
In a Web browser, go to
https://www.oracle.com/technetwork/java/javase/downloads/index.html
Click the DOWNLOAD button, as shown below.

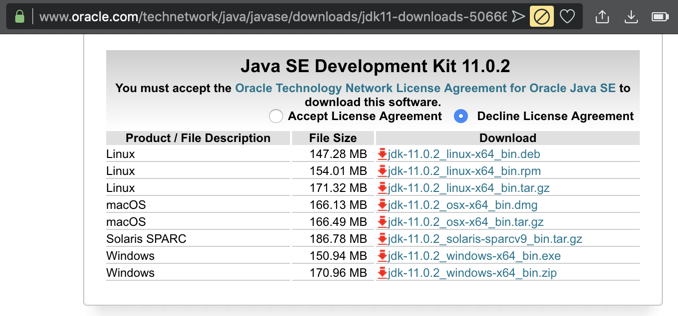
On the next page, download the correct version for your OS, as shown below.
Install the software with the default options, as shown below.
Click the "Download Ghidra" button, as shown below. Save the ghidra_9.0_PUBLIC_20190228.zip file in your Downloads folder.
Unzip the file. In Windows, don't double-click it; that just appears to unzip it. You must right-click it, click "Extract All...", and Extract.
If you are on a Mac or Linux, double-click ghidraRun, as shown below. If you are using Windows, double-click ghidraRun.bat.
An agreement pops up. Click "I Agree".
Ghidra opens, as shown below.
In the little "Tip of the Day" box, click the Close button.
One by one, right-click the links below and download the files. Save them in your Downloads folder.
Click Start, "File Explorer". In the left pane, click Downloads.
At the top left of this window, click File, "Open command prompt", "Open command prompt", as shown below.
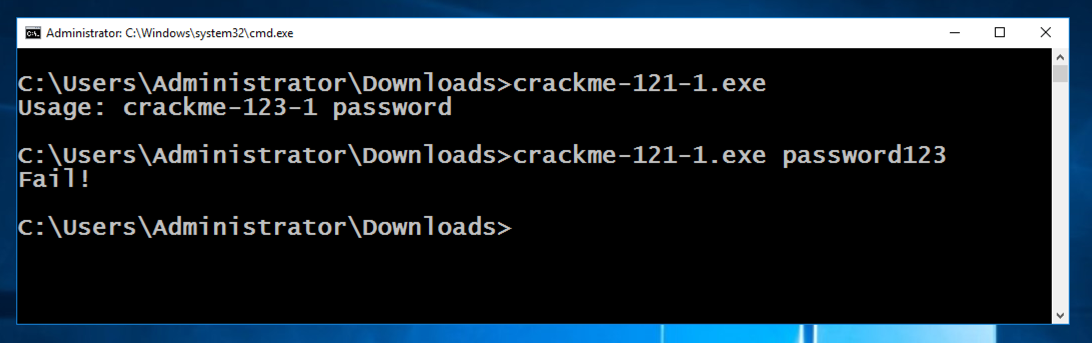
In the Command Prompt, execute these commands:
crackme-121-1.exe
crackme-121-1.exe password123
Close the Command Prompt window.
In the "Select Project Type" page, accept the default option of "Non-Shared Project" and click Finish.
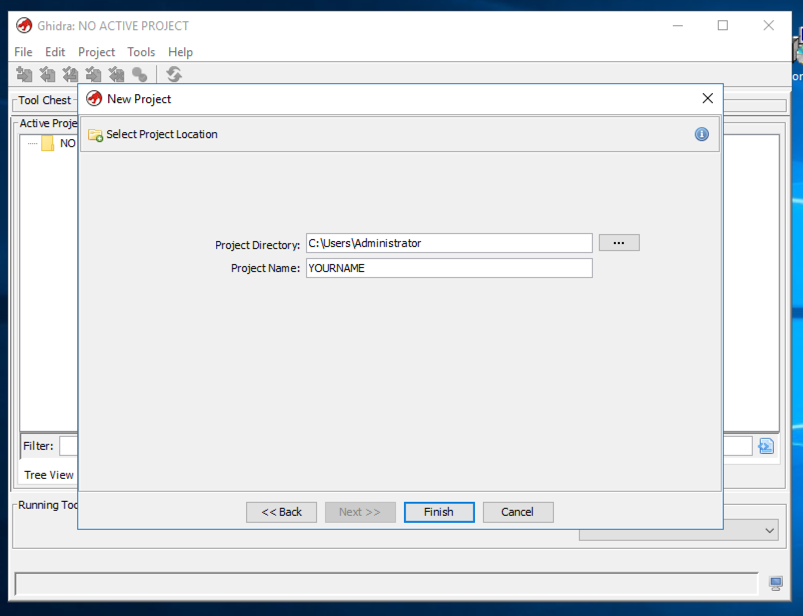
In the "Select Project Location" page, enter your name into the "Project Name" field, as shown below, and click Next>>.
