
However, the Stitcher Android and iOS apps have a serious security problem--they send login credentials without encryption. Instead, they obfuscate passwords with a modified Caesar cipher, a technique that is trivial to reverse.
This practice may be illegal in the USA. Two American companies were sanctioned by the FTC in 2014 for making a much less serious error, using HTTPS encryption without validating the certificate:
FTC Final Orders with Fandango and Credit Karma Provide Guidance on Mobile App Security
The Stitcher Android app also stores confidential data in plaintext on the Android device, as detailed below.
Here's the app:


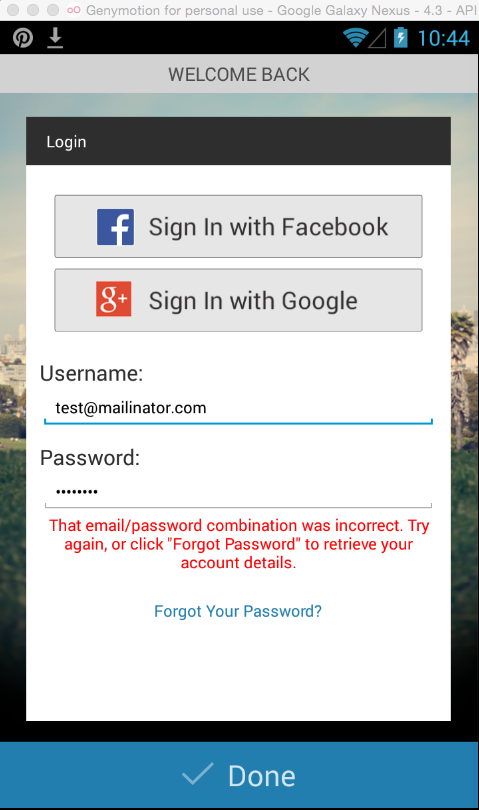
Sending test credentials:
Harvesting them from Burp:
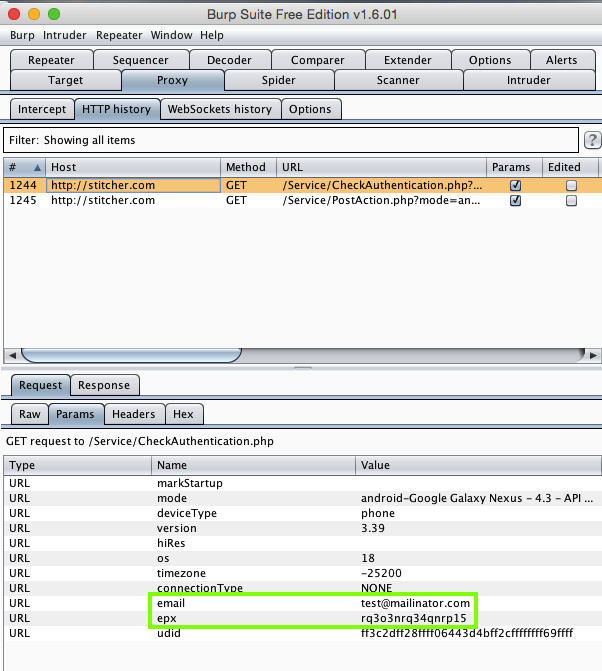
The email is sent in plaintext, but the password is obfuscated with a very simple Caesar chiper, that moves each character a different number of steps forward in the alphabet, and inserts a padding character before it. The pattern is obvious from the test cases shown below.
Password epx a sn b so c sp d sq e sr aa sn5k ab sn5l ac sn5m ad sn5n ae sn5o aaa sn5k4l aab sn5k4m aac sn5k4n
https://samsclass.info/128/proj/MacBurpWifi.htm
Here's the app:
Sending test credentials:
Harvesting them with Burp:
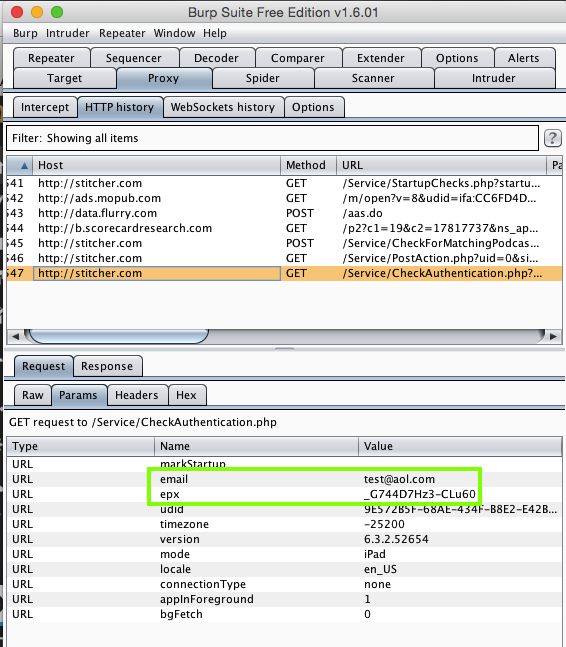
The email is sent in plaintext, but the password is obfuscated with a very simple Caesar chiper, that moves each character a different number of steps forward in the alphabet, and inserts a padding character before it. The pattern is obvious from the test cases shown below.
