In the Google Cloud Console, at the top left, click the three-bar "hamburger" icon. Scroll down to the COMPUTE section and click "Compute Engine, Disks.
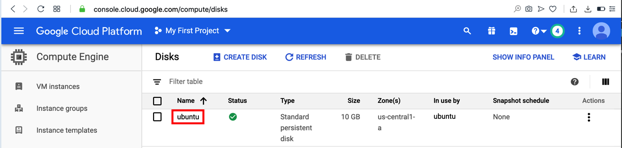
Click the name of your Ubuntu machine, which is probably ubuntu, as shown below.

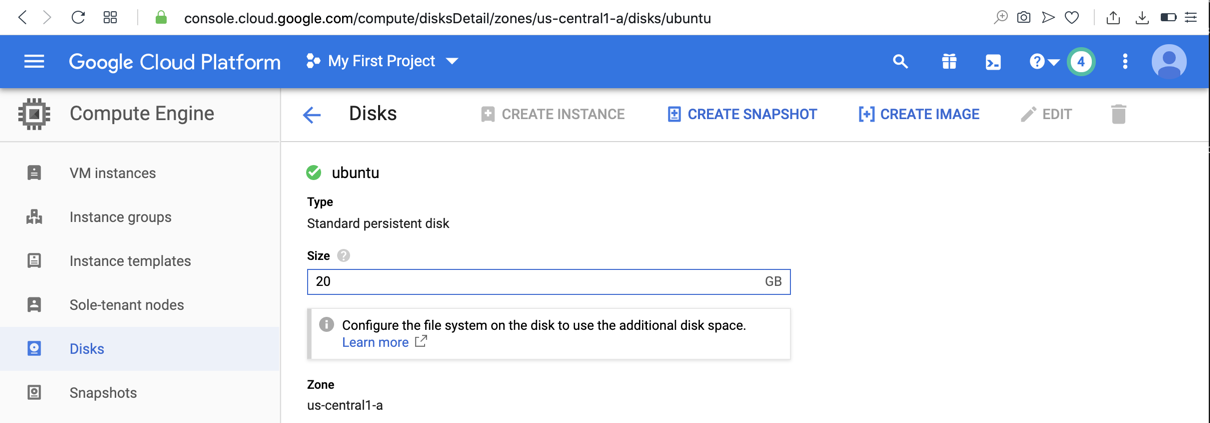
On the next page, at the top right, click EDIT. Change the disk size to 20, as shown below.
At the bottom of the page, click Save.
In your Ubuntu machine, in an SSH session, execute this command:
sudo reboot
In your Ubuntu machine, in the SSH session, execute these commands:
sudo /opt/splunk/bin/splunk start
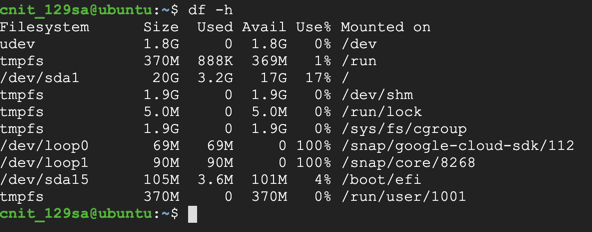
df -h
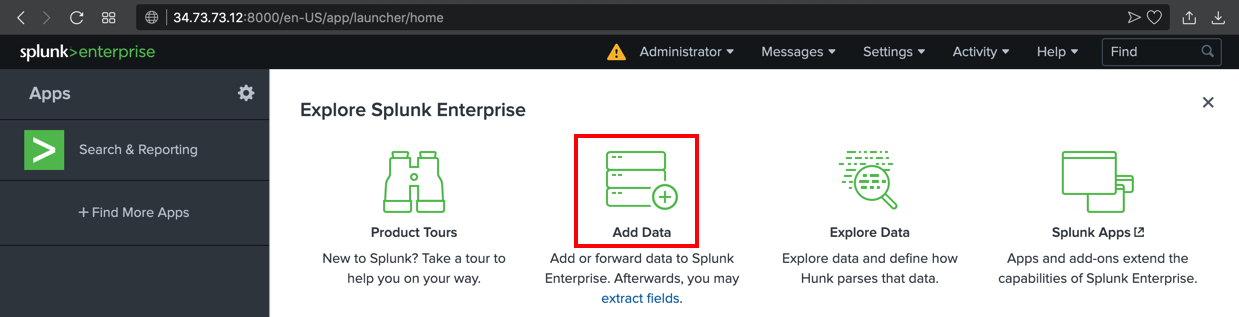
In the Splunk administration page, click "Add Data", as shown below.
