!SECRET MESSAGE!!SECRET MESSAGE!!
One common method is PKCS7, in which the padding is always one of these 15 byte-strings, chosen to make the total length 16 bytes.
01
02 02
03 03 03
04 04 04 04
05 05 05 05 05
06 06 06 06 06 06
07 07 07 07 07 07 07
08 08 08 08 08 08 08 08
09 09 09 09 09 09 09 09 09
0a 0a 0a 0a 0a 0a 0a 0a 0a 0a
0b 0b 0b 0b 0b 0b 0b 0b 0b 0b 0b
0c 0c 0c 0c 0c 0c 0c 0c 0c 0c 0c 0c
0d 0d 0d 0d 0d 0d 0d 0d 0d 0d 0d 0d 0d
0e 0e 0e 0e 0e 0e 0e 0e 0e 0e 0e 0e 0e 0e
0f 0f 0f 0f 0f 0f 0f 0f 0f 0f 0f 0f 0f 0f 0f
from Crypto.Cipher import AES
plaintext = "HELLO" + 11 * "0b".decode("hex")
key = "SECRET KEY 128 B"
iv = "00112233445566778899aabbccddeeff".decode("hex")
cipher = AES.new(key, AES.MODE_CBC, iv)
cipher.encrypt(plaintext).encode("hex")
Even if two users have the same password, they shouldn't have identical keys, so a salt value is used to make each calculation different.
The PBKDF2 algorithm uses a password, a salt, and cryptographic algorithms to create a long series of pseudorandom bytes. You can read as many bytes as you want to form a key.
This code creates a 16-byte key from
a password of
Password123
and a salt of
RANDOM STUFF
from pbkdf2 import PBKDF2
password = "Password123"
salt = "RANDOM STUFF"
PBKDF2(password, salt).read(16).encode("hex")
This site lets you calculate simple versions of PBKDF2 online. As you can see, it has the same result for the key.
To learn a bit more about PBKDF2, execute this command at the >>> prompt:
help(PBKDF2)
As shown above, the __init__ function requires the caller to specify the passphrase and salt parameters, and has these default values for the other parameters:
This is the first example algorithm specified in Appendix B.1.1 of RFC 2898: PKCS #5: Password-Based Cryptography Specification Version 2.0. It's called HMAC-SHA-1.
iterations1000 digestmoduleSHA (That is, SHA-1) macmoduleHMAC
Challenge C1-1: Encrypt the Message (5 pts)
Encrypt this cleartext using AES-ECB:Use the default PBKDF2 with no salt and a password ofSAFE AND SECURE!Use the form below to get your points.123
Challenge C1-2: Decrypt the Message (10 pts)
Decrypt this AES-ECB-encrypted ciphertext:The key was formed using the same one-digit PIN for both the salt and the passphrase, and default values for the other options.4e45e079c9c5b019d1ee66dde12db4fd8c05933ec3d01cc9df050e3791fe9cb0Use the form below to get your points.
Challenge C1-3: Decrypt the Message (25 pts)
Decrypt this AES-CBC-encrypted ciphertext:The passphrase and the salt are two-digit numbers. The iv contains 128 bits, all zero.4a3b101904aff330dcfdca5e7548f202f7273de7d35f7f0a51964f67d666b16167c2896095b001643cd9830a2c8e2a41Use the form below to get your points.