Search for
TD AMERITRADEInstall the "TD Ameritrade Mobile" app, as shown below.


When the app launches, close the "What's New" page.
A popup box asks "Do you want to see the New Features popup again?" Click No.
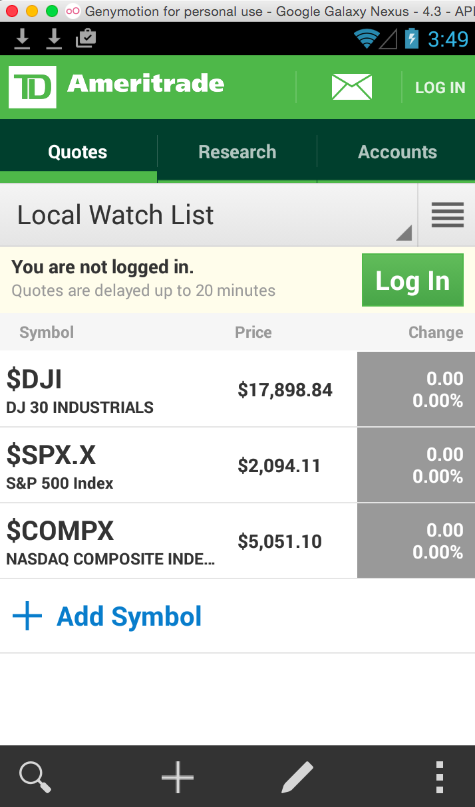
You see a home screen, with an inviting green "Log In" button, as shown below.
On your host machine, open a Terminal or Command Prompt window.
Execute these commands, changing the path in the first command to your correct SDK path.
NOTE: If you are using Windows, remove the "./" before "adb" in the third command.
cd /Users/sambowne/Library/Android/sdk
cd platform-tools
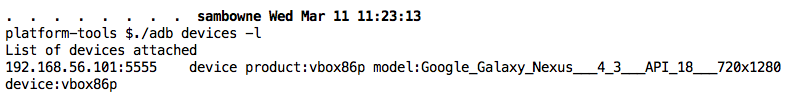
./adb devices -l
You should see a device listed, as shown below.
Troubleshooting
If the Genymotion device does not appear, try these troubleshooting steps.
- Make sure the Genymotion device is running and connected to the Internet. Open the Web browser and see if you can view Web pages.
- Try issuing these commands:
./adb kill-server./adb start-server
- Find the devices IP adress in Settings, Wi-Fi and connect to it with this command, replacing the IP address with the correct address in Genymotion
./adb connect 192.168.1.101
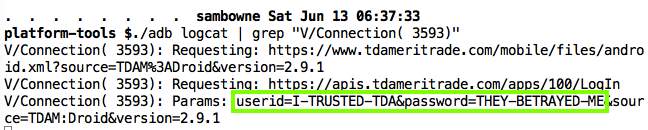
./adb logcat
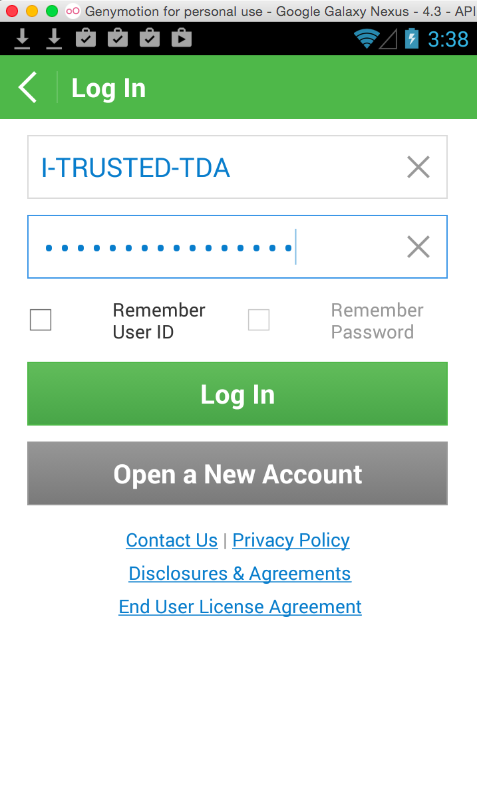
You can see the credentials in the log. If you want to make it easier, pipe the log through grep, as shown below.