If a box pops up asking you to take a tour, click Skip.
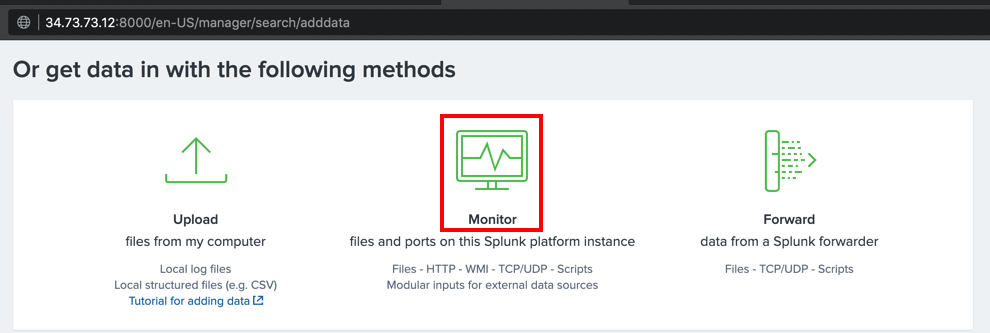
In the next page, scroll down to the "Or get data in with the following methods" section, and click Monitor, as shown below.
In the "Add Data" screen, on the left side, click "Files & Directories".
On the right side, enter a "File or Directory" of
/var/log
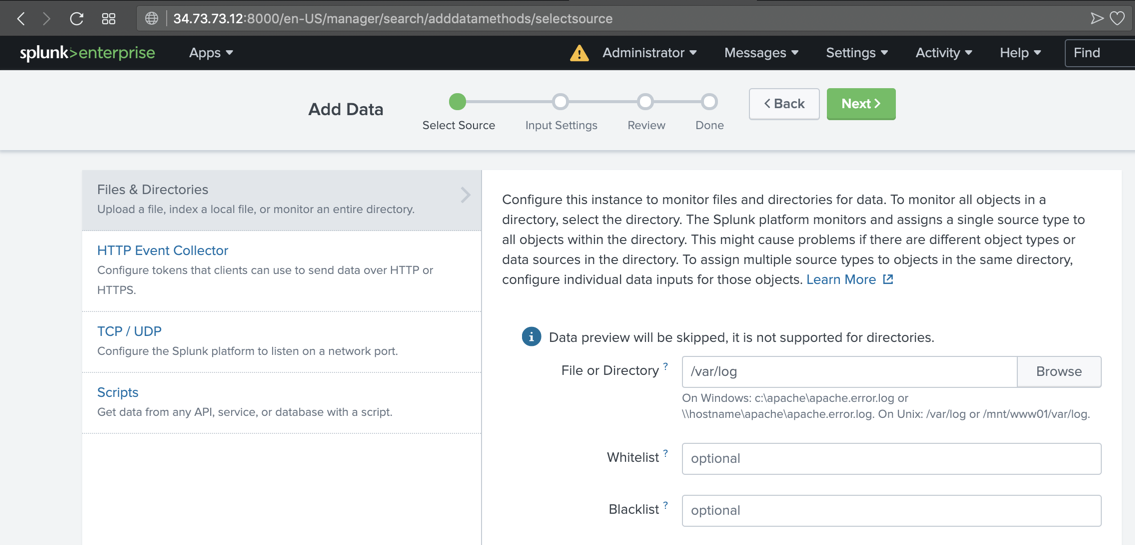
At the top right, click the green Next button.
Click Review. Click Submit.
Click "Start Searching".
If a box pops up asking you to take a tour, click Skip.
Splunk shows log entries, as shown below.
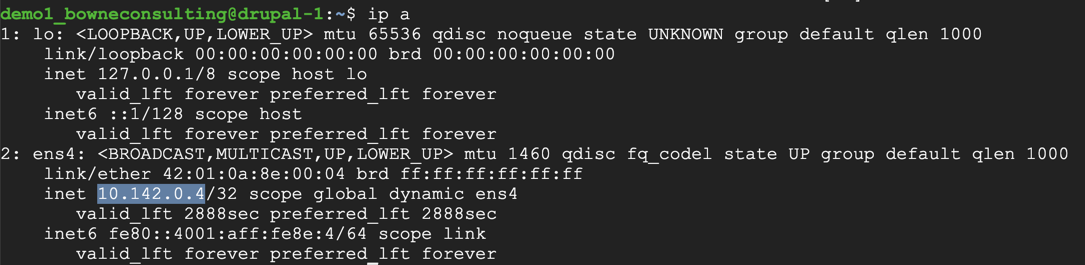
ip a
sudo nano /etc/ssh/sshd_config
Change the value from "no" to yes, as shown below.
