They are several of the same flaws we saw in the Android version of the app: plaintext network transmission of a password, sensitive information in the logs, and plaintext storage of a password in the file system.
Click Window, "Welcome to Xcode".
The "Welcome to Xcode" window appears, as shown below.

At the bottom left, click "Check out an existing project".
Enter a repository location of
https://github.com/SecurityCompass/iPhoneLabs.git
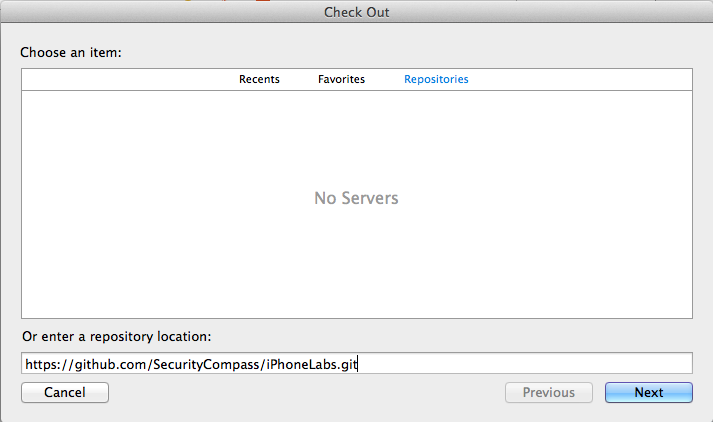
Click Next.
In the next window, accept the default selection of master as shown below.
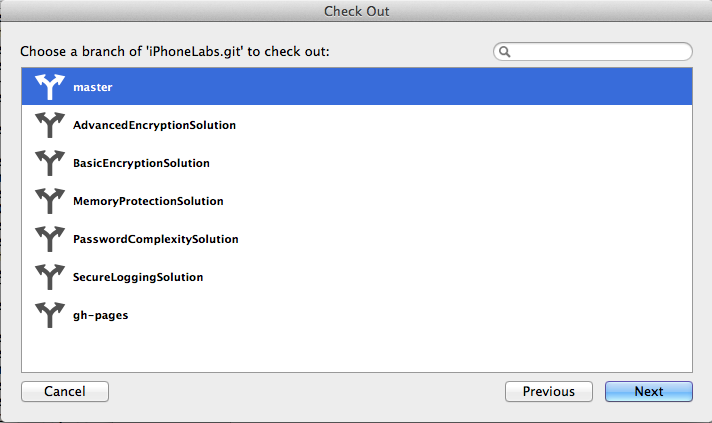
Click Next.
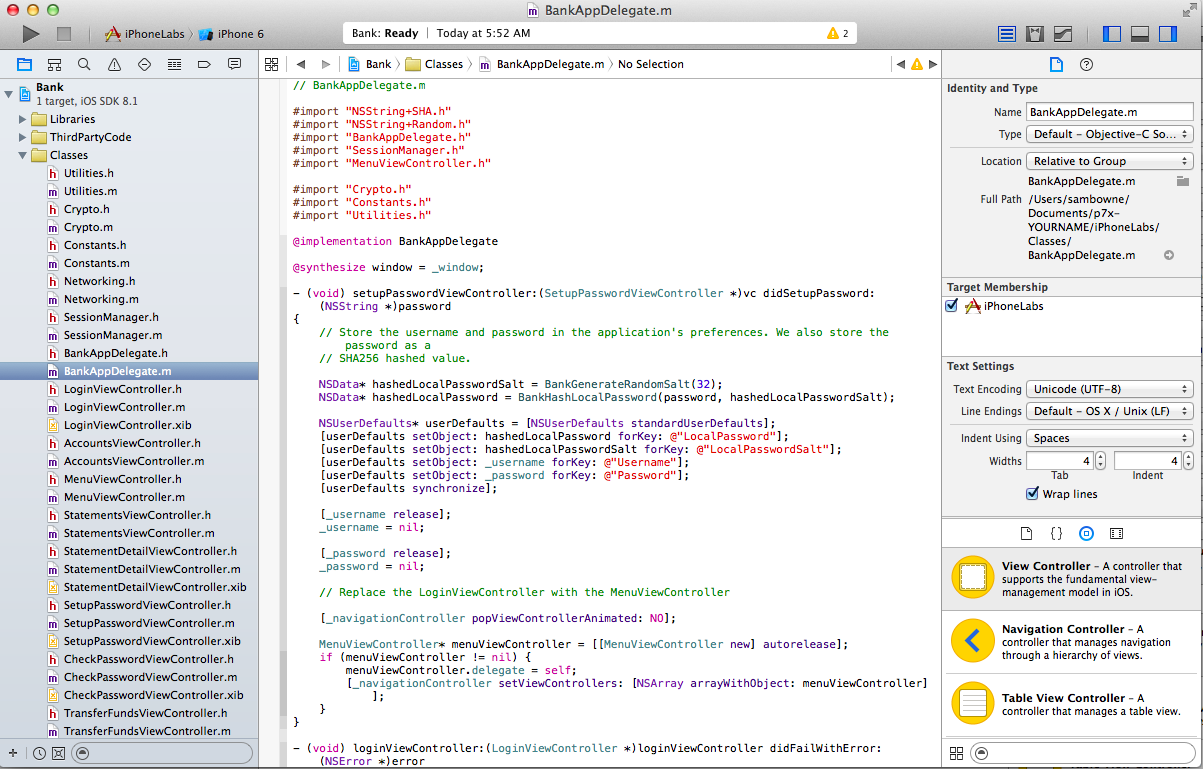
Click "Check Out".