In the "Ghidra:YOURNAME" window, at the top left, click File, "Import File...".
In the "Select File to Import" window, double-click Downloads and double-click crackme-121-1.exe.
A box pops up. Click OK.
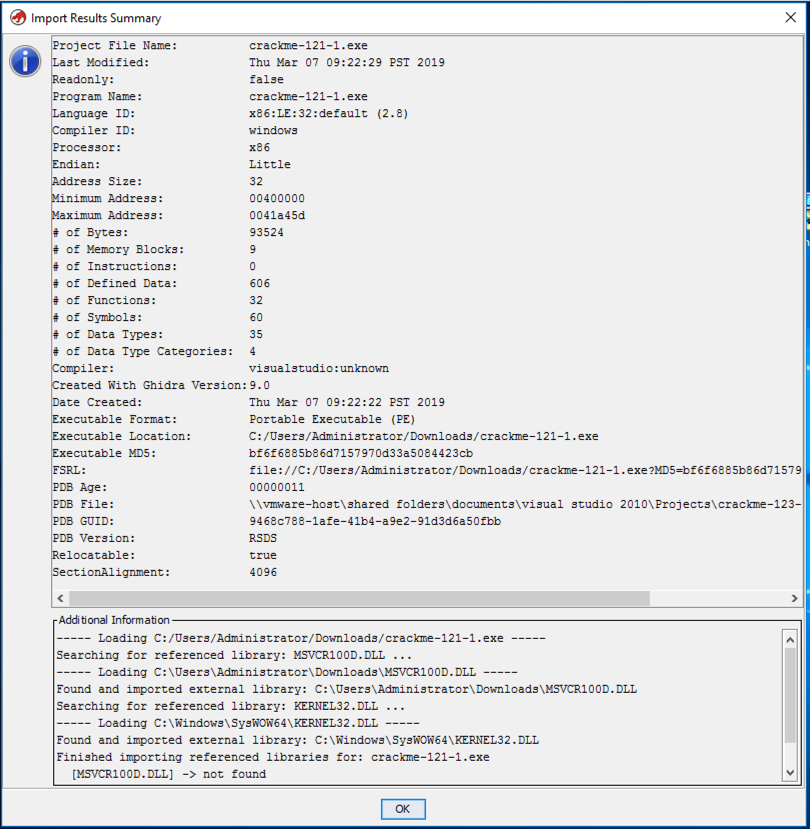
After a few seconds, an "Import Results Summary" box appears, as shown below.
Click OK.
A big window opens, with an "Analyze" box on top, as shown below. In the "Analyze" box, click Yes.
In the "Analyze Options" box, click Analyze.
In the "Auto-Analysis Summary" box, click OK.
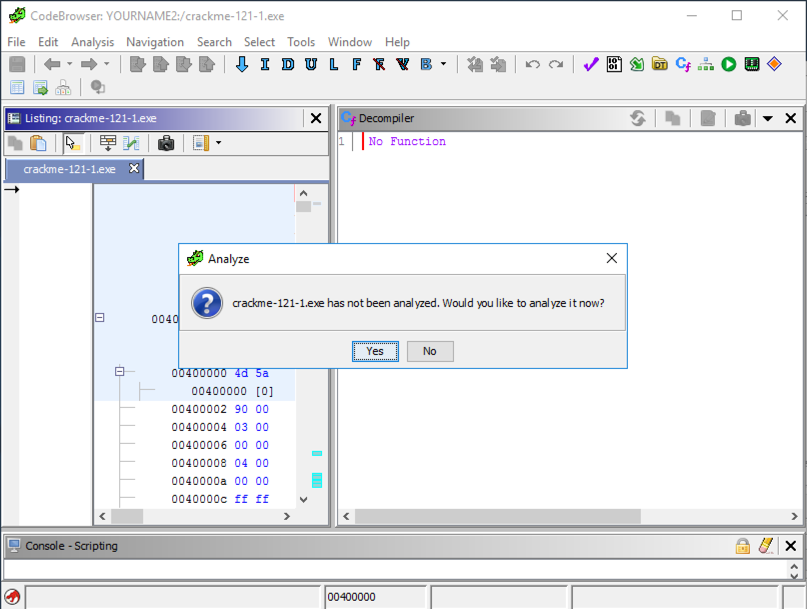
The main Ghidra window appears, showing the assembly code for the file in the large central pane, beginning at address 00400000 with the letters "MZ", as shown below.