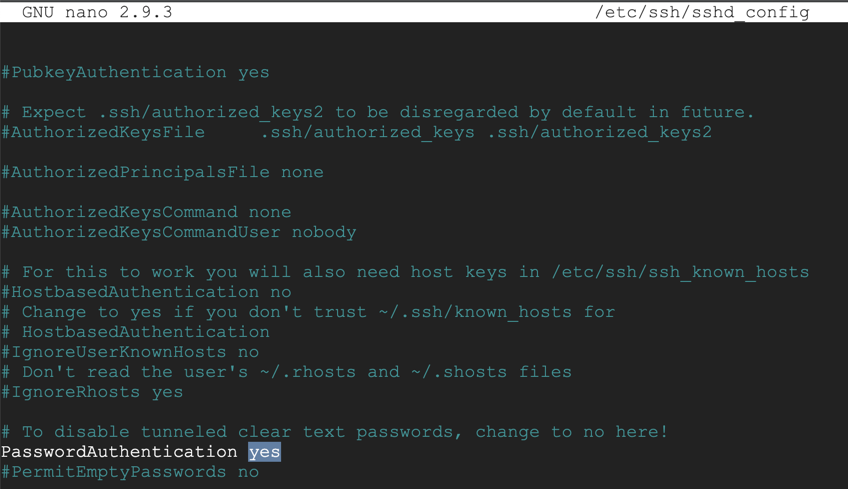
Save the file with Ctrl+X, Y, Enter.
Execute this command to restart SSH:
sudo systemctl restart ssh
ssh fred@10.142.0.4
On the left side, click "Search & Reporting".
In the Search page, in the lower right, click the "Data Summary" button, as shown below.

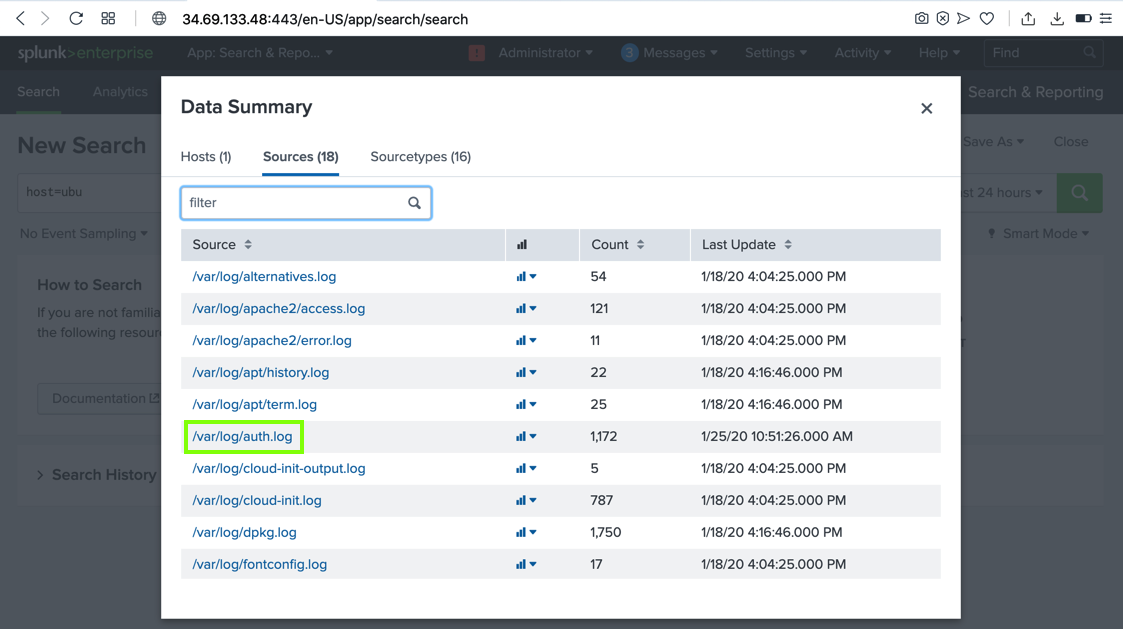
A "Data Summary" box pops up, as shown below. Click the Sources tab.