The app's code loads. In the left pane, expand Bank and expand Classes to see the modules containing the code that handles banking functions, as shown below.
https://github.com/securitycompass/LabServer
On the right side, click "Download ZIP".
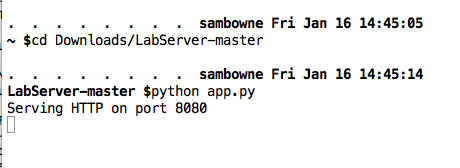
Find the LabServer-master.zip file and unzip it. A LabServer-master folder appears.
Find the complete path to this folder. When I did it on my Mac, it was:
/Users/sambowne/Downloads/LabServer-masterExecute these commands, adjusting the path in the first command to the correct path for your machine:
cd /Users/sambowne/Downloads/LabServer-master
python app.py
Leave this window open.
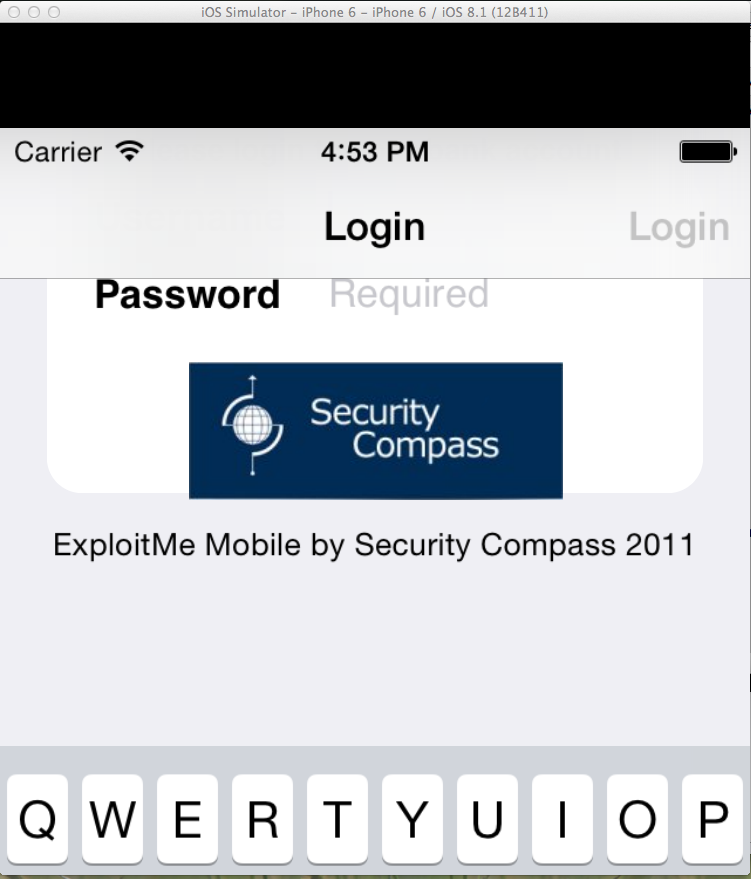
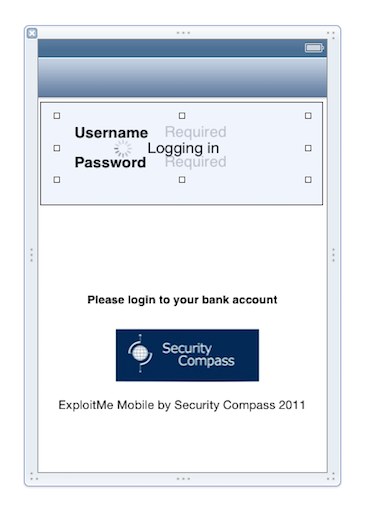
The app launches, very poorly laid out, so you cannot see the username field, as shown below.