All Windows executables start with those letters, at that relative address.
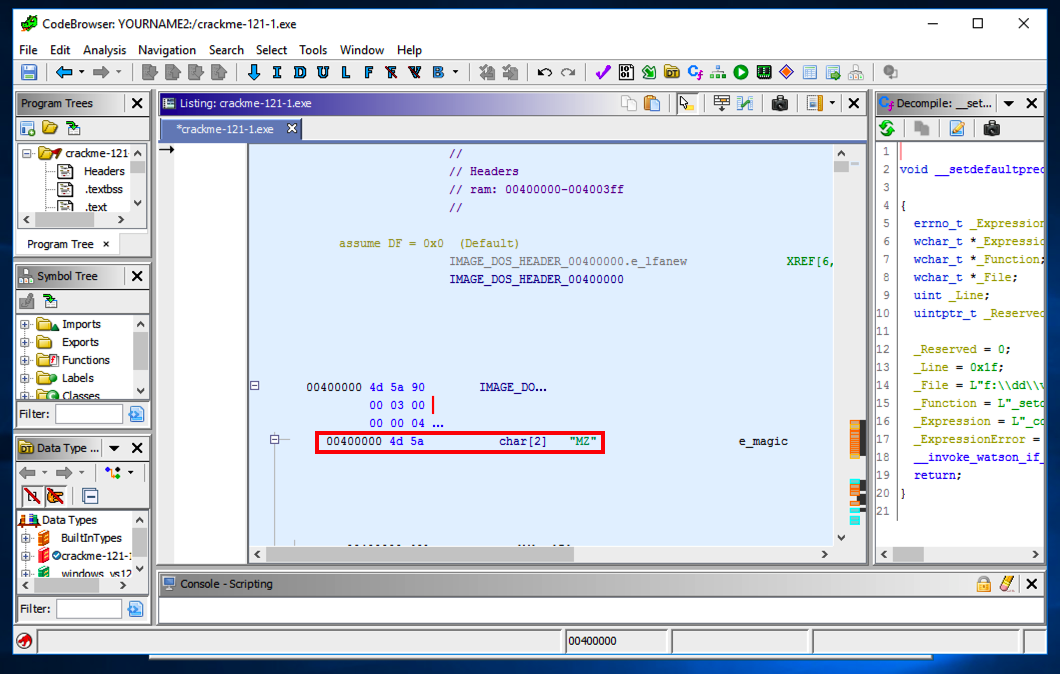
On the right side, a box appears showing readable strings.
Click Fail!.
The left pane shows the address where that string is stored, as shown below.