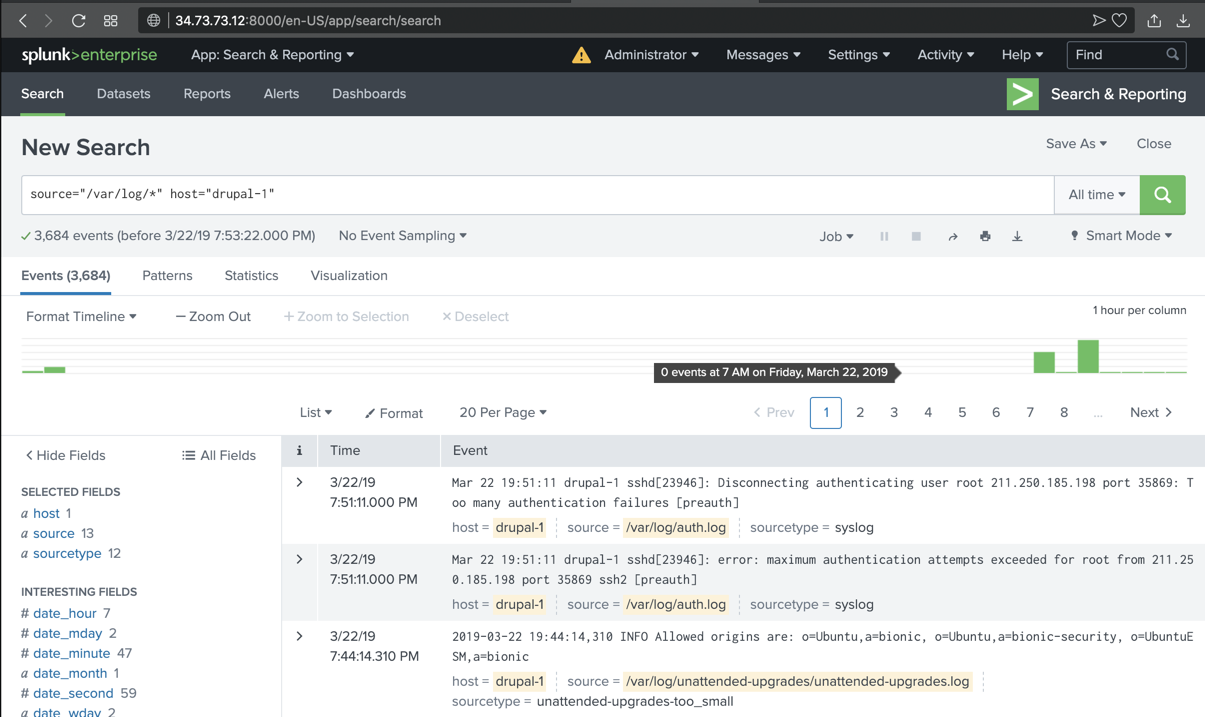
In the Source list, click /var/log/auth.log, as shown below.
Flag W 202.1: User type (10 pts)
In Splunk, find a "Failed password" event for "fred", as shown below.The text covered by the green box in the image below is the flag.
Capturing a Screen Image
Capture a WHOLE-DESKTOP image showing the flag.Save the image as "Proj W 202.2 from YOUR NAME".
sudo apt install software-properties-common -y
sudo add-apt-repository ppa:oisf/suricata-stable
On your Ubuntu Drupal server, execute these commands:
sudo apt update
sudo apt-get install suricata -y
sudo mkdir -p /var/lib/suricata/rules/
sudo nano /var/lib/suricata/rules/test-ddos.rules
alert tcp any any -> $HOME_NET 80 (msg: "Possible DDoS attack"; flags: S; flow: stateless; threshold: type both, track by_dst, count 20, seconds 1; sid:1000001; rev:1;)
On your Ubuntu Drupal server, execute this command:
sudo nano /etc/suricata/suricata.yaml
Add test-ddos.rules to the list, as shown below.
