
You should have the server app running, listening on port 8081, as shown below.
Burp should be running, forwarding traffic from port 8080 to port 8081, as shown below.
In the emulator, click Statement. If you are prompted to log in, log in with a password of P@ssw0rd
In the lower left of the emulator, click the back button.
In the emulator, click on Accounts.
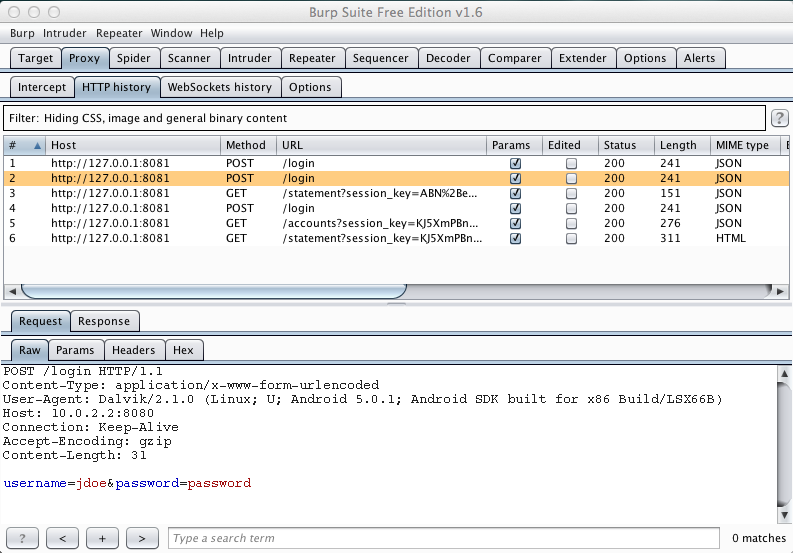
Burp should show intercepted HTTP traffic, as shown below.
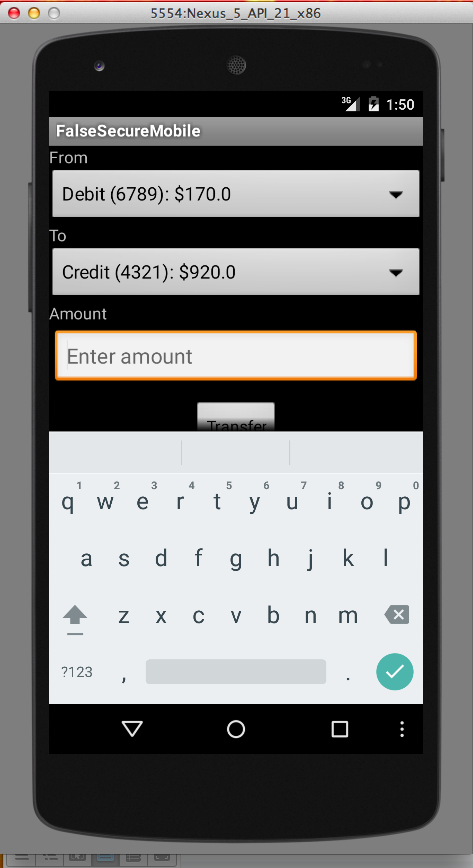
Note your current balances. When I did it, I had $170 in Debit, and $920 in Credit.
Also notice your account numbers. You have two accounts, one ending in "6789" and one ending in "4321".
Enter an amount of 10 but do NOT click the "Transfer" button yet, as shown below.
In Burp, on the Proxy tab, click the Intercept tab.
Click the "Intercept is off" button.
Now the button says "Intercept is on" as shown below.
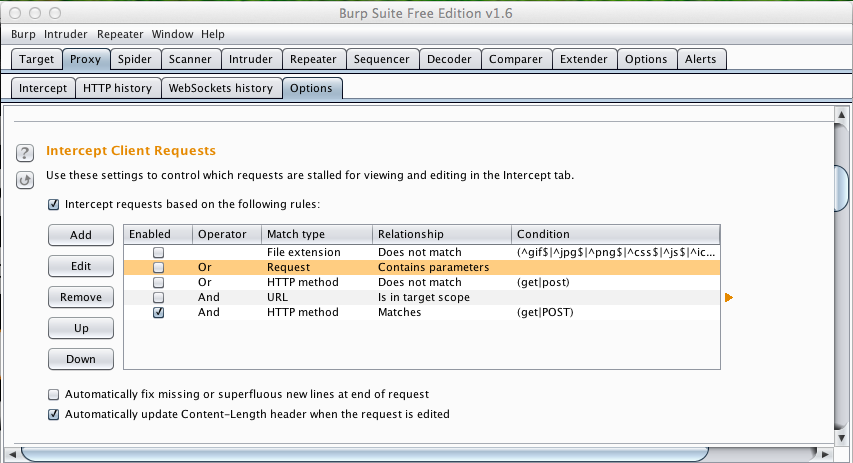
In Burp, on the Proxy tab, click the Options tab.
Scroll down to the "Intercept Client Requests" section.
Check the "Intercept responses based on the following rules:" box.
In the list of rules, check only the last item "HTTP method Matches (get|POST)", as shown below.
In the emulator, click the Transfer button.