Notice this phrase: "Please login".
Troubleshooting
If you see an "Unlock" screen instead of a "Login" screen, the app is retaining old data from a previous execution.To clear the old data, in iOS Simulator, from the menu bar, click "iOS Simulator", "Reset Content and Settings".
Then close the emulator and re-launch the app.
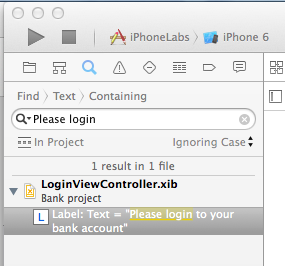
In Xcode, from the menu bar, click Find, "Find in Project...".
At the top left of the Xcode window, enter this search string:
Please login
A Label is found with the phrase "Please login to your bank account", as shown below.
Double-click "Please login to your bank account".
A window opens showing the layout of the screen at login, as shown below.
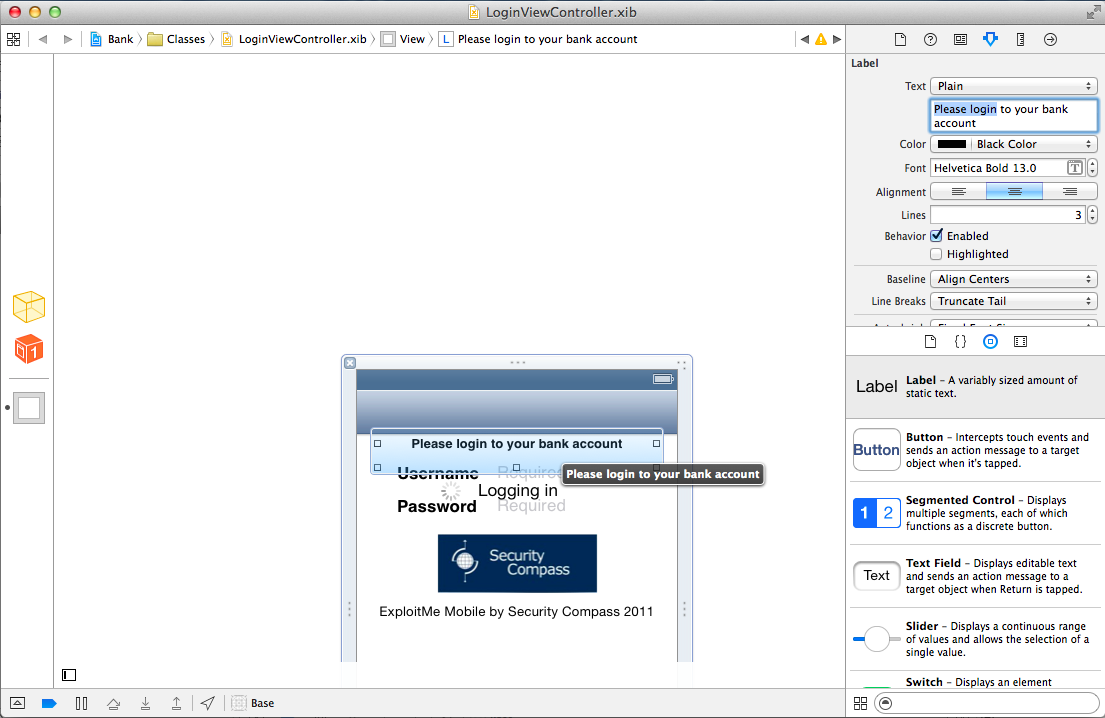
Drag the "Please login to your bank account" label, the logo, and the "ExploitMe Mobile by Security Compass 2011" label down 1 to 2 inches, as shown below.