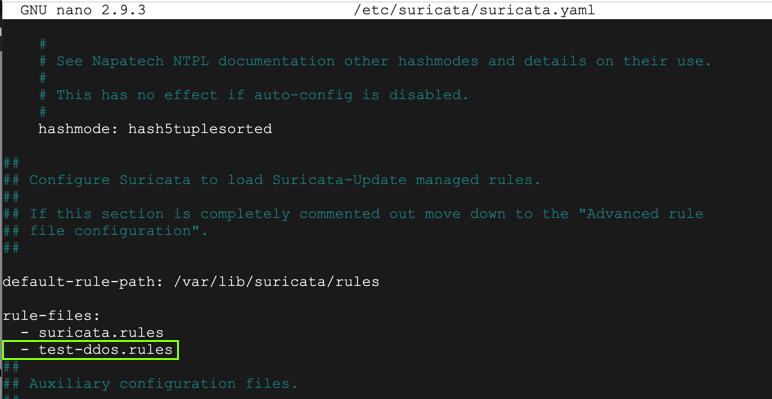
Use Ctrl+W, Ctrl+R to open the Search and Replace function. Change all occurrences of eth0 to ens4
Save the file with Ctrl+X, Y, Enter.
sudo service suricata stop
sudo rm /var/run/suricata.pid
sudo suricata -D -c /etc/suricata/suricata.yaml -i ens4
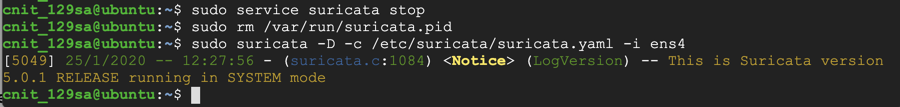
If Suricata doesn't start, and prints out red error messages, go back and check the suricata.yaml file for errors.
tail -f /var/log/suricata/fast.log
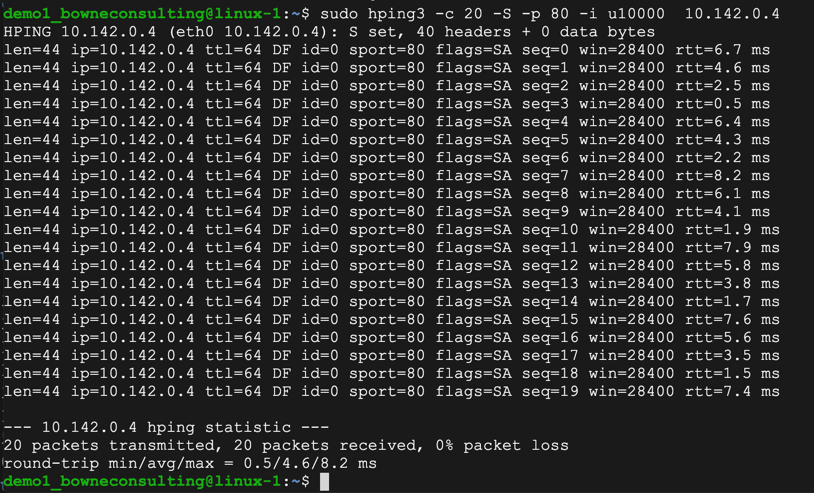
sudo apt install hping3 -y
sudo hping3 -c 20 -S -p 80 -i u10000 10.128.0.6
Flag W 202.2: Suricata alert (5 pts)
An alert appears on the Ubuntu Drupal server.The text covered by the green box in the image below is the flag.
Troubleshooting
If you see no alerts, check the /etc/suricata/suricata.yaml file and make sure it is exactly as shown above.Capturing a Screen Image
Capture a WHOLE-DESKTOP image showing the flag.Save the image as "Proj W 202.2 from YOUR NAME".
sudo suricata-update
sudo service suricata stop
sudo rm /var/run/suricata.pid
sudo suricata -D -c /etc/suricata/suricata.yaml -i ens4
On the left side, click "Search & Reporting".
In the lower center, click the "Data Summary" button.
In the "Data Summary" box, click the Sources tab. In the filter box, type suri
Several Suricata files appear, as shown below.
