Project 5x: Exploiting ECB Encryption (35 pts.)
What You Need
Purpose
To exploit an ECB-encrypted page without access to
the plaintext.
Warning
This is very difficult. You can't use Burp alpone.
I had to write a
custom Python application.
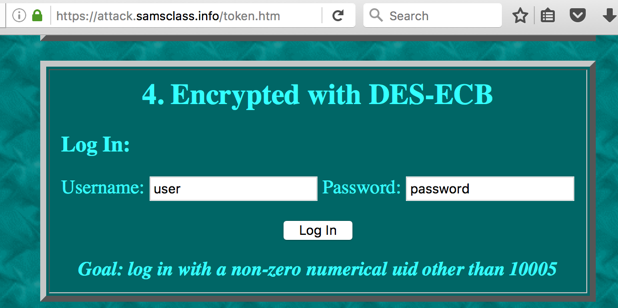
Go to this URL and scroll down to Challenge 4:
https://attack.samsclass.info/token.htm
The login form is
shown below. If you log in with the default
credentials, you have uid=10005.
If you prefer not to deal with the SSL encryption,
you can also use this URL:
http://attackdirect.samsclass.info/token.htm
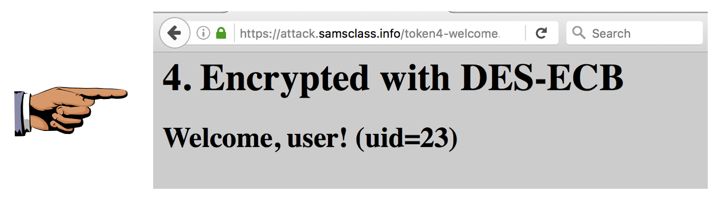
Perform Horizontal Privilege Escalation
Exploit that form and log in with
a different uid,
as shown below.
You need to get a different numerical value, not
a value containing both numbers and letters.
Capturing a Screen Image
Capture a
WHOLE-DESKTOP image showing
a numerical uid different from
10005.
Save the image as
"Proj 5x from YOUR NAME".
Turning in Your Project
Send the image to cnit.129s@gmail.com with a subject of
"Proj 5x from YOUR NAME". Send a Cc:
to yourself.
Posted 10-17-16