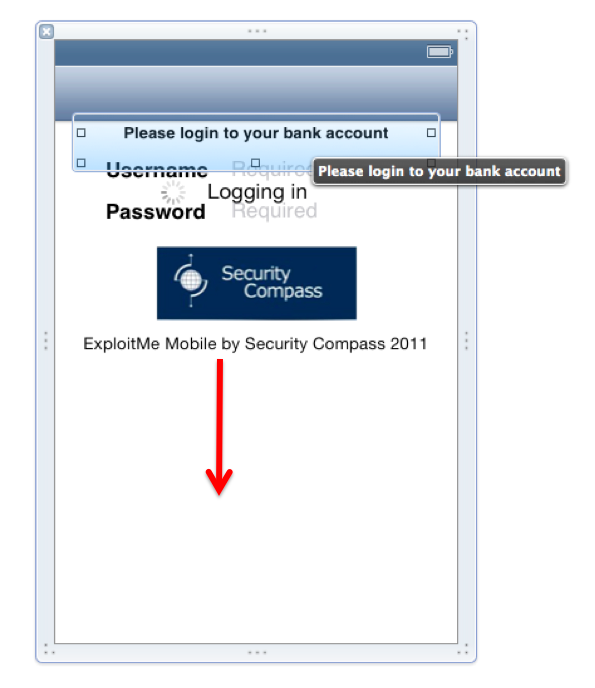
Your screen should now look like this:
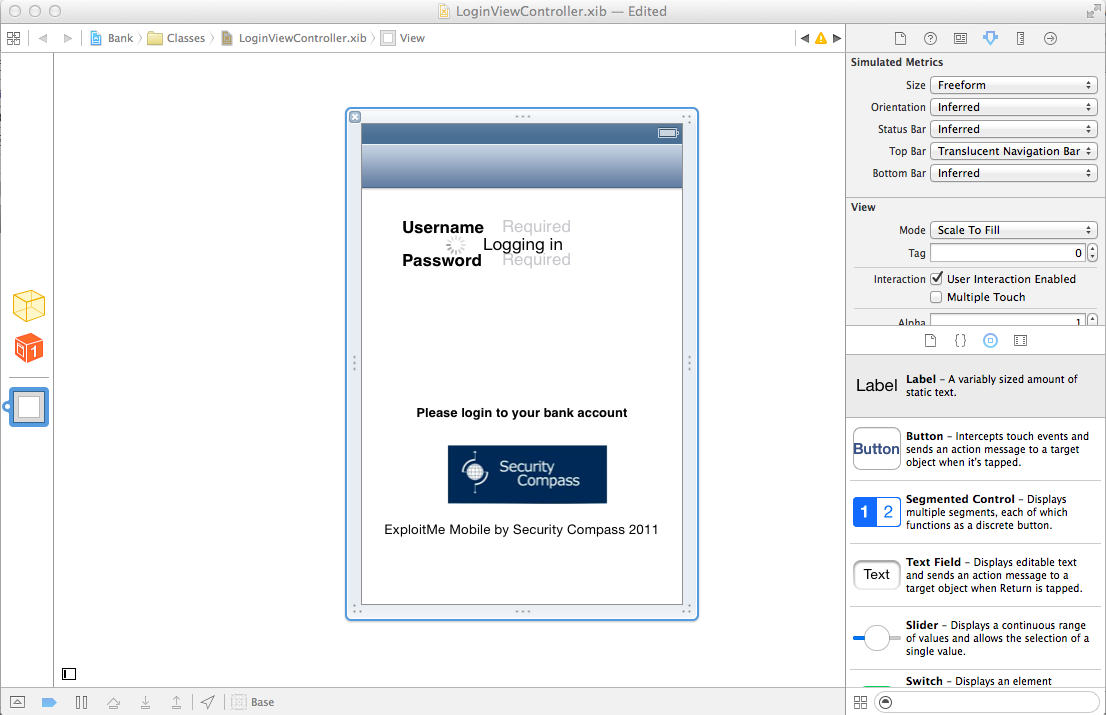
Using the mouse, draw a rectangle around the login area, as shown below:
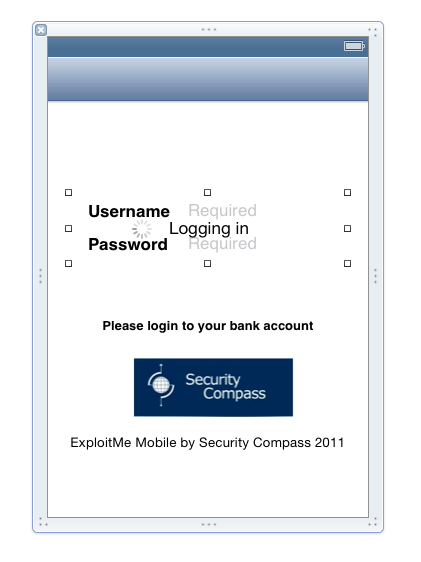
On your keyboard, hold down the down-arrow key long enough to move the login area down 1 inch, as shown below:
From the Xcode menu bar, click Product, Run.