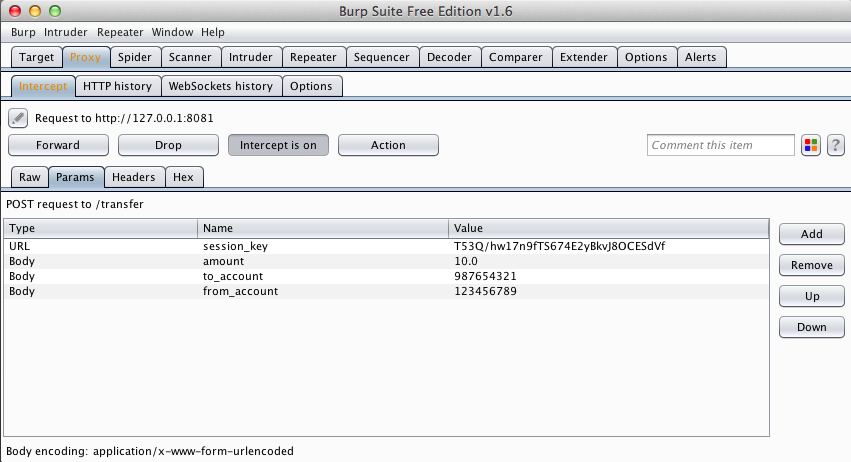
In Burp, click the Intercept tab. You see the intercepted request. In the center of the Burp window, click the Params tab.
You see the parameters of the request, including "amount", "to_account", and "from_account", as shown below.
In Burp, click the Forward button to allow this request to pass through.
Another request is intercepted within a few seconds.
Click the Forward button again.
The emulator shows a "Transfer complete" message.
In the emulator, return to the Transfers screen.
In Burp, forward the traffic, as required.
The balances have changed--Debit has gone down by $10 and Credit has gone up, as shown below.
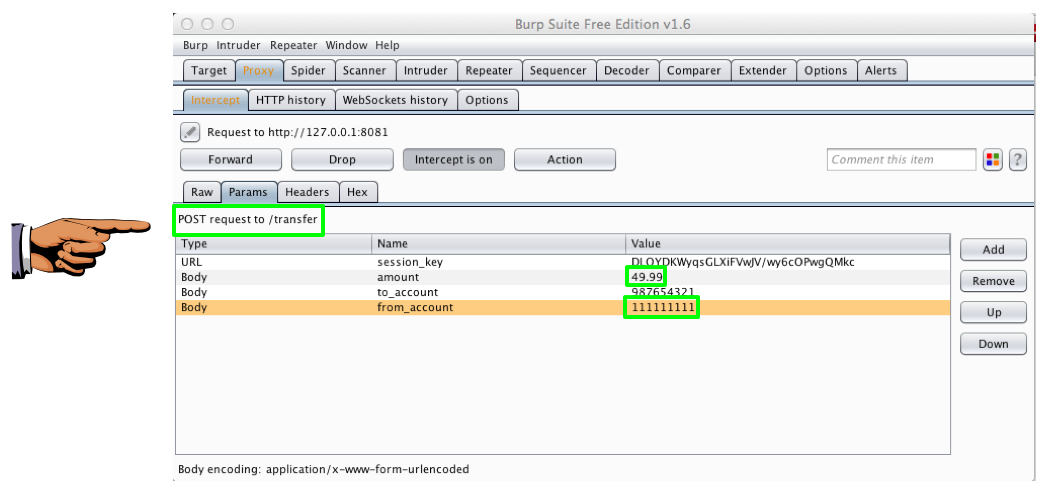
Burp intercepts the POST request.
In Burp, on the "from_account" line, double-cick the account number of 123456789.
Change that number to 111111111, and press Enter, as shown below.
Note: This is someone else's account. You are stealing that person's money.
YOU MUST SUBMIT A FULL-SCREEN IMAGE FOR FULL CREDIT!
Save the image with the filename "YOUR NAME Proj 5a", replacing "YOUR NAME" with your real name.
Another request is intercepted within a few seconds.
Click the Forward button again.
The emulator shows a "Transfer complete" message.
In the emulator, return to the Transfers screen.
In Burp, forward the traffic, as required.
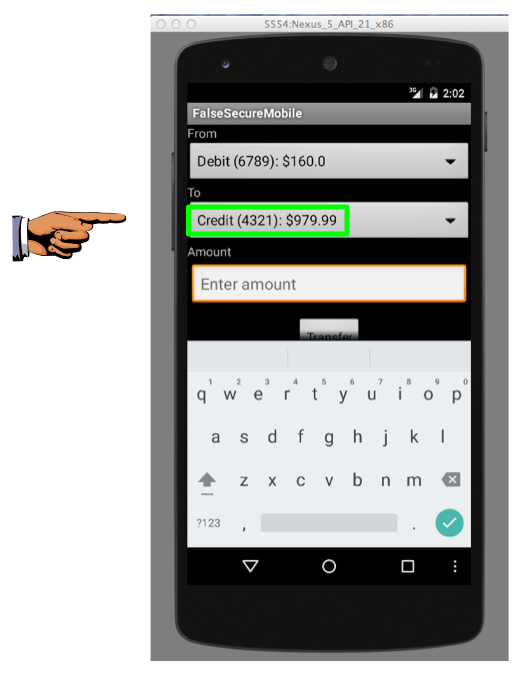
Now your Credit balance ends in 99 cents, as shown below.
Save a full-desktop image. On a Mac, press Commmand+3. On a PC, press Shift+PrntScrn and paste into Paint.
YOU MUST SUBMIT A FULL-SCREEN IMAGE FOR FULL CREDIT!
Save the image with the filename "YOUR NAME Proj 5b", replacing "YOUR NAME" with your real name.
#validate that accounts belong to user:
if to_account.user != session.user or from_account.user != session.user:
return error("E6")