Password epx a _F b _G aa _FLx ab _FLy ac _FLz ad _FL0 aaa _FLx-4 aab _FLx-5 aac _FLx-6 aaaa _FLx-474 A 9F B 9G C 9H 1 8F 2 8G 11 8FIx aaaaaaaa _FLx-474zD3D4u6E bbbbbbbb _GLy-575zE3E4v6F
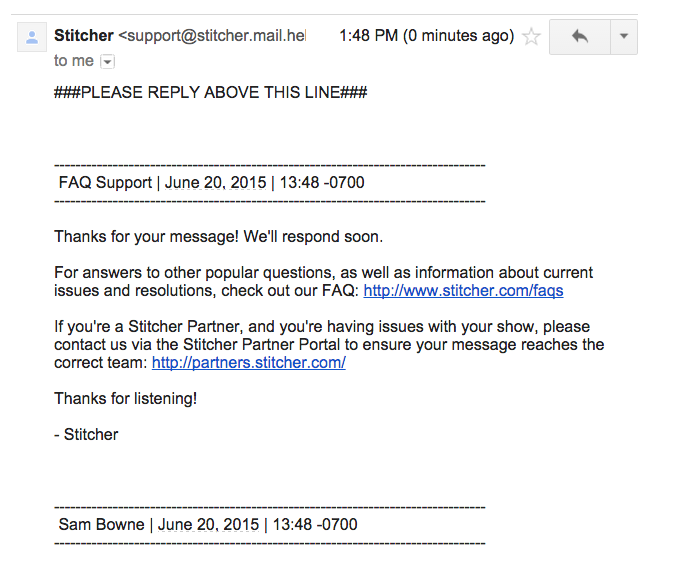
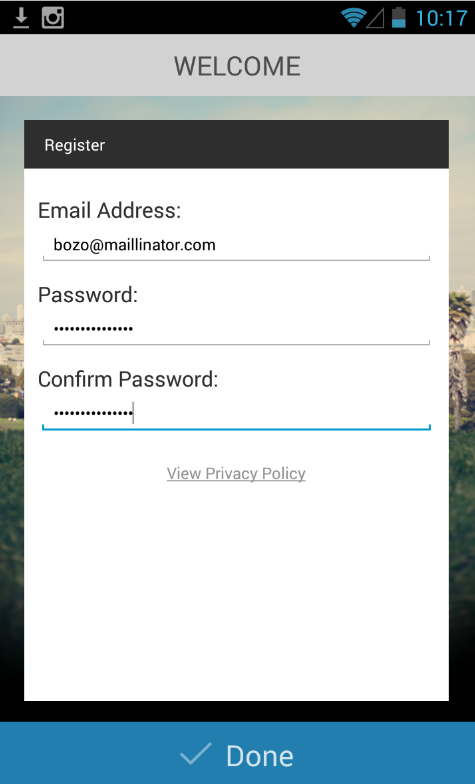
I registered an account on my Android device using a password of FLAPPY-PASSWORD:
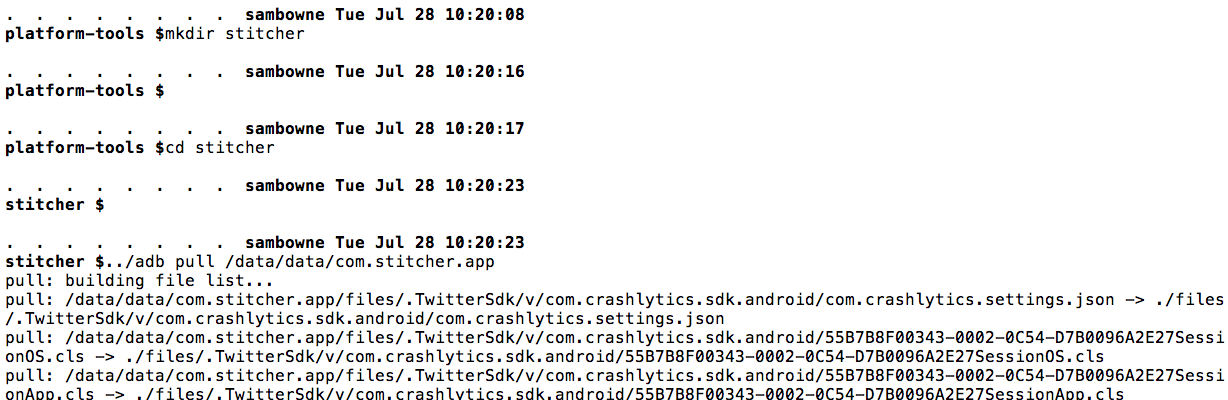
I used adb to pull the local data from the app's folder to my local Mac system:
Grep easily finds the locally stored password:
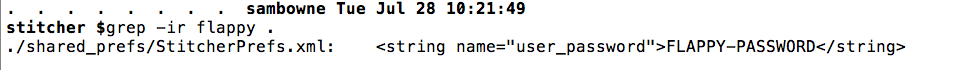
That file contains the plaintext email address and password, and, bizarrely, also contains the obfuscated password:
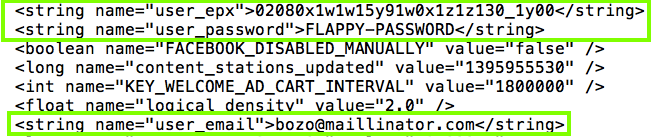
This is a poor security practice, because anyone who steals an unencrypted phone can recover the password.