A box pops up asking 'Stop "Base"?'. Click Stop.
The app launches. Now you can see what you are doing!
Log in as jdoe with a password of password, as shown below:
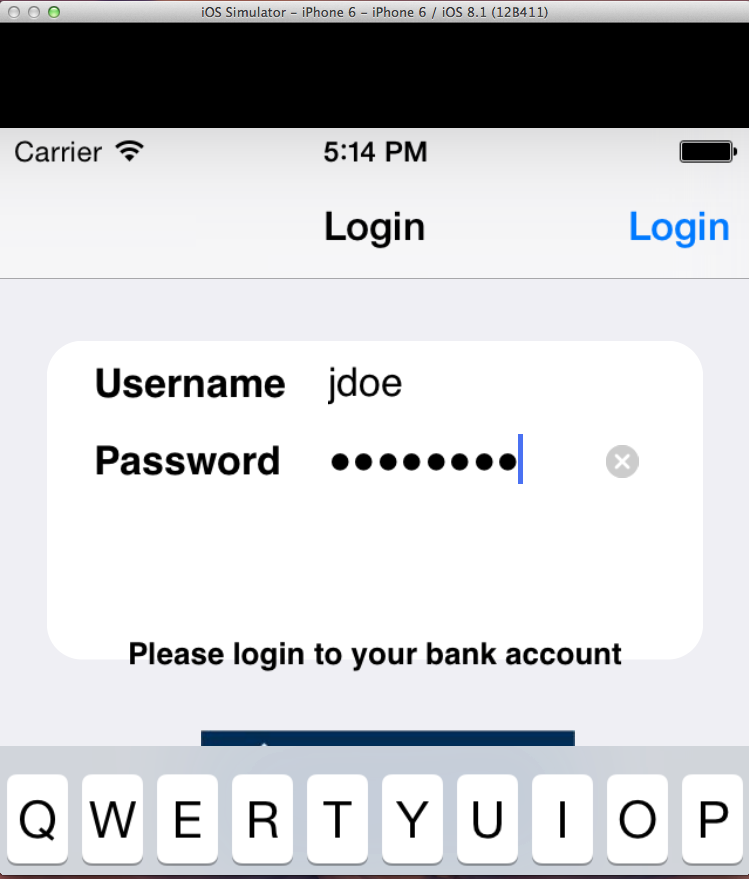
The next screen is also poorly laid out, but you can just barely see enough to use it.
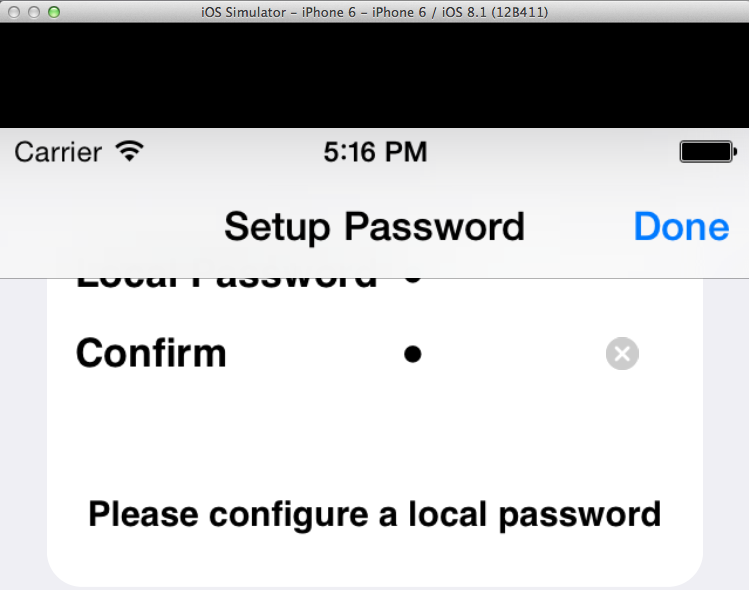
Enter a password of 1 in both fields, as shown below, and click Done.