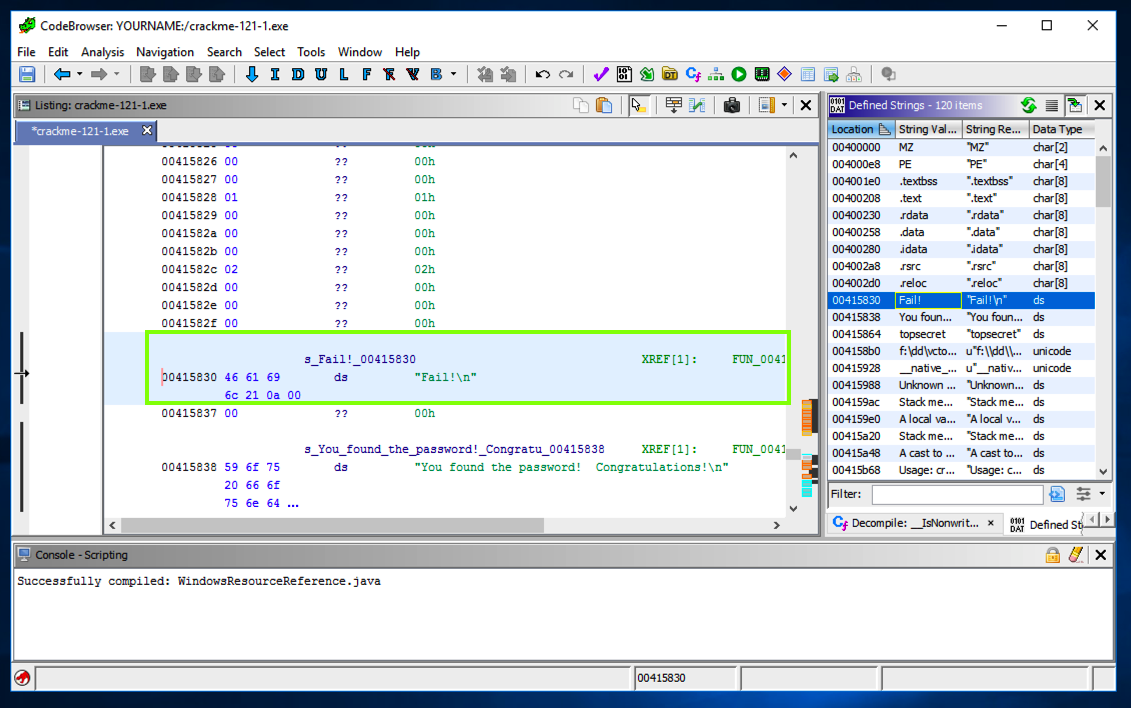
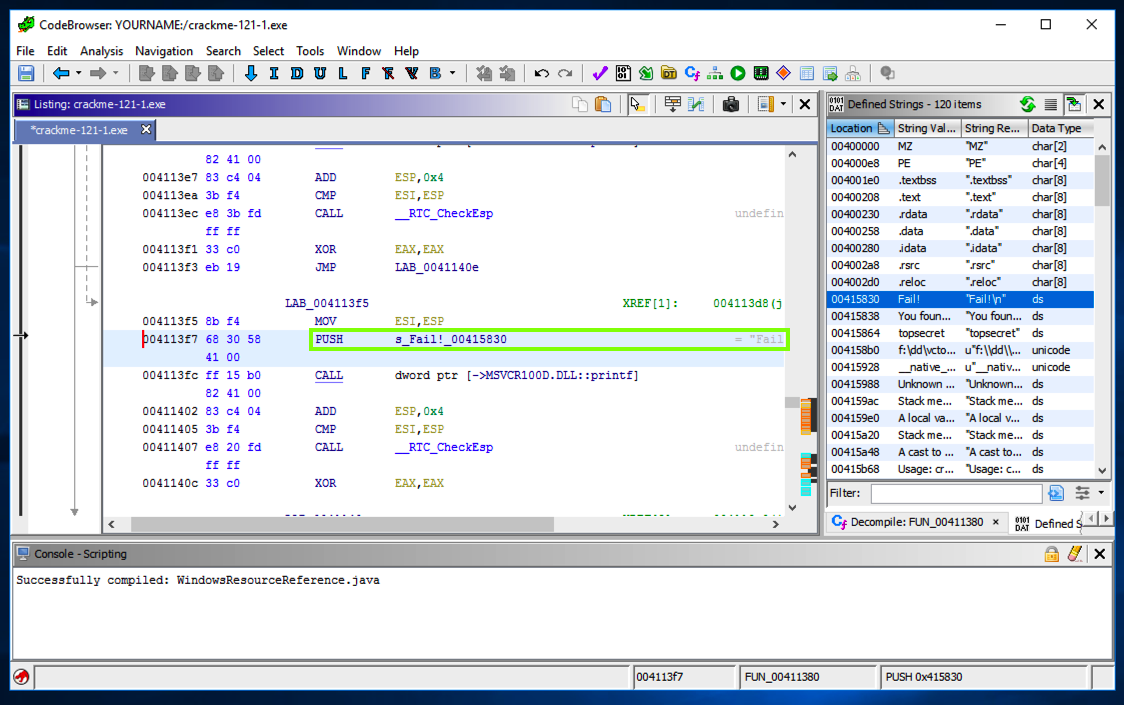
In the left pane, on the line showing the "Fail!\n" string, on the right side, after the "XREF" label, double-click FUN.