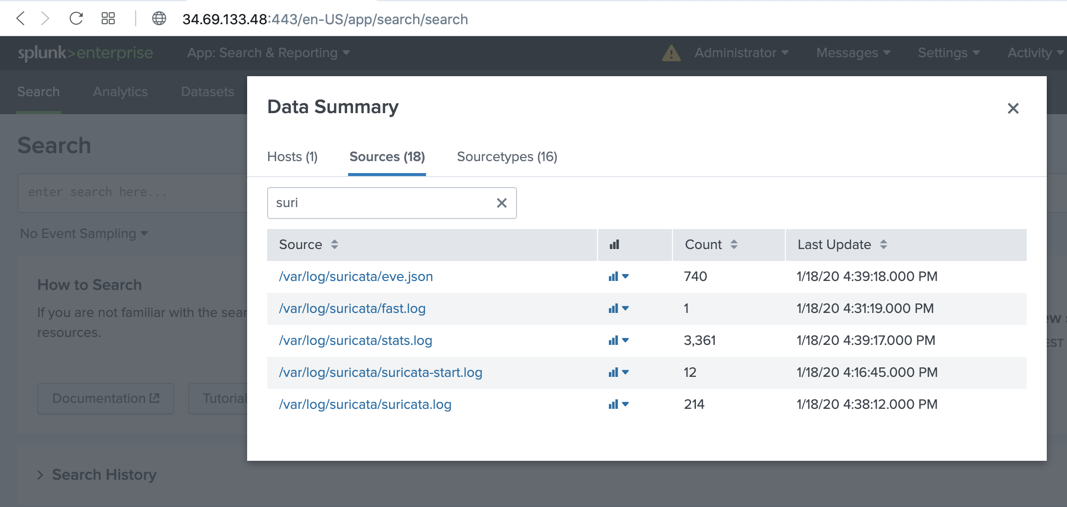
Click /var/log/suricata/fast.log.
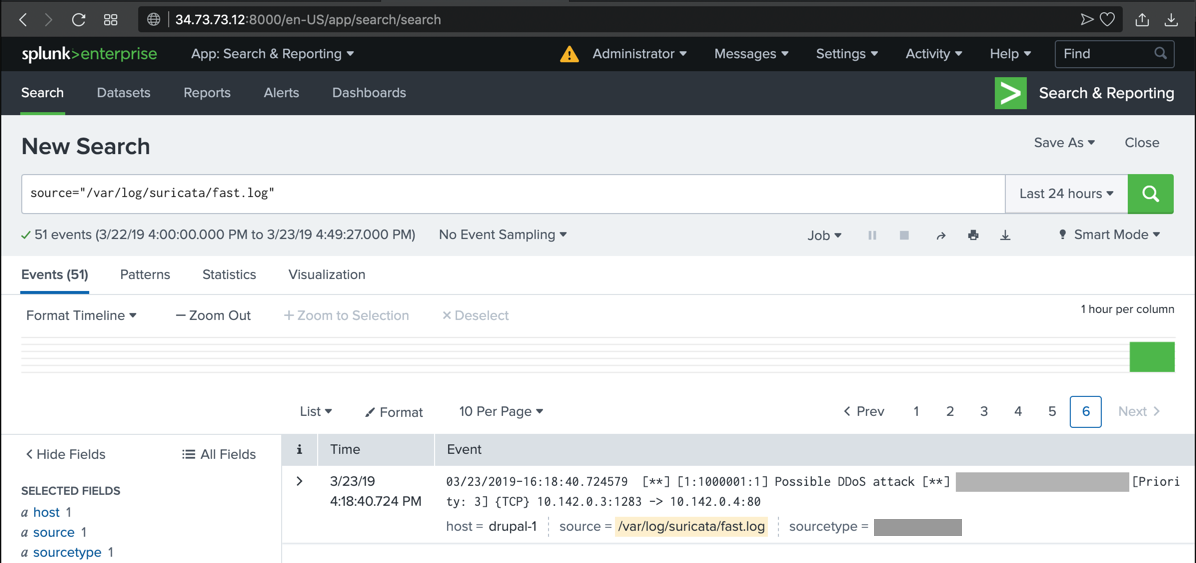
The alert you saw previously appears in Splunk, as shown below.
sudo hping3 -c 20 -S -p 80 -i u10000 10.142.0.4
Flag W 202.3: App server ports (5 pts)
Several new alerts appear. Find the alert , as shown below.The text covered by the green box in the image below is the flag.
Capturing a Screen Image
Capture a WHOLE-DESKTOP image showing the flag.Save the image as "Proj W 202.2 from YOUR NAME".
Posted 3-21-19
Install lshw added 5-20-19
Image fixed and software-properties-common added 5-20-19
Point total for 1.1 changed to 10 8-8-19
Update added for Ubuntu 8-8-19
Hint added for missing suricata fast alerts 8-8-19
Split into two projects for CNIT 129S 1-25-2020
Project numbers updated 4-7-2020