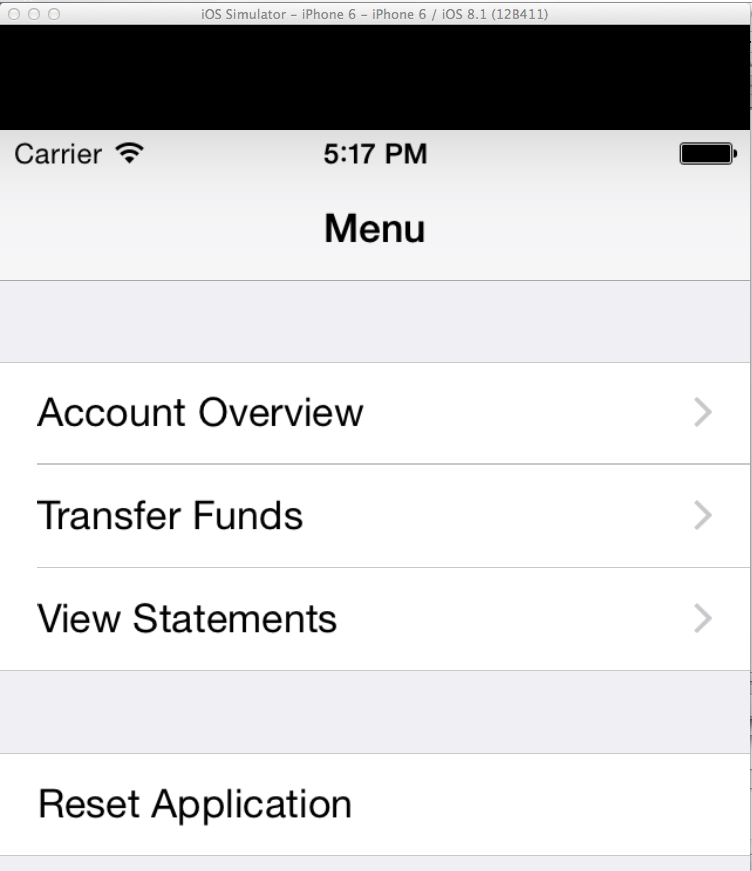
Now you see the main bank screen, as shown below.
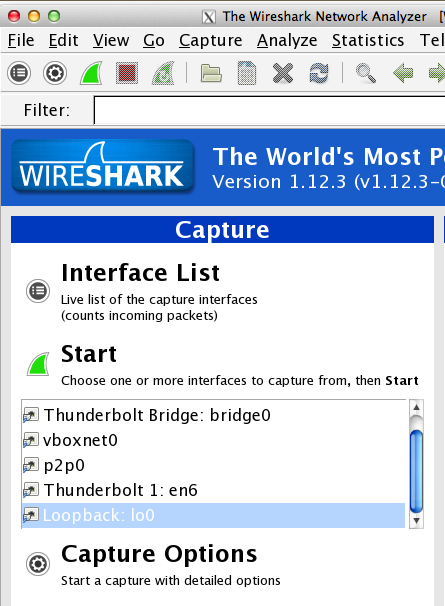
Launch Wireshark.
In the interface list, click "Loopback: lo0", as shown below, and click Start.
In Wireshark, in the green filter field, enter this display filter, as shown below.
tcp.port==8080
In the iOS simulator, click Transfer and transfer a dollar.
Wireshark shows several captured packets, as shown below.
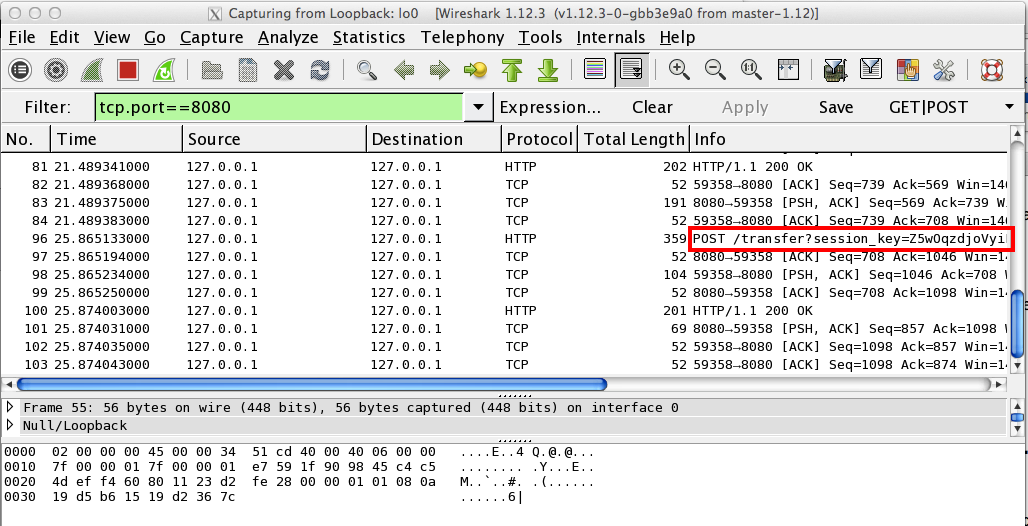
In Wireshark, find the "POST /transfer" packet, as indicated in the image above by the red outline.
