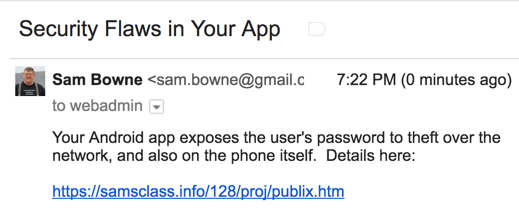
These are the #2 and #3 most important security flaws, according to OWASP.
As discussed here, passwords should not be stored on the phone at all. Because users re-use passwords, they are very sensitive information and handling them carelessly is a disservice to your customers. Locally stored passwords could be stolen by malware on the phone, or by simply stealing the phone itself. Instead, a random cookie should be stored on the phone, which is useless at any other company.


When I log in:
The data can be stolen via a MITM attack, because the SSL certificate is not verified.
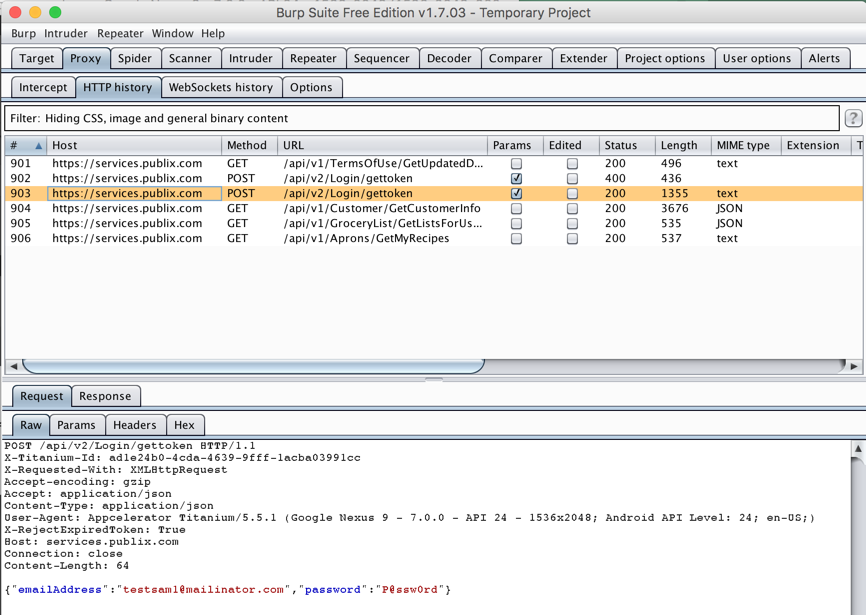
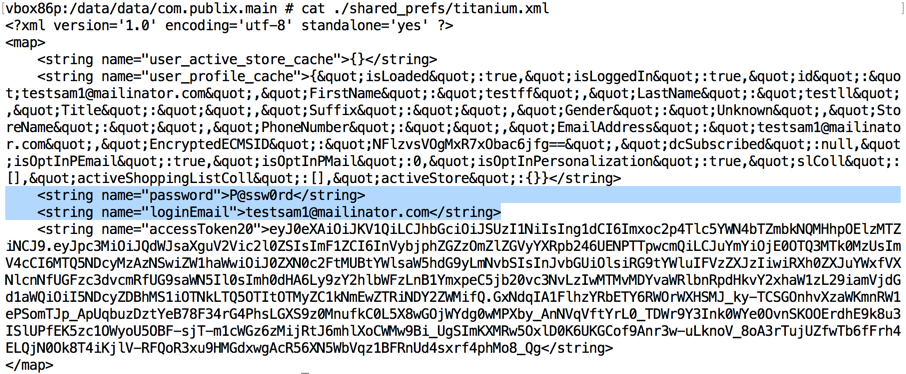
Here's the password stored in plaintext on the phone: