Proj 15: AndroBugs (10 pts)
What You Need for This Project
- A Kali virtual machine
- You should have that already set up from previous projects
Purpose
To practice using AndroBugs,
a really fast Android vulnerability scanner.
Installing AndroBugs
On Kali, in a Terminal,
execute these commands, to install
AndroBugs and scan the GenieMD APK file.
git clone https://github.com/AndroBugs/AndroBugs_Framework.git
cd AndroBugs_Framework
wget https://samsclass.info/128/proj/genie.apk
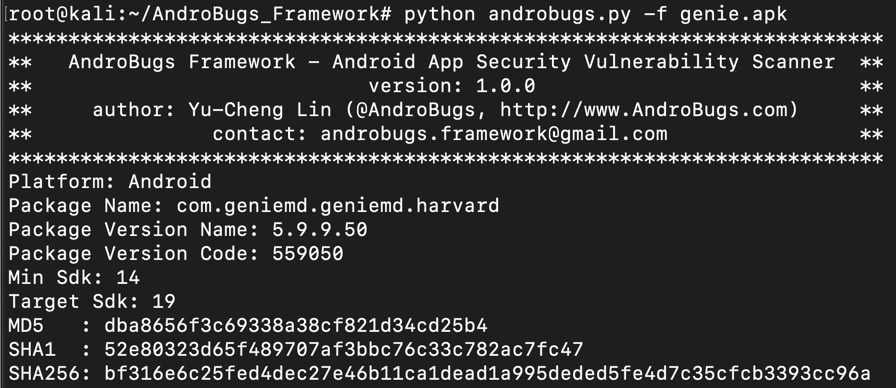
python androbugs.py -f genie.apk
The scanner starts,
as shown below.
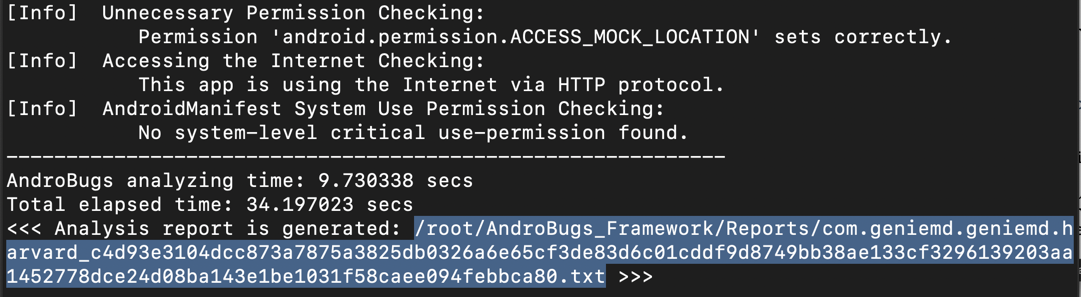
Within a minute, the scan finishes.
It prints out a long report
filename. Carefully copy the whole report name,
which is highlighted in the image below.
Viewing the Report
On Kali, in a Terminal, execute this command,
replacing filename with the correct filename
on your system:
nano /root/AndroBugs_Framework/Reports/com.geniemd.geniemd.harvard_c4d93e3104dcc873a7875a3825db0326a6e65cf3de83d6c01cddf9d8749bb38ae133cf3296139203aa1452778dce24d08ba143e1be1031f58caee094febbca80.txt
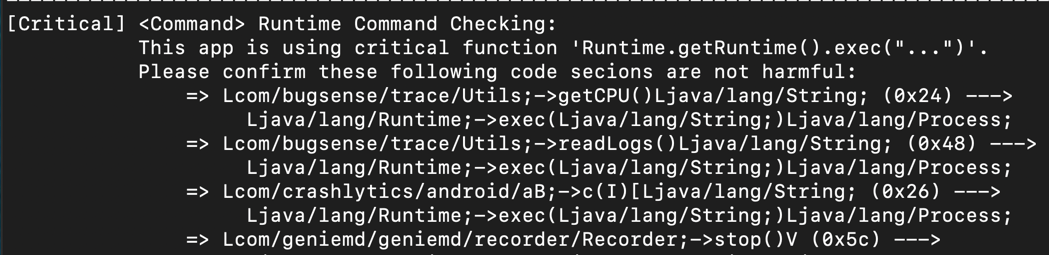
[Critical] <Command> Runtime Command Checking
This is the first vulnerability found, and it's
pretty scary.
These functions use Java to construct
Android shell commands, which frequently leads
to command injection flaws.
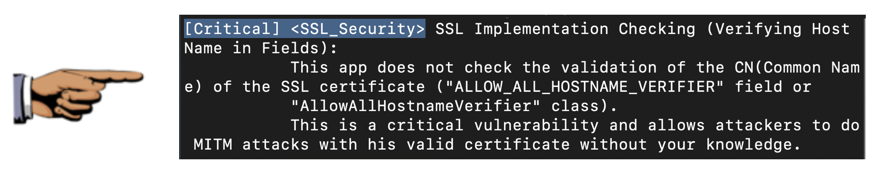
SSL Validation Flaws
Scroll down to find the SSL validation
error we exploited in a previous project.
This scanner provides a lot of information about
flaw, as shown below.
You should see your Genymotion device in the
"List of devices attached",
as shown below.
Saving a Screen Image
Make sure
you can see "[Critical] <SSL_Security>"
message,
as shown above.
Save a full-desktop image. On a Mac, press Shift+Commmand+3. On a PC, press Shift+PrntScrn and paste into Paint.
YOU MUST SUBMIT A FULL-SCREEN IMAGE FOR FULL CREDIT!
Save the image with the filename "YOUR NAME Proj 15", replacing "YOUR NAME" with your real name.
Turning in your Project
Email the image to
to cnit.128sam@gmail.com with the subject line:
Proj 15 from YOUR NAME
Posted 2-8-19 by Sam Bowne