Point to "POST /transfer", press command, and click.
Click "Follow TCP Stream".
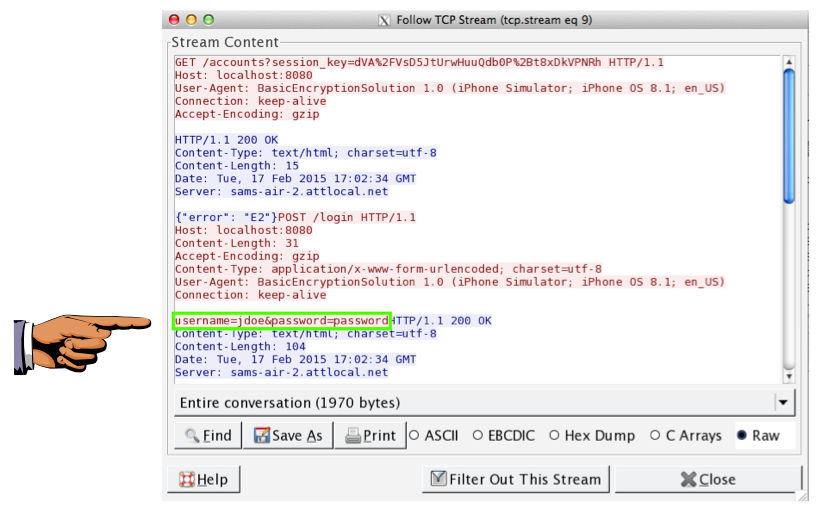
The stream should show the username and password transmitted in plaintext, as shown below.
Press Commmand+3 to save a full-desktop image.
YOU MUST SUBMIT A FULL-SCREEN IMAGE FOR FULL CREDIT!
Save the image with the filename "YOUR NAME Proj 8xa", replacing "YOUR NAME" with your real name.
On the left side, expand these items:
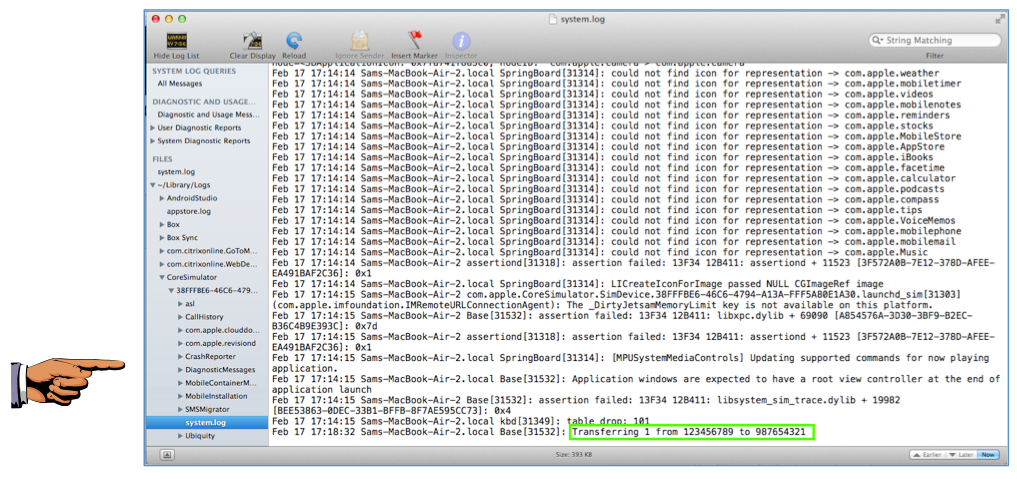
Find the log entry that exposes account numbers, as shown below.
Press Commmand+3 to save a full-desktop image.
YOU MUST SUBMIT A FULL-SCREEN IMAGE FOR FULL CREDIT!
Save the image with the filename "YOUR NAME Proj 8xb", replacing "YOUR NAME" with your real name.
~/Library/Developer/CoreSimulator/Devices
We'll search these folders with grep.