The left pane shows the assembly code that uses this string, with a "PUSH" command, as shown below.
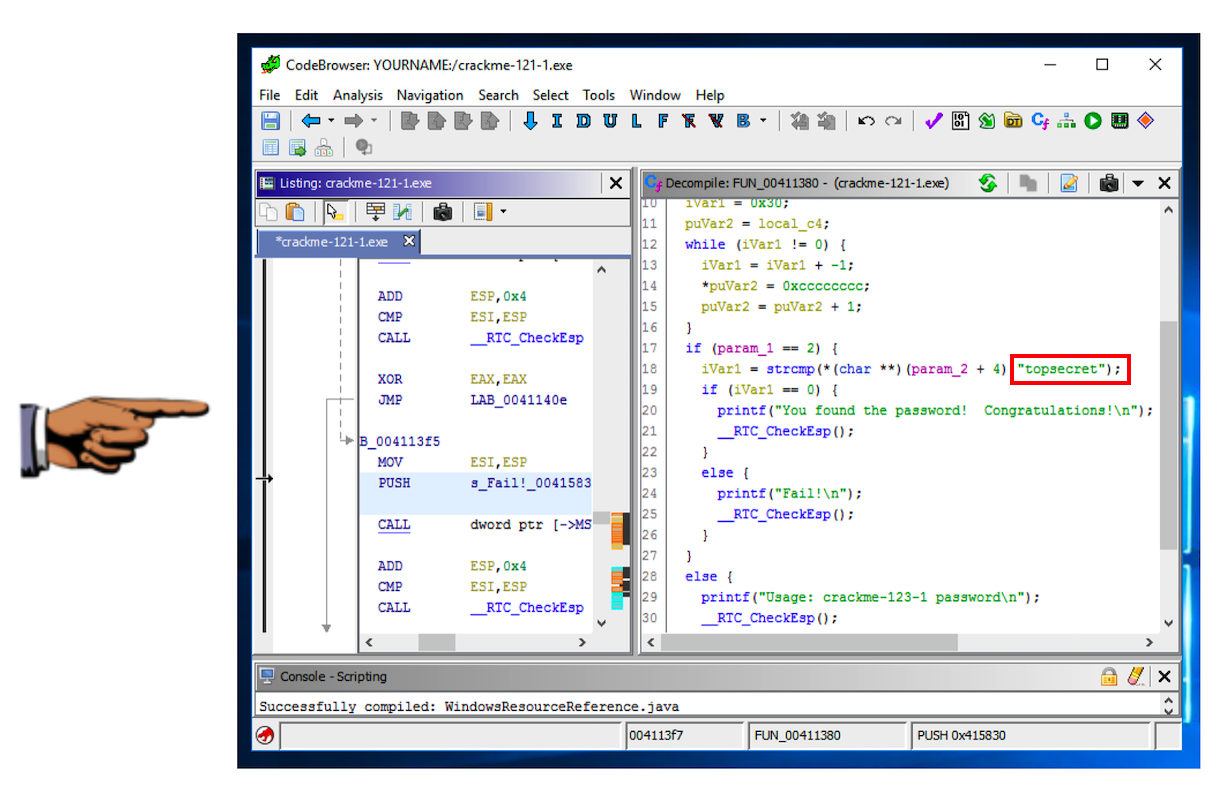
A "Decompile" pane appears, as shown below.
This is readable C code, and you can easily see that the password is topsecret
Save a full-desktop image. On a Mac, press Shift+Commmand+3. On a PC, press Shift+PrntScrn and paste into Paint.
YOU MUST SUBMIT A FULL-SCREEN IMAGE FOR FULL CREDIT!
Save the image with the filename "YOUR NAME Proj 11x", replacing "YOUR NAME" with your real name.
For extra credit, analyze the other three crackme files and find their passwords. Include those passwords in the body of your email message. Each correct recovered password is worth 5 additional points.