In a Terminal window, execute these commands:
cd
cd Library
cd Developer
cd CoreSimulator
cd Devices
grep -r jdoe .
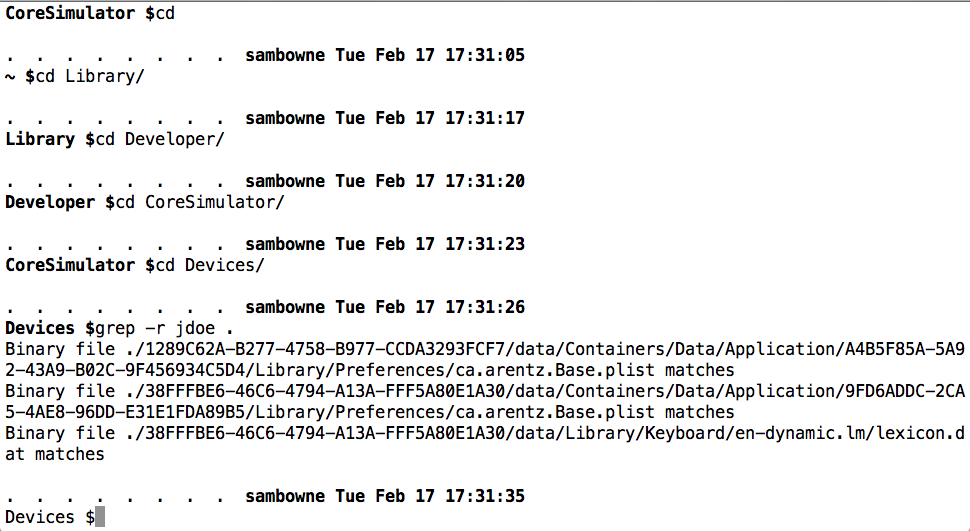
Copy and paste the whole path to one of these files, and append it to the word "nano", as shown below.
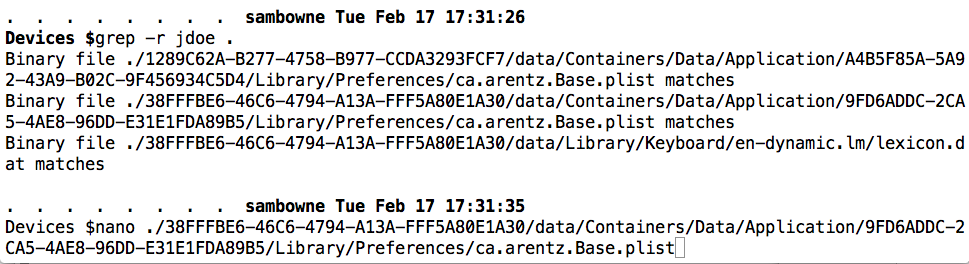
Press Enter to open the file in the nano text editor.
You see a file that contains a lot of unreadable binary characters, but it also contains jdoe and password in plain text, as shown below.
NOTE: "jdoe" and "password" may be separated by a long string of unreadable characters, so you may need to capture two images.
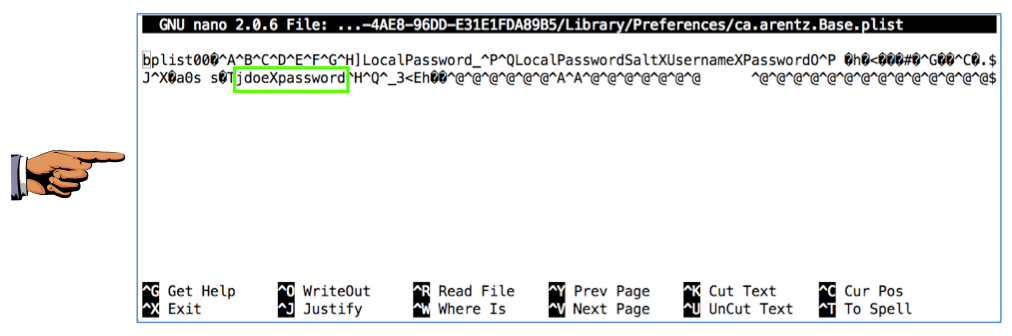
Press Commmand+3 to save a full-desktop image.
YOU MUST SUBMIT A FULL-SCREEN IMAGE FOR FULL CREDIT!
Save the image with the filename "YOUR NAME Proj 8xc", replacing "YOUR NAME" with your real name.
Where does the iPhone Simulator store its data?
Cleaning up the iPhone simulator